RFC 1918 Traffic leaving the WAN interface
-
Is it an issue that I see RFC 1918 traffic leaving the WAN interface. I have my local network setup using 10.23.X.X/16 as my local networks. However, I noticed that some Apple devices are trying to connect to various 192.168.1.X addresses on port 7000.
I did a packet capture on the WAN interface and I can see that they are indeed going out the WAN interface. Isn't this an issue? I worry that maybe a device outside my network, could be using 192.168.1.X.
I was wondering if I should have a static route to RFC1918 going to null?
I assumed that pfSense by default would prevent this type of traffic leaving the router.
-
Did you mess with outbound nat? Post up your outbound rules
Is your pfsense wan 192.168.1.x?
-
@IsaacFL said in RFC 1918 Traffic leaving the WAN interface:
I have my local network setup using 10.23.X.X/16 as my local networks
192.168.1.x would be outside of your subnet so logically the router will try to send it to the gateway address.
My question is why are those devices trying to use an address that has nothing to do with your network??
If RFC1918 addresses are supposed to go to null Im not aware. (someone else can correct me.. Your ISP would not route them any further than their premises.
-
10:34:06.116571 00:90:7f:88:b4:2e > 00:17:10:90:a7:a3, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 127, id 279, offset 0, flags [none], proto ICMP (1), length 60)
24.xxx.1xx.1xx > 192.168.50.5: ICMP echo request, id 14063, seq 36, length 40
10:34:10.909794 00:90:7f:88:b4:2e > 00:17:10:90:a7:a3, ethertype IPv4 (0x0800), length 74: (tos 0x0, ttl 127, id 286, offset 0, flags [none], proto ICMP (1), length 60)
24.xxx.1xx.1xx > 192.168.50.5: ICMP echo request, id 14063, seq 37, length 40192.168.50.5 is not an address we use anywhere in our network. So this ping fails but is still sent to my ISP via the WAN.
In fact I got a return from one of the headend routers that 192.168.50.5 was unreachable.
-
@chpalmer said in RFC 1918 Traffic leaving the WAN interface:
In fact I got a return from one of the headend routers that 192.168.50.5 was unreachable.
I get an Administratively prohibited message back.
-
@chpalmer said in RFC 1918 Traffic leaving the WAN interface:
192.168.1.x would be outside of your subnet so logically the router will try to send it to the gateway address.
Exactly - I read that too quickly I guess, I was thinking you were seeing that as the source of the traffic, ie you using the 192.168.1/x internally and it wasn't being natted to your public IP.
But yes @chpalmer is correct - if you try to go to some IP that is not local - pfsense would send it on to the gateway.. Be it not valid or not... Pfsense just knows its not local - so it would send it to its default gateway - but it would be natted to your public IP...
You can see from chpalmers example where its 24.x.x.x trying to ping 192.168.50.5 - that IP is his public IP.
If you do not want rfc1918 to leave your wan.. Couple different ways you can stop it.. Simple firewall rule blocking access to rfc1918 that your not using locally on some other vlan, etc.
Or you could get fancy and do a floating rule that blocks outbound traffic out your wan going to rfc1918 space.
-
What I was thinking of doing was to create an alias with 192.168.0.0/16, 172.16.0.0/12, 10.0.0.0/8 networks.
Then I create a static route using the Null4 - 127.0.0.1 as the gateway. I think that this should prevent that traffic from leaving the local network.
I was wondering though if this would cause a problem somehow, as I am surprised that this isn't already there by default?
-
@chpalmer said in RFC 1918 Traffic leaving the WAN interface:
@IsaacFL said in RFC 1918 Traffic leaving the WAN interface:
I have my local network setup using 10.23.X.X/16 as my local networks
192.168.1.x would be outside of your subnet so logically the router will try to send it to the gateway address.
My question is why are those devices trying to use an address that has nothing to do with your network??
If RFC1918 addresses are supposed to go to null Im not aware. (someone else can correct me.. Your ISP would not route them any further than their premises.
I don't know why the apple products do it. I see it from both iphones, ipads, and apple tvs. I tried resetting the network interface on an iPhone, thinking maybe it had leftover ip information but they still send out traffic to a subset of 192.168.1.X addresses.
It is puzzling to me too. I am wondering if it might be an app on the device.
-
I wouldn't do it that way... Just create a simple firewall rule, you can use your alias of rfc1918 space sure..
Put it on your wan via floating outbound rule, or put it on your local interfaces - and have it log... This way you can see when its being hit.
edit: My iphones and or tablets not doing such a thing... I have rules that block access to rfc1918 space on my psk and roku vlans for example.. That my iphones and tablet on now and then... And it doesn't really get any hits on them..
Normally the hits on see on those rules are out of state traffic to my plex..
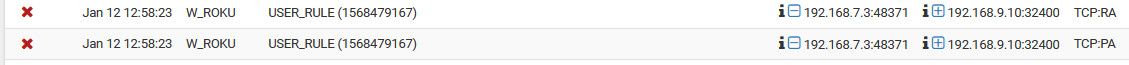
They normally then retry and works since that traffic is allowed by rule above when it sends a syn

-
@IsaacFL said in RFC 1918 Traffic leaving the WAN interface:
What I was thinking of doing was to create an alias with 192.168.0.0/16, 172.16.0.0/12, 10.0.0.0/8 networks.
I was wondering though if this would cause a problem somehow, as I am surprised that this isn't already there by default?
If you have a cable modem you will no longer be able to access its GUI.
Its really nothing to worry about.
-
^ yup very true - unless creates a rule to allow that access above... Again null route sort of solution not a good one.
example
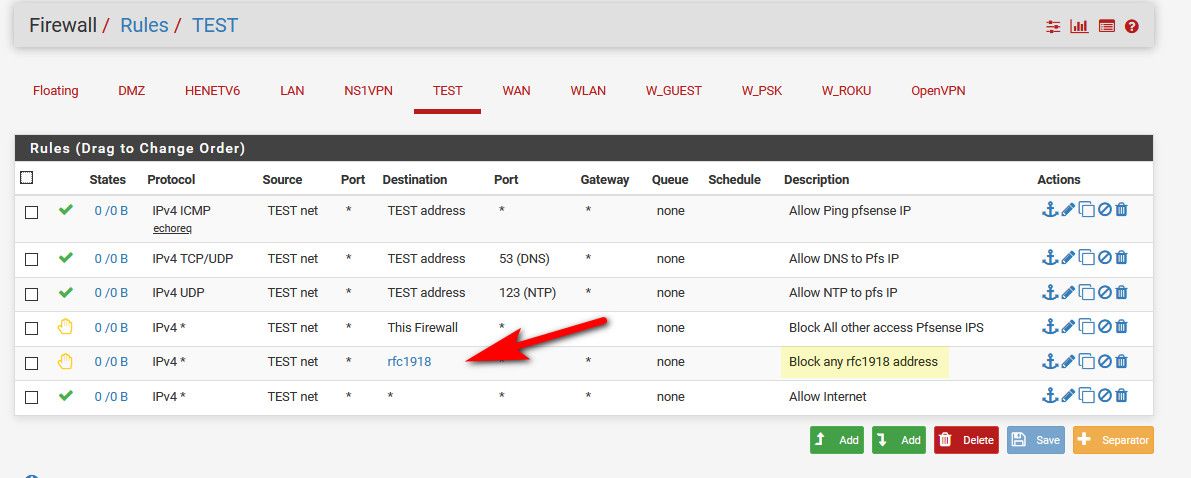
Something like the above would stop what your seeing, and if you set the rule to LOG - then you would see if anything is trying to go to some rfc1918 space.. And you would see what specific client is doing it, and exactly when.. Since it would be in your logs... And simple view of the rules would tell you if any hits on it to go look in the logs via 0/X number increasing..
edit:
example 2
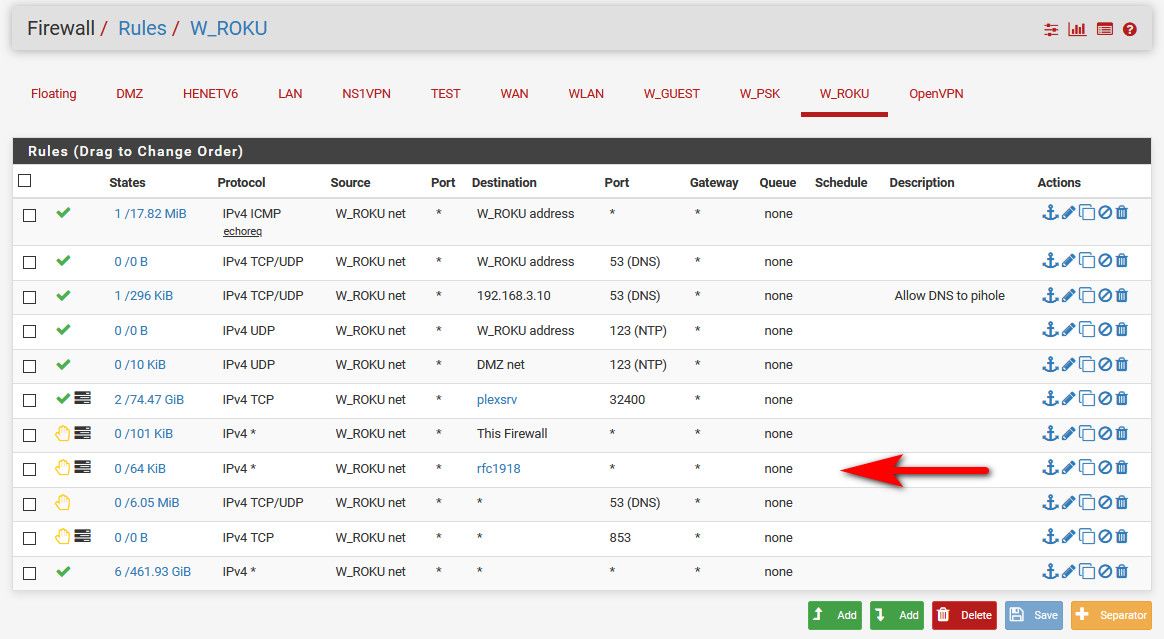
See the rule blocking access to rfc1918, and being logged - this is how I could show you stuff being blocking going to my plex IP on the plex port (out of state)..
-
@johnpoz said in RFC 1918 Traffic leaving the WAN interface:
I read that too quickly I guess
I refuse to comment on the grounds it may tend to incriminate me..

-
Ok, so I deleted my route, and created a RFC 1918 reject rule on the subnet with the Apple devices. It seems to log every few minutes. Weird thing is it is not even in the same /24. Googling tells me port 7000 is related to Airplay.
the .230 and .231 are both Apple Tv's but I have also seen it on the iphones.
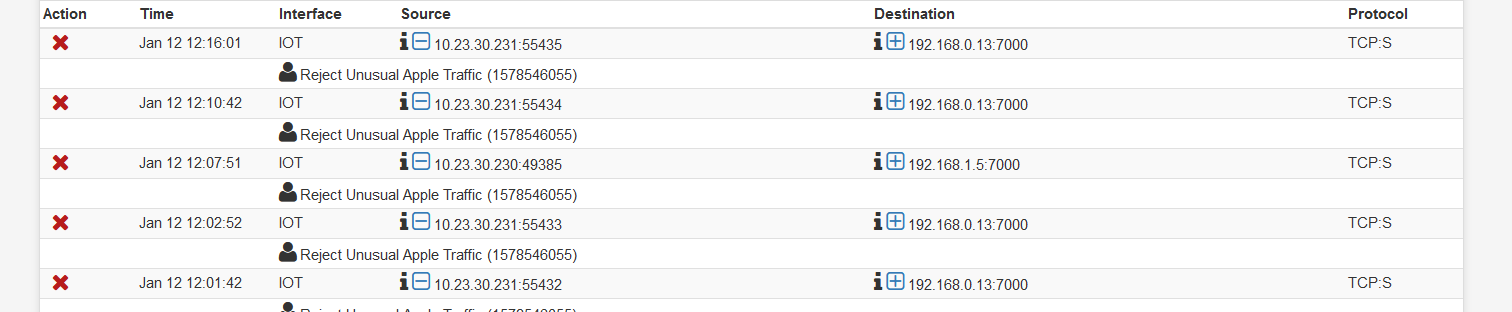
-
The problem with blocking the RFC 1918 traffic is that now all local traffic is getting blocked also, which is fine on an IOT network.
Probably this would require a floating rule on the WAN network.
What is the problem with adding the null route I had before? This seems to me more of a routing problem vs a firewall problem.
-
Do your neighbours have Apple products?
https://www.reddit.com/r/HomeKit/comments/bk1ee9/home_app_tries_to_communicate_with_random_ip_on/ -
@Pippin said in RFC 1918 Traffic leaving the WAN interface:
Do your neighbours have Apple products?
https://www.reddit.com/r/HomeKit/comments/bk1ee9/home_app_tries_to_communicate_with_random_ip_on/I don't know for sure but they probably do. That was my concern is that there might be an actual device outside my network.
-
@IsaacFL said in RFC 1918 Traffic leaving the WAN interface:
The problem with blocking the RFC 1918 traffic is that now all local traffic is getting blocked also
What the F you think could happen with your nonsense routing stuff to null?
If you want vlan on 192.168.X to talk to another vlan 192.168.Y for example - then allow that traffic above your block rule.. As shown in my example I allow to talk to my plex server on a different rfc1918 vlan.. I allow devices to talk to my ntp that is on another rfc1918 vlan. Just allow what rfc1918 traffic you want to allow before you block..
If you want lan to talk to your dmz net for example, then put that rule above where you block rfc1918.
Rules are evaluated, top down, first rule to trigger wins..
If all you have is 1 network, there is no other vlans to talk to using rfc1918.. Devices on your network don't talk to pfsense to talk to something on their own network.
-
@johnpoz said in RFC 1918 Traffic leaving the WAN interface:
@IsaacFL said in RFC 1918 Traffic leaving the WAN interface:
The problem with blocking the RFC 1918 traffic is that now all local traffic is getting blocked also
What the F you think could happen with your nonsense routing stuff to null?
If you want vlan on 192.168.X to talk to another vlan 192.168.Y for example - then allow that traffic above your block rule.. As shown in my example I allow to talk to my plex server on a different rfc1918 vlan.. I allow devices to talk to my ntp that is on another rfc1918 vlan. Just allow what rfc1918 traffic you want to allow before you block..
If you want lan to talk to your dmz net for example, then put that rule above where you block rfc1918.
Rules are evaluated, top down, first rule to trigger wins..
If all you have is 1 network, there is no other vlans to talk to using rfc1918.. Devices on your network don't talk to pfsense to talk to something on their own network.
I think it is just as much nonsense to route it out the WAN interface when the RFC explicitly says not to do that.
I have much more than 1 subnet.
When you route to null, the router just drops the packet.
So if I create a static route for 10.0.0.0/8 to Null4 - 127.0.0.1 and pfSense has already auto created routes for each defined interface ie. 10.23.30.1/24 etc.
The router knows to always pick the most explicit route.
But I am willing to hear why that might be an issue that I don't understand?
-
@IsaacFL said in RFC 1918 Traffic leaving the WAN interface:
I think it is just as much nonsense to route it out the WAN interface when the RFC explicitly says not to do that.
Those addresses are just as routeable as any other. What if the WAN side was also in RFC 1918 address space? They should be blocked from the Internet though, which can be done with appropriate filters.
-
@IsaacFL said in RFC 1918 Traffic leaving the WAN interface:
RFC explicitly says not to do that.
Yes. And your ISP handles that for you.

You will not find a single SOHO router that blocks out of subnet traffic from going out the gateway.
What is borked is a device that is trying to reach an RFC 1918 that is not in your network somewhere. Id be wanting to fix that and not be trying to band-aid the problem.