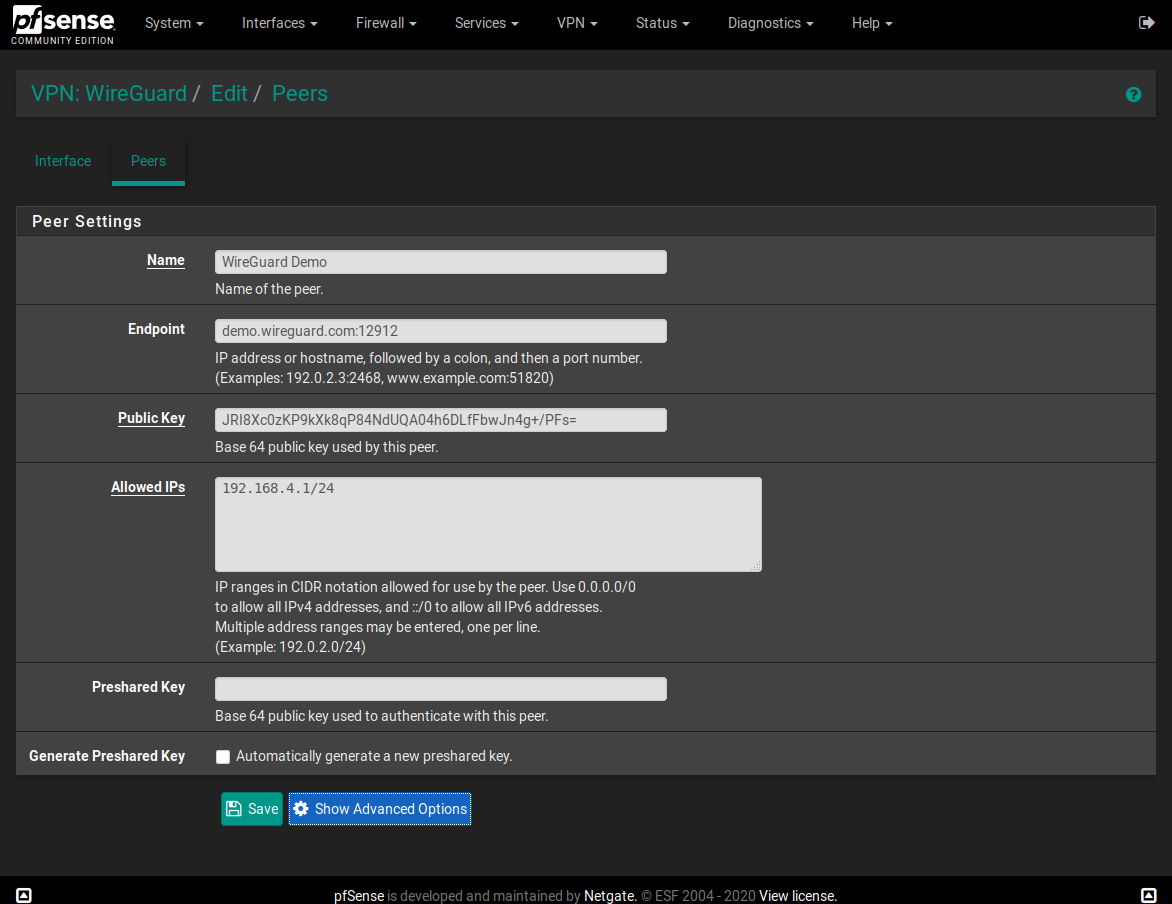
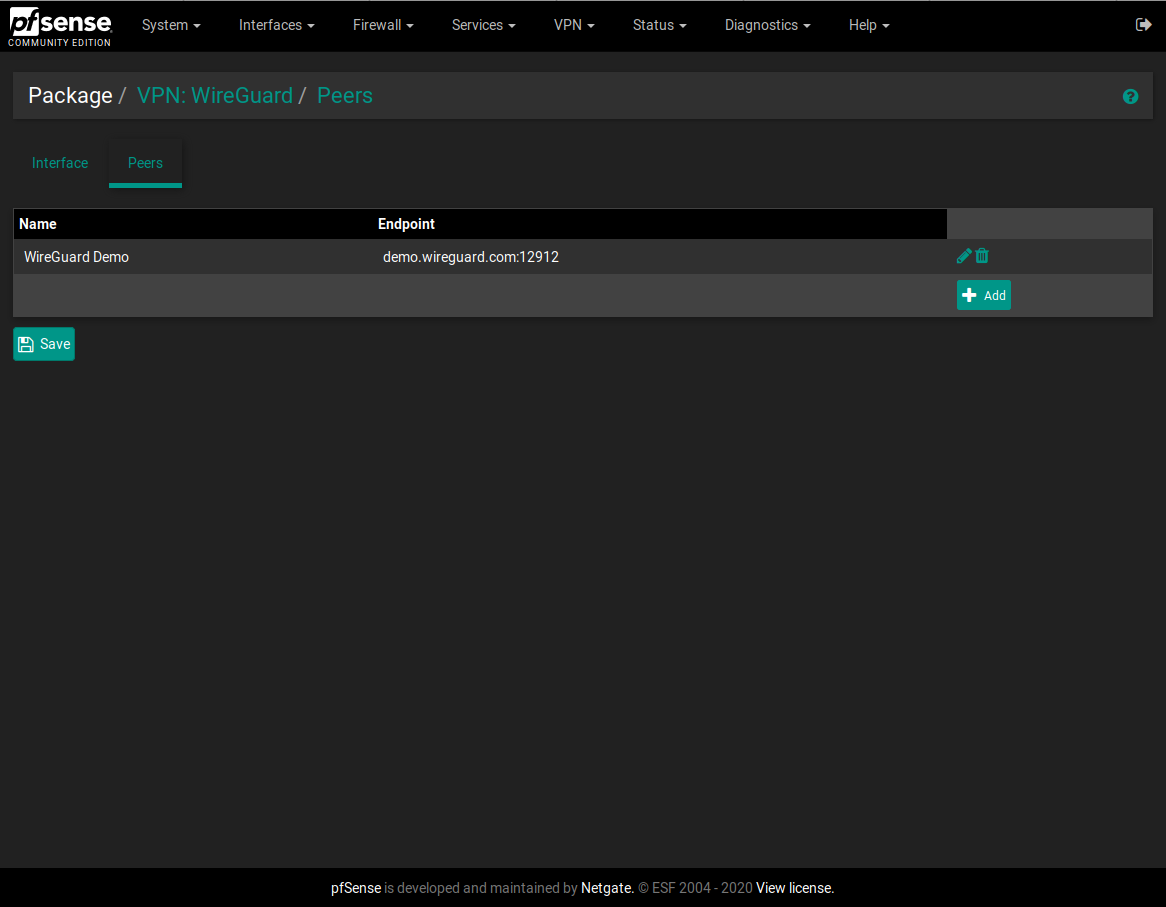
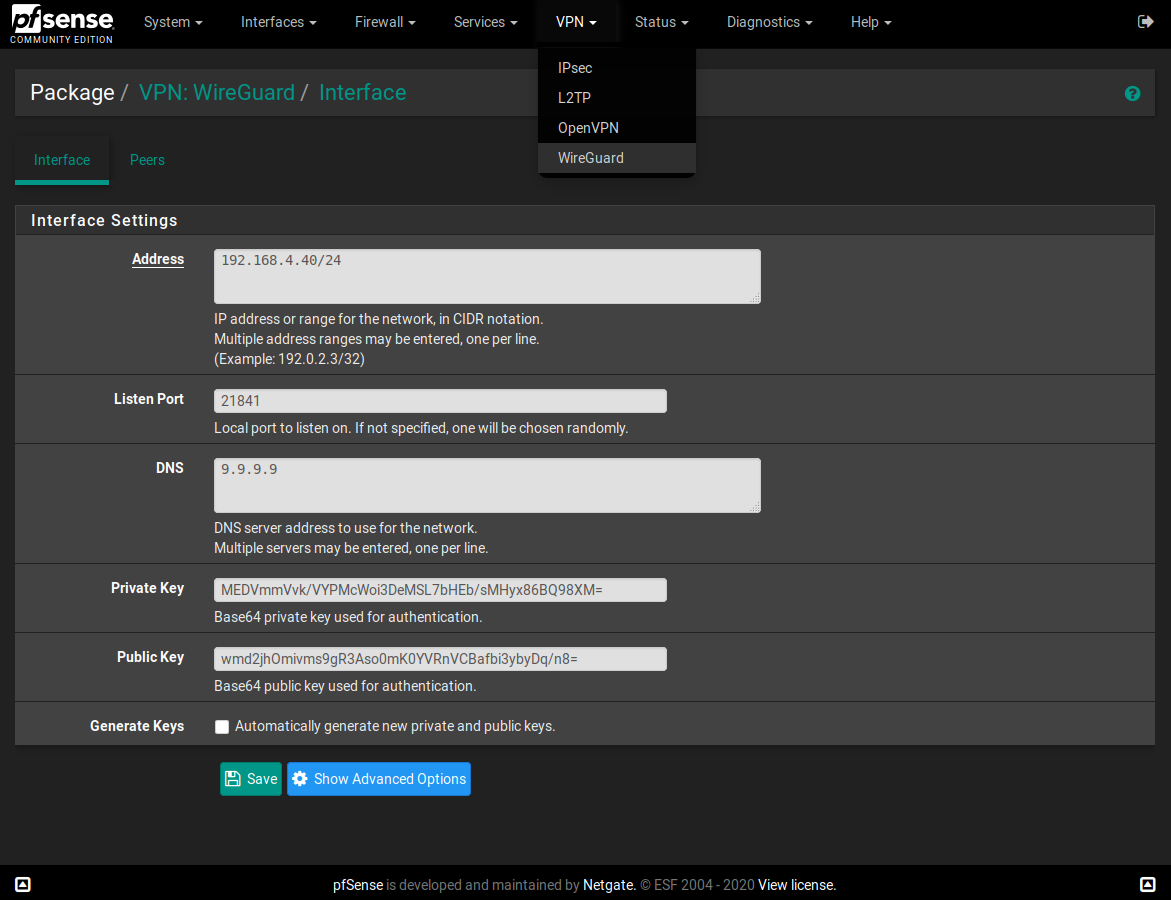
I made a WireGuard package for pfSense
-
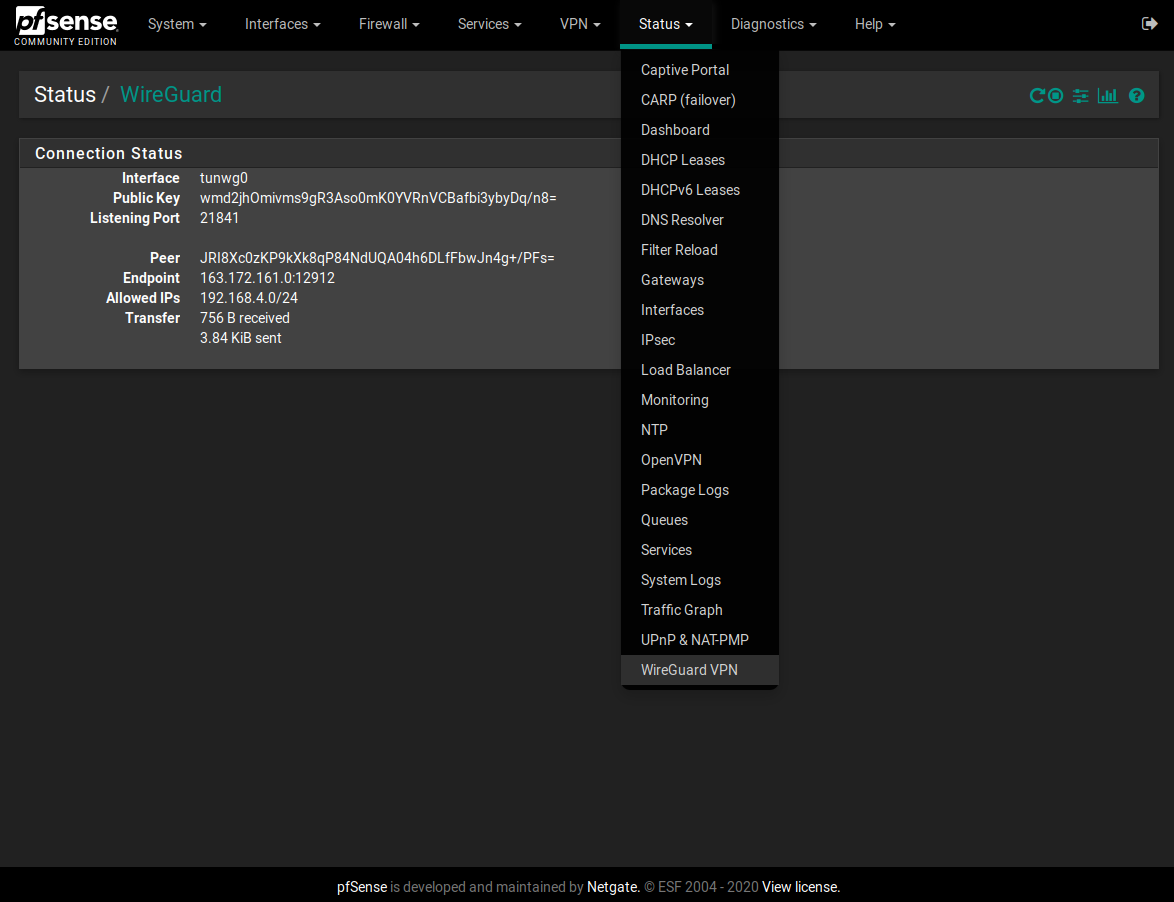
You can goto System>Routing and Add a new Gateway pointing it to the new WireGuard interface. You can then use it like a a normal gateway. The gateway will not appear automatically.
After you create a gateway, I ran into some routing issues related to my setup that I have explained in a post above. -
Solved it. Added the following configuration to the tunwg0.conf file ( can be done through the command line or the GUI).
PostUp = route delete 0.0.0.0/1
This deletes the route from the routing table, allowing pfSense to route based on source IP's.
-
@burntoc I'm in the same boat.
[2.4.5-RELEASE][admin@my-pfsense]/root: pkg add https://pkg.freebsd.org/FreeBSD:11:amd64/latest/All/wireguard-go-0.0.20201118.txz Fetching wireguard-go-0.0.20201118.txz: 0% Fetching wireguard-go-0.0.20201118.txz: 100% 890 KiB 911.1kB/s 00:01 Installing wireguard-go-0.0.20201118... Newer FreeBSD version for package wireguard-go: To ignore this error set IGNORE_OSVERSION=yes - package: 1104001 - running kernel: 1103507 Ignore the mismatch and continue? [y/N]:I'm on an SG-5100 running 2.4.5-RELEASE-p1 which is supposed to be the most up to date (as of this post). Anybody this out? I'm assuming I shouldn't mismatch.
-LamaZ
-
@lamaz said in I made a WireGuard package for pfSense:
LEASE-p1 which is supposed to
Your error is different fro the burntoc's. Your error is simply implying that the kernel we are running is 11.03 while the package is for 11.04 (latest). You can go ahead and ignore the mismatch to continue (if you wish to - I did the same).
-
Looks like the kernel package has just been merged into mainline for 2.5.0. Hope we see it functional out of the box by next release! https://redmine.pfsense.org/issues/8786
Updated by Renato Botelho about 3 hours ago
Project changed from pfSense Packages to pfSense
Category changed from New Package Request to VPN (Multiple Types)
Status changed from New to Feedback
Assignee set to Renato Botelho
Priority changed from Very Low to Normal
Target version set to 2.5.0
Initial kernel version wireguard support is now in place -
https://forum.netgate.com/topic/160025/soon
-Rico
-
Hello,
Anybody know how to completely remove this prior to updating to 2.5? By simply removing the packages, does it also remove the settings from the configuration or are there remnants? And if there are, do they cause a conflict or any errors?
I'd be curious to hear form someone who was running this (awesome, btw) homebrew package and who upgraded to 2.5. Did it work out? Did you have to manually delete things from the config and restore?
Things like that. I'm trying to figure out if I can just upgrade or if I will need to start from scratch (don't want to do that...).
Thanks!
-
@bla
I did that - I ended up removing the package and upgrading to 2.5. Unfortunately it did not work out very smoothly for me. I had some issues with packets 'disappearing'. I don't know if it was related but I ended up doing a clean reinstall. You can read more about the packet disappearing in my post in the Wireguard subsection. YMMV. -
@ab5g Thanks for chiming in (even though it's not the reply I was hoping for) ;-)
-
Now that WG has been disabled in 2.5, is this package still available for use in 2.5? Can it still be used in v2.5?
Would appreciate experiences before i take the plunge.
-
how can i manually remove this wireguard go version on my 2.4.5 system.I want to update my firewall and use the latest wireguard package..