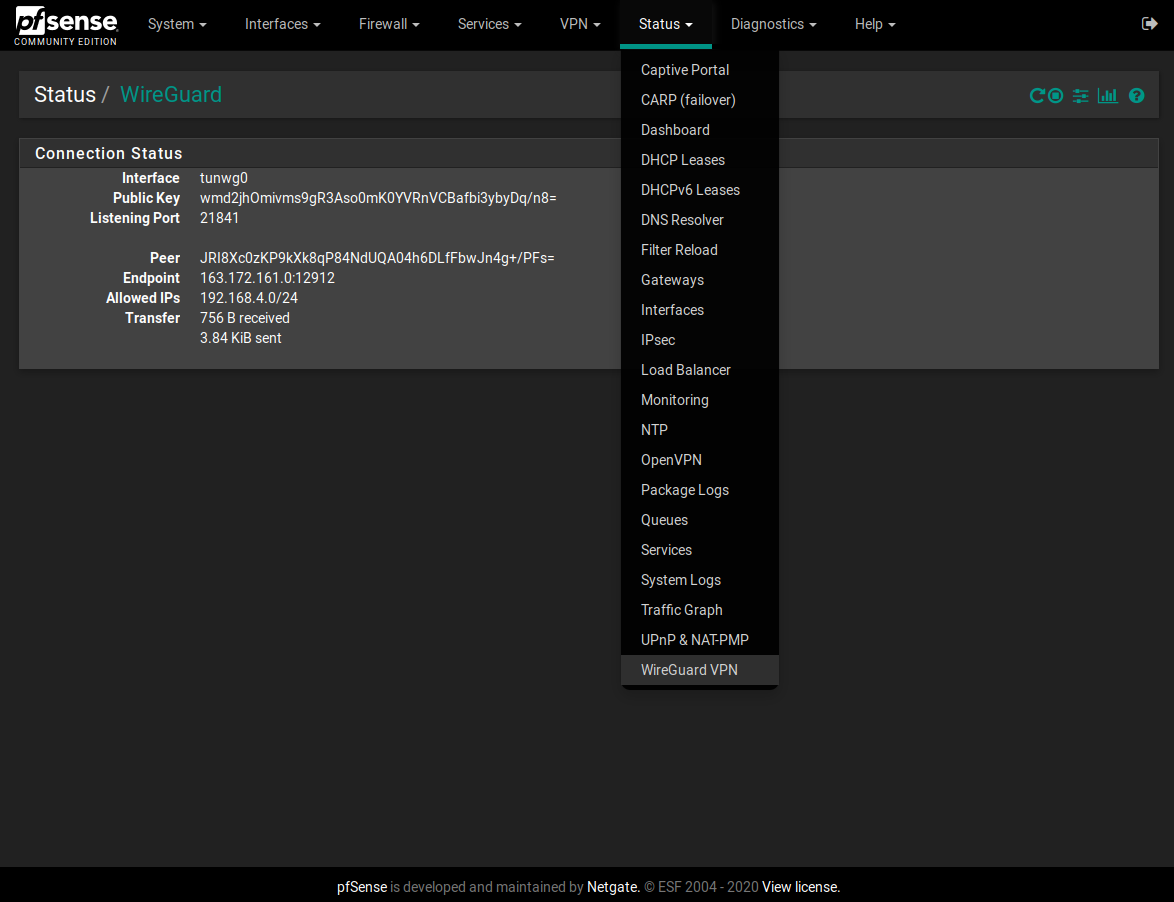
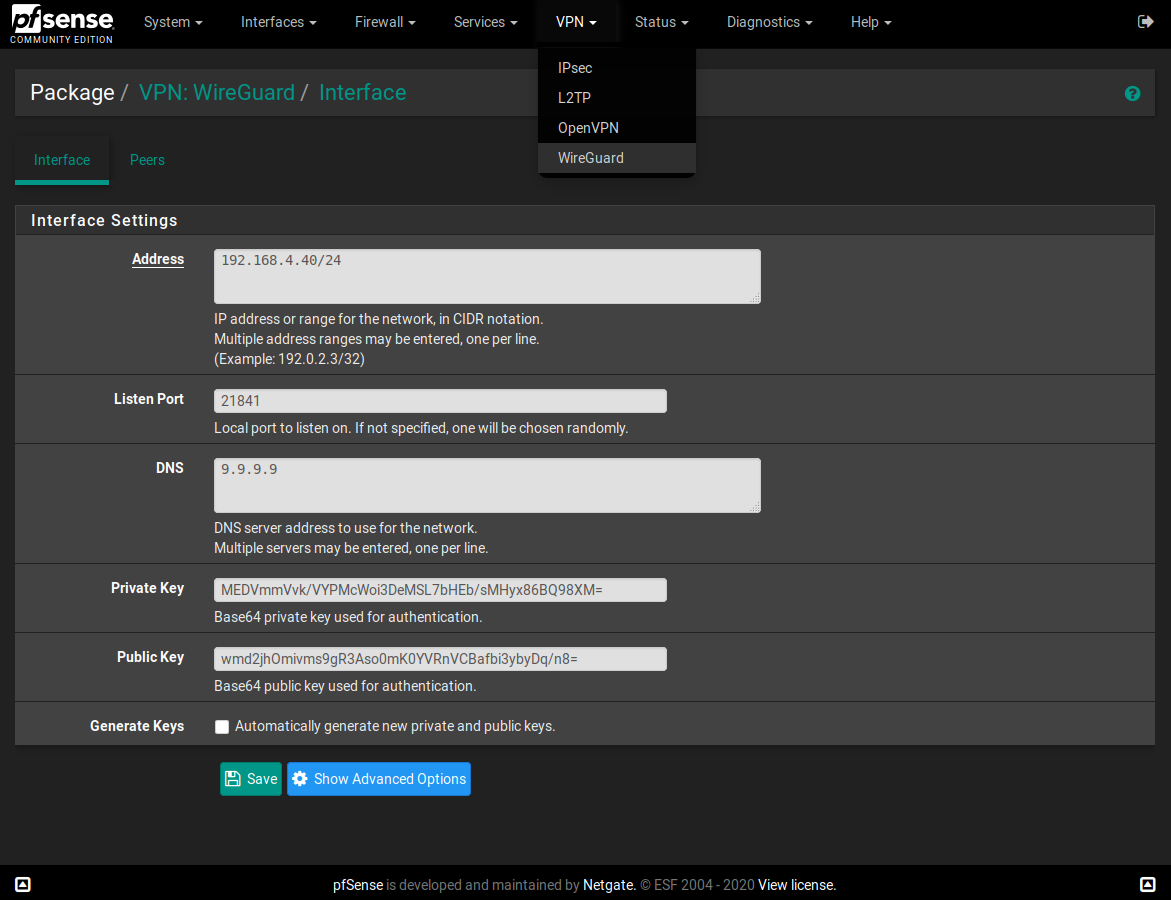
I made a WireGuard package for pfSense
-
OK, finally did a comparision....... I know WG is not in kernel on freebsd/pfsense yet!
Server Xeon E5-2667v2 (8x3.3Ghz turbo 4.0Ghz) pfsense running in VM on ESXi with 2 cores.
Pfsense openvpn 650Mbit (cpu 60%)
Pfsense Wireguard 650Mbit (cpu 80%)
Vyos Wireguard 900Mbit (cpu 65%)Symmetrical 1Gbit FIber Internet.
-
-
Thanks for the suggestions everyone, I'll give them a try and report back.
Edit
No dice.
I tried with the /30 and 192.168.16.1 & 16.2, and it got me the same result as the /31. Couldn't ping either endpoint from the other, and on the pfsense box pinging its own tunnel address went through the tunnel and back again.
Tried the /32s with the same addresses above and that didn't even allow the pfSense box to ping itself. Something is still strange with this setup.
Although as a sidenote, I just went and checked some of the other debian -> debian wireguard links I have set up the same way, and I actually can't ping their endpoint IPs directly either. But, those tunnels are still routing my subnet just fine so I'm thinking that might not be the root cause of my routing issues.
-
@xayide I have an older VMware installation and get the following.
OpenVPN 130 MBps
Wireguard 205 MbpsPFSense isn't my primary firewall, but I use it when I want to be anonymous. (Load balanced between OpenVPN/Wireguard on the VMware and hardware PFSense.) A little weird setup, but I need some projects...
-
So does anyone else use wireguard as a gateway in pfSense for policy-based routing?
I believe my testing so far has concluded that this is not possible. pfSense just ignores any firewall rules that specify the wireguard interface as the gateway.
-
@papkee As I mentioned earlier in this thread. I need to specify the IP adress for Wireguard as IP address on the gateway. It is dynamic as default and cannot be changed in the UI. I opened the configuration in text-mode and changed IP to the /32-address and it works.
-
@papkee I'm using exactly as a gateway since weeks, without problems.
You can create a new gw on System \ Routing \ Gateways and use the ip address you get from your wg provider as gateway ip.
-
@dubatech anyone have a guide how to set up a working "compiling environment"? I would like to be able to compile packages for FreeBSD 12.1, but I fail to do that. My idea was to set up a working environment for that and then produce a package for PFSense 2.5 ...
-
@Talisker I'm sorry, I really don't know if there is a guide for doing that.
Anyway, I don't know if you've tried but I set up the wireguard gateway using the Advanced option "Use non-local gateway".This gave me the ability to avoid using IP/32 received from Mullvad.
This is the gateway configuration:
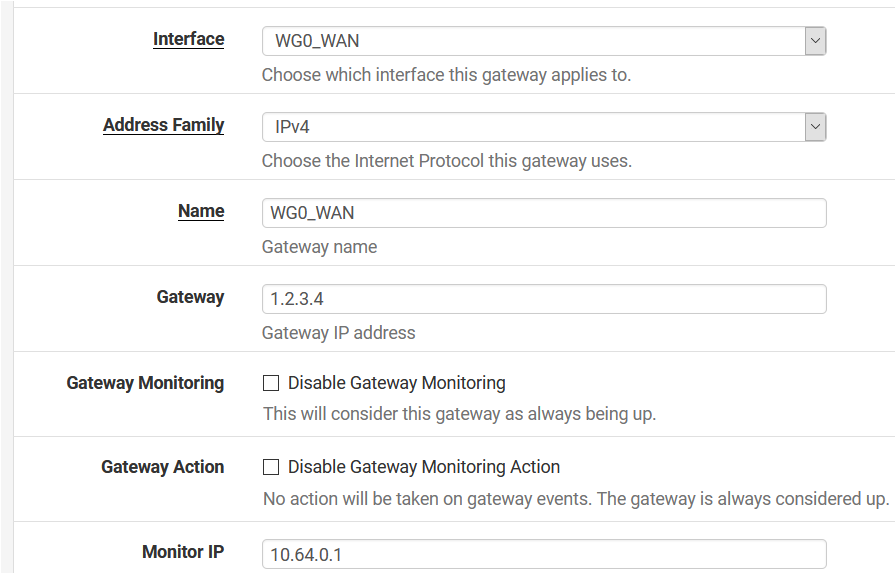
Advanced gateway options:
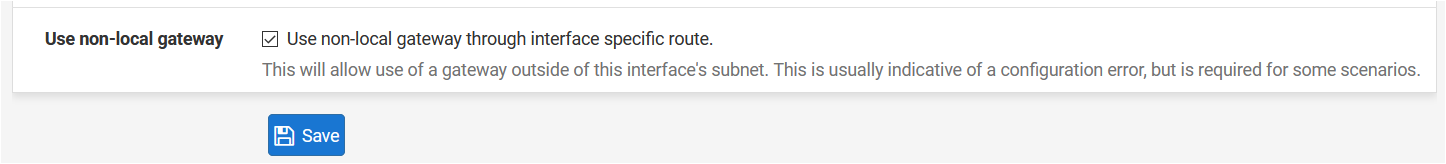
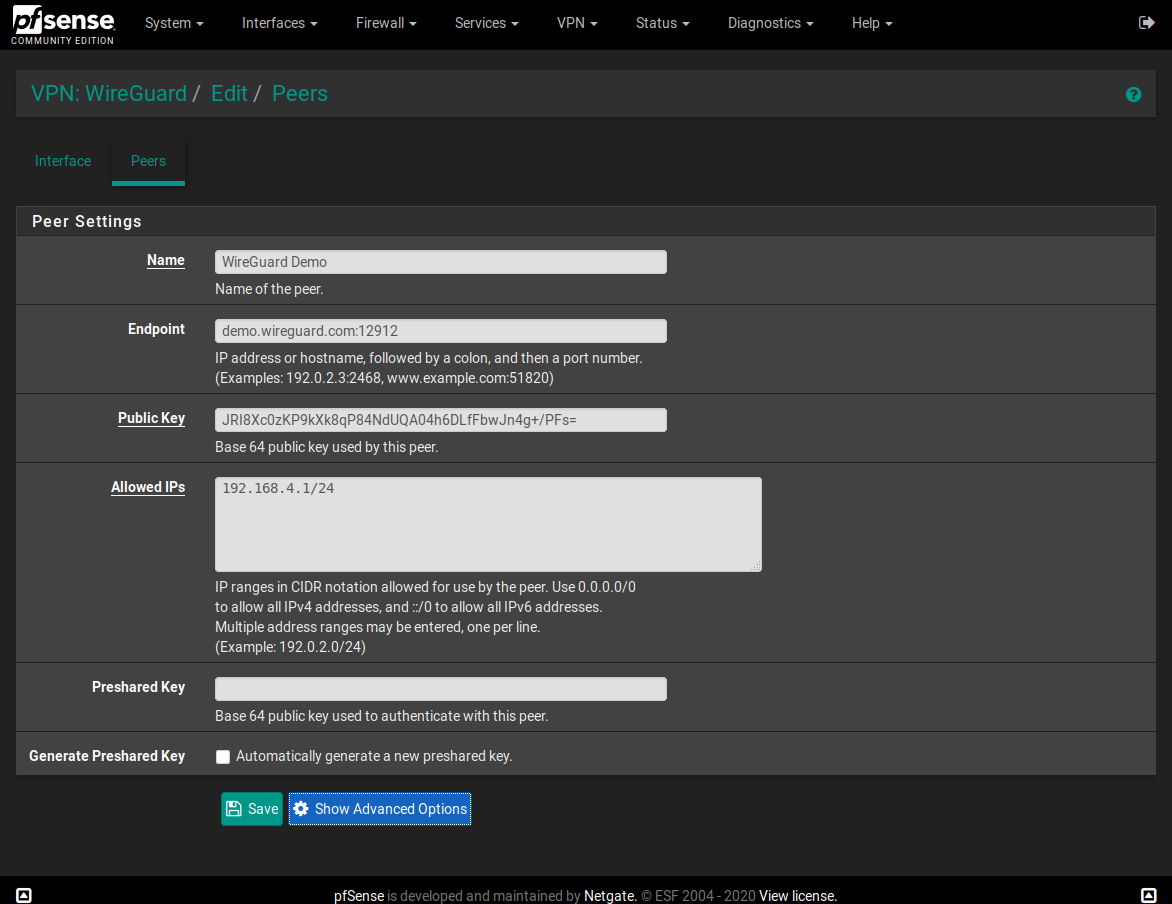
Now, on VPN: WireGuard / Edit / Peers put the following in the "Allowed IPs":

It's working great, without the need to edit config files, setting up the IP/32 obtained by the WireGuard VPN provider, etc...
Really thanks to @Ashus, who helped me with the manual configuration of the tunwg config files to set up multiple wireguard interfaces!
-
@Talisker
Dear @Talisker,
Hello and I hope that you are safe and well. I compiled and built Lucasnz pfSense-pkg-wireguard-1.0.1 For 2.5.0. With all due respect to Ascrod and Ashus, I found Lucasnz to work perfectly on pfSense 2.5.0. For you to get a basic idea as to how to setup a FreeBSD 12 Build Server - see my old tutorial here :https://forum.netgate.com/topic/130832/solution-posted-dns-tls-getdns-stubby-from-pfsense-freebsd-ports
I am attaching a text file with with detailed instructions as how to build Lucasnz pfSense-pkg-wireguard from github for pfsense 2.5.0. - There is also an extra added gift for those who are looking to setup Lucasnz pfSense-pkg-wireguard package on pfSense 2.5.0 Firewall. The reason that I chose Lucasnz to compile on a FreeBSD Build Server ( special thanks to @Talisker for suggestion that it " works " ) is just that. Lucasnz WireGuard for pfsense survives reboots, upgrades - and has no issues with DNS or any such other related problems. I have been running this for a few weeks with no issues. Good Luck - Hope this helps
Lucasnz pfSense-pkg-wireguard-1.0.1 For 2.5.0.txt -
@ubernupe all the changes I've made have been merged into Ascord's version. Possibly best to stick with his version as the primary fork (although currently they match)...
Luke -
@lucas_nz Thanks for your effort, I have a question, currently I have already installed version 1.0.0, how can I upgrade the package to your version (1.0.1) ? is it ok to just install it over the original one or ? Thanks.
-
@a-katib91 I did pkg remove and then pkg add on the new package.
Use "pkg info | grep wireguard" to determine what package to remove and then just add the one you want. You might need to reboot, but I am not sure. -
@ubernupe Fantastic!!!
I set up a server on VMware ESXi and managed to build the package. I downloaded your version and thats the one I am using, but I just wanted to be able to build packages for the 2.5 in case someone makes improvements.@dubatech the weird thing is that in the gateway section, Gateway is set to dynamic and greyed out.
If I manually edit the file I could put in the 1.2.3.4 (as in your example), but I cannot change the IP lates on. Then I get an error message The gateway address 1.2.3.4 does not lie within one of the chosen interface's subnets, which seams strange since 0.0.0.0/0 should be pretty much the whole internet. I thought adding 1.2.3.4/32 as allowed IPs would solve this, but now I found the "Use non-local gateway through interface specific route."
It is working great with 2.4.5, so I am happy with it.2.5 is another story. It starts working when I make adjustments and then dies after a while. From 5 minutes to 30 hours in my case. I have this monitoring where I monitor both OpenVPN and Wireguard from both firewalls. It is always 2.5 with wireguard that stops working and the other three works all the time...
-
@Talisker thanks, that worked.
-
I am having huge problems with the 2.5 version. The tunnel goes up and traffic flows. After a while it just stops. The only solution I have found is to reboot the firewall. Slightly annoying.
However. The 2.4.5 version is working perfectly. No downtime the last two weeks with Lucasnz package.
Btw, I discovered "Tag" and "Tagged" with floating rules in order to prevent traffic to leave the wrong way (directly to internet). PFSense is really weird considering rules and routing.
-
Don't know if happened to someone else, but I've problems with the 4th tunwg interface created.
I've removed tunwg3, then reinstalled @lucas_nz pkg, but nothing: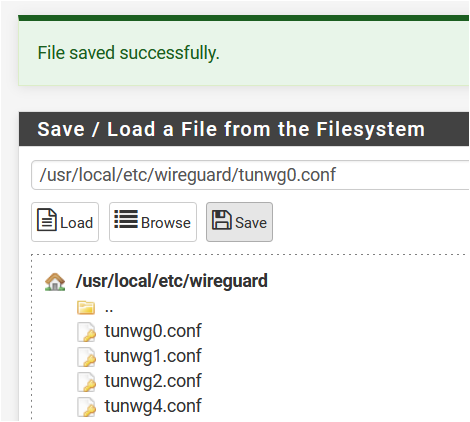
Here is the output of ifconfig:
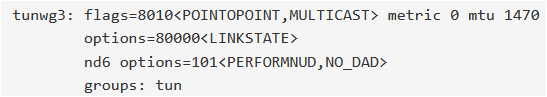
Is there a way to delete it?
I've created a new interface tunwg4 and it works but tunwg3 still visible.I'm on pfSense 2.4.5-RELEASE-p1 and using lucasnz pkg v1.0.1.
Thank you so much
Update: OK, just a reboot fixed the problem!
-
-
@abidkhanhk I followed the how to earlier in this thread.
-
For you and any and all seeking a setup guide - see below :
https://forums.torguard.net/index.php?/topic/1975-ascrod-ashus-pfsense-pkg-wireguard-tutorial-guide/
Also if you read through this thread see here ( my post ) - you can see the attached text for how to build / compile packages - and much more :
https://forum.netgate.com/topic/150943/i-made-a-wireguard-package-for-pfsense/125
Peace -