How to find spambot? Got network abuse report from my ISP
-
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
Is there something (Virus, Trojan or whatever) that could bypass the blocked mail ports?
Sending mails over something else?Sure !
That's like running a web server on port ....81 (for http) and, example, port 512 (https).
No one will be able to connect to it, except if the user knows about it, and uses on his side - the client - the special port override.Now for mails : Take a look at this setting :
System > Advanced > Notifications
I could set up any port here. Why not.
But .... when I want to send a notification mail to gmail, it has to be port 587 or 465 because gmail hasn't set up any other ports for receiving mail.You could be running your own mail server for your own domains( I actually do that) and thus mails leaving my local network could use any port, if I set up my mail server to use these ports to receive mails, so it can relay them afterwards. My mail server would have to use the standard ports 25 (clear text mail) or 465 (smtps mail) to hand it over to the destination MX.
No exception possible. -
@marvosa said in How to find spambot? Got network abuse report from my ISP:
Some other things to look at:- Start sending netflow data to a collector. The data would be captured either at the switch, which would be ideal if you have capable gear or on PFsense via the softflowd package. The idea being you would have historical top talker/top connection data that can be cross-referenced with the timestamps in your ISP's abuse reports which will aid in tracking down the offending device.
- Do you have any full tunnel road warrior setups or site-to-site tunnels configured where the remote end is routing its traffic through your connection? If so, it's possible that the offending device may not even be on your network.
- You could install Untangle in bridge mode behind PFsense and leverage the SPAM filter app
That all sounds really complicated. This is a home network and not the FBI headquarters :-)
I have a Netgear WNDR4300 with DD-WRT as AP and a ZyXEL GS1900-24E switch.I wonder what the Nvidia Shield is doing there all the time what gets blocked.
And how can i found out that other device that only shows a IPv6 (the one with 5353 UDP)?I did google if other people get mails from my ISP but there mails are about Open-DNS Resolver and open mDNS Service.
Most people get mails because of Amazon Fire TV/Fire HD or PlayStation 4 and port 5353. -
@MrGlasspoole said in How to find spambot? Got network abuse report from my ISP:
port 5353.
has zero to do with email - its mdns... No you shouldn't have those ports open to the internet.
-
@johnpoz said in How to find spambot? Got network abuse report from my ISP:
port 5353.
has zero to do with email - its mdns... No you shouldn't have those ports open to the internet.
I know it has nothing to do with email. I just wonder that my ISP is sending abuse mails to a lot of people about it and most of the time the PS4 was the problem.
I did install PRTG Network Monitor. Now i need to find out how that works.
Looks like flying a Boeing 747.I need to monitor the WAN port? I do that with softflowd?
-
Ok there are 18 new events on that abuse site this morning 2:52am (Dec 14).
pfSense is running on a standalone machine (no HyperV) and all the mail ports are blocked.I have now PRTG running but I'm not sure with some settings.
Should i leave the "Source Address" default or should i set it to LAN since I'm only looking for mails going out?
For "Syslog Contents" i only selected "Firewall Events".
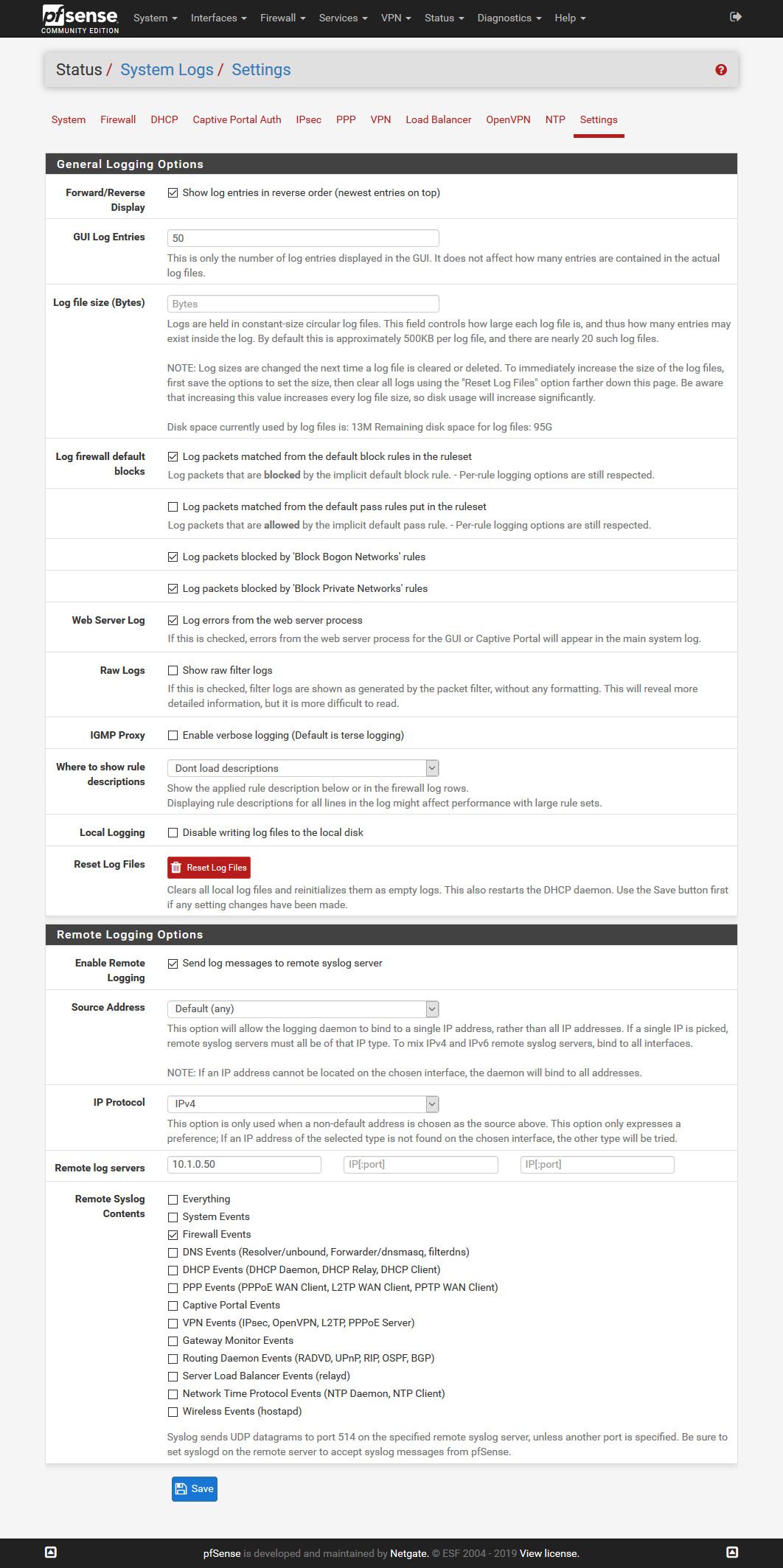
I did set the "Include Filter" in PRTG to "message[igb1]" because I'm only looking for what is blocked on the LAN interface.
This is what i have then:
I cant figure out how to filter that by port or how to make it more readable.
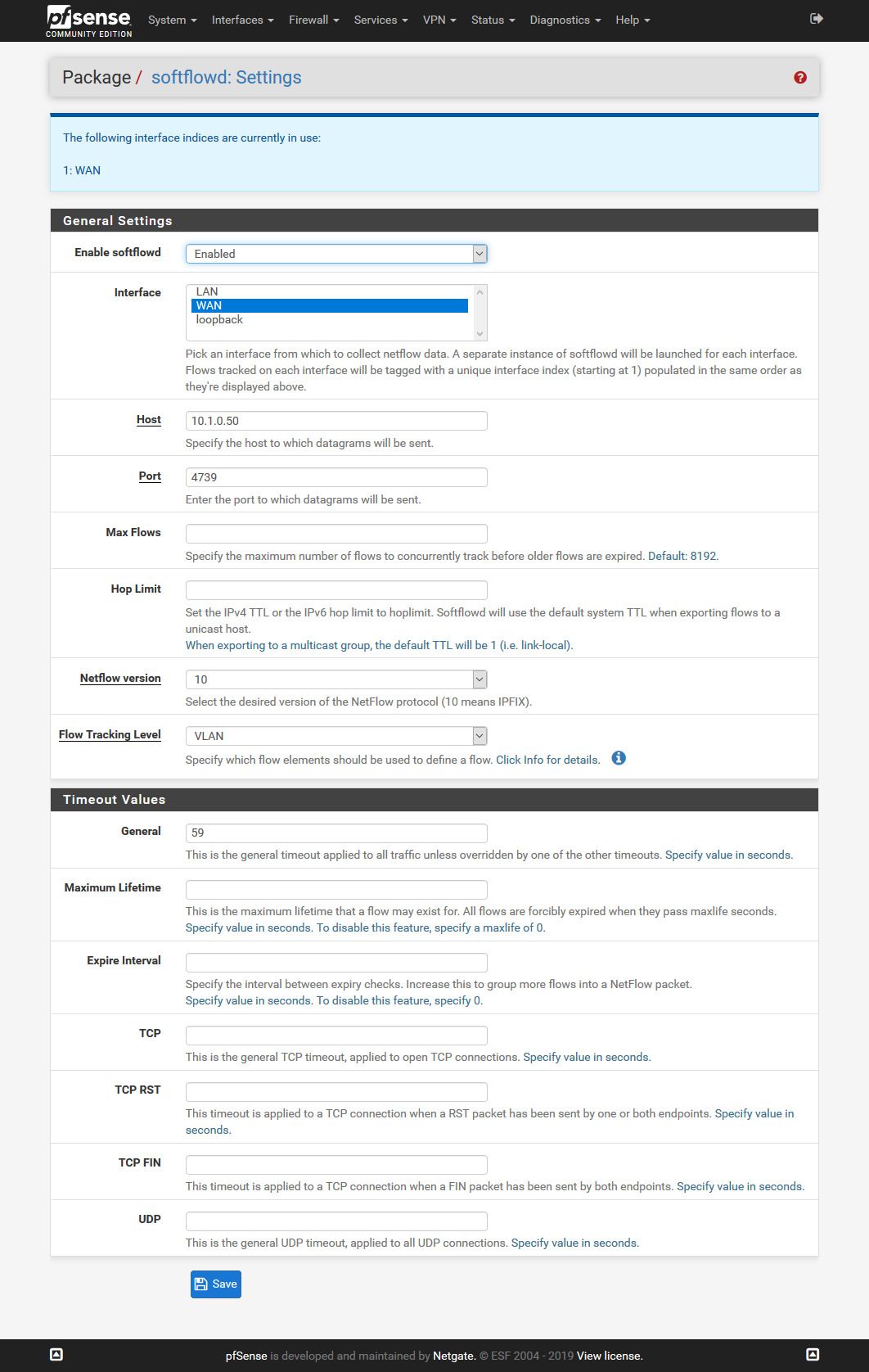
This two messages is PRTG trying to send some mails.Now that NetFlow thing. I have no idea what values to use on Max Flows, Hop Limit and on all this timeout settings.
Is it enough to select "IP" in "Flow Tracking Level"?
This this from PRTG but is over my head:
Make sure that you set an Active Flow Timeout in the sensor settings that is one minute greater than the flow timeout value that you set in the target device.
For more information, see https://kb.paessler.com/en/topic/66485.I did set the filter to Port[25] or Port[465] or Port[587] or Port[2525] or Port[2526]
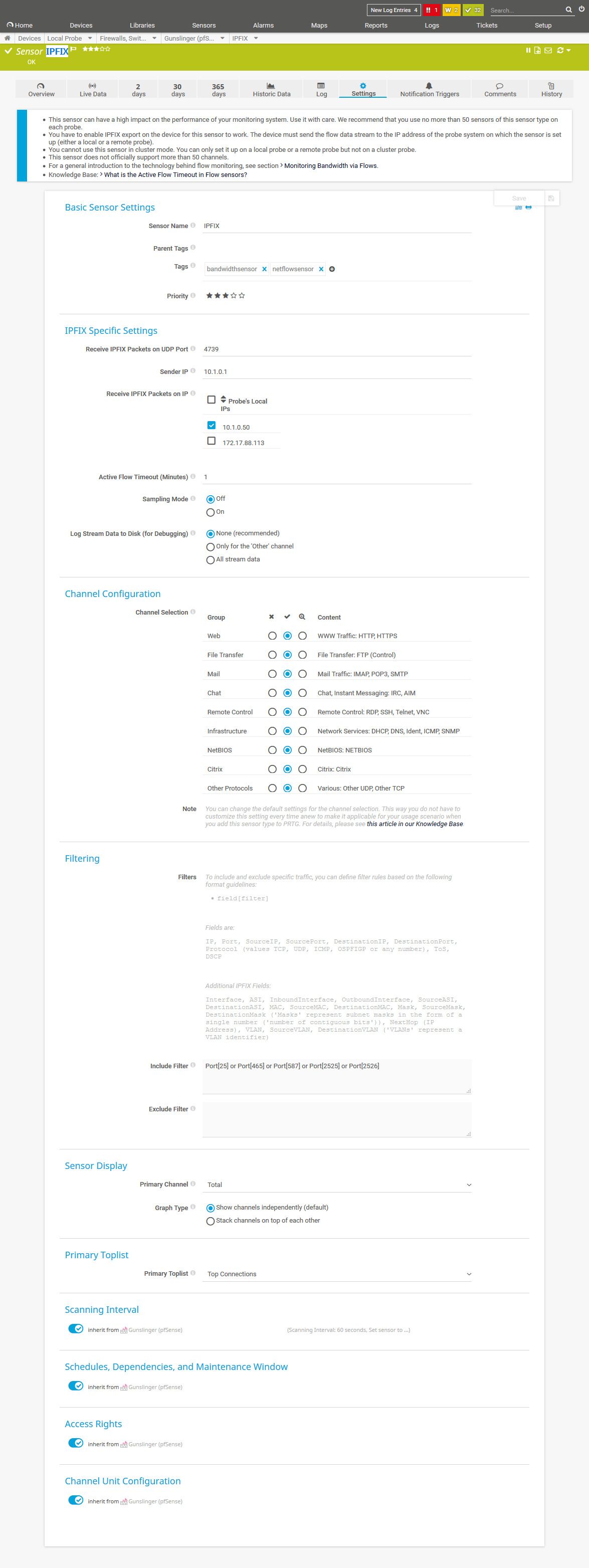
Here i did retrieve and send a mail with Thunderbird. Is it normal that i don't see the IP from my workstation?
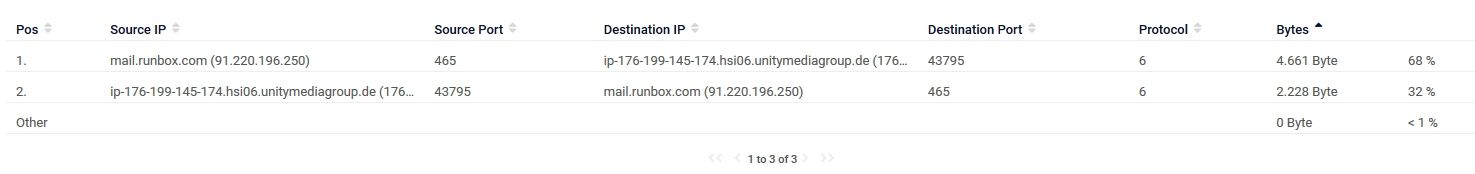
This is some other stuff i see. Stuff i don't know what it is:
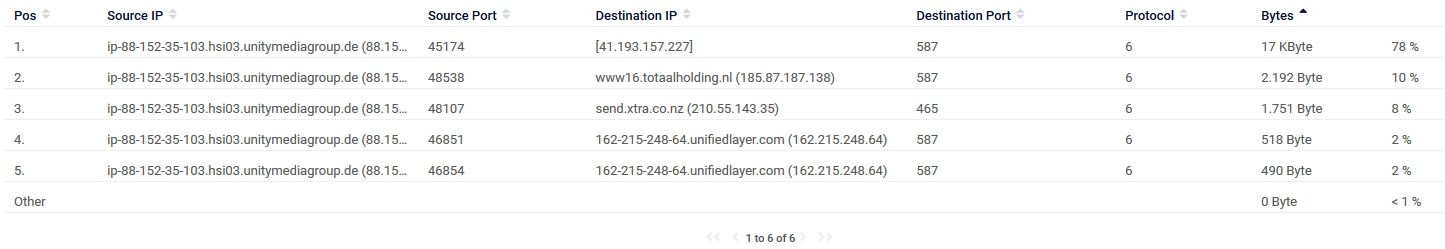
-
After my last posting i see this:
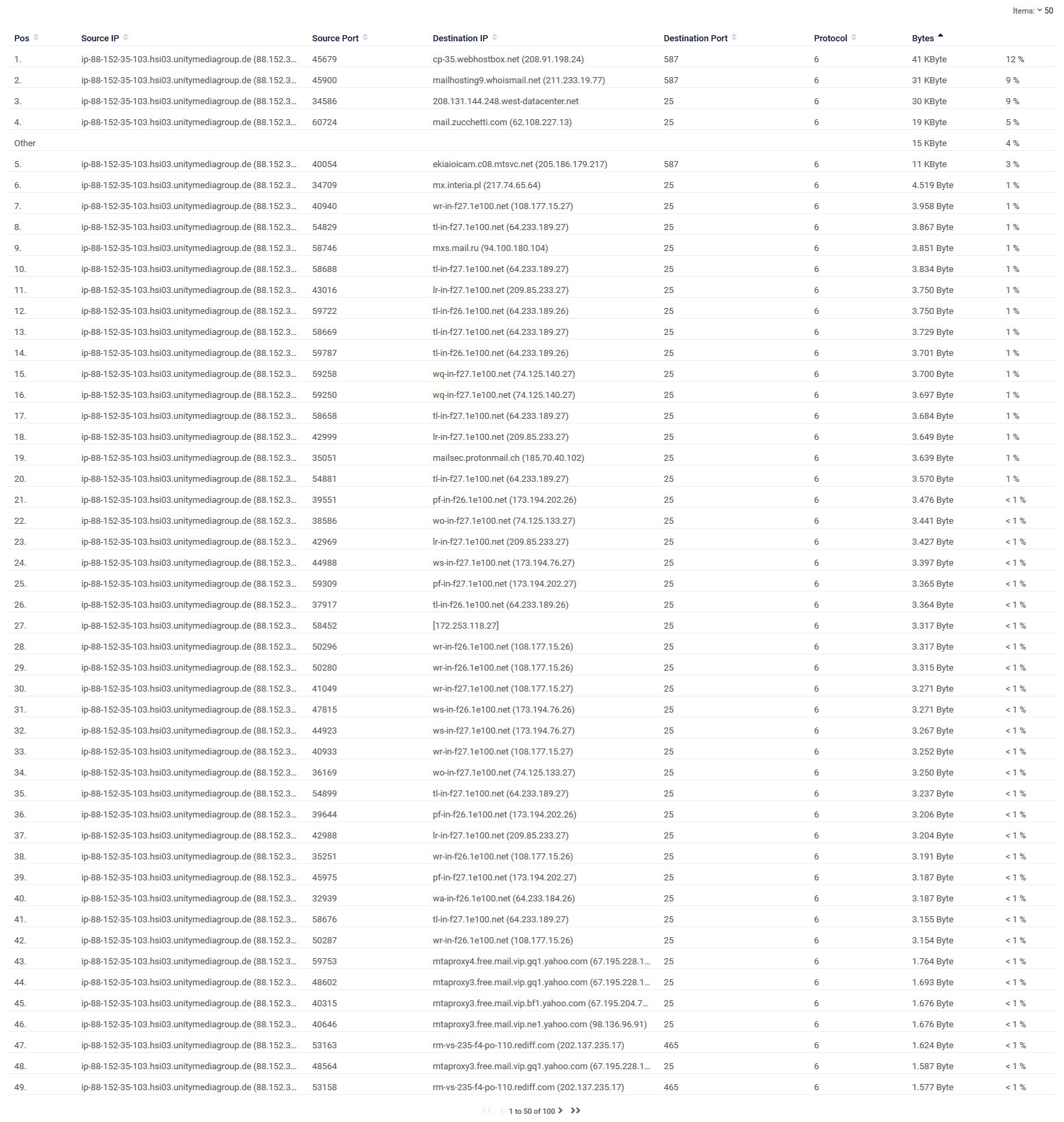
And ~50 new entries on the abuse website.

-
Have you considered that you might be relaying spam from an external source, rather than originating the spam on your own network - running an open relay?
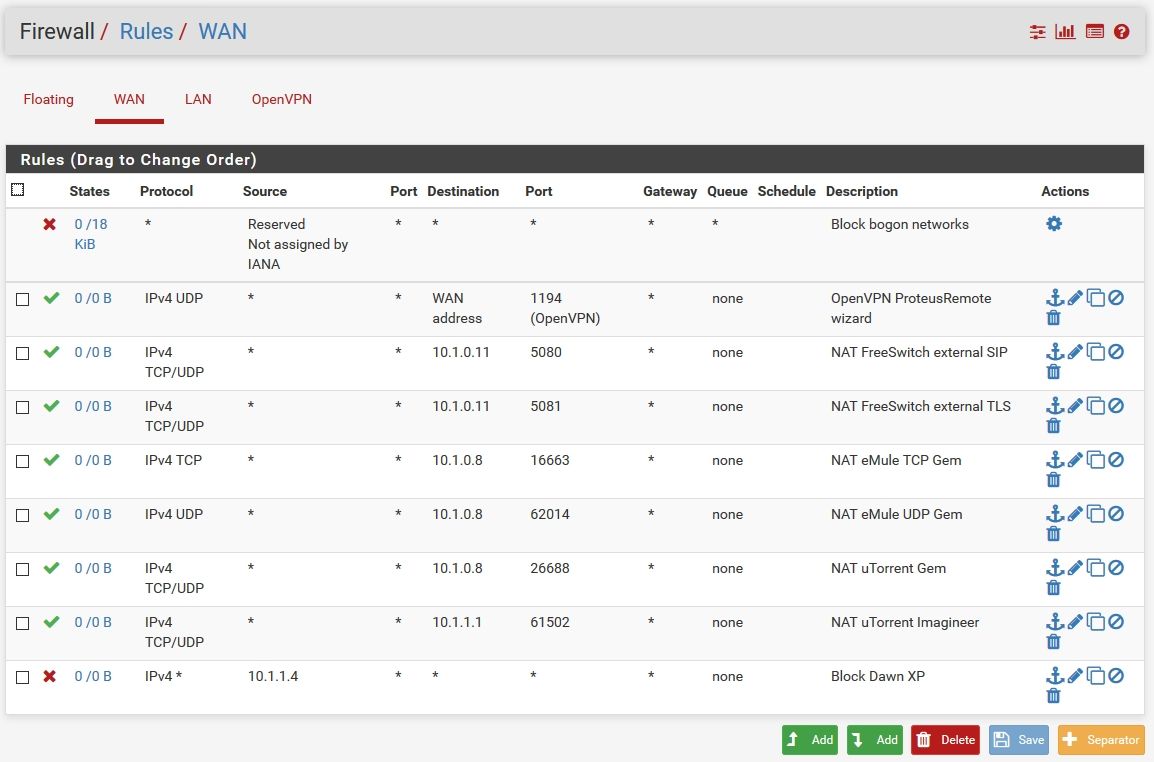
Show us a screenshot of your WAN rules.
-
-
There is a whole bunch of traffic to 25 in that listing... But its showing your wan IP..
-
@MrGlasspoole :
What type of network is this: a home network or a business?If home, then NAT is going to mask the local host that is spamming when looking at traffic on the WAN interface. To see that IP, you need to put your tools on the LAN interface and then examine all devices you see initiating connections to an Internet host on ports 25, 465 and 587. A spambot will need to make outbound connections to other mail servers using one of those three ports. The source port is immaterial as it will be an ephemeral port. What matters is the destination port (one of the big 3 mail server ports). Once you find that traffic entering the LAN interface, examine the source IP addresses to find the infection.
If you have a business network with multiple subnets hanging off the firewall, you will follow the same process but just do it for each configured interface.
You could have an infected PC or even an infected IoT device (Smart TV, Smart Home Hub, etc.).
-
@johnpoz said in How to find spambot? Got network abuse report from my ISP:
There is a whole bunch of traffic to 25 in that listing... But its showing your wan IP..
I did set softflowd to the WAN because if i understand it right: If it would be something in my LAN i would see it in the System Log?
@bmeeks said in How to find spambot? Got network abuse report from my ISP:
@MrGlasspoole :
What type of network is this: a home network or a business?If home, then NAT is going to mask the local host that is spamming when looking at traffic on the WAN interface. To see that IP, you need to put your tools on the LAN interface and then examine all devices you see initiating connections to an Internet host on ports 25, 465 and 587.
You could have an infected PC or even an infected IoT device (Smart TV, Smart Home Hub, etc.).Its a home network and as you can see in this threat the mail ports are blocked on the LAN interface and nothing raises an alert in the log.
-
But how you suppose to figure out what is sending it? You need to see both!
Also what are you rules on your floating?
Do you have more than 1 IP? Looks like your public IP is different or you have more than 1, see traffic to x.x.36.95, and then your also showing traffic to 25 from x.x.35.103..
-
There is nothing in floating.
pfSense is showing me a 176.xxx.xxx.xxx address on WAN.
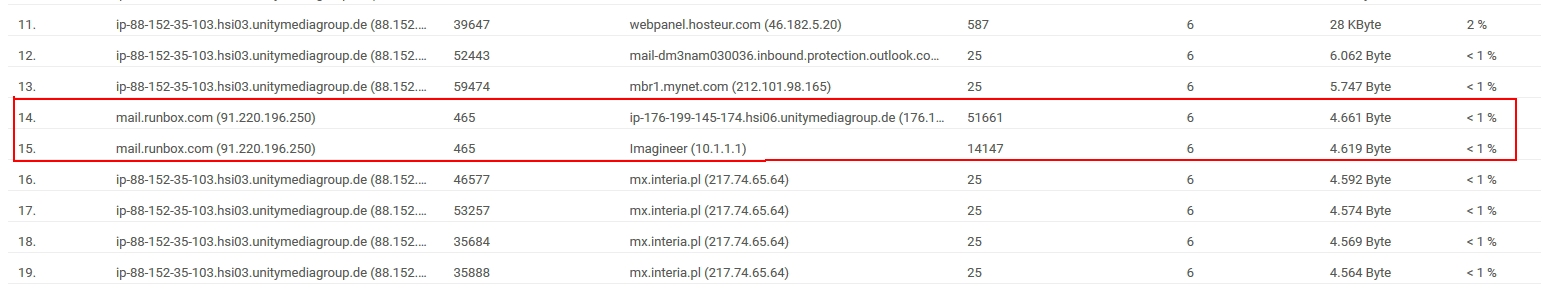
On that abuse site the last reports are 88.xxx.xxx.xxx.I enabled softflowd now also on the LAN.
Is it normal that there is no time on every single entry in that IPFIX thing?For testing i did open the port on LAN and did send a mail and it shows up and has the 176.... address:
-
So what is using that 88.x.x.x IP? Seems like it must be on the firewall...
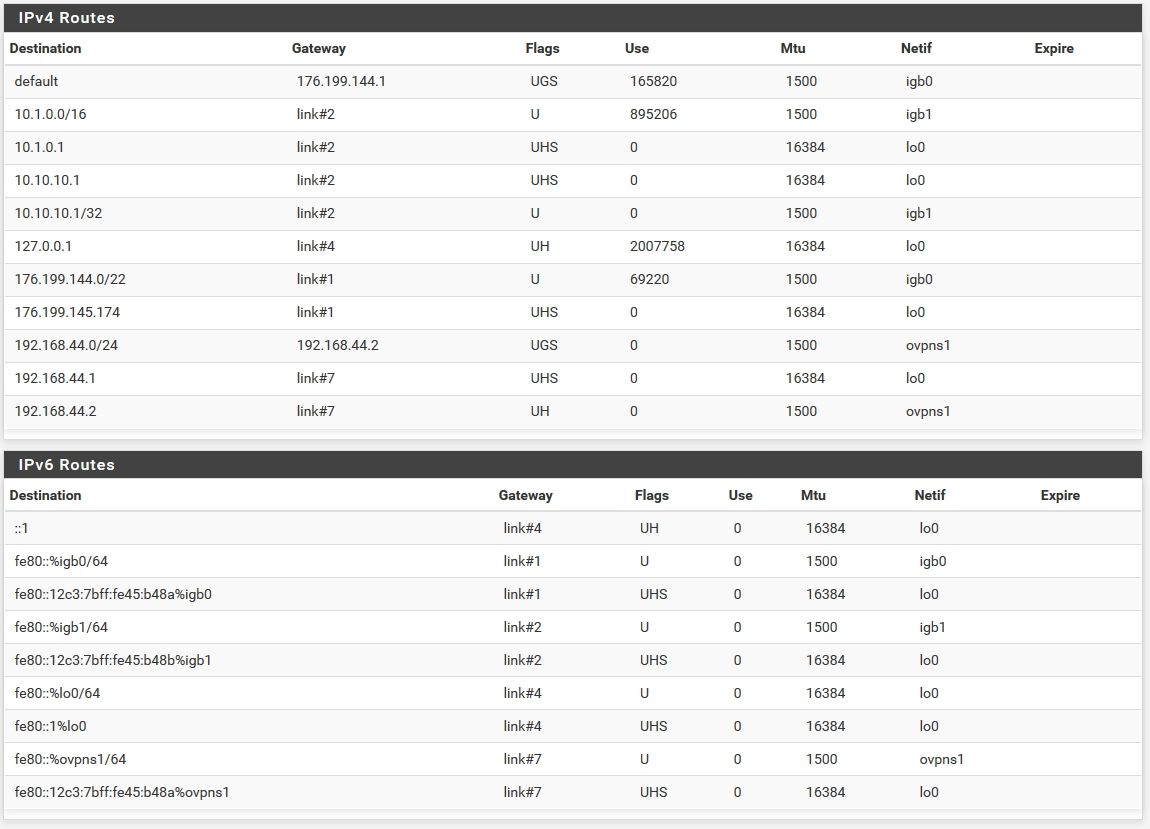
Check the pfSense routing table in Diag > Routes, do both IPs appear there?
Is the WAN configured as DHCP? Could it just be pulling a new IP from the ISP there?
Steve
-
Sure WAN is DHCP since the ISP router is in bridge mode.
This is what routes is showing:
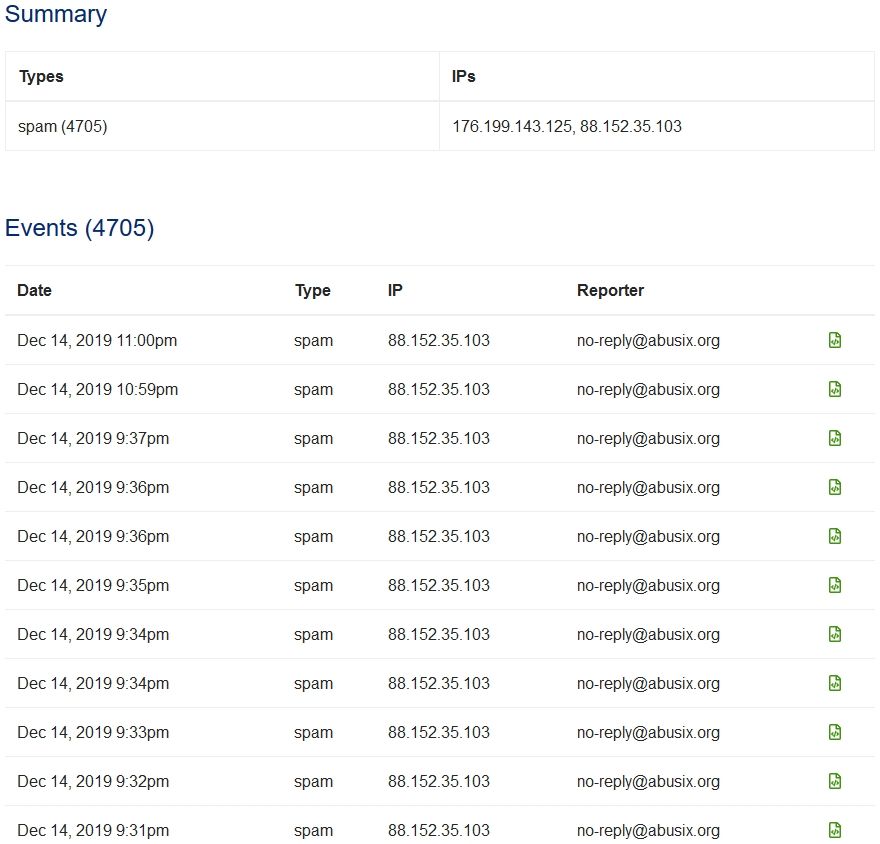
The last abuse entries. Always new entries:
-
Well that aint your IP...
Neither of them are.. atleast not with pfsense - do you have other devices connected to this isp?
-
Only the pfSense WAN is connected to the ISP router/modem.
And that network abuse report has my customer ID.
That 176.199.143.125 in that report is the old IP.
Now its 176.xxx.xxx.174 that i see on the WAN in pfSense.
Most of the time when you restart the modem you get a new one.Its driving me crazy

-
And how are you sure its not reports from some other guy that had that IP before you got it? ;)
That is part of the problem of changing IPs all the time - you can be held responsible for the sins of the guy that had it before you..
But you did show a bunch of traffic to 25...
-
But i can see that 88.xxx.xxx.103 that is on top on that report also in softflowd?
@johnpoz said in How to find spambot? Got network abuse report from my ISP:
But you did show a bunch of traffic to 25...
And that is what I (we) trying to figure out? Where does it come from?
It does not come from the LAN because the ports are blocked...
Only pfSense is connected to the modem...I don't get it

That IPFIX log is full of mail port entries.
100 every 15 minutes...
Are this entries blocked stuff from outside? -
Look in your state table... What doe you see for those connections to 25.