IP4 & IP6 Firewall Best Practices
-
Good afternoon all,
I have set up IP6 as well as the native IP4 on my pfsense system, my IP4 setup gets its single IP for WAN, as has four subnets (one for Home, One for Guest, One for Servers and one for VPN). IP6 works the same way except it has a /60 and I have allocated 4 x /64 to those same subnets.
I am slightly confused though on how I set up the firewall to only allow IP6 to communicate with the outside world and not with internal devices (i.e. I don't want a guest IP6 device to communicate with a home IP6 device).
For IP4 I would have just had a PASS to allow traffic out to the WAN net however, I am not sure how that works with IP6, can I have the address family as IPv4 and IPv6 and still have WAN net (i didn't think this would work as it is a track interface and link local).
How do I go about firewalling the IP6 connections, do I need to have a seperate rule for IP6 traffic, and what would the network range be (as I assume if I do something like 2000::: etc it will allow all traffic including back to the Home?)
Apologies if these are simple questions, just very confused with how to most securely firewall IP6 traffic. I am not after a rock hard paranoid system, just something that is not purposely leaving the door unlocked if that makes sense?
Many thanks!
-
There's not much difference between IPv4 and IPv6, other than not needing NAT for IPv6. You can create rules that work for IPv4, IPv6 or both. For example, if you were filtering based on protocol, then you could create a rule that does both. If you create one based on an address, then you'd need separate rules for IPv4 and IPv6.
-
Thanks, I guess because I am new to IP6 I just want to double check and not do something silly.
In this case, I have created a number of rules for my guest network (below), would it be a safe thing to do to have an alias for the local subnets (e.g. IP6 & 4) and then just create an inverse rule below, so if the traffic from the Guest network is not to local subnets, then let it out or is there a better / more efficient way to achieve this?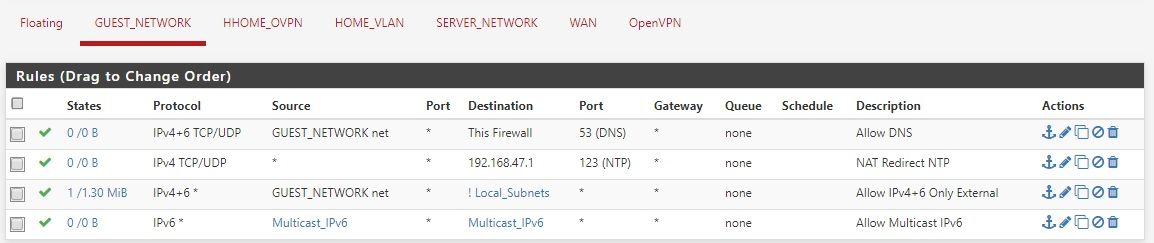
Many thanks!