Allowing ICMP/Ping From WAN to Machine On LAN for Ptunnel
-
Hello everyone!
I added the following NAT Port Forward Rule:
Interface: WAN ; Protocol: ICMP ; Source Address: * ; Source Ports: * ; Dest. Address: "WAN address" ; Dest. Ports: * ; NAT IP: "LAN IP of Machine" ; NAT Ports: *I also had it "add associated filter rule" to the Firewall but executing a ping against my WAN IP from an machine outside my network results in 100% dropped packets even though the machine I'm trying to reach can be pinged from my LAN.
I've seen where some say that ICMP cannot be forwarded? The reason I ask is because if that is the case then why is ICMP listed as a Protocol in the NAT Port Forward section? Am I missing something or am I going about this the wrong way?
-
i tested it and it work for me, what machine is it? windows?
if it's windows maybe you need to do this
https://forum.netgate.com/post/895254 -
@kiokoman said in Allowing ICMP/Ping From WAN to Machine On LAN for Ptunnel:
i tested it and it work for me, what machine is it? windows?
Thank you for responding! The machine I'm trying to ping on my LAN is Xubuntu and no firewalls are enabled on that particular machine. When you say it worked for you are you pinging or actually initiating a Ptunnel connection? If pinging, you are definitely receiving a response from the LAN machine and not the pfSense WAN interface?
-
during my ping test i had only one rule, an icmp nat from wan to my ubuntu server but i didn't check with packet capture to see what was going on. i didn't try ptunnel
ah ah really neat, i didn't know it existed

anyway it work ..kiokoman@nanto:~$ sudo ptunnel [inf]: Starting ptunnel v 0.72. [inf]: (c) 2004-2011 Daniel Stoedle, <daniels@cs.uit.no> [inf]: Security features by Sebastien Raveau, <sebastien.raveau@epita.fr> [inf]: Forwarding incoming ping packets over TCP. [inf]: Ping proxy is listening in privileged mode. [inf]: Incoming tunnel request from 151.3.xxx.xxx. [inf]: Starting new session to 172.17.0.100:6248 with ID 11724 [inf]: Received session close from remote peer. [inf]: Session statistics: [inf]: I/O: 0.00/ 0.00 mb ICMP I/O/R: 5/ 4/ 0 Loss: 0.0% [inf]: [inf]: Incoming tunnel request from 151.3.xxx.xxx. [inf]: Starting new session to 172.17.0.100:6248 with ID 23358laboratorio@server:~$ sudo ptunnel -p 217.133.xxx.xxx -lp 8000 -da 172.17.0.100 -dp 6248 [inf]: Starting ptunnel v 0.72. [inf]: (c) 2004-2011 Daniel Stoedle, <daniels@cs.uit.no> [inf]: Security features by Sebastien Raveau, <sebastien.raveau@epita.fr> [inf]: Relaying packets from incoming TCP streams. [inf]: Incoming connection. [evt]: No running proxy thread - starting it. [inf]: Ping proxy is listening in privileged mode. [inf]: Connection closed or lost. [inf]: Session statistics: [inf]: I/O: 0.00/ 0.00 mb ICMP I/O/R: 10/ 7/ 0 Loss: 0.0% [inf]: Incoming connection.laboratorio@server:~$ ssh kiokoman@localhost -p 8000 The authenticity of host '[localhost]:8000 ([127.0.0.1]:8000)' can't be establis hed. ECDSA key fingerprint is SHA256:CQ8dUWD3nPtV7cuaQqdtOxWCAAUlN1F8G7cZTIO7DhA. Are you sure you want to continue connecting (yes/no)? yes Warning: Permanently added '[localhost]:8000' (ECDSA) to the list of known hosts . kiokoman@localhost's password: Welcome to Ubuntu 19.10 (GNU/Linux 5.3.0-40-generic x86_64)we can almost consider this a security hole

-
@kiokoman said in Allowing ICMP/Ping From WAN to Machine On LAN for Ptunnel:
we can almost consider this a security hole

My thoughts exactly!
 . It looks like you are definitely getting this to work from outside your LAN but I cannot. I'm able to SSH to the Xubuntu machine from outside my network but still have 100% ping packet loss even after adding an ICMP Protocol rule to the NAT Port Forward redirected to my Xubuntu machine. I'm on AT&T fiber and wondering if my gateway device is blocking ICMP as I do not see anything showing up in the pfSense firewall logs when trying to ping my WAN IP. Did you have to change anything on your gateway device?
. It looks like you are definitely getting this to work from outside your LAN but I cannot. I'm able to SSH to the Xubuntu machine from outside my network but still have 100% ping packet loss even after adding an ICMP Protocol rule to the NAT Port Forward redirected to my Xubuntu machine. I'm on AT&T fiber and wondering if my gateway device is blocking ICMP as I do not see anything showing up in the pfSense firewall logs when trying to ping my WAN IP. Did you have to change anything on your gateway device? -
both side are directly exposed, modem are in bridge mode, i just set a nat rule and that's it
suricata and snort can block it if you have it running -
Found the culprit, which was this setting on my AT&T gateway:
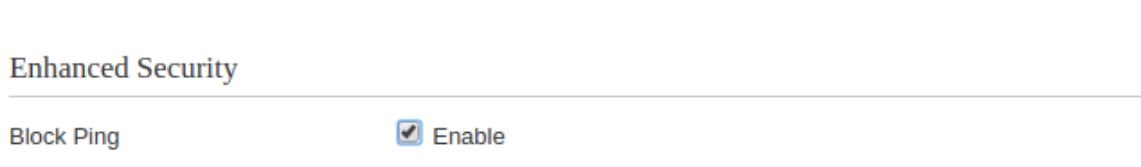
This is just poor AT&T UI layout because the firewall was set to disabled and Public Network on the entire block of static IP's. Yet somehow this setting was enabled and tucked away in another tab
 . Watching tcpdump on my Xubuntu machine I can now see the pings coming through from outside my network. Why is just a NAT port forward required and I do not need a firewall rule? According to this:
. Watching tcpdump on my Xubuntu machine I can now see the pings coming through from outside my network. Why is just a NAT port forward required and I do not need a firewall rule? According to this: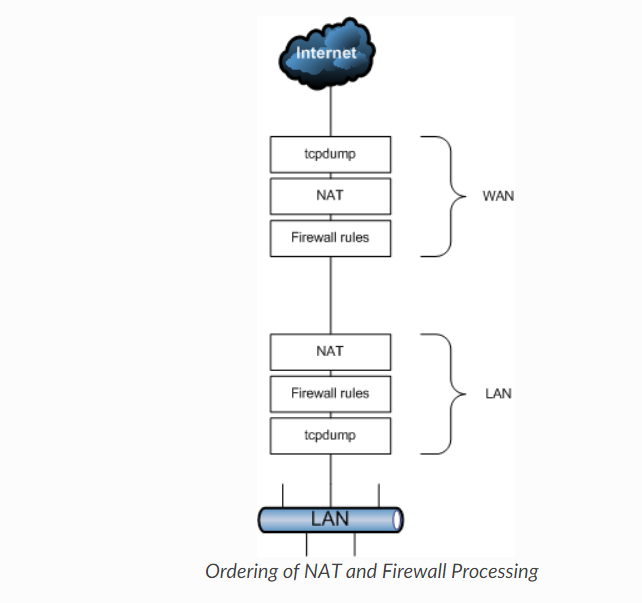
my pfSense WAN firewall should check the incoming ping against the firewall rules correct?
-
from the manual
When adding a port forward, a firewall rule must also be added to allow traffic in to the internal IP address designated by the port forward. There is an option to automatically add this rule when creating a port forward definition, and it is enabled by default.
https://docs.netgate.com/pfsense/en/latest/nat/forwarding-ports-with-pfsense.html -
@kiokoman said in Allowing ICMP/Ping From WAN to Machine On LAN for Ptunnel:
When adding a port forward, a firewall rule must also be added to allow traffic in to the internal IP address designated by the port forward.
Yes, but my concern is I'm able to ping my Xubuntu machine outside my network without a firewall rule passing the ICMP to the Xubuntu machine. All my other NAT port forwards require a firewall rule but why doesn't this one?
-
are you sure? show a screenshot of wan firewall rule maybe you have another rule that permit icmp