Mini ISP + servers on same public IP
-
Hi, just wondering what would be the best DNS/routing practices in my setup:
- one public IPv4 address.
- 3 internet customer VLANs
- 1 VM VLAN for servers
- 1 management VLAN
- 1 hypervisor VLAN
- 1 VPN VLAN
- Snort
There is one DHCP server per VLAN.
I have defined firewall rules for the 3 customer VLANs as follows:
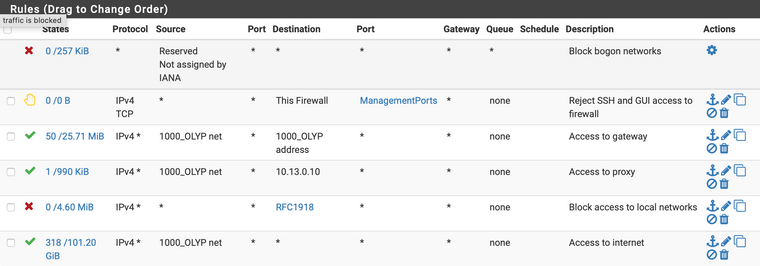
- Default "Block bogon networks"
- Reject | IPv4 TCP | * | * | This Firewall | ManagementPorts (443 + 22) | * | none
- Pass | IPv4 * | {customer} net | * | {customer} net | * | * | none
- Block | IPv4 * | * | * | RFC1918 | * | * | none
- Pass | IPv4 * | {customer} net | * | * | * | * | none
There is also a NAT port forward to a nginx proxy on the VM VLAN which then forwards the request to the correct server based on the domain.
I can access the servers from the internet, but when my internet customers try to access the servers it seems to be stopped by snort since the request originated on the WAN IP and it is marked as "potentially bad traffic".
I tried setting up a DNS resolver and adding the host/domain names to the servers, but then I guess it gets blocked by the RFC1918 block.
What are common/best practices in this scenario?
-
@jonasbarsten said in Mini ISP + servers on same public IP:
Pass | IPv4 * | {customer} net | * | {customer} net | * | * | none
Pass | IPv4 * | {customer} net | * | {customer} net | * | * | none << would only be seen on the local firewall interface
Use Pass | IPv4 * | {customer} net | * | {customer} address | * | * | none
Or Pass | IPv4 * | {customer} net | * | This Firewall | * | * | none
What exactly is snort blocking whats the rule ?
Also have you read https://forum.netgate.com/topic/55095/quick-snort-setup-instructions-for-new-users/147 don't set blocking to start off with get a baseline.
-
Thanks for clarifying!
Pass | IPv4 * | {customer} net | * | {customer} net | * | * | none << would only be seen on the local firewall interface
Without this rule customers didn't get internet access, I figured it had to do with obtaining the gateway and/or DNS server(s). That way using
| {customer} address |
makes much more sense, thanks!
But wouldn't I need:
Pass | IPv4 * | {customer} net | * | {customer} net | * | * | none |
to allow clients on the customer VLAN to talk to each other since I have the RFC1918 block?
What exactly is snort blocking whats the rule ?
I have some more reading to do, I have no idea, thanks for the link!
If I get snort to not block requests originating from the WAN IP, is it the recommended way to route requests from the customer VLANs to the servers via the public IP?
Thanks for helping!
-
Does Customer A actually need to talk to Customer B ?
I’d be unhappy if I was Customer B and had a Virus / Trojan down to Customer A.
BTW you can drag screenshots into the chat window.
-
Does Customer A actually need to talk to Customer B ?
No, my bad, still figuring things out. Your advice of giving the customer net access to the customer address seems like the best solution, thanks!
BTW you can drag screenshots into the chat window.
Didn't know that, thanks.
I solved the routing to the servers by giving the customer VLANs access to the proxy host. Seems more elegant than routing it out via the internet and back. I'm open for other solutions.
Final customer rules as follows, please feel free to suggest enhancements.