SG-3100 OPT1 Firewall configuration - basic help appreciated!
-
I am new to the SG-3100 / firewall configuration. OPT1 is configured as a secondary ADSL connection.
I can direct traffic out this interface. But cannot connect remotely to the webgui, VPN, SSH etc via OPT1 (WAN works fine). So I think I am missing something (hopefully very basic).
Any guidance would be very much appreciated!
-
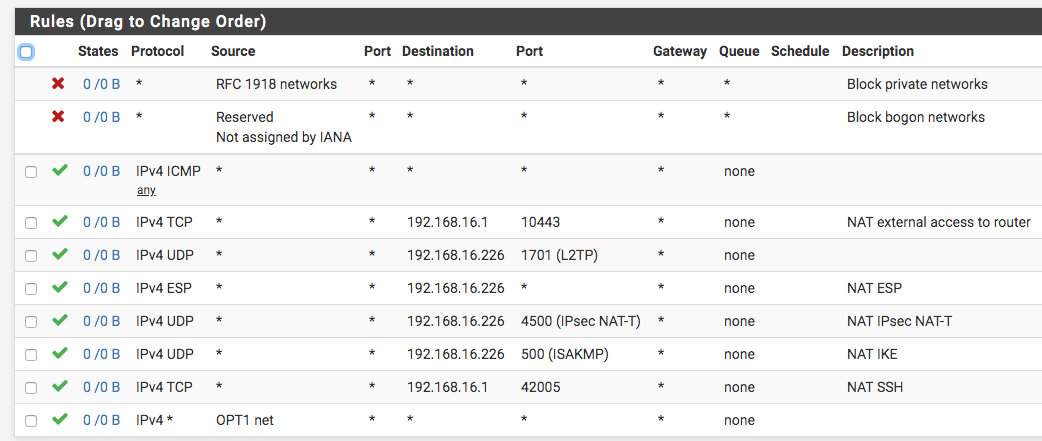
First things first.
When you sat OPT1, this means a second LAN type interface. The first one is called "LAN", etc.
It is possible to declare a third interface, after WAN and LAN, so being called initially OPT1, as a second WAN interface.@paul_endeavour said in SG-3100 OPT1 Firewall configuration - basic help appreciated!:
But cannot connect remotely to the webgui .....
Concerning the GUI, That's not a bug, it's a feature.
But a simple firewall rule on the WAN (WAN2) interface will do the job. Use the VPN wizard and you'll see it creates a firewall rule on the interface being used by the VPN server.
You probably should create a second VPN server that listens on the second WAN.SSH : just a firewall rule.
GUI : just a simple rule like
This :
means that there are zero packets that inter your WAN2 interface that match.
I pretty good proof that traffic is already blocked up stream : your ISP ADSL router.
You have natted all the ports/protocols on that device also ? If so, you see the incoming traffic, and your firewall would do it's job.When I add a rule like :
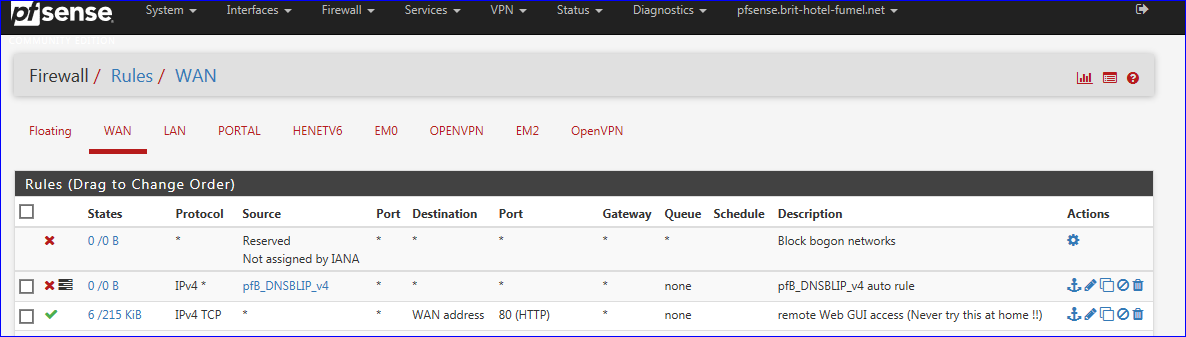
( see the last line ) and I add a similar rule to my ADSL ISP Router, I have access to the http WEB GUI from where ever on the world.
I just tried and it worked. -
Thank you for your help.
Problem solved. The issue was that the port forwards were not setup correctly. Fixed this under Firewall / NAT / Port Forward - creating a linked rule, and all is now good.
Thank you for your kind responses!
Paul
-
Ok, great.
@paul_endeavour said in SG-3100 OPT1 Firewall configuration - basic help appreciated!:
under Firewall / NAT / Port Forward
Keep in mind that, when you need to access IPv4 devices that are on a LAN, you need to create NAT rules.
The pfSense GUI, the SSH and VPN do not need a NAT rule. These 3 services are listening on any interface already, which includes WAN - VPN listens on the interface you choosed. The (hidden) default WAN firewall rule protects them from being accessed from the outside.So, see my image above : a simple firewall will do to let, for example, http traffic into pfSense to port 80 and your GUI is exposed on that interface. A very bad idea of course, but that's another story.