Clear method for sending specific VLAN traffic through VPN
-
I've read through a bunch of posts and tried several things and can't seem to get this right. What I would like to do is take an entire VLAN and route all traffic through a VPN.
I've managed to get a VPN configured and successfully running. However I run into two issues. I'm testing with two networks (default LAN and VLAN4). When I enable the VPN, and configure a firewall rule to send all traffic from VLAN4 through the VPN gateway, VLAN4 works, however my other networks lose internet connectivity.
In one guide, I saw the suggestion tto add "-route-nopull" to the Advanced Config of the VPN in order to prevent the VPN from adding to the routing table. When I do this, I regain connectivity on my other networks, but lose connectivity on VLAN4 which I want connected the VPN. I've managed to test and get a single host running on VPN, not sure why I can't get a whole VLAN to. Here are my relevant settings
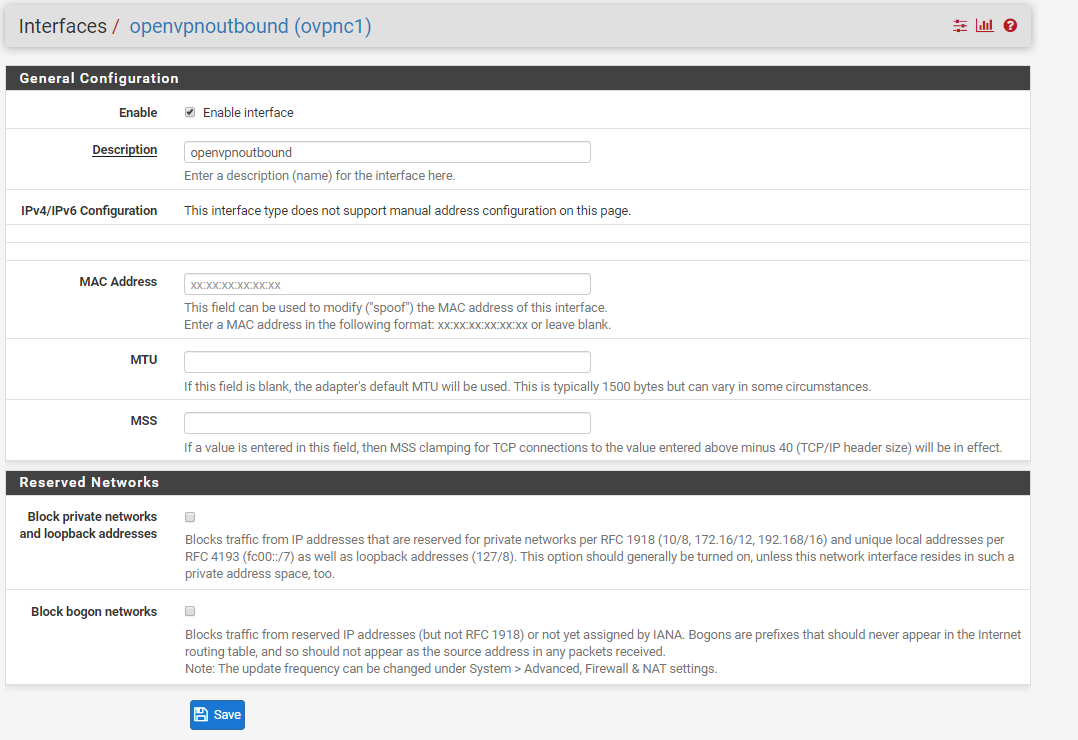
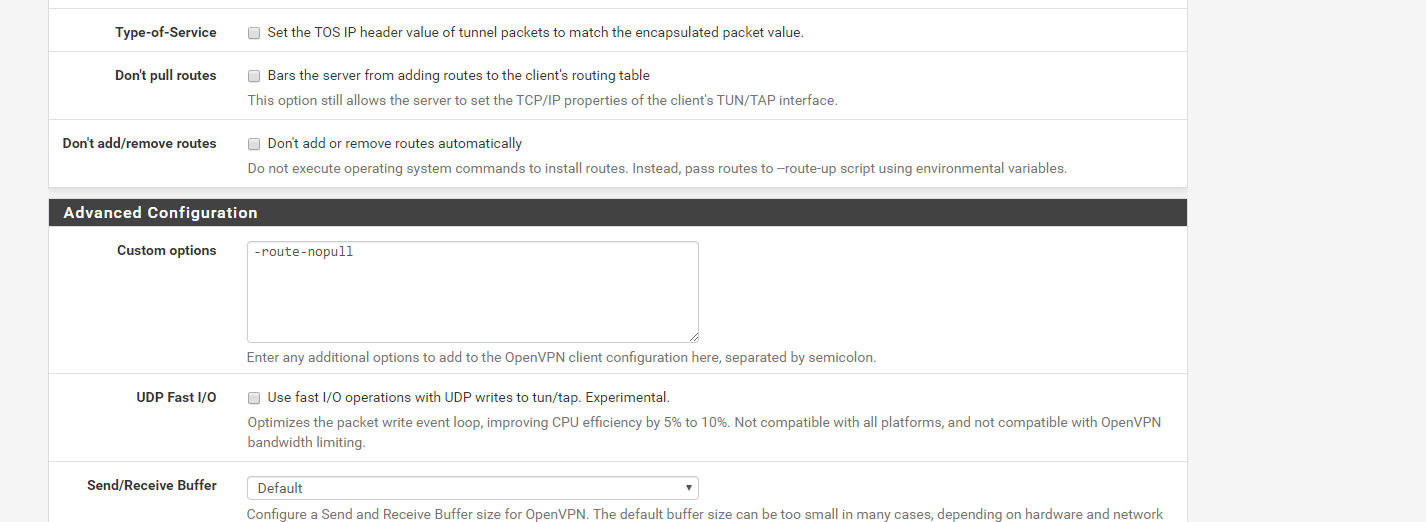
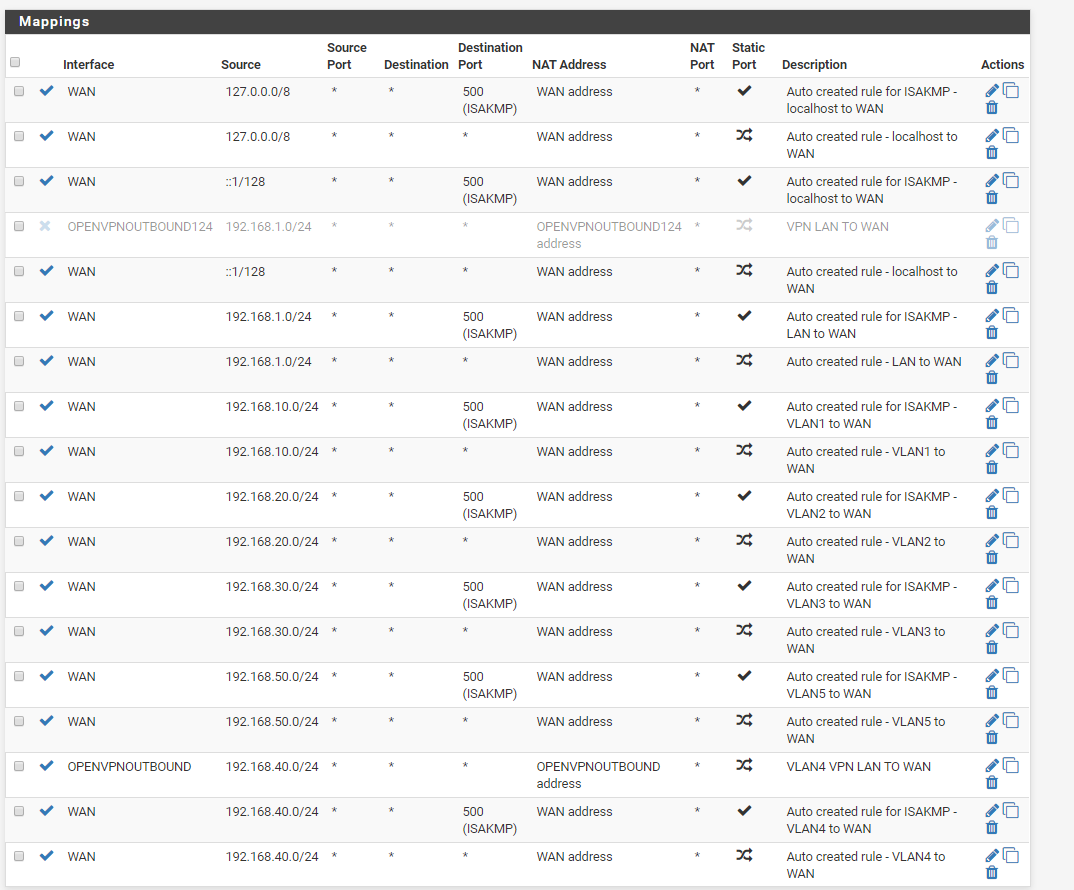
NAT outbound rules:
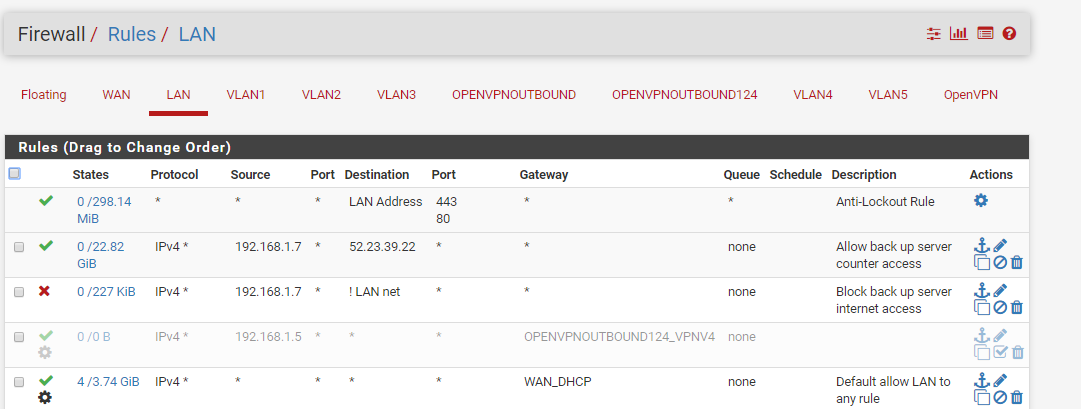
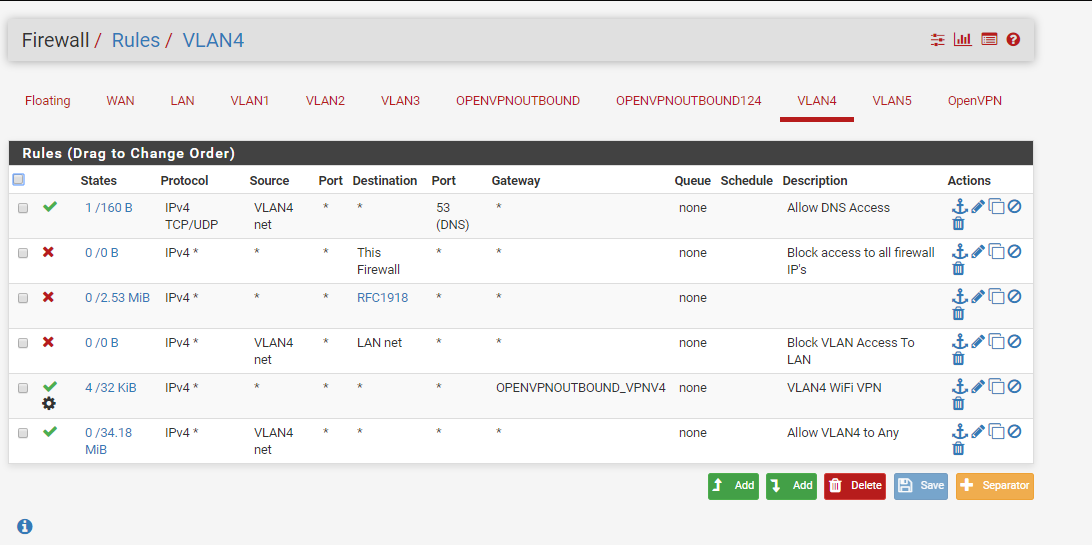
I did attempt re-ordering VLAN4 firewall rules but that didn't help.
I'd appreciate any insight / help. In an attempt to understand better and at the risk of exposing my ignorance:
Since VLAN4 is a separate interface, it shouldn't matter what my LAN rules are, correct? And since I set the advanced config option in the OPENVPNOUTBOUND interface, it should not add routing tables, which would mean that by default no traffic uses the VPN, correct? So if that's the case, then I need something to tell VLAN4 to use the VPN. Adding a firewall rule to "allow" traffic to use that gateway, is that the same as telling traffic to use that gateway, or simply saying that it can? I think this may be my issue, but I'm not sure.
-
@sef1414 said in Clear method for sending specific VLAN traffic through VPN:
Since VLAN4 is a separate interface, it shouldn't matter what my LAN rules are, correct?
Correct. Just think of everything as separate networks, be it LAN, WAN or VLAN. Once you drop the labels, it's just routing and rules according to what you want to do. Do you have a route specified for the VLAN to the Internet?
-
Ok, so to follow up on that:
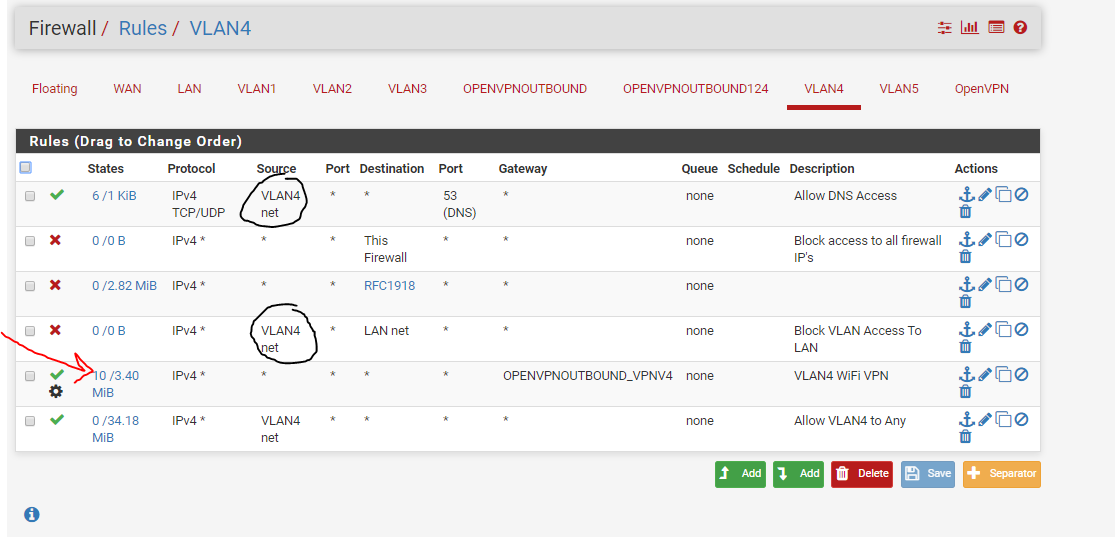
The source there is redundant and unnecessary?
And for the original question, the rule with the red arrow... shouldn't that tell VLAN4 traffic to route out the VPN gateway? What happens when I enable the VPN with without pulling the route is VLAN4 loses internet connectivity.
-
There are a few things I would do:
-
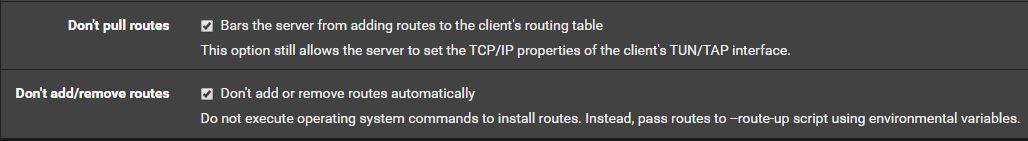
In your client config, remove "-route-nopull" from the advanced config section and click the "Don't pull routes" checkbox just above it (the command is actually "route-nopull" without a leading dash). My working config also has "Don't add/remove routes" checked, however, the instructions for your provider may differ. I use AIRVPN.
-
Based on what we can see, it looks like 192.168.40.0/24 is the subnet assigned to VLAN4, correct?. I would clean up the outbound NAT rules by switching to Hybrid Outbound NAT:
a) If the NAT for 192.168.40.0/24 to OPENVPNOUTBOUND address on the OPENVPNOUTBOUND interface does not get moved after switching, re-add it.
b) Add a similar NAT for 127.0.0.0/8 to OPENVPNOUTBOUND address on the OPENVPNOUTBOUND interface
c) I also just noticed that you have two different VPN interfaces, so I would re-verify that you are NATing to the correct address on the correct interface and make adjustments as necessary. -
On the LAN tab, on the last rule, change the source to LAN net and the gateway to default
-
On the VLAN4 tab, what DNS servers are you providing to your users?:
a) If internal, I would specify the destination on your DNS rule and then collapse the rest of your ruleset down to:
Block -> TCP/VLAN4 net/This Firewall/port (alias for 22 and whatever port your GUI is listening on)
Allow -> VLAN4 net/Invert match (alias for rfc1918)/OPENVPNOUTBOUND_VPNV4 (verify this is the correct gateway)
b) If they are forced to use VPN provided or public DNS, then I would remove the DNS rule altogether and collapse the entire ruleset down to:
Block -> TCP/VLAN4 net/This Firewall/port (alias for 22 and whatever port your GUI is listening on)
Allow -> VLAN4 net/Invert match (alias for rfc1918)/OPENVPNOUTBOUND_VPNV4 (verify this is the correct gateway) -
On the OpenVPN tab, make sure any rules that exist are explicit... i.e. there should NOT be an any/any rule on there or traffic will have a tendency to get matched on the wrong interface.
-
-
Thank you for the detailed response. So, I actually realized the VPN connection was down, and after removing the "-route-nopull" , it was connected again. There must have been a delay when I initially tested. Honestly I did a terrible job keeping track of everything I did. My firewall rules still look the same, although per your recommendations I can clean them up a bit. I believe the issue is that I did not have local DNS servers set in DHCP and there was no rule to allow connection to them, although I'm still not sure. I removed them, and left at default, and I believe that is when it started connecting.