able to nmap scan across vlans
-
So i have my completed my pfsense build and configured multiple VLAN's. My guest vlan40 is on 10.0.40.0/24 subnet and has block rule to RFC1918 and pass rule to DNS. All good, except that my laptop on vlan40(guest) can run nmap and discover every devices on other vlan vlan30(iot). When i see firewall logs during scan, lot of things get blocked, but i can still see that it located devices on vlan30. I can replicate is behavior on all vlans. Is this normal? Or did i miss something in the rules.
-
@gi2r2ig said in able to nmap scan across vlans:
Or did i miss something in the rules.
You would have to post them if you want info on that ;)
-
Here are my rules. Some might be redundant, but bare with me, i will get those fixed when i graduate in pfsense :)
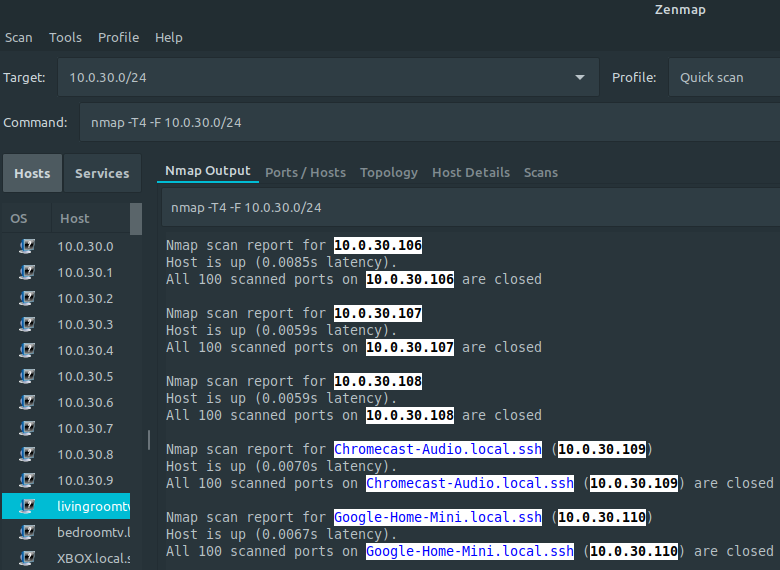
My laptop is in VLAN40 which is initiating nmap scan on VLAN30
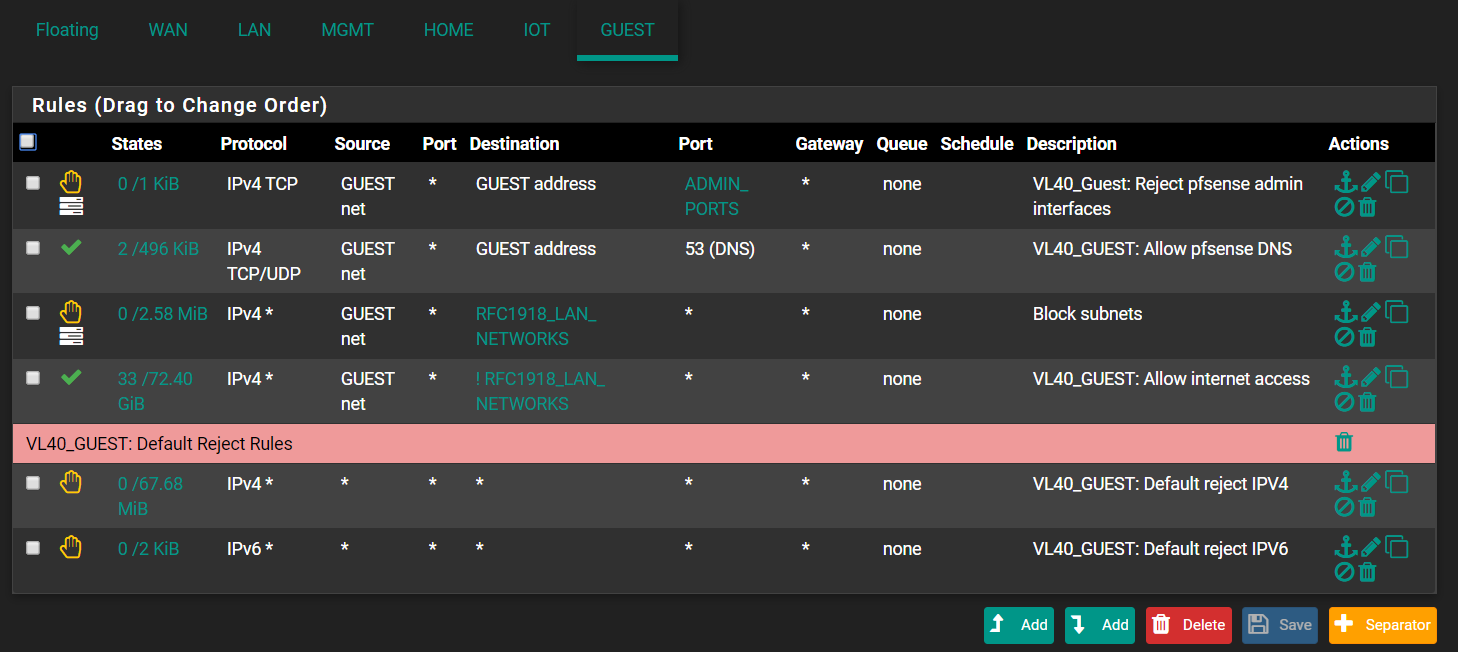 GUEST: VLAN40
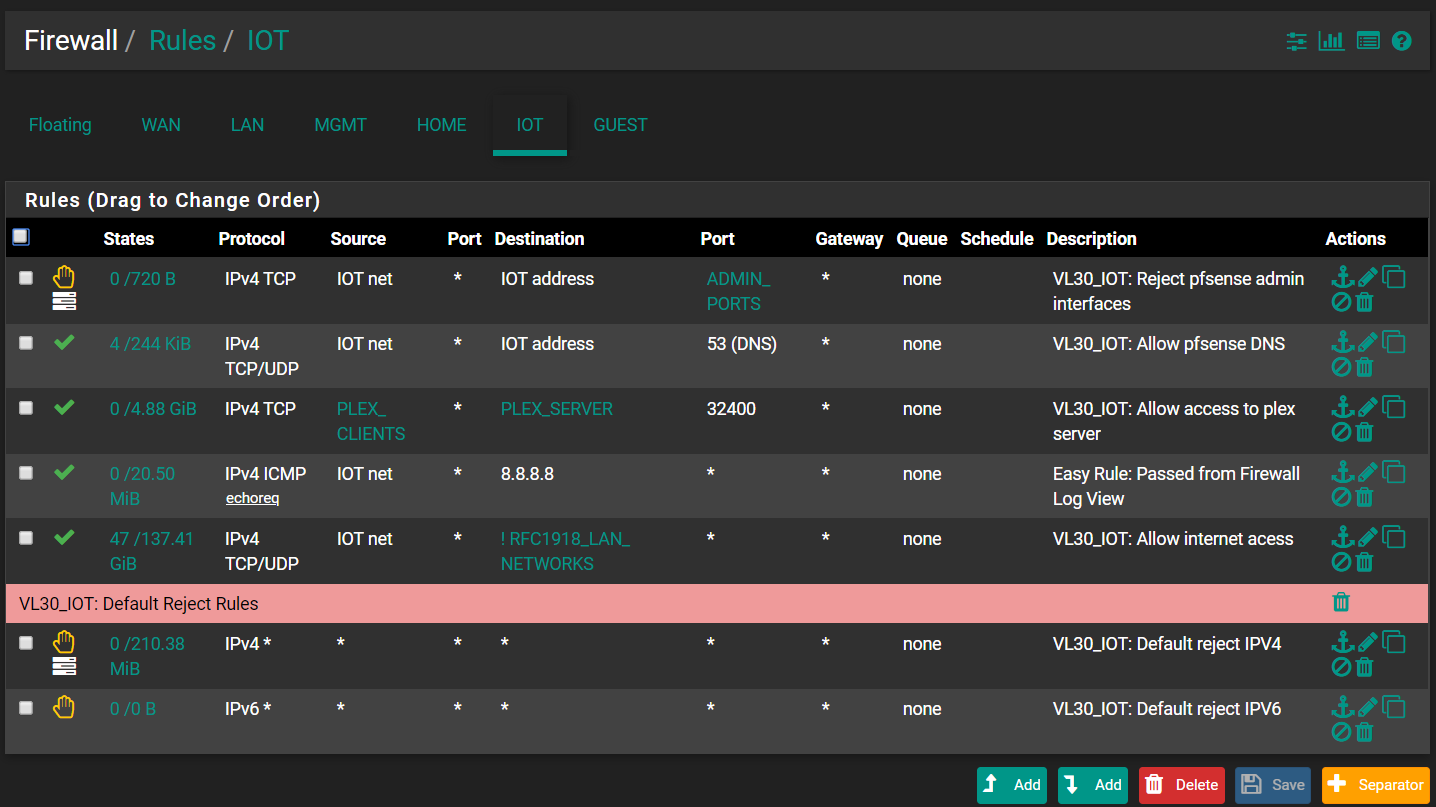
GUEST: VLAN40Below rule is for the VLAN30.
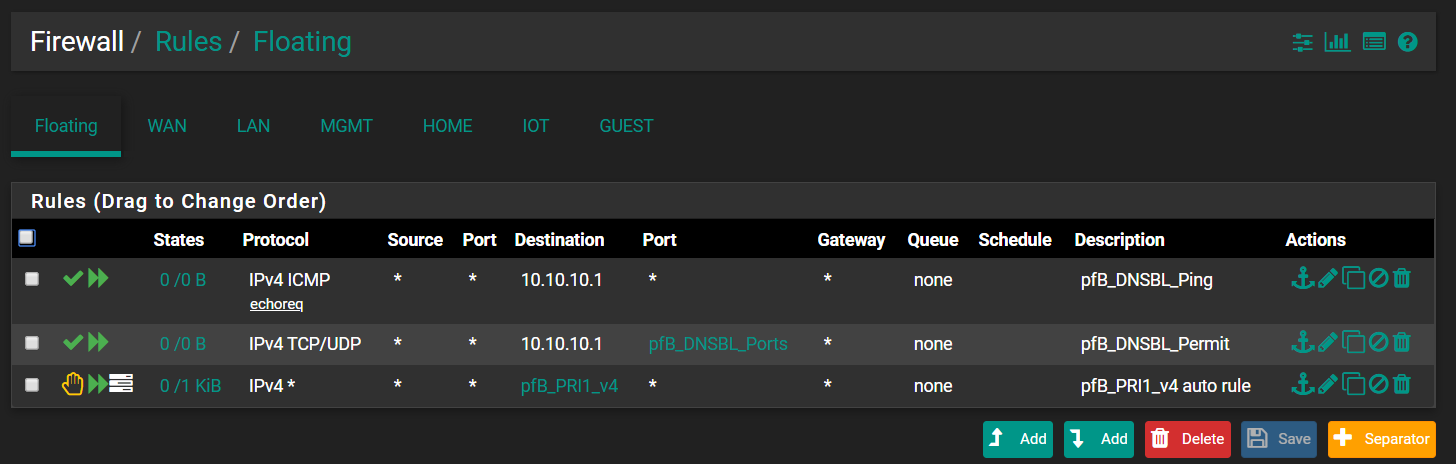
This is my floating rules: All generated by pfblocker
-
well your doing reject... so yeah anything you send that is blocked is going to send back a reject... So if you try and do nmap to something that sends back a reject.. Nmap would think its up, and port would be closed..
So here - I put in a block to 192.168.3.32, ntp server on my dmz vlan.. I then do a nmap to that IP.. Notice nothing returned.. host looks down.
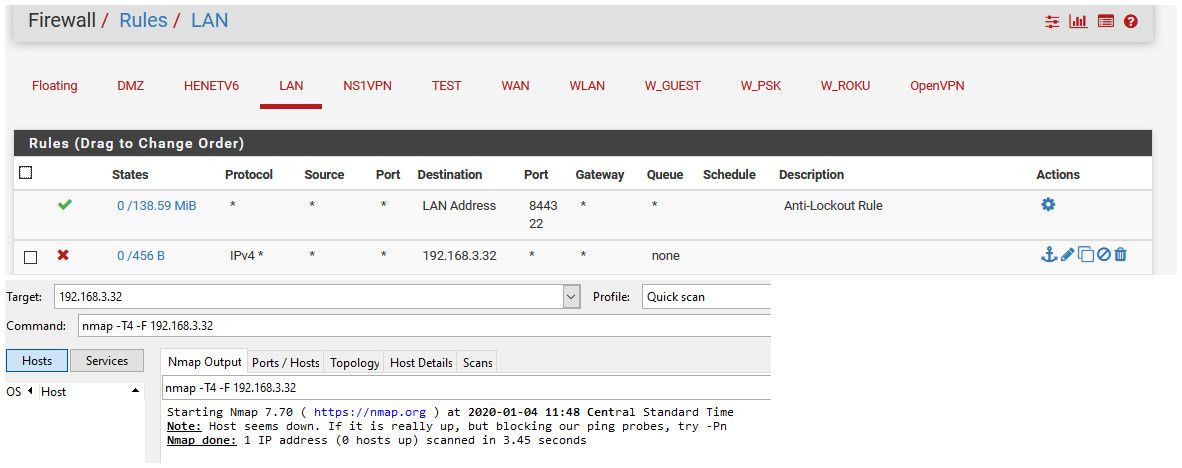
I now set the rule to "reject" and do the same scan... And it shows host is up, but all closed
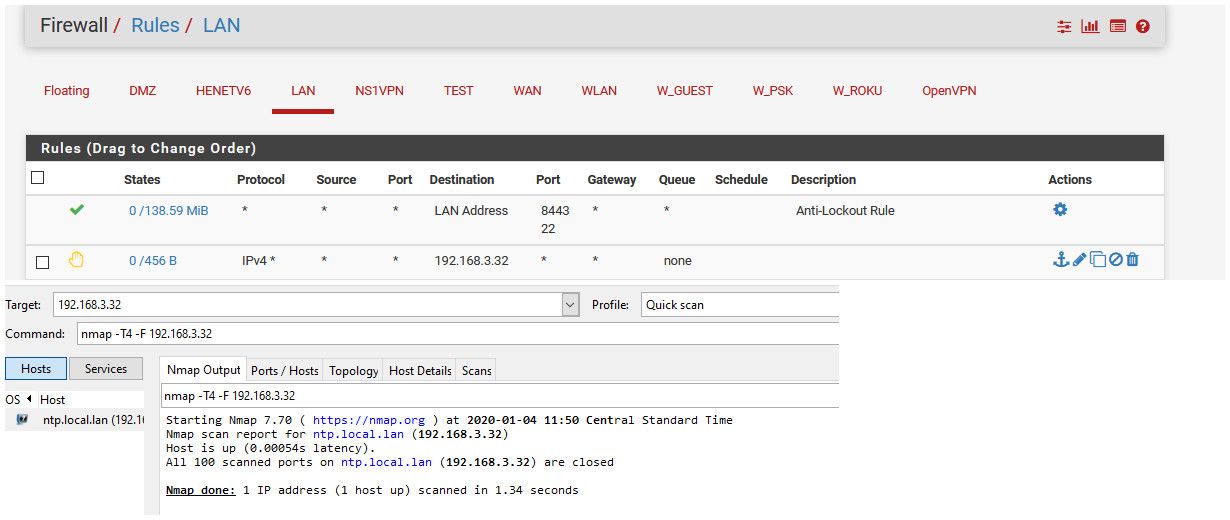
Now if you do a sniff while your scanning... You will see that pfsense is sending back RST for all the ports I tried to scan.. So to nmap... Hey must be "up" but all the ports are closed..
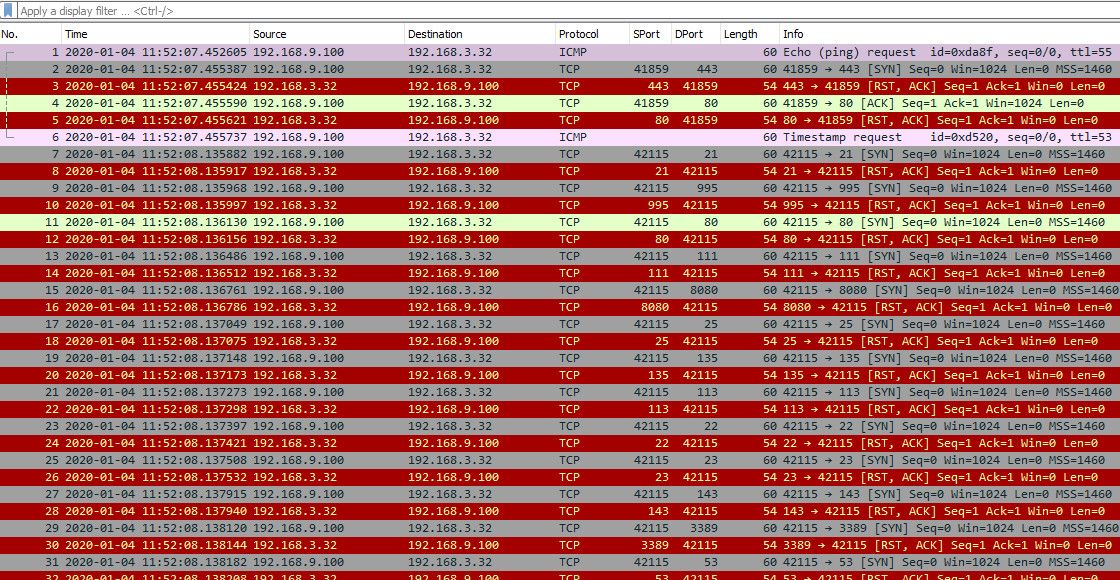
-
Thank you so much. I am glad issue was not what i expected. I was able to replicate this on my guest(vlan40) and got nothing.
So, it seems that if you don't want your Guest to know what's in your network, you will need "Block" rule instead of "Reject" rule.
Interesting to see that nmap was able to identify devices on different subnet even with reject rules. I can understand [host up/down] based on response, but wasn't expecting detail host info. -
Well he would do a dns query for it - dns is pointing to pfsense and allowed per your rules.. If he doesn't think the host is up, he won't bother to do a dns query.
Reject is normally done on your networks, you want to know right away if something not going to connect.. Vs having to wait for timeouts and retrans. But wan or guest - yeah you might not want to do reject.
If real guest network - just hand them some public dns via dhcp, etc.. And don't let them query pfsense for dns.
-
Got it. Once again thank you. I know what i need to do now.