captive portal and no internet after authentication.
-
@roundcube222 your problem seems related to your firewall rules, not to the captive portal
The logs you are sharing are (i guess) the logs of the WAN interface (because you didnt enabled logging on other rules).
Could you please check in the firewall rules of the LAN interface that you allowed TCP 80 and TCP 444 ?
there is an implicit rule "block everything that has not been previouslty allowed" applied under all rules on each interface. Therefore you need to allow these two ports if you want to be able to access the web from your LAN.
You should also whitelist other ports (such as the one for HTTP3/QUIC and Websocket) -
@free4
already in my LAN rules i input
ALLOW from ANY to ANYso there is no blockage from the portal firewall.
-
@Gertjan
ipconfig/all shows as followConnection-specific DNS Suffix . : localdomain
Description . . . . . . . . . . . : VMware Accelerated AMD PCNet Adapter
Physical Address. . . . . . . . . : 00-0C-29-F8-16-40
Dhcp Enabled. . . . . . . . . . . : Yes
Autoconfiguration Enabled . . . . : Yes
IP Address. . . . . . . . . . . . : 192.168.1.107
Subnet Mask . . . . . . . . . . . : 255.255.255.0
Default Gateway . . . . . . . . . : 192.168.1.23
DHCP Server . . . . . . . . . . . : 192.168.1.23
DNS Servers . . . . . . . . . . . : 192.168.1.23
Lease Obtained. . . . . . . . . . : Monday, February 24, 2020 8:27:01 AM
Lease Expires . . . . . . . . . . : Monday, February 24, 2020 10:27:01 Amy lan/firewall static ip is 192.168.1.23 and my client got DHCP 192.168.1.107
After authentication, still the firewall is blocking 192.168.1.107 , i disconnected portal client and connect them again, but same problem that the firewall is blocking 192.168.1.107
here is the log from firewall as follow
Feb 24 06:53:08 LAN Default deny rule IPv4 (1000000103) 192.168.1.107:1156 172.217.18.228:443 TCP:Ai do not know why the firewall is blocking my captive portal clients, although in LAN FIREWALL rules i added rule ACCEPT from ANY to ANY and protocal ALL.
this is very strange and i can not find a solution or reason for the issue...
Maybe the rules i pasted in my earlier post can help you to identify the problem ?
any ideas to solve this ?
-
@roundcube222 said in captive portal and no internet after authentication.:
here is the log from firewall as follow
Feb 24 06:53:08 LAN Default deny rule IPv4 (1000000103) 192.168.1.107:1156 172.217.18.228:443 TCP:AWhen you look at this rule, you can see the rule number : 1000000103
Look up this rule number (for easy check : open the file that is loaded into 'ip' which you can find here : /tmp/rules.debug) and you'll be in for a surprise.#--------------------------------------------------------------------------- # default deny rules #--------------------------------------------------------------------------- block in inet all tracker 1000000103 label "Default deny rule IPv4"so you're hitting the default build in block all rule, valid for ALL interfaces.
So, again, what is/are your LAN (== Captive portal interface ??) rules ?
Please copy paste the entire image of your rules (use a capture tools, Window<s/MAC/Linux/whatever have one build in) and paste (Ctrl-V) it in your message.Like :
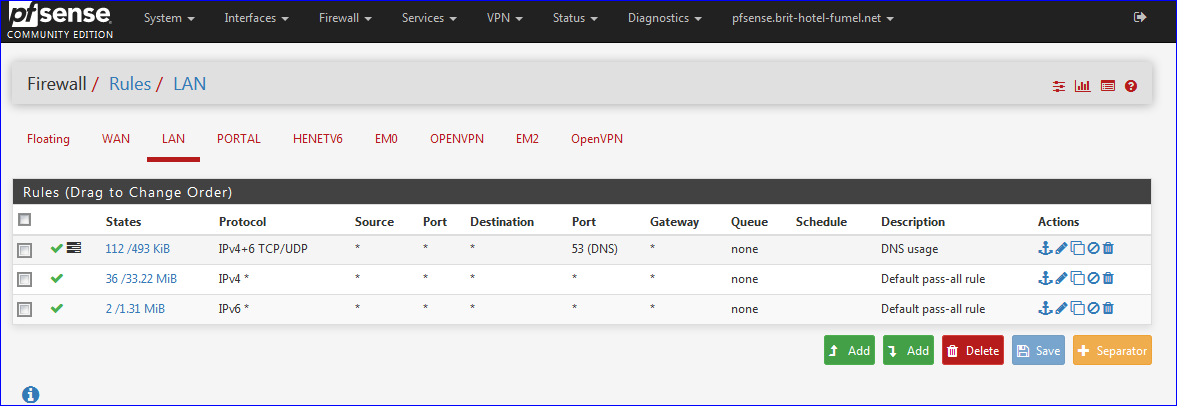
If there are no pass rules that match your traffic, the default 'hidden' block all rule kicks in.
Any floating rules ?
-
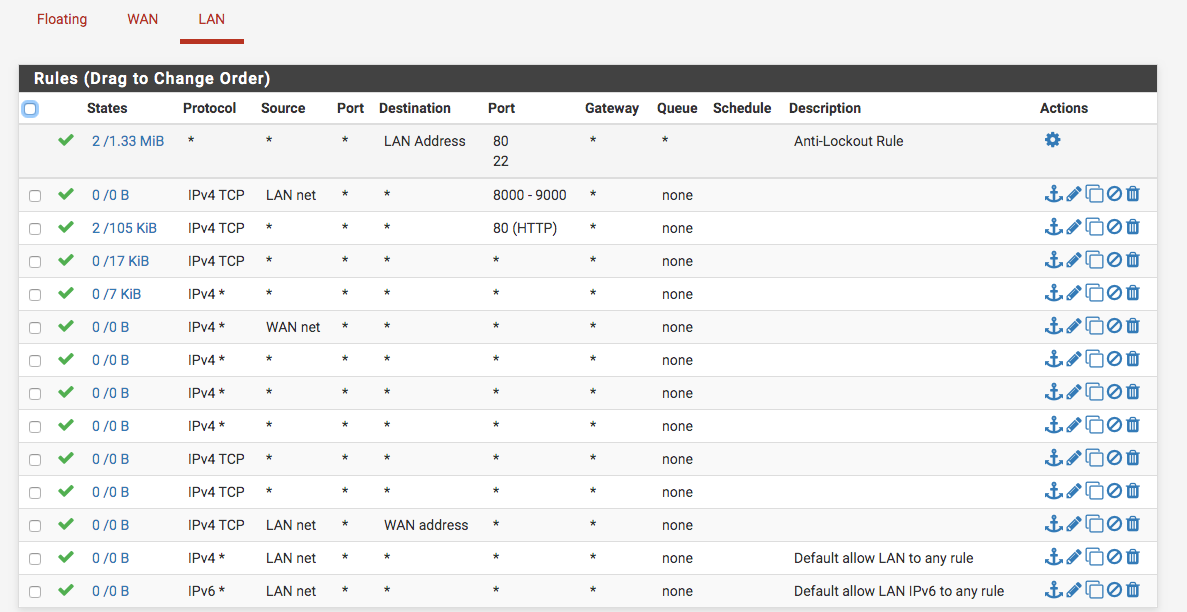
this is my LAN firewalland here is my FLOATING
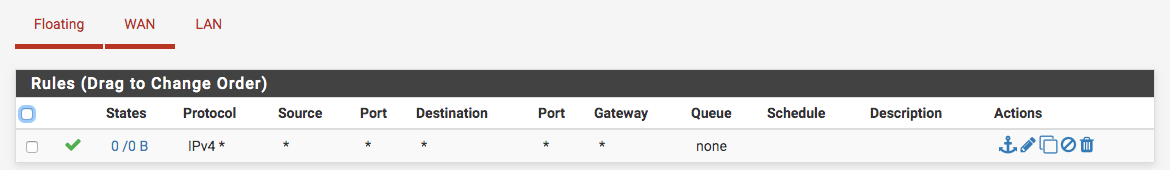
i already added in all PASS (ANY ) IN and OUT
what is the problem.... ?
-
@roundcube222 said in captive portal and no internet after authentication.:
what is the problem.... ?
Well, ok, the pass rules are not missing. You've an entire collection of, them.
em0 = WAN
em1 = LAN = captive portal - right ?I can't figure out why IPv4 is being blocked on your LAN interface == captive portal interface.
This is pfSense 2.4.4-p3, right ?
Who is 192.168.201.147 ?
I advise you to re install clean.
Use the video as shown above to make the captive portal work.
Keep the LAN as default. Do not change DNS / do not add change any firewall rules.
When the portal works, start adding your changes.Btw : your Floating rule is scary ...
edit : Your using a VM, right ?
-
Correct Em0 - WLAN
and EM1 = LAN = Captive portal
This is pfsens 2.4.4 correct
and i am using VMware correct
192.168.201.147 is WAN IPAny recommendations , other than re-installing again ?
-
You talk about a WLAN interface. is that another LAN or the WAN ?
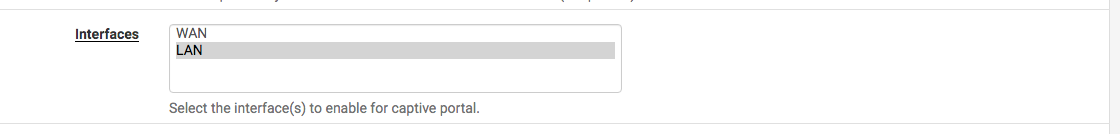
You selected in the captive portal the em1 interface = LAN , right ?
Here Services Captive > Portal > [ZONE] > Configuration:
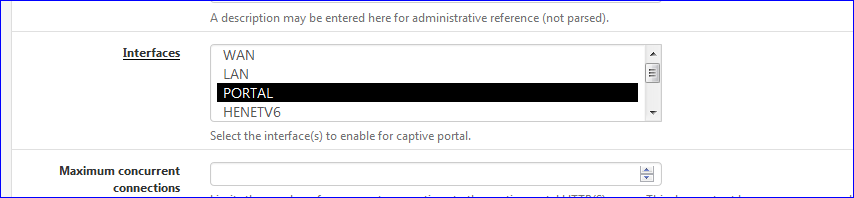
edit : Yep, you did.
em1 2100 621 61110 1582482492Make a backup of your config - and re install.
Set up the portal as explain by the video.
And please, tell us what you found / was different, when done. -
no we used the captive portal on LAN as per this screen shot.
I have re-installed a clean copy.. and still the problem their.. my authenticated client can not browse any sites (they can only ping hosts and make dns lookups)
Any ideas??
-
I tend to say that this is still valid these days : https://www.youtube.com/watch?v=qb5TDpihnq4
-
@Gertjan said in captive portal and no internet after authentication.:
https://www.youtube.com/watch?v=qb5TDpihnq4
do i have to create a VLAN for the captive portal ?
only can i create the captive portal on the LAN ??
-
@roundcube222 said in captive portal and no internet after authentication.:
do i have to create a VLAN for the captive portal ?
only can i create the captive portal on the LAN ??It can be activated on the LAN.
Advisable is use a dedicated, other LAN (OPT1) interface. This way, managning is waaaaaaaay more simple.
VLAN's should be be possible also, never tried it myself.
But you should use a device (A VM in your case) with at least 3 real physical NIC's so you respect the golden rule : keep it simple. Simple things also tend to work right away. Afterwards, you can make it complicated again ... ^^Also : per definition : LAN is a trusted network where you connect only devices you trust.
On the captive portal you put devices that you no not trusted. -
@Gertjan
i tired every thing ... my authenticated users can not access internet,,,i have pasted all the firewall rules
Can please one of the admins help me..............
-
did any one tried to use captive portal on LAN ? maybe it is not working because i set the portal on LAN ?
IPFW already added my authenticated clients to the allow list. so why still they can not access internet and they can just ping clients and resolve domains ?
can any one have any ideas what is wrong ? i already pasted my firewall rules in the post which allow ANY from/TO.
The problem only happen when i enable captive portal. if i disable captive portal, then my clients can access internet without any problems.
Maybe there is some bug when using the captive on LAN ?
-
@roundcube222 said in captive portal and no internet after authentication.:
Maybe there is some bug when using the captive on LAN ?
Using 2.4.4-p3 ? That explains your issue ? Then why all my clients (hotel Wifi network) are connected to the Internet using the very same code ?
Between your system, and min, only the settings are different.
The system - the code - is the same.My guide line was the video mentioned above.
Your issue isn't probably Captive portal related : Your LAN firewall rules are not taken in account anymore when you activate the captive portal : the default terminating Block all rules is hit, like the other, your GUI rules, do not exist any more.
I can't explain that.Any ideas, @free4 ?
-
@Gertjan
Maybe this bug happens only if you make the portal on the LAN ?While your portal is on the WiFi interface ?
-
@roundcube222 said in captive portal and no internet after authentication.:
While your portal is on the WiFi interface ?
Any other NIC on pfSense not being declared as "WAN" will get called OPT1, OPT2, OPT3 and is basicly a LAN with one 'minor' exception : no default PASS rule, so it blocks by default (with another exception : they will pass DHCP related stuff) etc. You can rename them, if you which.
Like "WiFi " or, "Portal" as I did.I can activate a portal on my LAN if I want to - for testing purposes.
I'll do that right now, and report back, give me 5 minutes.back.
Well, that was impressive. I really managed to break the inter Internet connection for all my LAN devices. Activating a portal is very radical.
The easy of setting up a basic the captive portal is impressive : A click, give it a name and description, another click for the save and another for the activation (somewhat in that order). I used the local build-in user data base (already populated with some users which have a granted portal access ).
Then saving all this, I closed my browser.Waited 10 seconds and fired it up again. Immediately I was present with a message :

clickIt's Firefox, using the french language saying to me that I need to connect using an account if I want to access the Internet. Hit the button on the right gave me direct access to the default blue pfSense captive portal login page. Never saw that one before ! I'm normally use my own, branded login page(s).
When I entered a user (= admin), allowed to use the portal, and the password, I saw the small word "Succes" in the upper left corner. After that, going to https://ww.google.com worked just fine.
So, yes, a captive portal on LAN works just fine, although very not useful for a basic company network.
On what device are you running pfSense ?
-
-
@roundcube222 said in captive portal and no internet after authentication.:
I am using VMware with 2 NIC
Ah.
That just doubles the list with possible issues. And isn't something you should not omit to mention when asking question.
It , a VM, can works of cours,I use a pfSense from a Hyper-V VM, build into Windows Pro right out of the box. I had some virtual NIC issues at first (sound familiar ?), though, at first, mostly because I didn't RTFM first.
If you have a spare drive - some small 10+ Gbytes disk size will do, take the actual disk out of your PC, install the spare (to be emptied) disk into your system, and install pfSense bare-bone, from scratch.
It's worth a try.Because you know it : it's not pfSEnse, your issue.