Inter-VLAN traffic Client Isolation
-
Hi Team,
I need help with an issue I’m facing and can’t really understand what is the cause, I’ll explain:
- I have a one pfsense.
- Two ubiquity unifi switches.
- one HP 1810-8g switch.
I have created 6 vlans:
Network design:
LAN is untagged vlan 1
Vlan 100 (MGMT) 192.168.2.128/25
Vlan 200 (Storage) 192.168.3.128/25 only L2
Vlan 300 (Intranet) 192.168.4.128/25
Vlan 400 (Guest) 192.168.5.128/25
Vlan 500 (Server) 192.168.6.128/25
Vlan 600 (IoT) 192.168.7.128/25
Untagged vlan is 1 all over, all the Rest is Tagged.Everything works as expected, i can reach every gateway of every vlan from every vlan as I pleases (at the moment I explicitly allow all IPv4 traffic between the vlans.
The only problem I’m facing is I cannot reach clients on different vlans from the native vlan or from any vlan and vise versa. (sort of like the clients are isolated).
I put logging on the firewall rules, and actually I can see that traffic is not being denied or blocked, but it’s going through!Also thing like DHCP off curse in the same broadcast domain are working well, but also dns to the lan address Shows everything is ok.
Thanks on advance, and have a nice weekend.
-
Someone please?
-
for example:
MBP ~ % ping 192.168.2.205
PING 192.168.2.205 (192.168.2.205): 56 data bytes
Request timeout for icmp_seq 0
Request timeout for icmp_seq 1
Request timeout for icmp_seq 2
Request timeout for icmp_seq 3
Traffic is being passed, but still I cannot reach clients on other vlans.
Mar 13 18:59:09 LAN 192.168.1.154 192.168.2.205 ICMP - Pass
Mar 13 18:58:05 LAN 192.168.1.154 192.168.2.205 ICMP - Pass
The rule that triggered this action is:@105(XXXXXXXX) pass in log quick on Vlan_trunk inet all flags S/SA keep state label "USER_RULE"
-
Do you have rules to allow traffic from one VLAN to another?
-
Post the LAN rules. You don't have a gateway selected under advanced, do you?
-
Thanks for the answer.
I have set for the troubleshooting Ipv4 allow allFor example:
On the Floating rules:
Allow all IPv4 * * * * * * noneAlso on the trunk I created under interface group (Where I bond all sub interfaces with the LAN uplink) rules:
Allow all IPv4 * * * * * * noneIn short I have fully allow all traffic, but still seeing the problem.
On the logs nothing is being blocked, but still I cannot trace route or ping from and to clients.Thanks,
-
Thanks,
The only gateway I have under advanced is the next WAN modem I have, I can reach the internet from all VLANs.
Here are the rules:rules.xls [0_1584124401963_Rules.rtf](Uploading 100%) [0_1584124167304_Rules.rtf](Uploading 100%)
-
A small correction, I was able to reach the internet, outbound traffic was ok yesterday for all vlans.
Now internet outbound traffic is only working on the LAN untagged. -
A few screenshots would have been fine. I Don't really have time to sort through the raw dump, but some things look goofy.
Not sure what you are doing with your 'interface group trunk'?? and floating rules. Why don't you start simple:
Firewall rules, vlan 100 tab, ipv4* vlan 100 net to any No advanced settings
vlan 200 tab, ipv4* vlan 200 net to any No advanced.
Then try to ping from vlan 100 to 200.... -
The interface “Trunk-Group” is where I Bond all vlans on the only wire (uplink) I have:
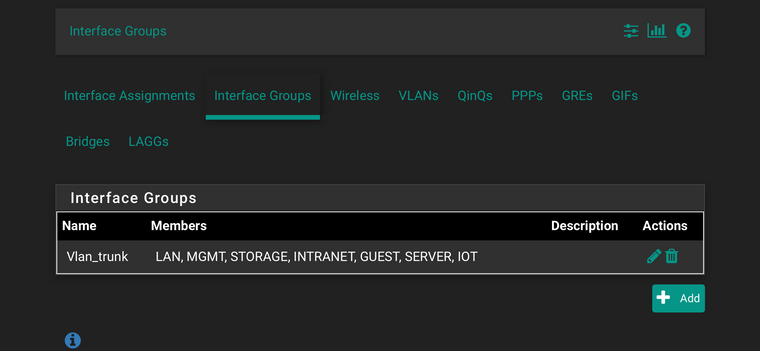
Over there I have a full ipv4 pass rule
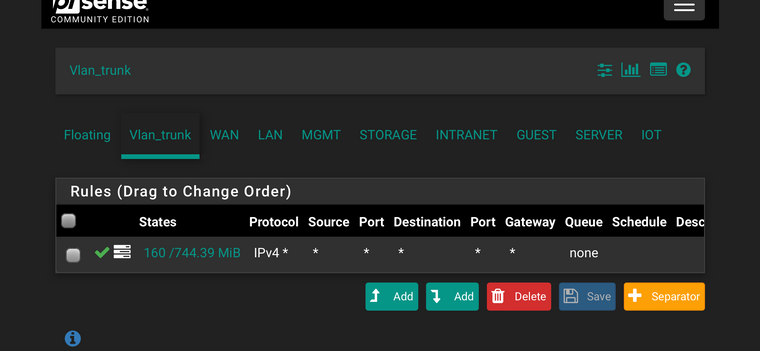
On the floating it’s the same, only that there are some public “bad” addresses that I have blocked, but that’s are only incoming from the WAN side, nothing internal.
-
In the interest of trying to walk before flying, why don't you see if it works when you add the rules to the interfaces, like I suggested before.
-
I do have the rules as you suggest on some interfaces for testing, when it works I’ll replicate to the other interfaces, but now it’s not working:
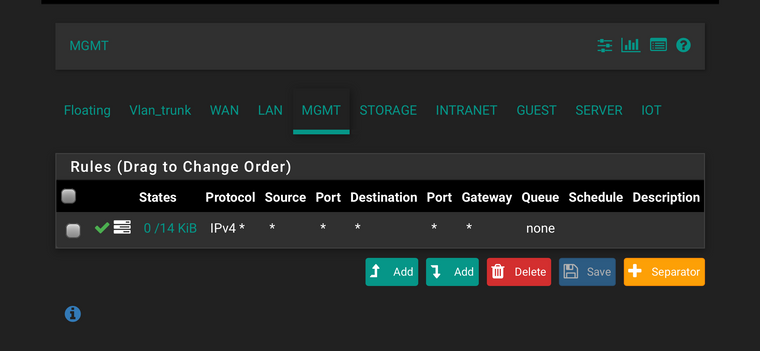
I suspect that I would need to factory reset the pfsense if nothing produces results, what I couldn’t do on a big production environment.
Maybe backup the configuration.
Reset to default.
Test with minimal configuration.
If works, the go step by step.
If not working restore configuration and troubleshoot again -
Here is an example where I ping to a client and I get no response:
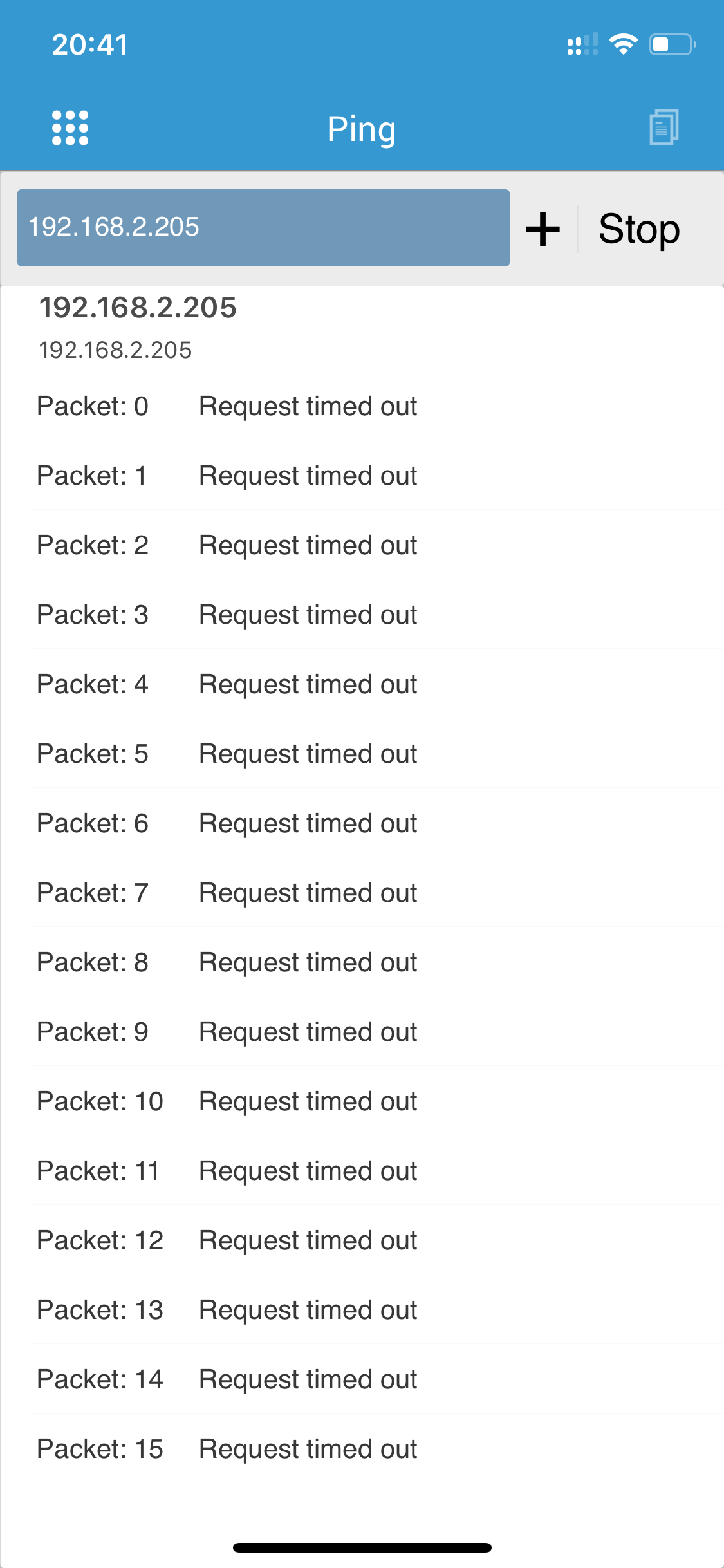
But looking in the logs everything looks good, my iP as source is reaching the destination:
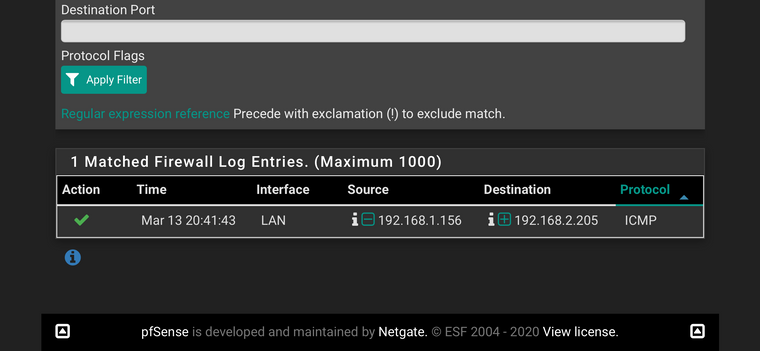
-
Thanks everyone, I’ve got it sorted out.
Did as I explained in my previous post and added allow rules under every vlan, then it started working.
Still doesn’t explains the firewall logs showing green for passed while it wasn’t the case.