Unable to ping LAN hosts after connecting to VPN
-
There seem to be quite a few of these questions on here already. Unfortunately none of them helped me directly. I was able to successfully setup the VPN, export profiles, and remotely connect to the LAN. I am not, however, able to ping any LAN hosts other than the pfsense.
From what I have gathered across all the other posts, the problem is likely related to routing. It might have something to do with the default gateway maybe? Here are the details:
My network is configured fairly simply:
|---- hostB internet - (WAN) pfsense (LAN) - (WAN) WiFi router (LAN) - | |---- hostATo clarify, I can "see" VPN clients from the LAN, I just can't see LAN clients from the VPN. Actually, I can't even route to the router after connecting to the VPN, so none of the VPN client packets seem to get off the Netgate into the network.
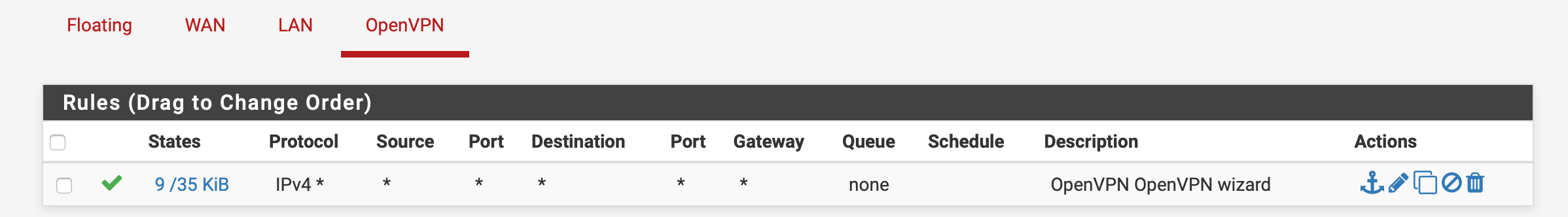
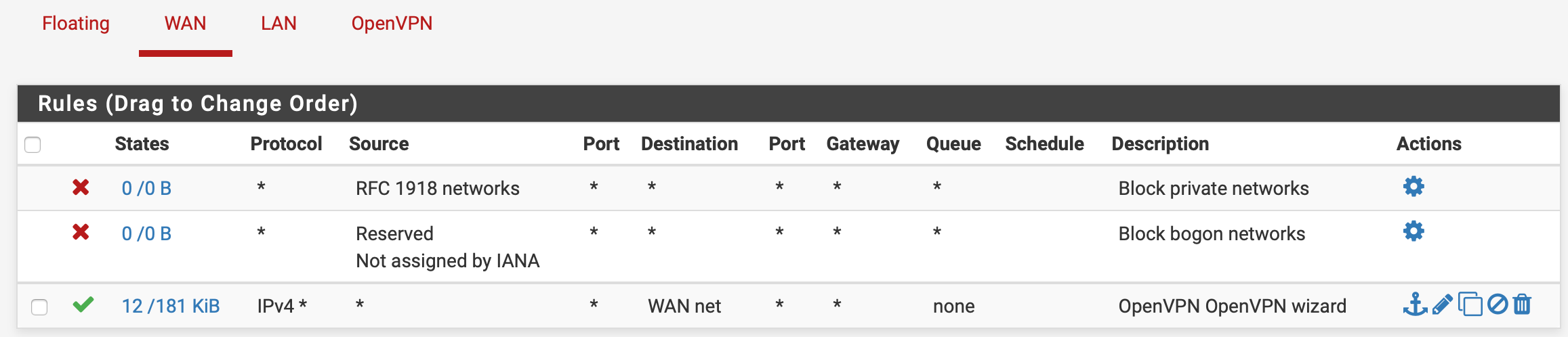
I'm no network guru, so I used the VPN setup wizard to help things along. It setup two rules in the firewall:
On the WAN:
On the OpenVPN group:
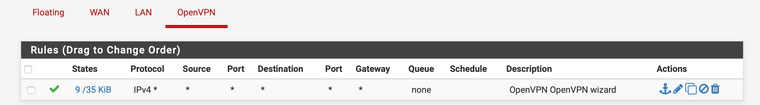
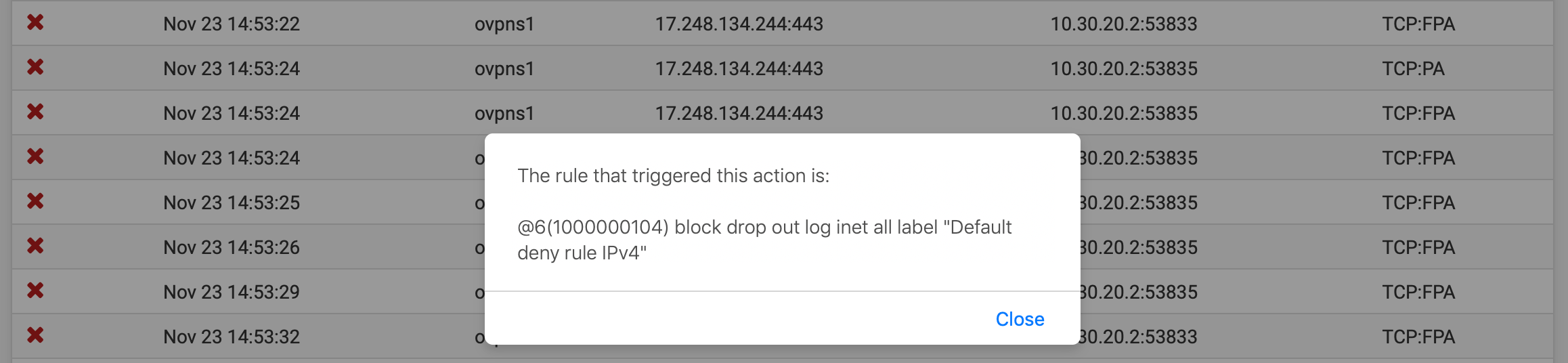
On all accounts it seems to me like the rules allow any to any, on any protocol. So I'm not sure why things aren't quite working. The firewall dynamic view shows lots of denied packets (10.30.20.2 is a client):
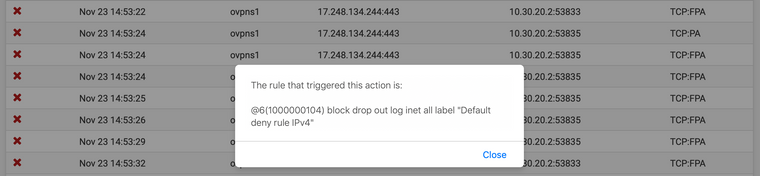
Except there is a rule explicitly allowing any IPv4, so I'm not sure why these packets are being denied.
Any advice?
-
And all of those blocked would seem to be out of state, see the A in the flags.. And even more than that all but one of them have the FIN flag, so they are FIN,ACK - meaning close this connection.
And they seem to be all to the same IP and port, so duplicate packets most likely anyway..
-
I wasn't aware those were flags. The column is labeled only as "Protocol". What can you infer from this?
The VPN has only a single client at the moment, which is me on another computer testing things out. On that client I am trying to ping LAN hosts or connect to a LAN share. The connections on the client are timing out, so it continues to try indefinitely.
Also, to further clarify, I can access the internet from the VPN as well. So rules back to to the WAN also work. It just seems that rules into the LAN are blocked. But the fact that I can see the VPN clients from the LAN is strange. Wouldn't the ICMP responses from the VPN client be blocked from being sent back into the LAN?
-
Without full understanding of your paths, hard to say exactly why your seeing them.
But the little i right on the firewall log shows you what they are
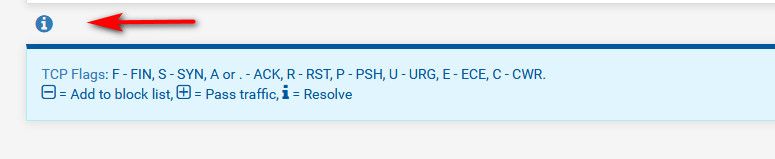
You can quite often see FA due to retrans when the client/server doesn't see a response for whatever reason on the closure of the session. And the state has been closed by the firewall.
When trying use a stateful firewall, its very helpful to understand how tcp initiates a session and how it closes a session ;)
Unless the block is S (syn) - its a given that the reason for the block is no state in the firewall for that traffic.
-
It depends on how things are connected and your config.
Post your server1.conf (/var/etc/openvpn).
Is PFsense connected to the WAN port on your WiFi router or the LAN port?
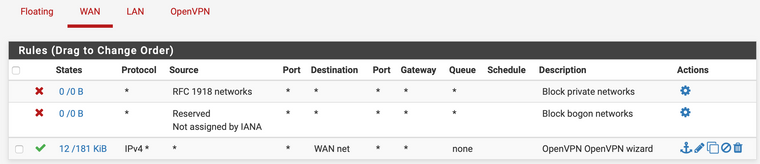
I'm also not sure about that firewall rule on your WAN tab. The wizard should give you something similar to this:
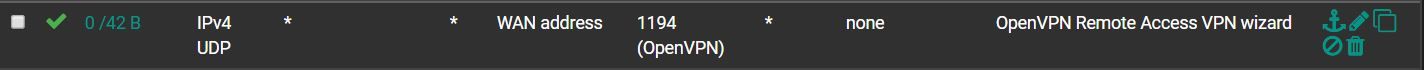
-
@sherrellbc said in Unable to ping LAN hosts after connecting to VPN:
I wasn't aware those were flags. The column is labeled only as "Protocol". What can you infer from this?
https://docs.netgate.com/pfsense/en/latest/firewall/tcp-flag-definitions.html
-
@marvosa said in Unable to ping LAN hosts after connecting to VPN:
It depends on how things are connected and your config.
Post your server1.conf (/var/etc/openvpn).
dev ovpns1 verb 4 dev-type tun dev-node /dev/tun1 writepid /var/run/openvpn_server1.pid #user nobody #group nobody script-security 3 daemon keepalive 10 60 ping-timer-rem persist-tun persist-key proto udp4 cipher AES-128-CBC auth SHA256 up /usr/local/sbin/ovpn-linkup down /usr/local/sbin/ovpn-linkdown client-connect /usr/local/sbin/openvpn.attributes.sh client-disconnect /usr/local/sbin/openvpn.attributes.sh local xx.xxx.xxx.xx tls-server server 10.30.20.0 255.255.255.0 client-config-dir /var/etc/openvpn-csc/server1 username-as-common-name plugin /usr/local/lib/openvpn/plugins/openvpn-plugin-auth-script.so /usr/local/sbin/ovpn_auth_verify_async user TG9jYYwgRGF1YWJhc2U= false server1 1194 tls-verify "/usr/local/sbin/ovpn_auth_verify tls 'xxx.net' 1" lport 1194 management /var/etc/openvpn/server1.sock unix max-clients 1 push "dhcp-option DOMAIN localdomain" push "dhcp-option DNS 10.0.0.1" push "redirect-gateway def1" ca /var/etc/openvpn/server1.ca cert /var/etc/openvpn/server1.cert key /var/etc/openvpn/server1.key dh /etc/dh-parameters.2048 tls-auth /var/etc/openvpn/server1.tls-auth 0 ncp-ciphers AES-128-GCM persist-remote-ip float topology subnetIs PFsense connected to the WAN port on your WiFi router or the LAN port?
The WAN port. And it serves DHCP to my router.
I'm also not sure about that firewall rule on your WAN tab. The wizard should give you something similar to this:
I think that rule is certainly better, as the other I showed allowed much more through the firewall. I edited the rule as you show. I am able to still connect, so I'll leave the restrictive rule. Thanks for that.
-
Is something happening to the connection, and you have it flushing states? Do you always see these blocks, all the time - or do they happen now and then?
Such out of state blocks will be seen from time to time depending... If a connection is wireless for sure you could see such dup packets and blocks on out of state when firewall closed the states due to see fins but one side didn't get the final fin and thinks its not actually closed.. At some point if the you should see a RST, when the device gives up his retrans and says F it, this is closed and sends a RST..
Cell phones are horrible at producing them when it switches from cell and wifi and tries to use the same session without reopening a connection with syn, etc.
-
I haven't really done any configuration tuning. All I did was use the OpenVPN wizard to setup the server. I exported the profiles and used them to connect a client. That's when I noticed can't see any any LAN hosts after connecting via VPN.
I actually had just configured the Netgate for the first time just before installing the VPN server package. So the whole config is nearly stock.
But no, the log is not generally filled with lots of blocks of the type shown. After connection from an mobile device I'll see a few.
Also, I forgot to mention that I can't even access the router from the VPN, though it is technically another LAN device. So it seems like I basically can't get off the Netgate after connecting to the VPN. I can't see anything after it on the network.
-
You are unable to access your LAN clients (hostA,hostB) from the VPN because your hosts are behind another NAT router and are not using PFsense as the default gateway. PFsense only knows about the IP given to the WAN interface on the WiFi router, it does not know about the network behind it nor does it have access to it.
The easiest way to address your issue is to modify your design slightly.
In other words, turn your router into an access point:
-
If your WiFi router has an access point mode, enable it.
a. Give the router a static IP on the subnet assigned to the PFsense LAN
b. Move the patch cable from the WAN port on the WiFi router into one of the LAN ports on the same router
c. Enabling access point mode automatically disables the DHCP server, so you will have to enable the PFsense DHCP server. -
If your WiFi router does NOT have an access point mode, the process is nearly the same, however, you'll have to disable services manually
a. Disable the DHCP server on the router
b. Disable the DNS forwarder (this is probably optional since it's not being used anyway, but doing so would save resources in theory)
b. Give the router a static IP on the subnet assigned to the PFsense LAN
c. Move the patch cable from the WAN port on the WiFi router into one of the LAN ports on the same router
d. Enable the DHCP server on PFsense
e. Enable the DNS server on PFsense
At this point, assuming there are no subnetting conflicts, you should now have access to your LAN resources after connecting to the VPN. Personally, I'd switch to a split tunnel deployment vs. full tunnel for performance reasons, but your use case may require different priorities.
-
-
That actually was the problem. I was mistakenly connecting the router's WAN port to the LAN port of the Netgate. Admittedly I should have recognized the issue with having the two networks (Netgate - Router, then Router's LAN).
So, everything just about works. I want to access a particular host on the LAN (a network share). I looked up the DHCP client list and found its assigned IP address and was able to remotely (through the VPN) connect to it. Because I wan't this to be reliable, I assigned a static DHCP rule for this specific LAN host. But now the VPN client's cannot see it anymore. What could be going on? All other dynamically allocated DHCP slots remain reachable from the VPN.
I have a rule on the OpenVPN group to allow any to any, which is why the first part worked. But for some reason the statically assigned DHCP rule is acting as if it were not part of the LAN? I did notice that the host was marked as "offline" in the DHCP client list despite being active and reachable from other hosts on the LAN.
I tried adding a rule specifically allowing access to this static IP from the VPN, but of, course, the any to any rule takes precedence so this new rule does not get used.
Any ideas?
Actually, the issue seemed to have resolved itself after some time.