Spent 3 days trying to implement simple VLAN, help please, picture and details inside.
-
Things I have tried:
Fresh install of pfsense 2.4.3
Different nics in pfsense machine, including trying the onboard nic in pfsense for the vlan
Several different network cables.
A completely different machine with a fresh install of pfsense 2.4.3 and 2.4.4
Tried 4 different machines hooked to the VLAN interface, none of them will receive an IP, and none of them can ping 192.168.20.1The four port network card is an HP NC365T, I ordered 4, 2 for me and 2 for a friend, his VLANs are working with the SAME card. I am at a complete loss, I have compared my setting to his, he has looked at it a bit as well and everything seems fine except for the fact that nothing is working.
My setup:
Modem -> pfsense-WAN(igb0) -> pfsense-LAN(igb1) -> 24-Port Gigabit Unmanaged switch -> all the PCs on my network, except one.
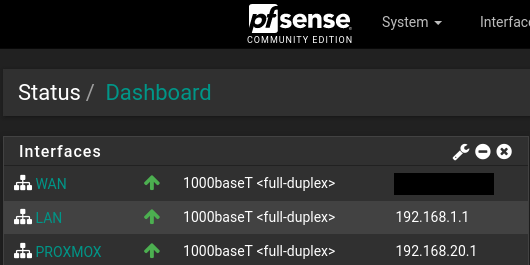
Modem -> pfsense-WAN(igb0) -> pfsense-VLAN(igb2) -> Proxmox(supermicro server) -> 10 or so VMsMy lan is 192.168.1.1/24
My Vlan is 192.168.20.1/24any machine on my LAN received an IP via DHCP and can successfully ping 192.168.20.1
any machine that I have hooked to igb2 does not receive an IP from the DHCP vlan, and CANNOT ping 192.168.20.1
I have also configured a machine with a static ip of 192.168.20.100 and it also CANNOT ping 192.168.20.1VLAN procedure:
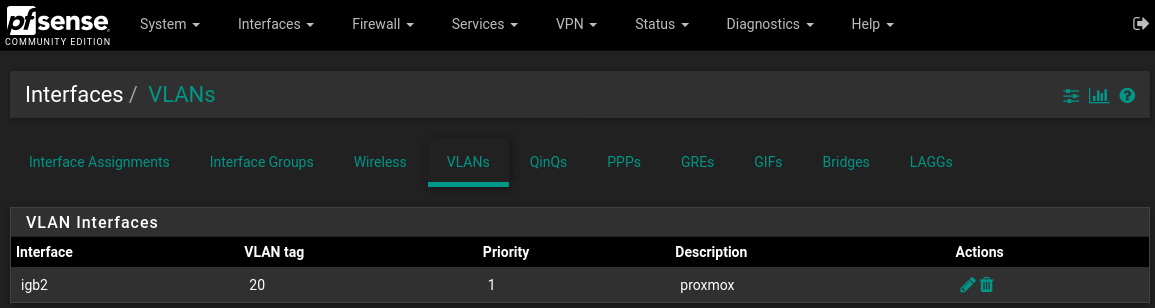
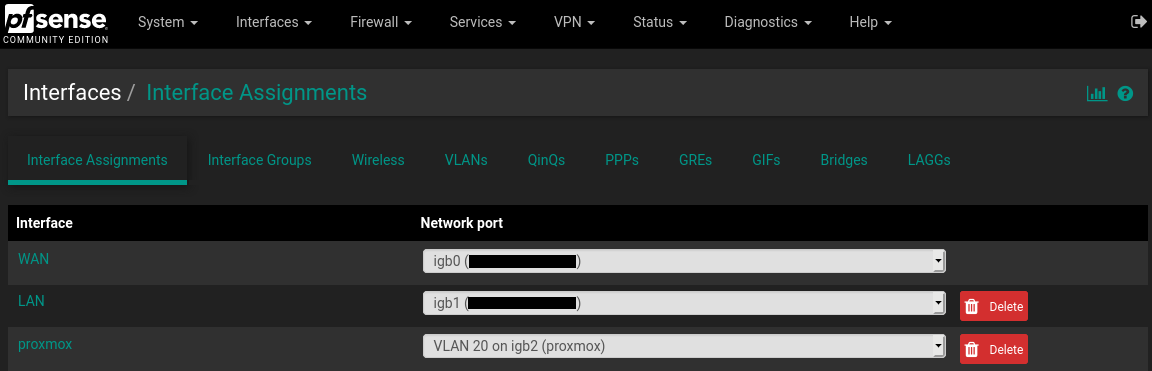
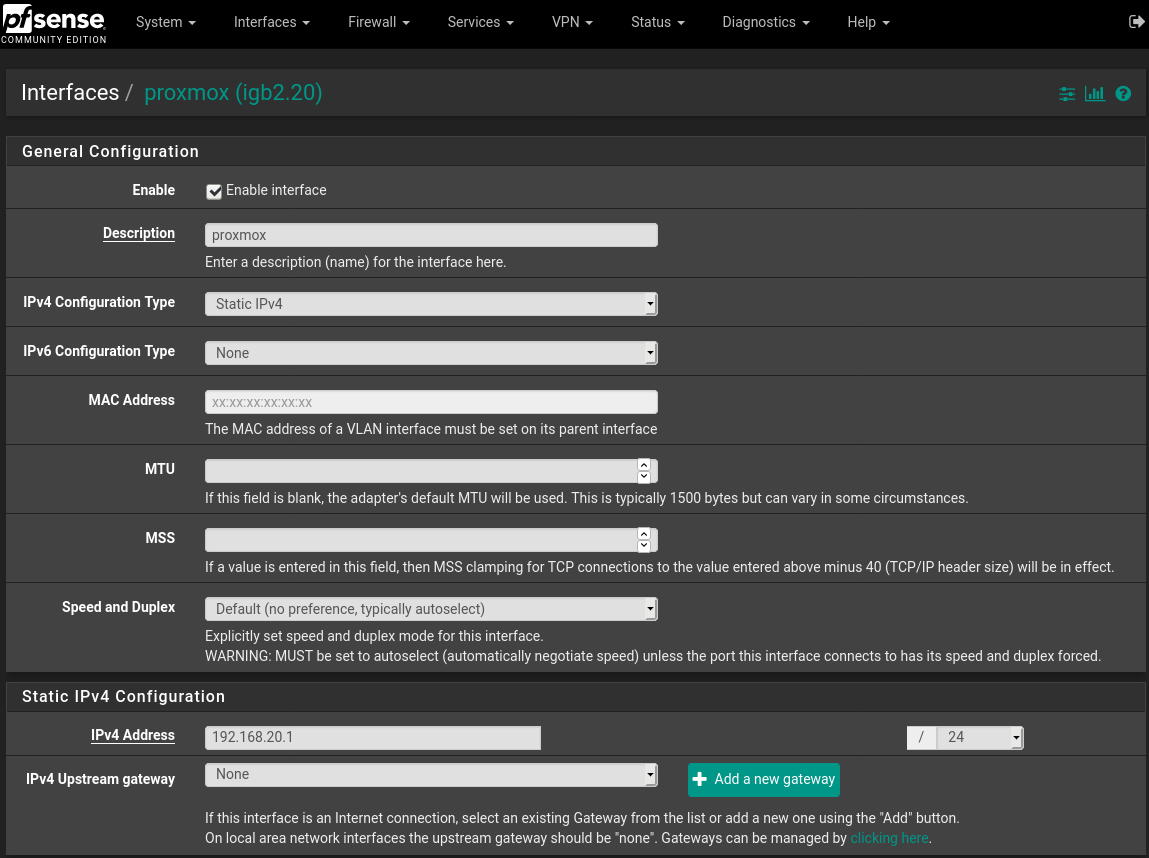
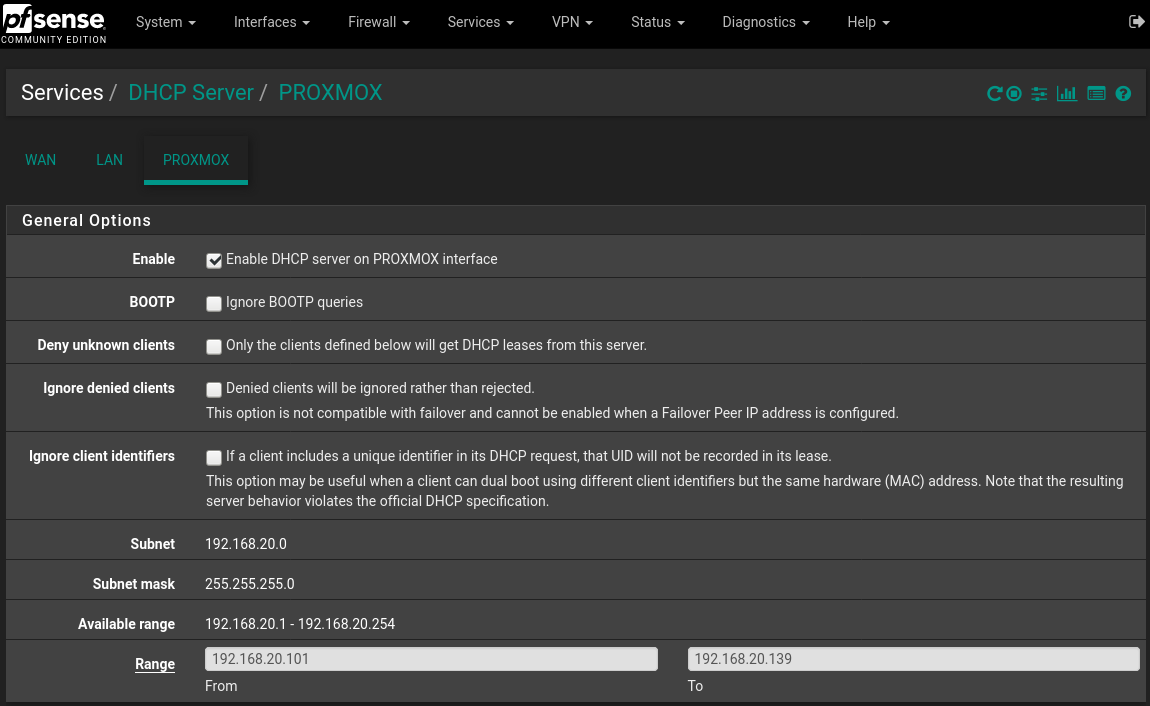
Interfaces->Assignments->"VLANs" tab, click add Parent Interface: igb2 VLAN Tag: 20 VLAN Priority: 1 Description: Proxmox click save Interfaces->Assignments->"Interface Assignments" tab Assign the new VLAN that was just created. Available network ports: VLAN 20 on igb2 (proxmox) select it from the dropdown menu, click Add button click save Enable the interface by clicking into it or accessing from the Interfaces menu check the "Enable interface" box IPv4 Configuration Type: Static IPv4 IPv4 Address: 192.168.20.1 /24 Enable DHCP for that interface Services->DHCP Server->Tab of New VLAN (proxmox) Check the enable box to enable DHCP set the range such as: 192.168.20.101 - 192.168.20.139 click save/apply Firewall->Rules->Tab of New interface (proxmox) Add new rule: Action:Pass, Protocol:Any, Source/Destination:any click save/applyPictures:
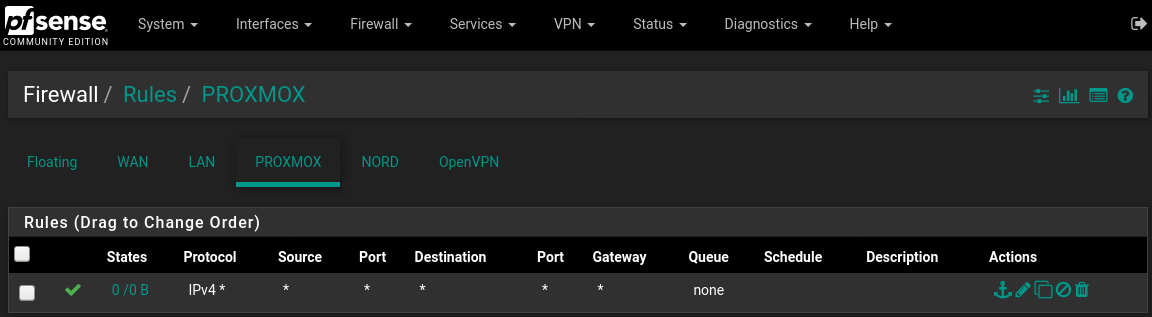
-
@xanaro said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
Tried 4 different machines hooked to the VLAN interface,
So you connected the machine direct to the interface igb2..
You understand you created a VLAN, so its tagged! Normally this would connect to a switch and port connected to pfsense would have the vlan 20 tagged.
Then you would connect your devices to switch ports where they are in vlan 20 Untagged.
If your going to connect a device directly to the port, you would have to set the device to understand the TAG..
If you want to connect this interface just to a machine, you don't need a vlan, you just create the network right on the interface... Like you for lan.
-
Yes I understand that, however I had planned to have that single machine(proxmox server) that is directly connected to the interface igb2 host like 10 or so virtual machines, so each virtual machine as I see fit could be on different VLANs.
Do you have any idea why my friends machine seems to understand the TAG but mine does not?
Also why does a machine that is configured with a static ip and connected to the VLAN interface not able to ping 192.168.20.1? however my desktop on the lan can ping 192.168.20.1 just fine.
-
@johnpoz said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
you would have to set the device to understand the TAG..
Thank you so much @johnpoz I modified my proxmox according to this: https://pve.proxmox.com/wiki/Network_Configuration#_vlan_802_1q
I now have it working. The confusing part is the traffic works on my friends without setting this. It makes me wonder if it is my network or his network that is acting irregularly.
I am kinda wondering if something in his setup is either dropping the tagging or not even applying it when it should be, either way I am happy to be up and running now.
-
I have no idea how your friend is setup... But this is how vlans work.. There is nothing odd going on with your setup..
So are you going to run virtual machines on this proxmox machine on different vlans?
You understand you can have native network just on the igb2 and then vlans on top of that... So talking to the host proxmox would be the native untagged network.. And then when you create your vswitches etc on the proxmox those could be different tagged vlans, etc.
-
@xanaro said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
Yes I understand that, however I had planned to have that single machine(proxmox server) that is directly connected to the interface igb2 host like 10 or so virtual machines, so each virtual machine as I see fit could be on different VLANs.
Do you have any idea why my friends machine seems to understand the TAG but mine does not?
Also why does a machine that is configured with a static ip and connected to the VLAN interface not able to ping 192.168.20.1? however my desktop on the lan can ping 192.168.20.1 just fine.
Have you actually configured the VLAN on that computer? To access a VLAN, you use either a managed switch or configure the NIC to use a VLAN.
-
@johnpoz said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
You understand you can have native network just on the igb2 and then vlans on top of that... So talking to the host proxmox would be the native untagged network.. And then when you create your vswitches etc on the proxmox those could be different tagged vlans, etc.
Yes @johnpoz I do understand that the proxmox could have used native network for igb2, however what I have read is that for a single interface it is better for ALL traffic to be TAGGED, otherwise Untagged traffic can spoof their tag and hop onto any VLAN that they want, so from a security standpoint its better to have all traffic for an interface that is supporting VLANs to all be TAGGED.
I think I read this from the pfsense book actually.
@JKnott I have now configured the VLAN on that computer. that was the page that I linked, it shows how to do that: https://pve.proxmox.com/wiki/Network_Configuration#_vlan_802_1q
-
@xanaro said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
however what I have read is that for a single interface it is better for ALL traffic to be TAGGED, otherwise Untagged traffic can spoof their tag and hop onto any VLAN that they want
No - not really... If connected to a port on a switch.. Then No matter what tag I put on the traffic it wouldn't be allowed.. Unless you misconfigured the port on the switch to allow vlans that you shouldn't have.
In your scenario directly connected to some device.. Once you run multiple vlans, then sure it could jump vlans by setting the tag to other vlans.. But it you used all tagged vlans or 1 native (untagged) and others tagged doesn't matter. Can still jump vlans on any port that handles more than 1 vlan be tagged or untagged.
In your setup with vlan (ie tagged) directly connected to a device... Then that device would have to be set to use the tag as well.. This is how it works... If your saying your friends is working differently - then your miss understanding how they have it setup. These are just the facts..
-
@johnpoz said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
If your saying your friends is working differently - then your miss understanding how they have it setup. These are just the facts..
Cool, thanks. I feel good knowing that mine is the one behaving properly. This means that my friends system is doing something odd. I have access to his pfsense and proxmox and I can assure you that he set his up the same way that I did initially, which for me is where a lot of the confusion came from.
My question is can something like wireshare check for the presence of a TAG? I am thinking it might be a good idea to check if my friends traffic is even getting properly TAGGED.
-
Yeah if you can sniff, you can see any tags that are being put on the wire sure..
-
@xanaro said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
My question is can something like wireshare check for the presence of a TAG?
Yep, you can even configure a column just to show VLAN ID.
-
Just curious -- are you using wireshark for the sniffing?
-
Doesn't matter where/what you sniff with - you can always just load it into wireshark..
I don't think the gui in pfsense allows for the tcpdump -e flag to see the tags... But you can just do it via tcpdump on pfsense and write the capture to a file.. Then load that file in wireshark, etc.
-
Perhaps a question for a different thread -- however is it true the xn driver used for the paravirtualization in FreeBSD does not support 802.1q tagging? Any reason for this?
-
That is prob better in its own thread - sounds unlikely to me.. I have never ran across a driver that can not do tags..
-
Thanks I'll open a different thread
-
But that is really not a hardware driver - specific vm driver.. So you never know what they might not include, etc.
-
@kevdog said in Spent 3 days trying to implement simple VLAN, help please, picture and details inside.:
Just curious -- are you using wireshark for the sniffing?
Yes, I use Wireshark frequently.
-
Interesting discussion here - I know at one point a couple years ago I also read (or heard somewhere) that one shouldn't mix tagged an untagged (native) traffic on the same interface. I realize that it can be done, but I am trying to figure out why it might be a bad idea. So far all I could find was this old article from 2009:
https://www.networkworld.com/article/2234512/cisco-subnet-tagging-the-native-vlan.html
What do you guys think - is this a problem to be concerned about? Thanks in advance for your insight, I really appreciate it.
-
I read the article you referenced however I'm not sure its exactly relative to your questions. When you're saying interface -- are you talking about switch ports? Usually trunk ports for example contained an untagged and tagged traffic. When you create VLANs within pfSense you are essentially mixing native or untagged traffic with tagged traffic.