Ubuntu failing to update with Suricata enabled.
-
Howdy, I have yet another question on blocking lists and the likes. When not in my network with suricata, I can run an update and get something like the following:
Reading package lists... Done E: Could not get lock /var/lib/apt/lists/lock. It is held by process 1616 (packagekitd) - open (11: Resource temporarily unavailable) N: Be aware that removing the lock file is not a solution and may break your system. E: Unable to lock directory /var/lib/apt/lists/ Reading package lists... Done Building dependency tree Reading state information... Done Calculating upgrade... Done The following packages will be upgraded: signal-desktop-beta unattended-upgrades 2 upgraded, 0 newly installed, 0 to remove and 0 not upgraded. Need to get 98.9 MB of archives. After this operation, 217 kB of additional disk space will be used. Do you want to continue? [Y/n] y Get:1 http://us.archive.ubuntu.com/ubuntu eoan-updates/main amd64 unattended-upgrades all 1.14ubuntu1.2 [47.6 kB] Get:2 https://updates.signal.org/desktop/apt xenial/main amd64 signal-desktop-beta amd64 1.32.0-beta.4 [98.8 MB] Fetched 98.9 MB in 4s (26.9 MB/s) Preconfiguring packages ... (Reading database ... 195957 files and directories currently installed.) Preparing to unpack .../unattended-upgrades_1.14ubuntu1.2_all.deb ... Unpacking unattended-upgrades (1.14ubuntu1.2) over (1.14ubuntu1.1) ... Preparing to unpack .../signal-desktop-beta_1.32.0-beta.4_amd64.deb ... Unpacking signal-desktop-beta (1.32.0-beta.4) over (1.32.0-beta.3) ... Setting up unattended-upgrades (1.14ubuntu1.2) ... Replacing config file /etc/apt/apt.conf.d/50unattended-upgrades with new version Setting up signal-desktop-beta (1.32.0-beta.4) ... Processing triggers for mime-support (3.63ubuntu1) ... Processing triggers for hicolor-icon-theme (0.17-2) ... Processing triggers for gnome-menus (3.32.0-1ubuntu1) ... Processing triggers for systemd (242-7ubuntu3.7) ... Processing triggers for man-db (2.8.7-3) ... Processing triggers for desktop-file-utils (0.24-1ubuntu1) ... All snaps up to date.However, running this while suricata is blocking ends up resulting in a lot of failed updates:
Hit:3 http://us.archive.ubuntu.com/ubuntu eoan InRelease Ign:1 https://ppa.launchpad.net/peek-developers/stable/ubuntu eoan InRelease Hit:5 http://us.archive.ubuntu.com/ubuntu eoan-updates InRelease Ign:2 https://ppa.launchpad.net/thopiekar/miraclecast/ubuntu eoan InRelease Hit:6 http://us.archive.ubuntu.com/ubuntu eoan-backports InRelease Hit:8 https://updates.signal.org/desktop/apt xenial InRelease Hit:9 http://us.archive.ubuntu.com/ubuntu eoan-security InRelease Err:4 https://ppa.launchpad.net/peek-developers/stable/ubuntu eoan Release Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. The name in the certificate does not match the expected. Could not handshake: Error in the certificate verification. [IP: 91.189.95.83 443] Err:7 https://ppa.launchpad.net/thopiekar/miraclecast/ubuntu eoan Release Certificate verification failed: The certificate is NOT trusted. The certificate issuer is unknown. The name in the certificate does not match the expected. Could not handshake: Error in the certificate verification. [IP: 91.189.95.83 443] Get:10 https://gitlab.com/paulcarroty/vscodium-deb-rpm-repo/raw/repos/debs vscodium InRelease [3,828 B] Reading package lists... Done E: The repository 'http://ppa.launchpad.net/peek-developers/stable/ubuntu eoan Release' no longer has a Release file. N: Updating from such a repository can't be done securely, and is therefore disabled by default. N: See apt-secure(8) manpage for repository creation and user configuration details. E: The repository 'http://ppa.launchpad.net/thopiekar/miraclecast/ubuntu eoan Release' does not have a Release file. N: Updating from such a repository can't be done securely, and is therefore disabled by default. N: See apt-secure(8) manpage for repository creation and user configuration details. Reading package lists... Done Building dependency tree Reading state information... Done Calculating upgrade... Done 0 upgraded, 0 newly installed, 0 to remove and 0 not upgraded. All snaps up to date.I can't see any entries in alerts for the IP's or domains mentioned in the previous update lines. Is there something I'm missing? Has anyone else seen this issue? Thank you!
-
Are you sure Suricata is the cause of this? The errors talk about untrusted certificates. Do you have any other packages installed such as Squid, Squidguard or pfBlocker?
Suricata will put any IP addresses that alert and result in block on the ALERTS tab. Blocked IP addresses can be viewed in the BLOCKS tab.
-
squid is running on there too, only in http mode. I imagine I'd need do something there to get that fixed.
-
@strongthany said in Ubuntu failing to update with Suricata enabled.:
squid is running on there too, only in http mode. I imagine I'd need do something there to get that fixed.
Based on the errors I saw in your posted images, my suspicions are with Squid. Suricata would simply add an IP to the blocked list and also log it on the ALERTS tab, but it would not fiddle with certs in any way.
-
When I want to update ubuntu or download the driver for nvidia video card, I have to turn off suricata before I can do it. I'm using default rules in snort 3. I don't use squid.
-
@convoi said in Ubuntu failing to update with Suricata enabled.:
When I want to update ubuntu or download the driver for nvidia video card, I have to turn off suricata before I can do it. I'm using default rules in snort 3. I don't use squid.
There is no Snort 3 package for pfSense, so what are you talking about?
-
@strongthany said in Ubuntu failing to update with Suricata enabled.:
Has anyone else seen this issue?
What Bill also mentions is probably Squid, given the ALERT tab...
but...
just for the sake of curiosity:I used to have problems with these rules, so they are suppressed:
(but this would also appear on the ALERT tab, so it's just interesting)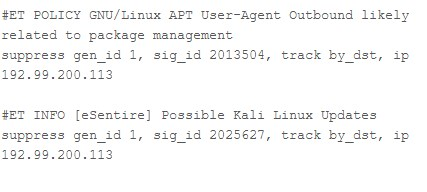
One is only an ET INFO rule, so it is not relevant
-
I have the same issue apt-get doesn't work with Suricata enabled. It's in my firewall logs. It places the server IP's needed in the snort2c table. I don't know how to set pfsense so it allows Ubuntu updates.
-
@mxczxakm said in Ubuntu failing to update with Suricata enabled.:
apt-get doesn't work with Suricata enabled. It's in my firewall logs. It places the server IP's needed in the snort2c table.
Hi,
Delete the entry (es) from snort2c and disable the rule or rules which causes...this

[https://doc.emergingthreats.net/bin/view/Main/2013504](link url)
as an example:
