FQDN
-
Hello,
I have a Remote Access OpenVPN setup and working however when trying to map a network drive it's forcing me to use the FQDN of the server instead of just the computer like like normal.
Example: DC1.domainname.local - works
Exmaple: DC1 - does notOn the tunnel settings I have a DNS server specified and Block outside DNS turned on. Any ideas?
-
That is the default domain. That is pushed using this in the OpenVPN server:
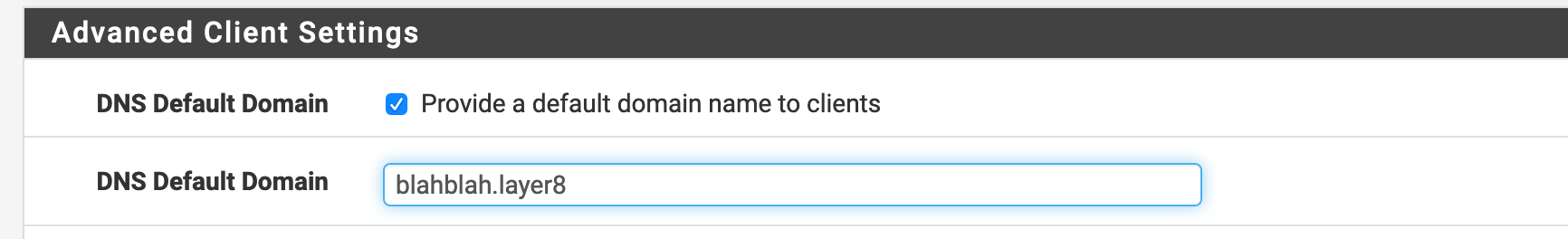
As with most pushed settings it is up to the client to honor it and use it properly.
-
@Derelict so I do specify the domain name as well. When you say honor that you mean force DNS suffixes elsewhere on the device?
-
When a host wants to resolve a name it appends a default domain to its query.
If its default domain is domainname.local and it wants to resolve hostname host, it submits its query to its configured DNS resolvers as host.domainname.local
It is completely up to the client to do this.
-
If its default domain is domainname.local and it wants to resolve hostname host, it submits its query to its configured DNS resolvers as host.domainname.local
Got it working, thanks everyone!
Is there a command that can be put in the advanced configuration for disconnecting after a time period?
-
Probably the client sleeping, power saving, etc. You might need to better-describe what you are actually experiencing.
There is an automatic renegotiation/reauthentication that happens by default every hour but unless you are using multi-factor authentication, that should be hitless if the client and server are both still communicating.
-
There is an automatic renegotiation/reauthentication that happens by default every hour but unless you are using multi-factor authentication, that should be hitless if the client and server are both still communicating.
Hello,
We do have it authentication with AD through radius. Definitely not getting disconnects ever hour.
Looking to add a time limit to disconnect. Thinking if there's an employee in the field that is released, would like to know their VPN connection will drop. At that point their AD authentication will no longer work.
-
As I stated, the connection is re-authenticated every 60 minutes by default. That will hit the RADIUS server again. If the authentication succeeds again the user connection will continue. Logs should be able to be evaluated to determine this is actually occurring to your satisfaction. You can connect a test user then disable it in AD by whatever method you use and see what happens too.
This time period is controlled on both the server and the client with:
reneg-sec 3600;3600 is the default there.reneg-sec 0;disables renegotiation on that side. -
As I stated, the connection is re-authenticated every 60 minutes by default. That will hit the RADIUS server again. If the authentication succeeds again the user connection will continue. Logs should be able to be evaluated to determine this is actually occurring to your satisfaction. You can connect a test user then disable it in AD by whatever method you use and see what happens too.
I will check that, thanks!
We are also having an issue where the GUI errors out and we've been able to determine it's because most of our users don't have Administrative privileges on their laptops. I've done some searching and found ways of running the GUI service through scheduled tasks but hopefully someone else has a better option.
https://forum.netgate.com/topic/115680/openvpn-without-admin-rights-win-7-and-xp-on-pfsense-2-3-3_p1/2
-
That is almost all taken care of by running current OpenVPN client code on the windows machines.
If you remove all OpenVPN traces (Add/Remove Programs or whatever it is called these days) and reinstall a configuration export, current code will be installed.
Or you can manually upgrade OpenVPN on the devices.
-
-
It does but it does not automatically update the client host unless you REMOVE what is already there before you run the export. I do not know whay that was chosen. Probably considered to be a POLA thing.
-
We are using Revo Uninstaller to remove the client package before re-installing. Should this not be enough? Revo is even finding the registry and remaining files.