FreeRadius / EAP-TLS: Client certificate cannot be found
-
I recently did my first pfSense installation and I'm now trying to get device authentication with EAP-TLS to work in a non-domain (workgroup) Windows 10 environment.
I have a ZyXEL GS1900 series managed switch that connects some wired PCs into the pfSense box. So far I have installed and configured FreeRadius, created a Root CA and an issuing CA with Cert.Manager, as well as created a client certificate request and signed it and installed the client certificate into a PC.
When trying to authenticate from the PC the only error message I seem to receive is in to PC's Wired-AutoConfig Event Log: "Network authentication failed. The user certificate required for the network can't be found on this computer".
No messages in the switch syslog and no messages in FreeRadius log, even after starting debug mode (radiusd -X).
I think I must have done some beginner's error but seem to be blind for that... I wonder if anyone has recently successfully configured EAP-TLS for Windows PCs with pfSense/FreeRadius and could give me some hint where I might have erred?
The certificate I created for the PC was a "User Certificate" in FreeRadius terms, but I want it to authenticate the PC and not the user, so I filled the CN field with the hostname of the PC. In the Windows PC I have so far tried to import the certificate to both Local Machine and Current User vaults, in the "Personal" store and have tried both "Computer authentication" and "User or computer authentication", but the results are always the same...
-
Hi,
FreeRadius is a package ;)
What is your package version ?
Is it up to date ??Check this out : https://forum.netgate.com/topic/148414/freeradius3-certificates-for-tls-gone-after-updating-to-0-15-7_4
-
I'm still at 0.15.7_3 so that should not be a problem. I'm pretty sure it's just some stupid user error that I have done somewhere...
-
@DaveU said in FreeRadius / EAP-TLS: Client certificate cannot be found:
certificate required for the network can't be found on this computer".
That is not pfsense issue - that is on your PC..
-
That sounds logical, and it's one of the main things I have been suspecting, too...
However, since I have not been able to find the reason despite of several hours of googling and testing/trying I decided to ask here.
So currently my hope is that someone who has successfully configured FreeRadius to use EAP-TLS in a trivial wired non-domain Windows 10 environment, could point me to what the problem might be...
Any suggestions are greatly welcomed.
-
How are you trying to setup the connection - you manually select the certs you want to use
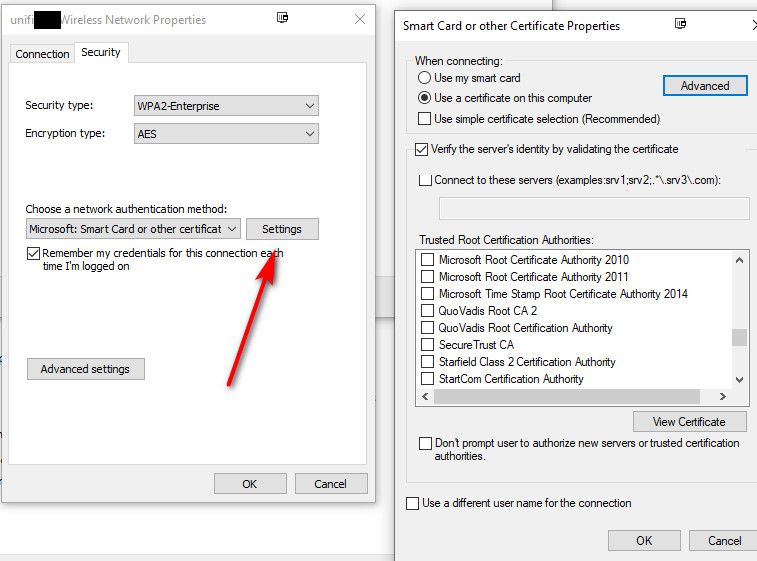
-
- When connecting: Use a certificate on this computer
- Use simplified certificate selection: Checked (have also tried unchecked)
- Verify the server's identity by validating the certificate: Unchecked
- Use a different user name for connection: Checked (have also tried unchecked)
- Advanced / Certificate Issuer: My Root CA and my Issuing CA selected (have also tried with Certificate Issuer unchecked)
- Extended Key Usage + All Purpose + Client Authorization + AnyPurpose and Client Authentication checked (have also tried with all of these unchecked)
-
Install the CA in your trusted ca authorities
Grab the p12 for your user account, grab the server cert your using for your freerad..
Install he p12 into your personal store and the server cert... When you setup your connection, pick your CA..
Now if your name machine and everything you will just connect..
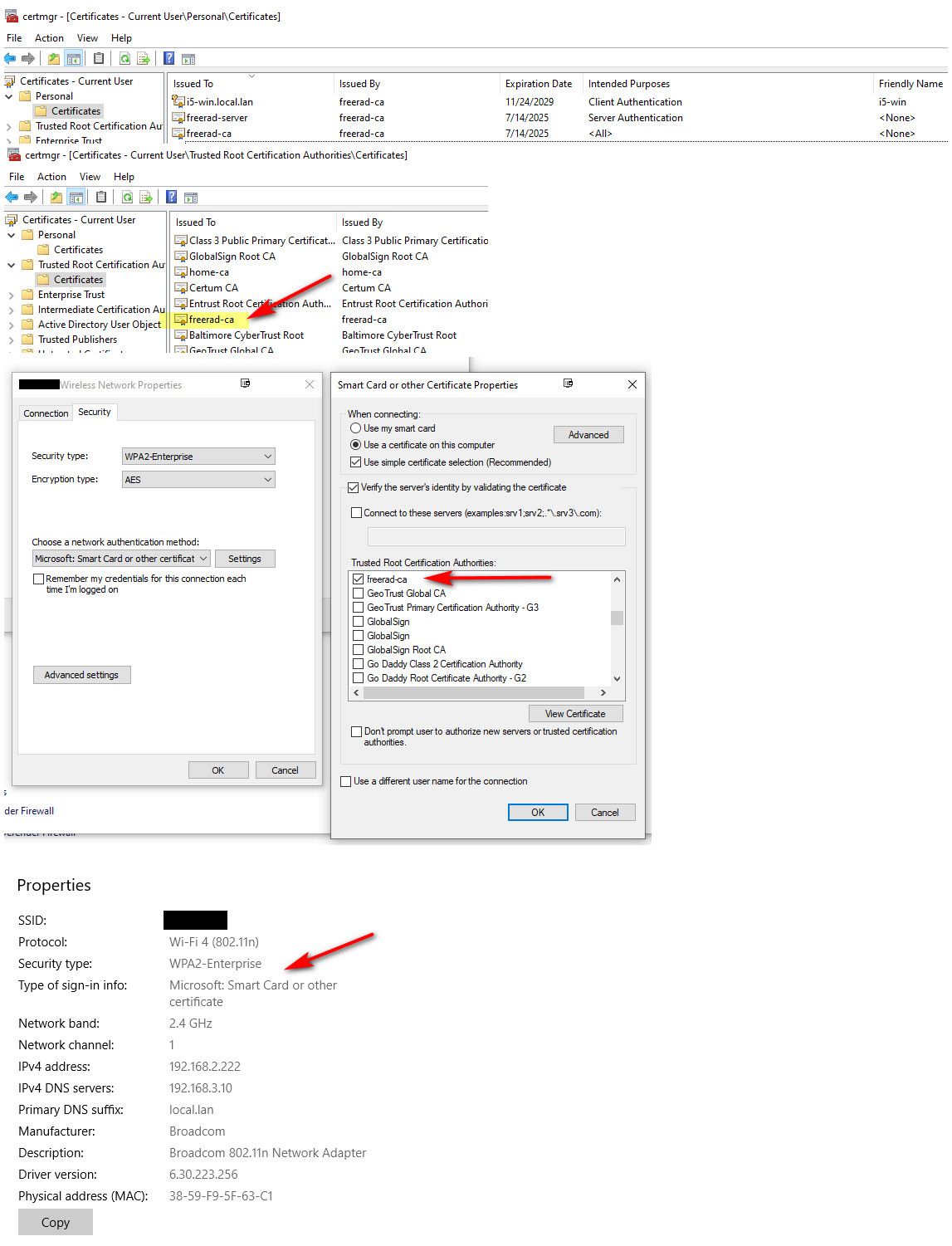
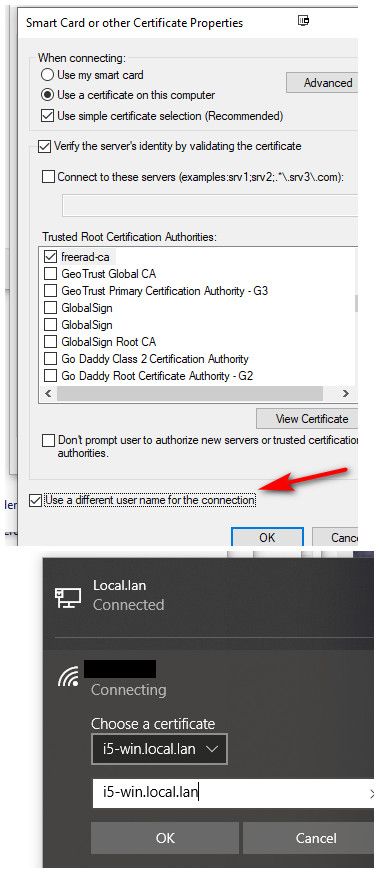
I you set to use a different name - you will get to pick the cert and put in the username, etc
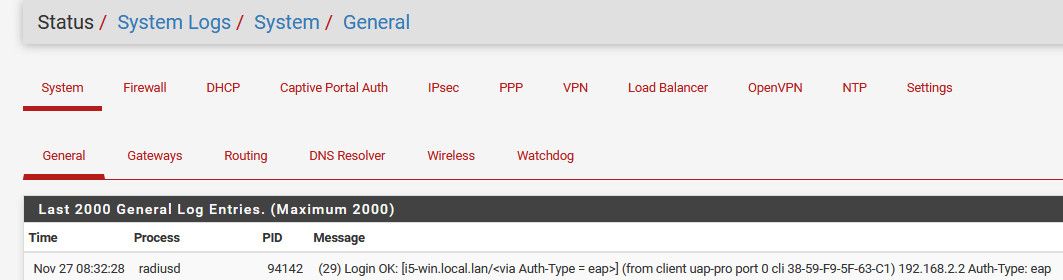
And you will see the auth in your log
-
Thank you for your ongoing support and quick replies. I do appreciate it!
To try to narrow down the problem I re-created the CA and certificates as follows:
- Root CA: DN = "A Root CA", CN = "A-Root-CA", all other fields in default values
- Server certificate: DN = "A Server Certificate", CA = "A Root CA", CN = "A-Server", all other fields in default values
- Client Certificate: DN = "A Client Certificate", CA = "A root CA", CN = "K5" [= Client PC Host name], all other fields in default values
Then I imported the CA into Trusted Root Certification Authorities in the PC, and the client and server certificates into Personal certificates (both into Current User and Local Machine vaults), used simple certificate selection, verify server's identity by validating the certificate "A-Root-CA", used a different name for the connection, and tried both "User or computer authentication" and "Computer authentication" as the authentication mode.
Still getting the same error message in the PC's Wired-Autoconfig Event Log "Network authentication failed. The user certificate required for the network can't be found on this computer" (Connection ID: 0x5, Identity: NULL, User: PK, Domain: K5, Reason: 0x50005).
To clarify one detail, I want to authenicate the workstation, not the user. That's why I have specified the PC host name as the CN in the Client certificate.
I must say that I'm a little bit confused on the terminology in the error message which talks about "user certificate" and not about "device certificate" even when I have specified "Computer authentication" for the authentication mode in the ethernet adapter properties...
-
You want the device to connect to the wifi network without a user logged in? What name you put on the cert has nothing to do with the user account actually logged in.
Notice my cert had name i5-win.local.lan on it - that is not the user name that logged into the machine with.
Make sure you forget this network if you had tried to set it up before, and start over...
PC's Wired-Autoconfig Event Log "Network authentication failed
Are you trying to set this up as 802.1x auth? Or eap-tls auth to wifi network?
I didn't read all the details of your first post :( When I get home I will look into 802.1x auth with certs.. For your wired connection? I have never needed or wanted to do that..
What switches are you using? This would not be setup direct from your client to freerad.. 802.1x auth would require your switch to be configured as well.. It would be the NAS that auths the client before it allows it to connect.
On your switch what have you setup - a simple google for your switch gs1900 and 802.1x setup finds their manual about how to do it and setup of NAS on the switch
-
I'm currently renewing a small office network. I have already replaced three Asus / Huawei Wi-Fi Routers with pfSense as a firewall and router, three ZyXEL GS1900 series managed switches and two Ubiquity UniFi access points.
I have already deployed some VLANs which work fine for both wireless and wired connections, and my next steps are to deploy EAP-TLS first to some wired wall outlets and later to wireless networks.
Some of the Windows PCs are used by multiple persons, so there are multiple user accounts. Hence I have planned to authenticate only the devices to the network, and users only to the devices. This is a non-domain network, consisting of one Windows workgroup.
FWIW, I forgot to mention in my previous reply that by default I have exported the certificates and CA in .crt instead of .p12. I also tried with the .p12 file but with same results. I wonder if there should be a major difference in whether I import the CA and certificates in .crt or .p12?
-
I forgot to mention that I do have enabled Radius authentication and configured the pfSense box as the radius server for the switches. I also have enabled 802.1X on the switch ports I'm currently testing.
-
I have lots of experience with doing eap-tls with wifi, but not so much with wired 802.1x on wired.. We have always done that in the past with full nac setup in a AD environment - have never tried to set it up with pfsense and freerad.. But I should have some time to play with it over the long holiday.. But no experience with those switches.
To be honest this seems a bit over the top for a small business setup - and your prob just going to cause yourself more pain supporting such a setup.. Is it justified?
Wouldn't it be easier to just setup port security if you don't want clients bringing in new devices or moving around - where you lock a port to a specific mac address?
What specific scenario are you trying to prevent?
-
Actually it's not a business but a non-profit organization where I work as a volunteer in my free time. And although I have a long work history within ICT business I'm neither a network specialist nor a security specialist...
The organization handles sensitive data but I cannot go into specifics here. That and the way the premises are used by various people, as well as my interest in getting to learn something about 802.1X has lead me to aim using EAP-TLS also in wired connections. FWIW, some years ago I worked in a company where they had deployed wired EAP-TLS and to my eyes and ears (as an end-user) it worked well.
I also think that EAP-TLS would be easier to manage (and should also be more secure) than MAC based port configuration: Only install a certificate once to each device and after that use it in whatever switch port, i.e. no client device based switch port configuration needed.
I also already verified that should the device authentication fail, the workstation etc. can still connect to the guest VLAN; the switch can do that trivially. This is exactly what I want: good service for all users, good security and easy to manage... if I only can figure out how to configure the certificates (and assuming that EAP-TLS within a non-domain UniFi WiFi network can also be configured with reasonable effort; that's something I have to try next..).
-
It seems that I can get Radius authentication to work without any problems with a username/password, both wired and wireless. It was very straightforward and easy.
However I cannot seem to find the correct way to authenticate with a certificate, neither wired nor wireless.
FreeRadius on pfSense throws four error messages into syslog for each authentication attempt with a certificate:
-
Nov 29 12:47:47 radiusd 35329 tls: TLS_accept: Error in error
-
Nov 29 12:47:47 radiusd 35329 (5) Login incorrect (Failed retrieving values required to evaluate condition): host/XXX/<via Auth-Type = eap>] (from client AP21 port 0 cli XX-XX-XX-XX-XX-XX) host/XXX -
-
Nov 29 12:47:51 radiusd 35329 tls: TLS_accept: Error in error
-
Nov 29 12:47:51 radiusd 35329 (10) Login incorrect (Failed retrieving values required to evaluate condition): [xx.xx@xxx.xxx/<via Auth-Type = eap>] (from client AP21 port 0 cli XX-XX-XX-XX-XX-XX) xx.xx@xxx.xxx -
So it seems quite obvius to me that I'm most likely doing some simple and stupid mistake, or I'm missing some crucial piece of information that I should have to get the certificates created and installed correctly. I understand the PKI principles and basic concepts but I have no previous practical experience in setting up a 802.1X authentication framework.
I wonder if there exists a step-by-step guide on certificate creation and deployment when using EAP-TLS authentication somewhere? Things like what is the exact requirement for the CN field format when creating the server and client certificates, or what other client dependent things should I keep in mind when creating the client certificate, or do I have to deploy the client and/or server certificate with the private key into the client etc...
Or could someone with recent practical experience please just give me the necessary steps?
One other thing that I have been wondering is I'm doing something wrong also in starting FreeRadius in debug mode, since I think I am not seeing Radius related debug level messages in syslog. I used the GUI Command Prompt to execute "killall radiusd" which seems to shut it down as expected. However executing "radiusd -X" in the same Command Prompt does not produce more information in the syslog for the next authentication attempts...
-
-
There is really nothing to creating the certs other than pushing go in the ca manager..
You problem is most likely around your settings in freerad..
Login incorrect (Failed retrieving values required to evaluate condition):
-
Yeah, but what setting?
I think it cannot be within the Interfaces or NAS/Clients settings, since I can successfully authenticate with username/password. So that leaves us the Users and EAP settings, right?
In EAP I have specified:
- disabled Weak EAP types
- TLS as default EAP type
- SSL CA Certificate "A Root CA" [imported in client Local Machine as Trusted Root CA vault]
- SSL Server Certificate "A Server Certificate" [imported in client Local Machine in Personal vault]
- All other in default settings
In Users settings I have tried to enter the Username in the same formats that can be seen in Radius syslog error messages when authentication is rejected (both in the hostname and in the email formats), all other fields in default values.
Do you happen know the exact steps to start radiusd in debug mode within pfSense GUI so that I could possibly get more info on the authentication reject reason?
Do you happen to know the exact format how the Username field in Radiusd configuration vs. CN etc. fields in the certificate have to be set to guarantee a match?
Do you happen to know in which format the client andr server certificates as well as the CA must be imported in the client (i.e. .crt / .p12, and why, if the format matters?)
-
A. To run Radius in debug mode , you need To
1. stop Radius service
/Status/Services
2. in the console type
radiusd -X
B.

C. (Mac OS)
Result
Fri Nov 29 16:39:45 2019 : Auth: (3181) Login OK: [macbookpro2015.XYZ.org/<via Auth-Type = eap>] (from client Asus_WRT port 110 cli 9801a78ceb89) Fri Nov 29 16:41:30 2019 : Auth: (3186) Login OK: [sony_xperia.XYZ.org/<via Auth-Type = eap>] (from client es.XYZ.org port 473 cli 176.AB.CD.67[55742]) -
@Konstanti Thank you for your examples!
The only menaningful difference btw your configuration and mine seems to be that you have imported the client certificate as a .p12 archive which (as far as I understand) contains also the private key, whereas I have imported the .crt file.
If I export the client cert from Cert.Manager and import it into the client, Windows asks me to enter the password with which the private key was protected, but I have not been able to find a way to specify the password for the private key in Cert.Manager. How did you do that?
I also seem to be getting somewhat inconsistent results in my authorization tests, i.e. not the same results each time I try to authorize. For the last few hours I have been trying only the wireless network since @johnpoz mentioned that he has experience with only that...
I have tried with two clients using different configurations, and I have got e.g. following results:
Case a)
Waking up in 4.9 seconds.
(1) Received Access-Request Id 186 from 10.16.1.105:45863 to 10.16.1.1:1812 length 385
(1) User-Name = "host/xxxxxxxxxxxxxxx"
(1) NAS-Identifier = "xxxxxxxxxxxxxx"
(1) Called-Station-Id = "XX-XX-XX:XXX_XXX"
(1) NAS-Port-Type = Wireless-802.11
(1) Service-Type = Framed-User
(1) Calling-Station-Id = "XX-XX-XX"
(1) Connect-Info = "CONNECT 0Mbps 802.11b"
(1) Acct-Session-Id = "XXXXXXXXXXX"
(1) WLAN-Pairwise-Cipher = 1027076
(1) WLAN-Group-Cipher = 1027076
(1) WLAN-AKM-Suite = 1027073
(1) Framed-MTU = 1400
(1) EAP-Message = 0xxxxxx...
(1) State = 0xfe5ef851fec1f531117b750213ef0752
(1) Message-Authenticator = 0xdf7173c3453436c0a6827cedf4c2427d
(1) session-state: No cached attributes
(1) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/default
(1) authorize {
(1) [preprocess] = ok
(1) [chap] = noop
(1) [mschap] = noop
(1) [digest] = noop
(1) suffix: Checking for suffix after "@"
(1) suffix: No '@' in User-Name = "host/xxxxxxxxxxxxxxx", skipping NULL due to config.
(1) [suffix] = noop
(1) ntdomain: Checking for prefix before ""
(1) ntdomain: No '' in User-Name = "host/xxxxxxxxxxxxxxxxxx", skipping NULL due to config.
(1) [ntdomain] = noop
(1) eap: Peer sent EAP Response (code 2) ID 159 length 166
(1) eap: No EAP Start, assuming it's an on-going EAP conversation
(1) [eap] = updated
(1) files: users: Matched entry host/xxxxxxxxxxxxxxxxxx at line 17
(1) [files] = ok
rlm_counter: Entering module authorize code
rlm_counter: Could not find Check item value pair
(1) [daily] = noop
rlm_counter: Entering module authorize code
rlm_counter: Could not find Check item value pair
(1) [weekly] = noop
rlm_counter: Entering module authorize code
rlm_counter: Could not find Check item value pair
(1) [monthly] = noop
rlm_counter: Entering module authorize code
rlm_counter: Could not find Check item value pair
(1) [forever] = noop
(1) if (&request:Calling-Station-Id == &control:Calling-Station-Id) {
(1) ERROR: Failed retrieving values required to evaluate condition
(1) [expiration] = noop
(1) [logintime] = noop
(1) pap: WARNING: Auth-Type already set. Not setting to PAP
(1) [pap] = noop
(1) } # authorize = updatedCase b)
Ready to process requests
(0) Received Access-Request Id 196 from 10.16.1.105:45863 to 10.16.1.1:1812 length 200
(0) User-Name = "host/XX"
(0) NAS-Identifier = "xxxxxxxxxxx"
(0) Called-Station-Id = "XX-XX-XX:XX_XXX"
(0) NAS-Port-Type = Wireless-802.11
(0) Service-Type = Framed-User
(0) Calling-Station-Id = "XX-XX-XX"
(0) Connect-Info = "CONNECT 0Mbps 802.11b"
(0) Acct-Session-Id = "XXXXXXXXXX"
(0) WLAN-Pairwise-Cipher = 1027076
(0) WLAN-Group-Cipher = 1027076
(0) WLAN-AKM-Suite = 1027073
(0) Framed-MTU = 1400
(0) EAP-Message = 0x02xxxxxxxxxxxxx
(0) Message-Authenticator = 0xdxxxxxxxxxxxxxxx
(0) # Executing section authorize from file /usr/local/etc/raddb/sites-enabled/default
(0) authorize {
(0) [preprocess] = ok
(0) [chap] = noop
(0) [mschap] = noop
(0) [digest] = noop
(0) suffix: Checking for suffix after "@"
(0) suffix: No '@' in User-Name = "host/XX", skipping NULL due to config.
(0) [suffix] = noop
(0) ntdomain: Checking for prefix before ""
(0) ntdomain: No '' in User-Name = "host/XX", skipping NULL due to config.
(0) [ntdomain] = noop
(0) eap: Peer sent EAP Response (code 2) ID 68 length 12
(0) eap: EAP-Identity reply, returning 'ok' so we can short-circuit the rest of authorize
(0) [eap] = ok
(0) } # authorize = ok
(0) Found Auth-Type = eap
(0) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(0) authenticate {
(0) eap: Peer sent packet with method EAP Identity (1)
(0) eap: Calling submodule eap_tls to process data
(0) eap_tls: Initiating new EAP-TLS session
(0) eap_tls: Setting verify mode to require certificate from client
(0) eap_tls: [eaptls start] = request
(0) eap: Sending EAP Request (code 1) ID 69 length 6
(0) eap: EAP session adding &reply:State = 0x6a7e65856a3b682d
(0) [eap] = handled
(0) } # authenticate = handled
(0) Using Post-Auth-Type Challenge
(0) # Executing group from file /usr/local/etc/raddb/sites-enabled/default
(0) Challenge { ... } # empty sub-section is ignored
(0) Sent Access-Challenge Id 196 from 10.16.1.1:1812 to 10.16.1.105:45863 length 0
(0) EAP-Message = 0x014500060d20
(0) Message-Authenticator = 0x00000000000000000000000000000000
(0) State = 0x6a7e65856a3b682d8e67b5cd26b0f8d7
(0) Finished request
Waking up in 4.9 seconds.
(0) Cleaning up request packet ID 196 with timestamp +171
Ready to process requestsCase c)
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!
!! EAP session with state 0x6a7e65856a3b682d8e67b5cd26b0f8d7 did not finish! !!
!! Please read http://wiki.freeradius.org/guide/Certificate_Compatibility !!
!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!!And yeah, I went to see the above mentioned freeradius wiki page and followed several chains of hyperlinks, but to no avail...
-
your going to want the key - yeah if your client will not allow you to import the p12 without a password... Just use opensl to do that..
https://docs.netgate.com/pfsense/en/latest/packages/using-eap-and-peap-with-freeradius.html
openssl pkcs12 -export -certfile ca.crt -in user.crt -inkey user.key -out user.p12
This is a requirement to get say iphone to import.. Pretty sure the wording on that doc, is mine from the old wiki ;) There are for sure some old threads around here where that was discussed putting password on .p12 since some clients will not allow import of it without password on it.