How to block RDP access in 1:1 NAT setup
-
Hi All,
WAN IP: 27.50.90.100
LAN IP: 192.168.0.65
Pfsense IP: 27.50.90.200Port 6665 on pfSense mapped to LAN 192.168.0.65 port 3389
So I can reach my VM through : 27.50.90.200:66651:1 NAT enabled on pfSense for this VM so RDP to 27.50.90.100 reaches to 192.168.0.65 as well.
I want to block RDP access from WAN IP "27.50.90.100" to this VM
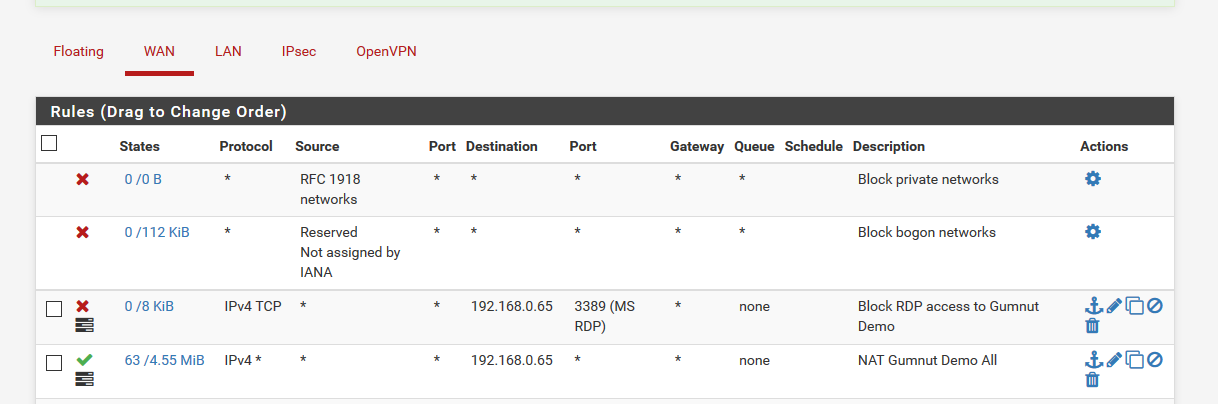
I've added a WAN rule to block anything coming to 27.50.90.100 port 3389 but it does not stop RDP. If I block RDP to LAN IP 192.168.0.65 it will block RDP access to this VM, so pfSense port forwarding will be blocked as well.
I made port forwarding test form outside and found in Diagnostics->States
Source (Original Source) -> Destination (Original Destination)
52.167.131.95:50466 -> 192.168.0.65:3389 (27.50.90.100:3389)So destination and original destination are external and internal IP. How to block external RDP access?
Thank you.
-
@Henry said in How to block RDP access in 1:1 NAT setup:
've added a WAN rule to block anything coming to 27.50.90.100 port 3389 but it does not stop RDP.
not how it works... You would block the destination, after the nat happens.. Post up your wan rules.. Without rule to allow it, it wouldn't of worked because of the default deny.
https://docs.netgate.com/pfsense/en/latest/nat/1-1-nat.html
To allow traffic in from the Internet, a firewall rule must be added on the associated WAN interface allowing the desired traffic, using the destination IP of the internal private IP. -
Check my rules, I've added the public rule as source and destination but no luck
-
Dude you have an ANY rule that to your dest (internal) IP... So again, yes that will allow it.. Did you read the link, and what I quoted from it..
-
@johnpoz Yes I did read and I understand I put allow all.
Please consider I want to have No.1 working and No2. block
1-pfSense Port forwarding to VM :27.50.90.200:6665
2-Direct IP RDP to VM :27.50.90.100:3389If I make a rule to destination and block port 3389 it will block No.1 as well. That's the reason I've allowed all for the time being to work it out. (I changed it to allow all for port 3389)
-
Well put a block to rdp to your internal dest IP, before your allow all.
Rules are evaluated top down, first rule to trigger wins, no other rules evaluated.
-
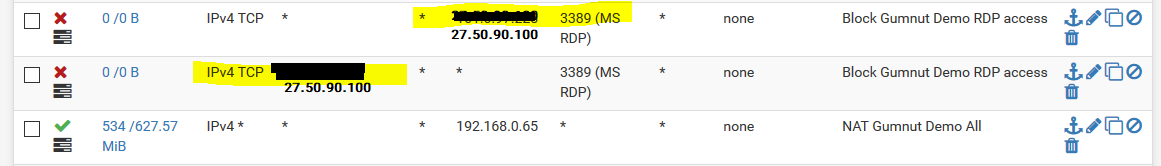
@johnpoz That's exactly what I've done form the beginning. I've blocked all traffic from 27.50.90.100 to any and even I've added any to 27.50.90.100 but RDP is working to 27.50.90.100
-
NO that is not what you did... The destination is your INTERNAL IP!!! Which you have an ALLOW ALL ON!!! Though you stated you read what I linked too?
Put a rule above that last rule that blocks rdp to 192.168.0.65
The 1:1 is evaluated before you rules - so the thing you have to block is the dest internal IP.
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-processing-order.html
-
@johnpoz I set a rule above that to block port 3389 to 192.168.0.65 and now
pfSense Port forwarding 27.50.90.200:6665 is not working
-
Great! Miss read that ;)
-
I brought the rules up and it's blocking 3389, how to allow traffic for 27.50.90.200:6665?
-
@johnpoz did you see this update?
-
Given a 1:1 NAT setup you should be able to block traffic with a firewall rule on WAN that blocks traffic from * to 192.168.0.65:3389. Remember to block both TCP and UDP.
If you're blocking that and also trying to allow traffic to WAN:6665 that is redirected to 192.168.0.65:3389 I don't know that you can block one and allow the other. Can you allow the connection by source IP? Perhaps VPN to pfSense?
You could always change Windows to listen on another port besides 3389 but port scanners will find that eventually.
-
@teamits Thank you for the update. No I can't restrict it by source IP because of many different customers connect to that. Even if I change the default RDP port, it won't block the connection.
-
@johnpoz Dude I found a way to block the connection to WAN and allow it on Port forwarding.
"Filter rule association" should set to pass for port forwarding, so all NAT traffic will pass without any rule and WAN is blocked by default.
-
Why are you doing 1:1 nat if you want to do port forwarding? Just not understanding what your freaking trying to accomplish exactly to be honest. Not understanding the use case at all..
-
@johnpoz 1:1 NAT is for my web-server and I needs to access it by RDP, so direct RDP should be blocked and port forwarding allowed
-
Why do you think you need 1:1 nat? Just do the port forwarding for the ports you need.. There is almost zero reason to do 1:1 nat unless your hosting someone else's server on an RFC1918.. 1:1 nat is for when you have so many ports you need to forward that is easier to just do 1:1. Or you have a whole block of public IPs and you want to do a range of 1:1 nat for a range of public to a range of rfc1918.
If all you want is rdp, then just forward that... How many other ports do you need open on this box that you want to do 1:1?
-
I thought 1:1 NAT is easier to setup and also I can remember the setup later easily.
Secondly, outgoing traffic to the Internet originates from the associated external IP, helps for my reporting.
I only need HTTP & HTTPS on the box.
-
Well if you only need http and https, just forward those.. If your forward it on a VIP the return traffic will use that VIP to return the traffic.
If you want originating traffic from this box to use your vip - just do that with a outbound nat.
BTW opening up RDP, even if you change the port is a HORRIBLE idea.. Unless you can lock it to a specific source IP