OpenVPN individual firewall rules for different users: Best practise?
-
Hello experts,
we currently use an Endian firewall appliance for OpenPVN access of different users (Roadwarrior configuration).
Many of these users need to have different permissions to access different areas of company-internal networks and hosts.
We use username + passwords (no certificates) for user authentication in OpenVPN.ENDIAN firewall allows to use OpenVPN user ID directly in a firewall rule to allow definition of different firewall rules for different OpenVPN users (This works also with dynamic IP addresses of OpenVPN users).
For pfsense it seems that one has to use fixed IP addresses for OpenVPN users (using a RADIUS server or TLS/SSL certificates) to accomplish this target.
So please allow me following questions:
- Are there other ways to be able to set different firewall rules on OpenVPN user base? What is currently possible? What is recommended?
- Is it planned for future to be able to use users as part of firewall rules (kind of "identity aware firewall")?
Many thanks for your experience,
Roman
-
AFAIK there is no other way then using a Cert for each user together with OpenVPN CSO.
Working great here...what is your problem with using Certs? It is the most secure and recommended way.
What is your actual workflow when a device gets compromised, lost or stolen? A nightmare without Certs when you have a lot of Users.-Rico
-
- See @Rico reply, recommended.
- Probably Endian has this automated... ?
One can also create groups of users.
Each group it's own OpenVPN server instance.
Each OpenVPN server instance has it's own tunnel subnet.
Each OpenVPN tunnel subnet can have firewall rules. -
Thank you Rico and Pippin.
There's not really a problem with certificates, my concerns are more related to having many different firewall configurations and having to set up a different VPN server for each of these configurations.
Any how, many thanks for your feedback!
Roman
-
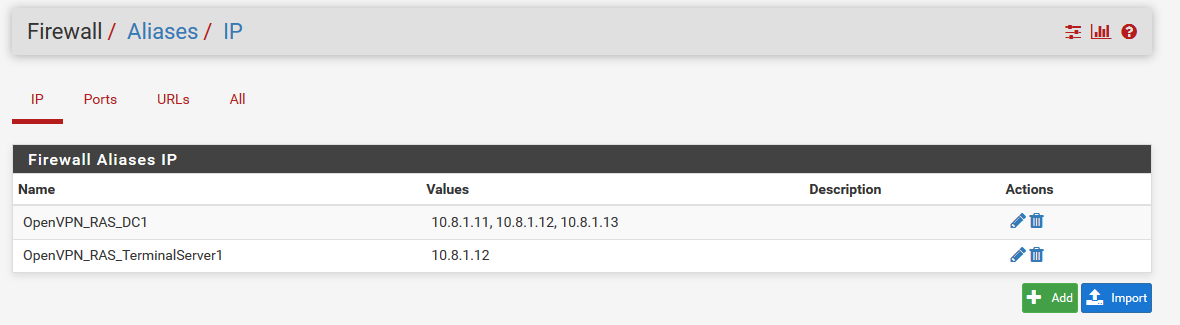
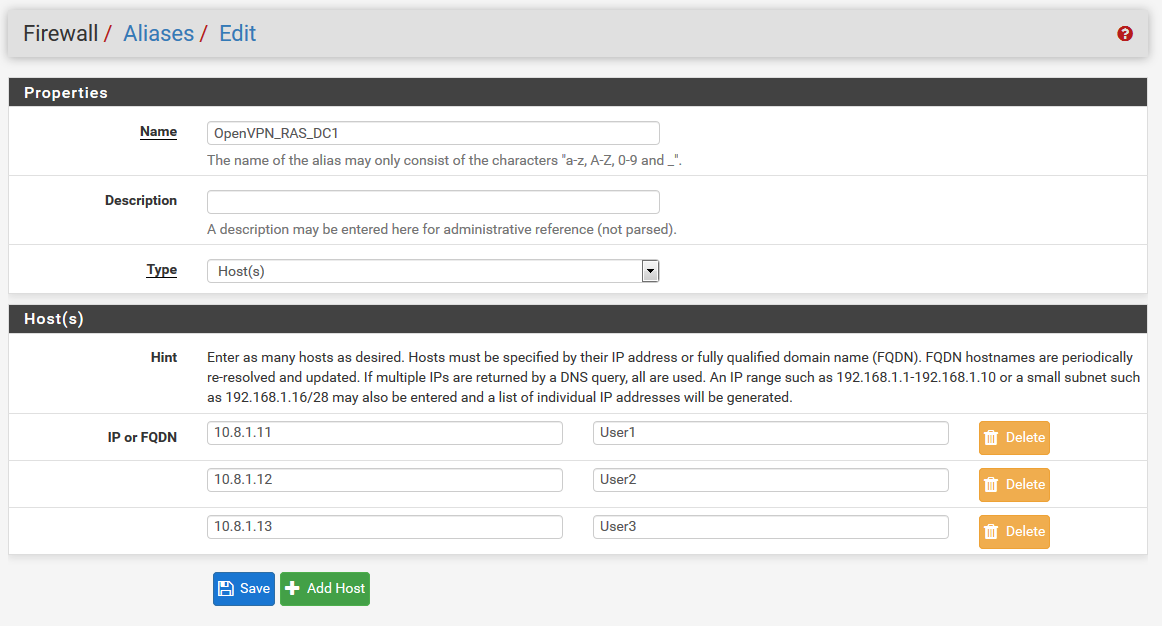
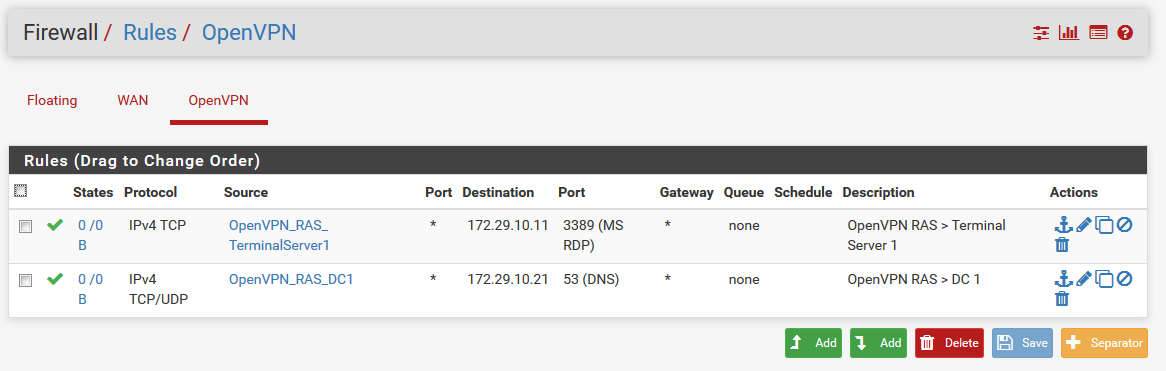
You can just create one Alias per target server and add the allowed OpenVPN User IP there.
Then create one Firewall Rule per Alias in the OpenVPN tab. This can be done with only one OpenVPN RAS.In this example User1, User2 and User3 can access DNS on Server DC1, only User2 can RDP connect the Terminal Server.
-Rico