Windows RADIUS Server
-
Hi,
I also tried use Microsoft NPS as radius server, but it didn't work, here is the detail:Client side, user got the error message "could not connect to authentication server." after they input username and password.
NPS server side, I can see "Audit Success" log from windows event logs, i.e. NPS granted access to the user, authentication request was accepted.I don't know why it showed error in client side.
btw, one authentication request will trigger 2 logs in NPS logs, but when I tried to authenticate in the portal page, NPS server will got 3x2 repeated logs, it seems that pfsense tried to authenticate 3 times (all successful).
-
@mohkhalifa May I know which version of pfsense do you use?
I tried following two version pfsense, neither of them works. I tried both MS-CHAPv1 and MS-CHAPv2, It seems that pfsense doesn't handle the radius response from NPS well.
-
2.3.4-RELEASE-p1
error sending request: No valid RADIUS responses received. -
2.4.5-RELEASE-p1
error: could not connet to authentication server.
but when I checked the NPS (network policy server), I can see the success log when I tested both versions, I got twice success logs when I test 2.3.4 p1, got 3 times success logs when I test 2.4.5 p1.
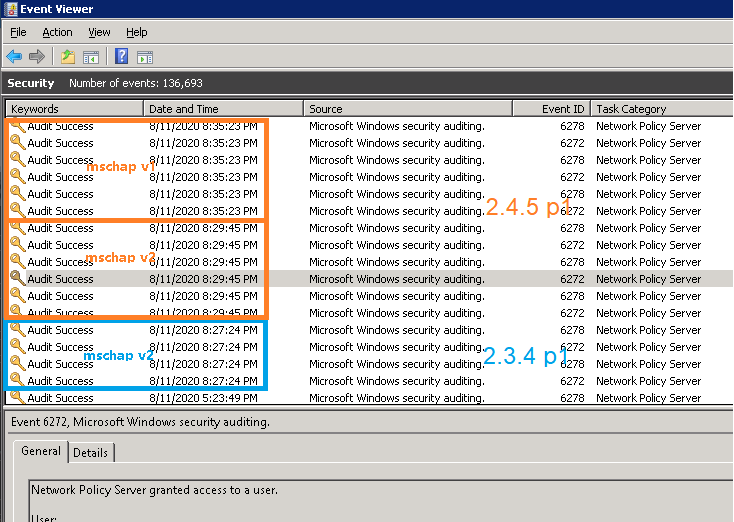
-
-
Dear @yanqian,
I'm using the latest version of pfSense 2.4.5-RELEASE-p1
also I sent you a private message -
I've got PfSense with version 2.4.5-RELEASE-p1. In the same LAN subnet I have my Windows Server 2016 with a Radius server working under Network Policy Server. I have followed the tutorial at https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/authenticating-openvpn-users-with-radius-via-active-directory.html
I'm having the same problem as @yanqian.
- For any authentication attempt in "PfSense > Diagnostics > Authentication" I get the error message "Authentication failed".
- In "PfSense > Status > System logs" for each attempt appears a new line with the message "/diag_authentication.php: Error during RADIUS authentication : No valid RADIUS responses received".
- In the NPS event log, for each authentication attempt appear at least 4 log entries with event ID 6272 which indicate a successful attempt.
Both servers can see each other via network.
-
After writing the last message, I have successfully configured LDAP authentication server in the same PfSense device that points to the same Windows Server. This way everything works, including OpenVPN clients validation using allowed domain user accounts.
-
@Xavi_IT said in Windows RADIUS Server:
After writing the last message, I have successfully configured LDAP authentication server in the same PfSense device that points to the same Windows Server. This way everything works, including OpenVPN clients validation using allowed domain user accounts.
Sounds good. Also, you can add custom attributes to control per user bandwidth. it's really amazing integration. ENJOY :)
-
@mohkhalifa
Could you please share the configuration tips with me?
I did get your private message, but I am not able to let you do the configuration remotely.
Thanks any way.@Xavi_IT
May I know how did you solve this issue ?
Thank you! -
Hello @yanqian,
I could not configure a Radius server in PfSense "Authentication Servers". I followed several tutorials and Windows NPS event log was returning succesfull authentication attempts, but I could not figure out why didn't PfSense was not getting them.Finally I had success using LDAP instead of Radius in PfSense "Authentication server" to connect to Windows Active Directory. With LDAP It worked at first attempt.
-
@yanqian did ur issue got resolved .. i to have the same issue in pfsense
-
@anwarmoinudeen Hi Sir did your issue got resolved already? i also have the same issue in pfsense
-
@anwarmoinudeen As I recall, I hadn't solved this issue, and I gave up NPS radius server test. I hope @mohkhalifa would provide the guide in detail.
-
Old topic but try this:
First you need to know the vendor code for PFSENSE which I found in https://github.com/pfsense/pfsense/blob/master/src/usr/share/doc/radius/dictionary.pfsense
VENDOR pfSense 13644 BEGIN-VENDOR pfSense ATTRIBUTE pfSense-Bandwidth-Max-Up 1 integer ATTRIBUTE pfSense-Bandwidth-Max-Down 2 integer ATTRIBUTE pfSense-Max-Total-Octets 3 integer END-VENDOR pfSenseNow you can go to your network policy in NPS for the captive portal. Go to:
SETTINGS, VENDOR SPECIFIC, ADD, "custom", "Vendor specific/Radius standard", ADD,ADD:- Enter Vendor Code = 13644
- Yes it conforms
- configure Attribute -> 1 for pfSense-Bandwidth-Max-Up with decimal and you bandwidth
repeat for 2 = pfSense-Bandwidth-Max-Down
Untested but this should work in theory.
-
@jimmychoosshoes after that how can we limit bandwidth by users can you help me?
-
Y yanqian referenced this topic on
-
@anwarmoinudeen I know this is old, just want to update here, I tried to use NPS on server 2016 as RADIUS server today, and it works without any issue.
Pfsense version is 2.7.0, RADIUS MS-CHAPv2 . -
@yanqian with FreeRadius?
-
FreeRadius is not " NPS on server 2016 as RADIUS server".
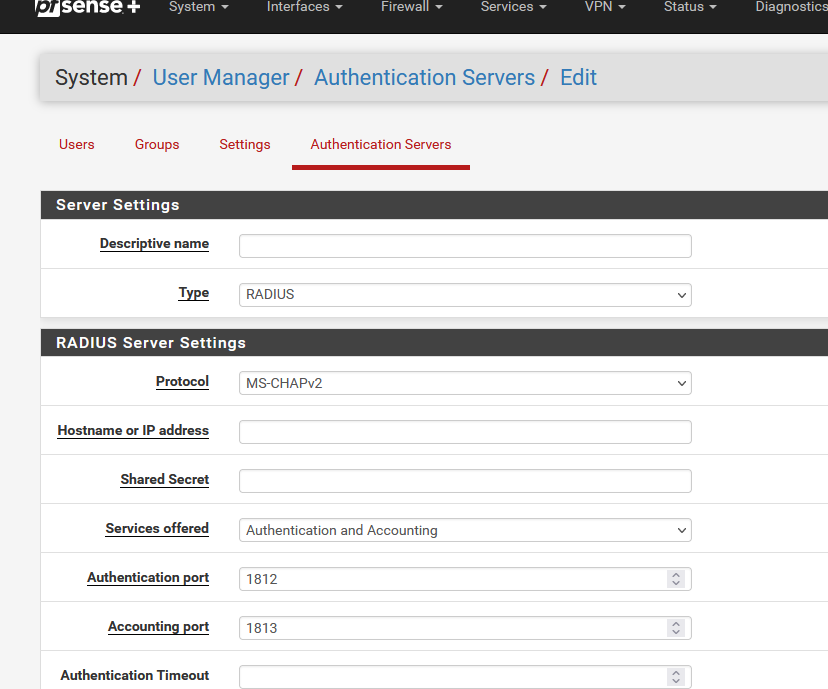
Instead of install the FreeRadius pfSense package, @yanqian installed a Radius serves on a Micorsoft (server ?) and use that Radius server.
It isn't a free one (as it is from Microsoft)
He probably used this :
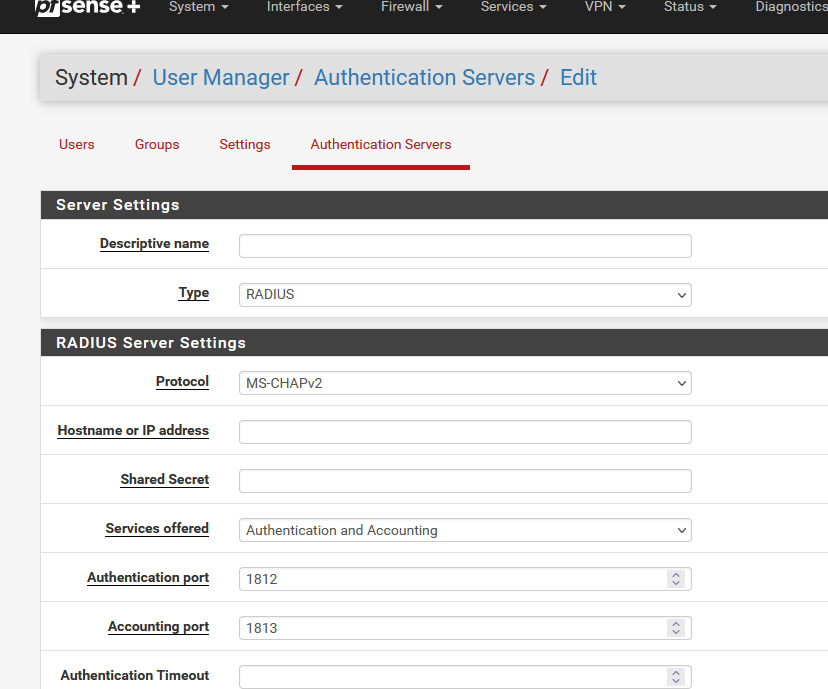
to set up an external authorization/authentication (Radius) server.
-
@Gertjan )) i use this method too and it is not hard to configure
-
@dochy Yes it's hard but you have to prepare a good coffee and I trust that you will did it.
-
This post is deleted! -
@mohkhalifa we are still waiting for that manual please can you help us