Is pfBlockerNG able to block all outbound traffic except whitelistet sites?
-
I've been going back and forth with TAC about this, since like @CZvacko, we need to have a replacement for SquidGuard when it is removed. For completeness, since I don't see it linked anywhere else in this thread, here are the firewall requirements for a local WSUS server in an isolated network. If you aren't' using a WSUS server and update directly from microsoft then the same requirements apply to workstations.
Also before anybody jumps in with Windows Update specific workarounds, this issue is not limited to Windows Update, it's just a good example use case. We have other applications with the same requirements, namely no access to the internet except for specific whitelisted URLs that may be wildcards and almost certainly point to a CDN. Both of which requiquirements preclude using the native pfsense firewall.
I have not set up a test environment to try this in yet and I have some reservations about it being a suitable replacement for a filtering forward proxy but this is TAC's recommended solution at this time:
Start reply from TAC support on 2023-11-29:
pfBlockerNG is not a supported package by TAC, so we cannot provide any assistance beyond best effort for it.
However, if you want to go the DNS-based filtering route, it's fairly straight forward:
- Create a rule allowing DNS traffic on ports 53 and 853 to the firewall and a deny rule for any other DNS destinations.
- Install pfBlockerNG and configure it to have a whitelist of the hostnames you want to allow. You can reuse the lists you have in squidGuard now and paste these hostnames with wildcards into the whitelist. Then simply deny all other DNS lookups besides the ones you wish to allow.
- Point your hosts at pfSense Plus for DNS lookups. Any hostnames not in the whitelist will return the IP of the firewall's block page for pfBlockerNG
You can also provide the ASNs for the various Microsoft IP blocks into pfBlockerNG, tell pfBlockerNG to use the "Alias" option, and then add firewall rules allowing and denying traffic like any other firewall rule using these ASN Aliases as the means of blocking or allowing traffic. Bear in mind that this will allow or deny all of Microsoft and not simply Windows Update, but if that is acceptable to you as a scope then it would work as well.
End reply from TAC support on 2023-11-29:
-
@AlternateShadow said in Is pfBlockerNG able to block all outbound traffic except whitelistet sites?:
DNS-based filtering route
I created a lab environment to see if such a solution is workable.
But since I have no experience with pfBlockerNG, I'm not sure if I'm going in the right direction. Step 1+3 seems clear, but step 2 does not.What I did: in IP - IPv4 I disabled default blocking category (since my logic is reversed - I'm bloking everything by default). Then I created new categories for allowed sites:
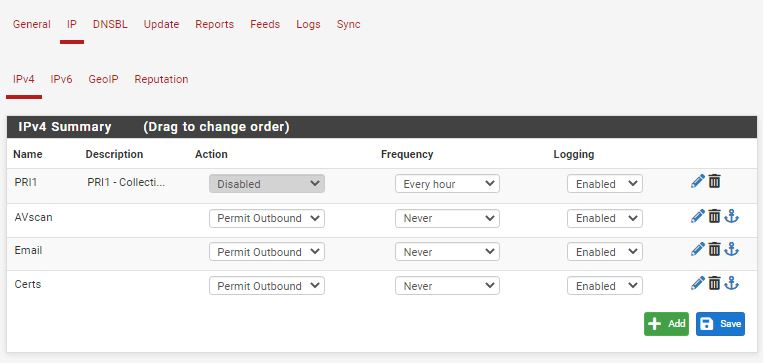
In each category I input related domains into IPv4 custom list (is this correct approach?)
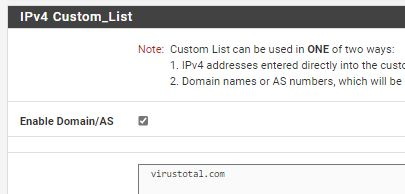
When I force update setting, it generate firewall rules
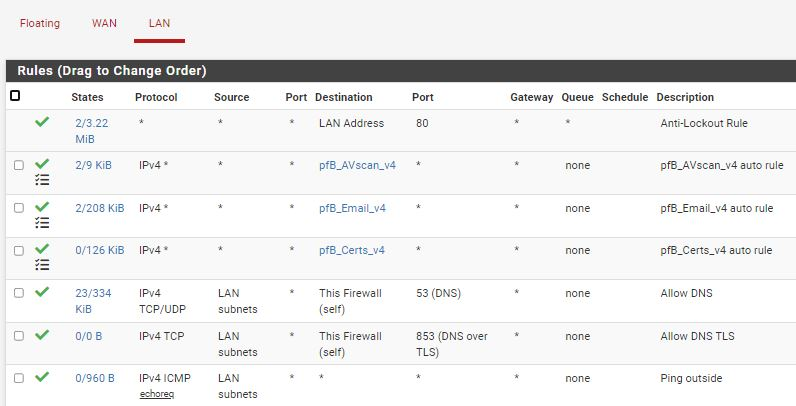
When try open related sites in webbrowser, not always they work. I thing issue is with IP based concept, for example: virustotal.com have different IP than www.virustotal.com (which in not allowed by FW).
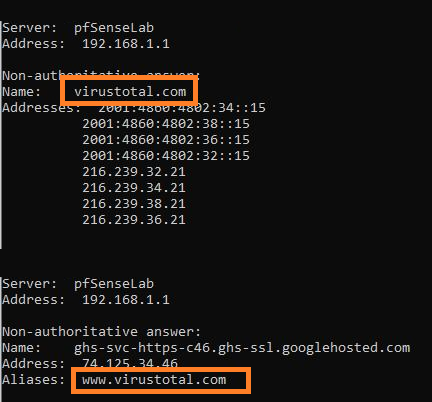
This is how step 2 should be performed ?
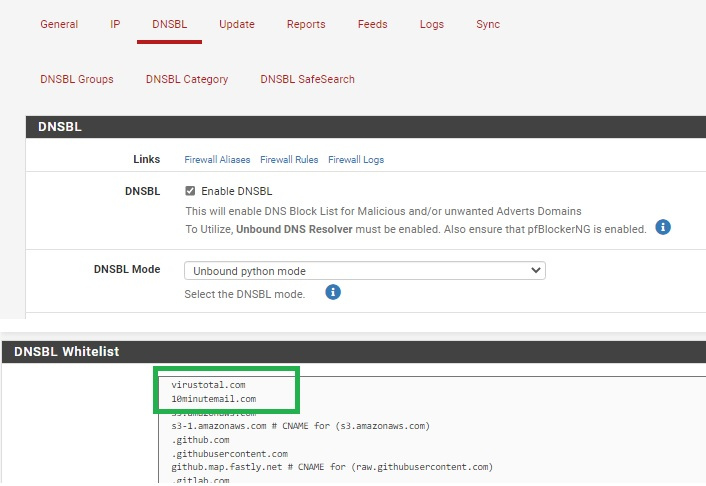
I also did some experiment under DNSBL - DNSBL Whilelist, but that didn't work at all :-(
For example in Fortigate firewall is webfilter feature, where I can input wildcard and it allow website correctly.
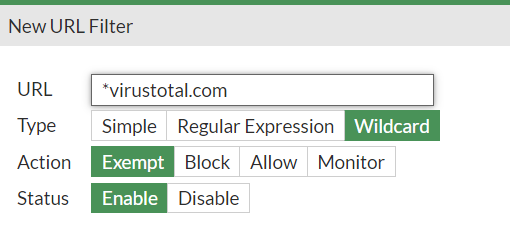
I'm looking for something similar in PFsense. -
@CZvacko For the first attempt/part, technically you can do that without pfBlocker...create an alias, add your hostnames, and pfSense will resolve the hostnames in the alias every 5 minutes by default. However there are caveats as you found:
- every hostname initially queried has to be entered (www.example.com, svr2.example.com)
- one cannot use a wildcard (*.example.com)
- hostnames may change IPs frequently
Doing that in pfBlocker, I don't know offhand if it resolves the names every 5 minutes or at reload. Haven't tried.
An option is to create a host override or domain override in DNS Resolver, and point the names to nowhere.
In pfBlocker one can create a DNSBL Group and block domains, but that's the opposite of what you're asking for.
I have not tried, but possibly you could block *.com, *.net, etc., enable Wildcard Blocking (TLD), and then add entries to the DNSBL whitelist?