Questions regarding VLANs
-
I am really unexperienced regarding VLANs, so I hope you guys can help me out.
I have the following setup in my home:
- SG-1100 as router
- The SG-1100 connects with a single ethernet cable to some 16-port ethernet switch
- In addition, I have a WLAN access point (Ubiquiti UniFi AP AC Pro) which is also connected to the ethernet switch
- The access point is serving 2 networks with 5GHz and 2.4GHz
- All devices/computers in the network are then either connected to the ethernet switch or using WLAN
I have the following devices in the network:
- Windows computer (cable)
- Laptop (WLAN 5GHz)
- Mobile phone (WLAN 5GHz)
- FreeBSD based NAS (cable)
- FreeBSD based NAS (backup) (cable)
- Printer (WLAN 2.4GHz)
- Rasberry pi for brewing beer
 (WLAN 2.4GHz)
(WLAN 2.4GHz)
And a crapload of smart home related stuff:
- Vacuum cleaner (WLAN 2.4GHz)
- Smart-TV (cable)
- Bedside lamp (WLAN 2.4GHz)
- 2x Raspberry pi for home automation (cable)
- 1x Raspberry pi for home automation (WLAN 2.4GHz)
- Roller Blind (WLAN 2.4GHz)
Now currently, all of those devices are in the same network and can communicate with each other. What I would like to achieve is a separation of the devices smart-home section from the rest of the devices. Guests who visit my home and want to use wifi should also go to the smart home section.
Will this be possible with the above setup of router/access point/switch using tagged VLANs? How can I achieve this? And if I have the devices separated, how would it be possible to connect e.g. from the laptop to the home automation raspi? Of course I need to do this from time to time to make configuration changes. Also, the GUI must be accessible to control the home automation. Can this be achieved by some sort of extra routing?
-
yes sg-1100 and unifi wlan are capable of that but your switch need to be smart/managed to be able to correctly manage vlan
-
@soul710 What 16-port ethernet switch do you have? Make and model, or a link to a webpage with some specs?
Jeff
-
Okay so the switch is a HP 1410-16G switch (J9560A).
And I forgot to mention that I have a second switch (HP 1410-8G) in the living room which connects the smart TV and the home automation pi (and is connected to the other switch).
So, as it seems, those are unmanaged switches. Thus I would need to replace the two switches with managed switches in order to make all this work?
-
@soul710 said in Questions regarding VLANs:
So, as it seems, those are unmanaged switches.
Yes if you want to properly do vlans, your switches, your router and your AP need to support them.
Your router can do them, and your AP can do them - so you just need switch or switches.. You can use a dumb switch downstream of smart switch, as long as all the devices on the dumb switch will be on the same vlan.
-
@johnpoz said in Questions regarding VLANs:
Yes if you want to properly do vlans, your switches, your router and your AP need to support them.
Your router can do them, and your AP can do them - so you just need switch or switches.. You can use a dumb switch downstream of smart switch, as long as all the devices on the dumb switch will be on the same vlan.Ah okay, so in the first step I can just replace the 16 port switch. How would I then go about configuring all this? How does it work?
And can you recommend a good switch for this job? Should be 16 port, but maybe shouldn't be that expensive.
-
@soul710 said in Questions regarding VLANs:
maybe shouldn't be that expensive.
And what is that to you? 200 might be expensive for some, while 2k is not for others.. How expensive something is relative... What is your budget for this 16 port switch?
-
Okay well I think I don't really want to spend more than 200€. Is that realistic?
-
You could find something that does vlans at that price point I would think.. All comes down to feature set, ports, poe or not, etc..
I have a cisco sg300-28 port that was under $200 when I picked it up back in 2017..
Yeah never know with currency conversions, etc.. But I have the little brother to this dgs-1100 (8 port model) and works good for entry level stuff
https://www.amazon.com/D-Link-16-Port-EasySmart-Ethernet-DGS-1100-16/dp/B004M0LFSA
$104 on amazon currently. I would stay away from tplink stuff.. They have issues with vlans on their entry level stuff for sure.. There are many a thread here about it even..
If I needed a switch right now - I would prob go with this cisco sg350-28... $231 - thats a good price..
https://www.amazon.com/Cisco-Sg350-28-28-Port-Gigabit-Managed/dp/B01HYA38CADon't be afraid to buy something with more features than you actually need, or more ports.. You will prob end up using them ;) My 28 ports is full.. Couple of ports open.. And I replaced a 10 port sg300, which I moved to my av cabinet - it also only a couple of ports left.. So don't let 24 ports or even more think its too many ports ;) If your in the market for a 16 port model, prob 48 too many... But I wouldn't shy away from looking at 24 port models if you find a price in your budget.
And you can not have too many features, while you might only want vlan support today - maybe tmrw you want to do some multicast ACLs - I use this feature a lot actually... Freaking noise bucket devices spewing garbage I don't want onto the network ;)
One feature for example like to play with in the 350 line vs my 300 is rspan support.. So while you might think - shit that is pretty much everything I could ever need it todo.. You never know what tmrw might bring in something you want to do.. So not like you can have too many features of your switch ;)
The good thing is - any smart/managed switch can just be dumb as well.. Just because it can do something doesn't mean you have to use it or configure it, etc. Pretty much any smart/managed switch will just be dumb if you just turn it on and plug shit in... Then you can play with the features when you get around to it.
-
Okay so I can get both a SG300/SG350 with 18 Ports at around 200€, which would be okay. However those things a pretty big.
I could also get a Catalyst 2960L-16TS-LL (WS-C2960L-16TS-LL) for about the same price.

-
The sg300 is end of sale, still supported til 2023... But would get a 350.. What 18 port model you looking at - there are no such models.. You mean the 28 port, must of been a typo?
But sure that line works too, won't do L3 I don't think like that 300 or 350 can do... If in the same ball park of price - then yeah you have to compare feature sets, etc..
Keep in mind that once you move to Catalyst, your going to have to have a account to get downloads of firmware updates. Which you may need to have support on, etc.
The SG line software is just download for free... Now when I log in with my cisco account, I can download it - but we also have support contracts with cisco... Would be something I would verify before pulling the trigger on the Catalyst line..
-
300/350 are only 10 port or 28 port or more, must be a typo
afaik catalyst's IOS are free to download, i have a couple of old and now out of service 2960 plus that i upgraded without contract
i was able to download c2960l-universalk9-mz.152-7.E1.bin with only a simple cisco account -
@kiokoman said in Questions regarding VLANs:
afaik catalyst's IOS are free to download
I think once you register it yes, but would be something to validate for sure.. For example I have no support contract for wlan controllers. And I can not download them..
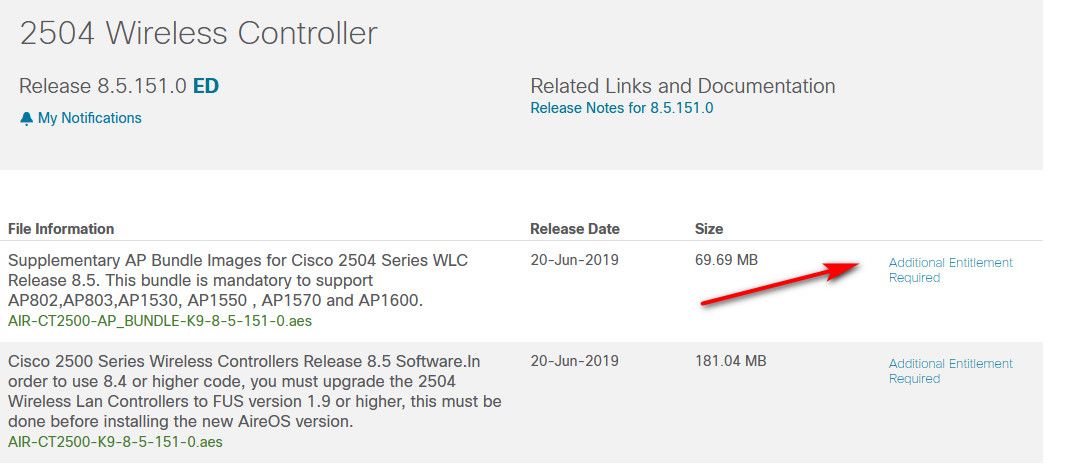
Would be something I would verify... smartnet not cheap ;)
-
Ok so the SG350 actually has 20 ports, its 18xRJ45 + 2xRJ45/SFP.
https://www.amazon.de/dp/B07BBCSGT6?linkCode=xm2&camp=2025&creative=165953&smid=A1AOD6NZ8T40S4&creativeASIN=B07BBCSGT6&tag=geizhals10-21&ascsubtag=7lTUh0cAsZh0thVvBEYFwNow regarding the intial question, in case I need to be able to communicate between 2 VLANs (e.g. my laptop on the "main" VLAN shall be able to access the raspberry pi on the "home automation/GUEST" VLAN) it means I must have a L3 switch which does the routing? Or how is this going to work? Still totally clueless about how the VLAN stuff will function.
-
@soul710 said in Questions regarding VLANs:
it means I must have a L3 switch which does the routing? Or how is this going to work?
If both VLANs are configured in pfSense, it can do the routing.
-
there are 2 way to do it, the first is to configure the vlan inside pfsense and let it manage the routing, this mean that your switch will be configured as layer 2
or you can set the switch as layer 3 and configure the vlan there, but this way pfsense will see all the traffic coming from only one interface and you need to create rules inside the switch.
i prefer the first method when possible -
Okay, maybe for now I'll go for something cheaper and smaller, I think I'll get the D-Link DGS-1210.
But back to the VLAN question, so, how is it going to work? So basically I need 2 VLANs, the guest/home automation one, and the "private" one.
Currently, in my pfsense it looks like this:

I am not entirely sure why there is 3 VLANs, but I remember it was set up like this when I bought the box. Its because the 3 physical ports share 1 unix network interface (mvneta0) or something? I don't know.
How would I then configure the "private" VLAN? Just add a fourth VLAN with some arbitrary ID? How do I make my "private" devices use this VLAN then? In general, how are devices assigned? By Port? MAC address? ... ?
Will the IP-nets be different in the VLANs? Currently, the pfsense is serving as DHCP server for all devices (LAN+WLAN) in the network.
How do I establish a routing from my "private" VLAN (laptop) to the home automation raspberry pi (for management purposes)?
-
If it was set up that way when you bought the box, restore to factory settings and start from scratch. Otherwise you'll find yourself working around whatever it was set up for by the original owner. Figure out what you want and then configure for that. Do you have a need for LAGG? That's link aggregation and it must be configured at both ends. Do you need that?
-
@JKnott said in Questions regarding VLANs:
If it was set up that way when you bought the box, restore to factory settings and start from scratch.
There is no original owner. It was like that when I bought the box. And I remember that I had to reset it a couple of times to make some stuff work, and I ended up having a really hard time restoring those very VLAN settings on the console prompt / pfsense menu in order to make the box work again.
Still, I don't know why this is needed. However, while the box has 3 physical ethernet ports, it seems to have only 1 network interface, so that might be the reason. Again I am not an expert here, and my previous pfsense appliance did not have this (it had 3 distinct network interfaces).This is how it looks like:
[2.4.4-RELEASE][root@aeon.localdomain]/root: ifconfig -a mvneta0: flags=8a43<UP,BROADCAST,RUNNING,ALLMULTI,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=bb<RXCSUM,TXCSUM,VLAN_MTU,VLAN_HWTAGGING,JUMBO_MTU,VLAN_HWCSUM> ether xx:xx:xx:xx:xx hwaddr xx:xx:xx:xx inet6 xxx::xxxx:xxxx:xxxx%mvneta0 prefixlen 64 scopeid 0x1 media: Ethernet 1000baseT <full-duplex> status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> enc0: flags=41<UP,RUNNING> metric 0 mtu 1536 groups: enc nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> lo0: flags=8049<UP,LOOPBACK,RUNNING,MULTICAST> metric 0 mtu 16384 options=600003<RXCSUM,TXCSUM,RXCSUM_IPV6,TXCSUM_IPV6> inet6 ::1 prefixlen 128 inet6 fe80::1%lo0 prefixlen 64 scopeid 0x7 inet 127.0.0.1 netmask 0xff000000 groups: lo nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> pflog0: flags=100<PROMISC> metric 0 mtu 33160 groups: pflog pfsync0: flags=0<> metric 0 mtu 1500 syncpeer: 224.0.0.240 maxupd: 128 defer: on syncok: 1 groups: pfsync mvneta0.4090: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=3<RXCSUM,TXCSUM> ether xx:xx:xx:xx:xx inet6 xxx::xxxx:xxxx:xxxx%mvneta0.4090 prefixlen 64 scopeid 0xa inet 192.168.0.3 netmask 0xffffff00 broadcast 192.168.0.255 groups: vlan vlan: 4090 vlanpcp: 0 parent interface: mvneta0 media: Ethernet 1000baseT <full-duplex> status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> mvneta0.4091: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=3<RXCSUM,TXCSUM> ether xx:xx:xx:xx:xx inet6 xxx::xxxx:xxxx:xxxx%mvneta0.4091 prefixlen 64 scopeid 0xb inet 10.0.0.1 netmask 0xffffff00 broadcast 10.0.0.255 inet 10.10.10.1 netmask 0xffffffff broadcast 10.10.10.1 groups: vlan vlan: 4091 vlanpcp: 0 parent interface: mvneta0 media: Ethernet 1000baseT <full-duplex> status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL> mvneta0.4092: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500 options=3<RXCSUM,TXCSUM> ether xx:xx:xx:xx:xx inet6 xxx::xxxx:xxxx:xxxx%mvneta0.4092 prefixlen 64 scopeid 0xc groups: vlan vlan: 4092 vlanpcp: 0 parent interface: mvneta0 media: Ethernet 1000baseT <full-duplex> status: active nd6 options=21<PERFORMNUD,AUTO_LINKLOCAL>192.168.0.x is going to the cable modem, 10.0.0.x is going to the LAN switch. The last interface/port (OPT) is unused.
@JKnott said in Questions regarding VLANs:
Do you have a need for LAGG? That's link aggregation and it must be configured at both ends. Do you need that?
I didn't know so far what that is, googling for it, it feels to me that this is nothing I would need.
[edit] So I found this:
https://docs.netgate.com/pfsense/en/latest/book/vlan/pfsense-vlan-configuration.html
and this:
https://docs.netgate.com/pfsense/en/latest/book/vlan/switch-vlan-configuration.htmlMaybe I'll try those instructions and see how far I get.
-
@soul710 said in Questions regarding VLANs:
Maybe I'll try those instructions and see how far I get.
Determine your requirements, then worry about configuration. You mentioned you need 2 VLANs. I assume that's on top of the native LAN, so you'd have 3 subnets. That's easy enough for pfSense to handle. You just create the 3 interfaces as required and configure addresses, DHCP, etc. for each one. Then you worry about routing & filter rules.