Trouble getting ExpressVPN running on pfSense 2.3.5
-
Hi all,
I tried configuring EpressVPN on my pfSense 2.3.5 box following the guide provided by EpressVPN.
I configured the CA, Certificate and Client. After configuring the client I should be able to confirm that the OpenVPN connection was successful by navigating to Status > OpenVPN.
However in this screen status says either "down" or "reconnecting; tls-error". I had some chat and e-mail sessions with ExpressVPN but it seems that they can't find the problem for some reason.
Here are the relevant log entries (/var/log:openvpn.log):
Mar 7 15:31:03 firewall openvpn[92755]: NOTE: the current --script-security setting may allow this configuration to call user-defined scripts Mar 7 15:31:03 firewall openvpn[92755]: Socket Buffers: R=[42080->524288] S=[57344->524288] Mar 7 15:31:03 firewall openvpn[92755]: UDPv4 link local (bound): [AF_INET]80.201.118.199 Mar 7 15:31:03 firewall openvpn[92755]: UDPv4 link remote: [AF_INET]104.237.51.203:1195 Mar 7 15:31:03 firewall openvpn[92755]: TLS: Initial packet from [AF_INET]104.237.51.203:1195, sid=8ee52f73 d602875c Mar 7 15:31:03 firewall openvpn[92755]: VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com Mar 7 15:31:03 firewall openvpn[92755]: Validating certificate key usage Mar 7 15:31:03 firewall openvpn[92755]: ++ Certificate has key usage 00b0, expects 00a0 Mar 7 15:31:03 firewall openvpn[92755]: ++ Certificate has key usage 00b0, expects 0088 Mar 7 15:31:03 firewall openvpn[92755]: VERIFY KU ERROR Mar 7 15:31:03 firewall openvpn[92755]: OpenSSL: error:14090086:SSL routines:SSL3_GET_SERVER_CERTIFICATE:certificate verify failed Mar 7 15:31:03 firewall openvpn[92755]: TLS_ERROR: BIO read tls_read_plaintext error Mar 7 15:31:03 firewall openvpn[92755]: TLS Error: TLS object -> incoming plaintext read error Mar 7 15:31:03 firewall openvpn[92755]: TLS Error: TLS handshake failed Mar 7 15:31:03 firewall openvpn[92755]: SIGUSR1[soft,tls-error] received, process restarting Mar 7 15:31:03 firewall openvpn[92755]: Restart pause, 2 second(s)I did some searches on google and this forum but I can't lay my finger on the cause of the problem.
Any suggestions where to look?
Thanks very much,
Erik
-
For some reason when I try to insert a link to the guide my post content was flagged as spam by Akismet.com ?????
-
Instead of coping htpps://some.domain.tld/file make it robot friendly like htpps://some dot domain dot tld/file
@ehoitinga said in Trouble getting ExpressVPN running on pfSense 2.3.5:
++ Certificate has key usage 00b0, expects 0088
What certs are you using ? You should import the certs into System > Certificate Manager, CA and Cert, and use them when setting up the Open VPN client.
I used this one in the past https://www.expressvpn.com/fr/support/vpn-setup/pfsense-with-expressvpn-openvpn/ and it worked for me. It was already somewhat outdated back then, as things do change over time.
-
@Gertjan I used the certificates that are in the .ovpn file I got from ExpressVPN. I created the CA, thet certificate and the client as described in the link you gave. I copy/pasted the certs from the .ovpn file to pfSense.
Later on it crossed my mind that there is a difference in line ending between Unix and Windows. So I looked into the relevant files in /var/etc/openvpn on my pfSense box, and noticed there where ^M characters at the end of each line. But removing these characters did not solved the problem.
I really can't see why TLS handshaking fails. I'm pretty sure I copy/pasted the right verts in the right place.
-
@ehoitinga said in Trouble getting ExpressVPN running on pfSense 2.3.5:
But removing these characters did not solved the problem
You can't change a file encoding like that.
But coyping the cert and CA using the clipboard will take care of it. If not, the info, would get accepted as CA or cert.
All is well in this section ?
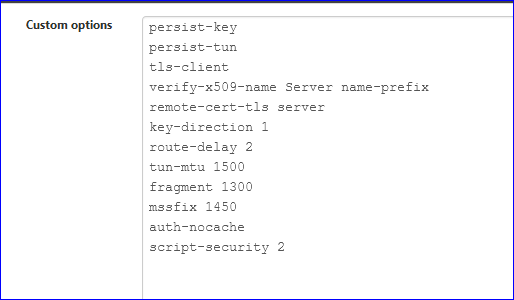
This part can override every setting above. The minimum should be entered.
Btw : these are for the EpressVN client. -
So I deleted the client, CA and cert and started over. I copy pasted the CA and the certificate and they where both accepted as certificate. The only thing is that I don't have a "Valid until" date for my client certificate (System->Certificate Manager->Certificates).
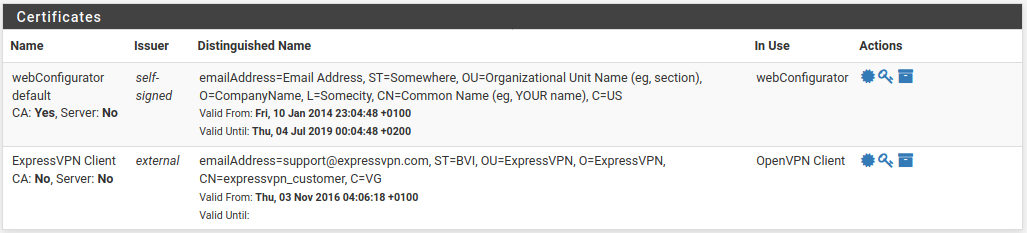
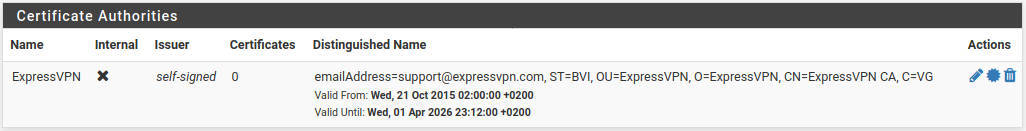
My cryptographic settings:
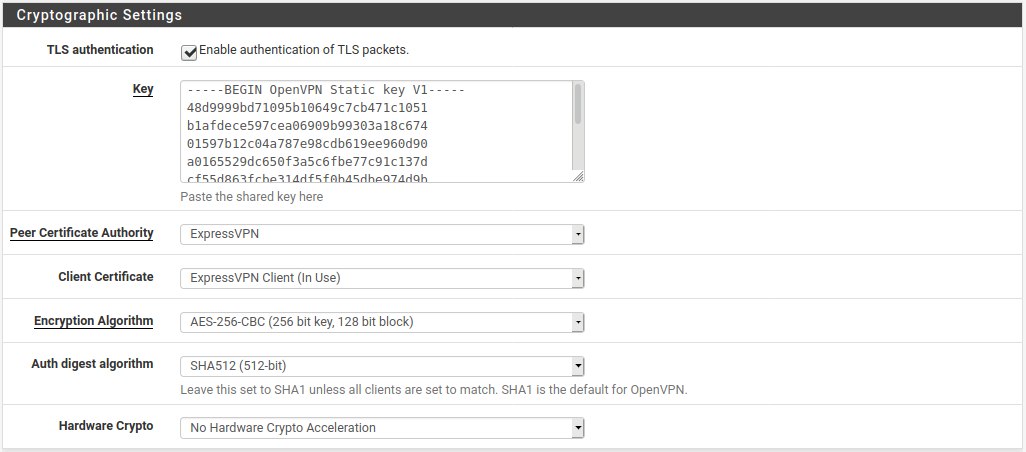
My advanced configuration:
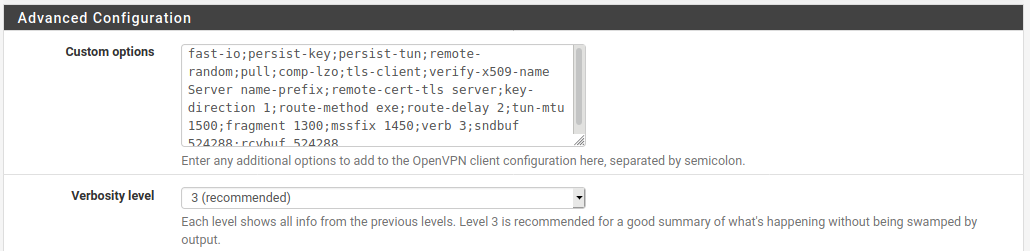
As far as I can see everything should be OK in this config. Still I get the same error when looking at Status->OpenVPN/
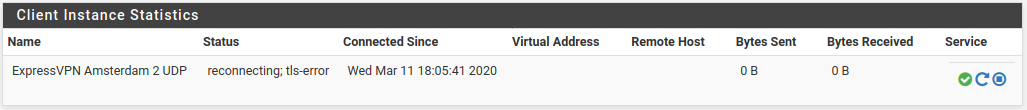
Really don't know what going wrong here.
Erik
-
@ehoitinga said in Trouble getting ExpressVPN running on pfSense 2.3.5:
The only thing is that I don't have a "Valid until" date for my client certificate
I've an end date :
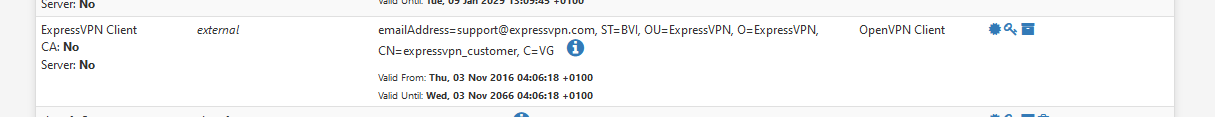
It's probably the same cert.
-
@Gertjan Really don't know what's going on. I saw that the CA's, certificates, RSA private key's and the OpenVPN static key are the same in every .ovpn file I downloaded from expressvpn after logging in to their site.
I retried entering the certificate in System->Certificate Manager->Certificates but no luck. Still no "valid until" date.
I have a rather "old" pfsense box. It is an 32bit OPNSense 1U rack server with pfSense 2.3.5-RELEASE-p2 (i386) installed on it.
The only thing I can think of that causing the problem is either the lacking "valid until" date or the old software/hardware combination that I have.
Does somebody has other idea's.
Kind regards,
Erik
-
That might be an issue.
OpenVPN is based onopenssl version OpenSSL 1.0.2u-freebsd 20 Dec 2019for pfSense 2.4.4-..... updated to the last RC yesterday).
Your version is years old - you have to check with Expr*ssVPN if they accept ancient openVPN openssl versions ...
If 'security' is present on their list then .....Btw : keep in mind that no one can remember what 2.3.5 issues were or could be.
-
OK, I did some further digging on these lines coming from my openvpn.log file:
Mar 11 22:19:57 firewall openvpn[99120]: ++ Certificate has key usage 00b0, expects 00a0 Mar 11 22:19:57 firewall openvpn[99120]: ++ Certificate has key usage 00b0, expects 0088I found an article on this site which is talking about OpenVPN and remote-cert-tls server option in Advanced Configuration -> Custom options.
When I add the option "remote-cert-ku b0" just after the option "remote-cert-tls server" my openvpn client connection status went to "up".
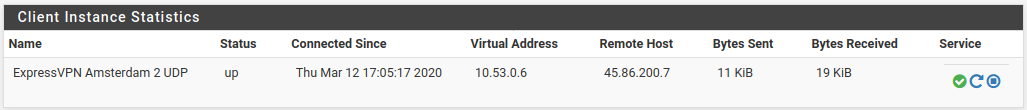
So now the VPN connection is up I can continue to configure pfsense to route the WAN through the tunnel.
Keep you posted if necessary. Thanks for the help so far.
Erik