pfSense 2.4.5 Now Available
-
@johnpoz said in pfSense 2.4.5 Now Available:
pkg-static update
This is first time I see this issue and I have not changed anything.
Why now ?[2.4.4-RELEASE][admin@pfsense.wawona.lan]/root: pkg-static update -f
Updating pfSense-core repository catalogue...
Fetching meta.txz: 100% 944 B 0.9kB/s 00:01
Fetching packagesite.txz: 100% 2 KiB 1.7kB/s 00:01
Processing entries: 100%
pfSense-core repository update completed. 7 packages processed.
Updating pfSense repository catalogue...
Fetching meta.txz: 100% 944 B 0.9kB/s 00:01
Fetching packagesite.txz: 100% 141 KiB 144.4kB/s 00:01
Processing entries: 0%
Newer FreeBSD version for package xe-guest-utilities:
To ignore this error set IGNORE_OSVERSION=yes- package: 1103504
- running kernel: 1102000
Ignore the mismatch and continue? [Y/n]:
-
I updated pfBlockerNG-devel to 2.2.5_30 only .
Maybe that's the reason. I am still on 2.4.4
cc: @BBcan177
-
The golden rule is :
Update first pfSense, if an update is available (not RC).
Then the packages ....There is an update to pfSense, 2.4.5 - that should be done first.
Only then you can continue upgrading packages.If not ......
-
@johnpoz said in pfSense 2.4.5 Now Available:
I updated 4 Days 05 Hours 47 Minutes 35 Seconds ago, with the following packages installed with the only issue that I have discovered is I had to click the update graphs in the traffic totals package.
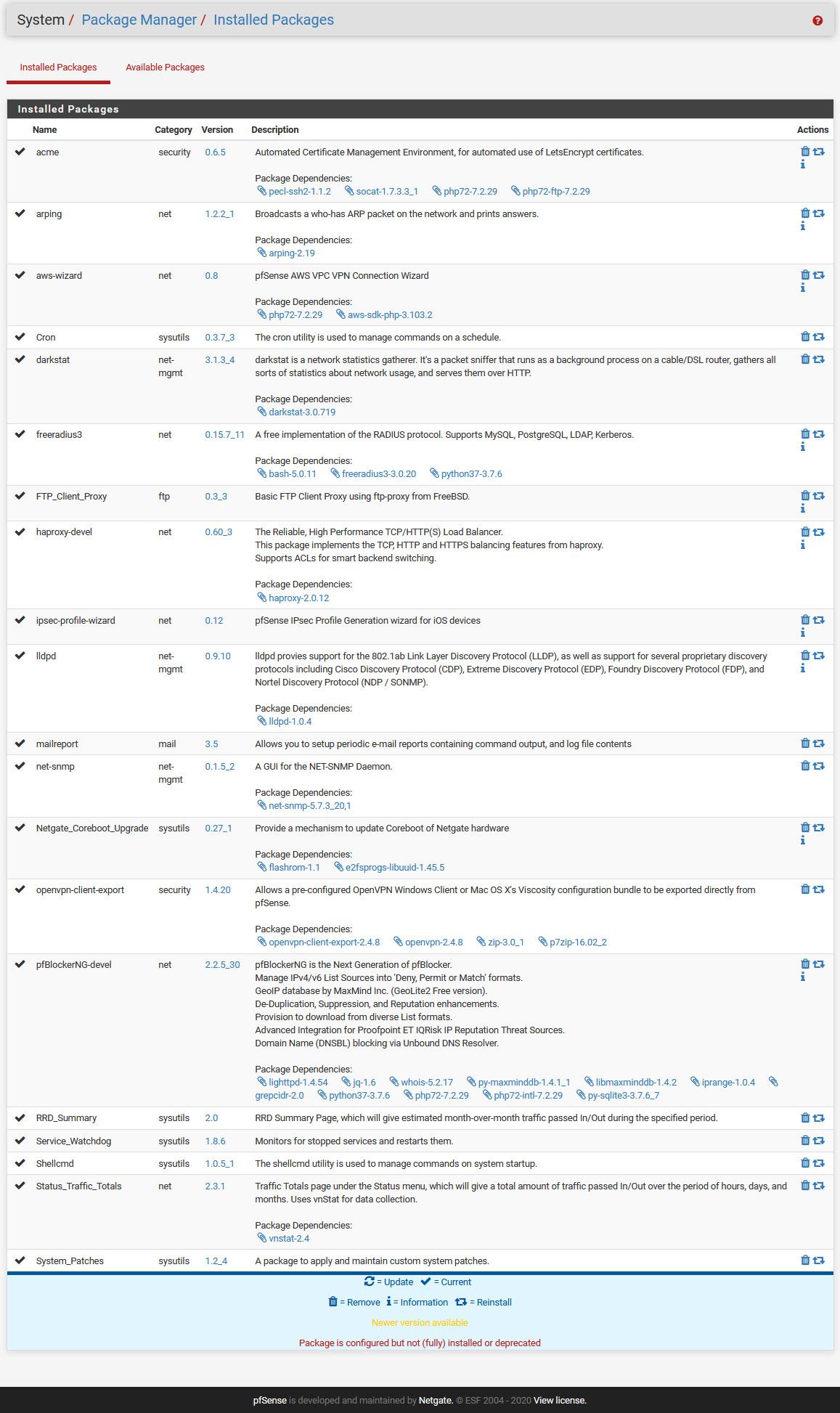
@johnpoz noticed you are running pfBlockerNG-devel, would you mind posting your settings? Assuming you have not seen any of the issues reported in the topic below post upgrade to 2.4.5 -- that some have traced back to pfBlockerNG, unbound, pfctl or some combo thereof -- your setup may help provide workarounds for some (especially if running on netgate or other bare-metal servers).
https://forum.netgate.com/topic/151690/increased-memory-and-cpu-spikes-causing-latency-outage-with-2-4-5/
-
-
I only use pfblocker for the geoip aliases - I don't have it doing any rules or anything. It just maintains the aliases that I then use in my own rules. And only then for allowing specific access to my forwards. My settings would not be in line with how most people use it..
I use it to limit access to my plex to the countries that my users are in, and allow access to my vpn to only US, that sort of thing.
BTW - not suggesting that anyone just click upgrade.. You should follow the guide for sure.. But I wouldn't have any issues if it completely blew up either. I have backup of my config, I have image to do a clean install. And my setup overall isn't all that complicated.. Plus have 10+ years of running pfsense - so I am pretty sure if it took a dive I wouldn't have any issues to get my home network up and running in a few minutes. Worse case I do have a spare USGp3 box I could fire up if the hardware decided to take a dump during the process.. You always need to have plans in place when doing any sort of upgrade to this sort of equipment - things always seem to go wrong at the worse times.. So you have to plan for them!
That is why I just did click without removing all the packages, etc. If you are not at this same comfort and skill level, then for sure you should follow best practice upgrade..
I am also right next to the box, and its only a home network - not production.. So even if was down for extended period.. Worse case is wife wouldn't be able to use the internet, and friends and family wouldn't be able to access my plex server ;)
I am not going to update any of the work netgate boxes until we get back to the office, even though right now would be a good time since nobody is there.. But if they had some sort of an issue, they would be down for quite some time - and when people do start going into the offices, which might before I do, etc. they would be down. So yeah those can wait.
-
@Gertjan said in pfSense 2.4.5 Now Available:
The golden rule is :
Update first pfSense, if an update is available (not RC).
Then the packages ....There is an update to pfSense, 2.4.5 - that should be done first.
Only then you can continue upgrading packages.If not ......
I think Package Manager should even allow update packages meant for new version. Then we would not have any of these issues!
-
So you will have a pull request later to day for that I take it?
https://docs.netgate.com/pfsense/en/latest/development/submitting-a-pull-request-via-github.html -
@johnpoz said in pfSense 2.4.5 Now Available:
I only use pfblocker for the geoip aliases - I don't have it doing any rules or anything. It just maintains the aliases that I then use in my own rules. And only then for allowing specific access to my forwards. My settings would not be in line with how most people use it..
I use it to limit access to my plex to the countries that my users are in, and allow access to my vpn to only US, that sort of thing.
That type of use may explain what's happening in some cases where spikes seem to happen due to unbound and (presumably) a large DNSBL entries file. Which you wouldn't have, so it does not impact unbound. Anyway, fortunately, not as affected as others have been and could downgrade pretty easily if it came to that. Right now though, still trying to figure out if there may be any fix short of downgrading available or coming. The point was made and would seem sensible, that pkg should not be switched to pull data from a new version prior to an actual update (happened to me too which sort of forced the matter of the upgrade).
-
@chudak said in pfSense 2.4.5 Now Available:
I think Package Manager should even allow update packages meant for new version. Then we would not have any of these issues!
Very true.
But ... pfSense is just pfSense. Packages are nice addons but mostly written and maintained by guys like you and me.
I me and you will not (like never) want to deal with version management. That means you have to support the guys that use the older versions of pfSense, with the bug and issues from back then and the new issues that just came up. That will mean : problem solved because no more packages.
It might work out for a $$$$ environment.
Also : pfSense has to support the "where to get my updates" - you do remember that Netgate is doing this all for close to free so they decide what is needed - what should be done. -
In my case I was trying to be very careful, but did not see that system has a new version available and simply updated some packages - and there problems started !
I think this can be avoided not by forcing package developers to change anything, but simply by displaying some warning messages in the pfsense UI
Look at how many people having troubles ?!
Hope you agree.
Thx
-
@chudak said in pfSense 2.4.5 Now Available:
Look at how many people having troubles ?!
No way.
Count the people that still have problems copying an iPhone to a new iPhone. That will always last. Although it's a finger in the nose trick these days.The pfSense upgrade procedure has been guided, documented and explained - with every major version update, for several years now.
Issues are not possible, because pfSense is a close-to-industrial firewall. They do not oblige you to write out that big cheque like Cisco to have it dealt with, or send one of the employees to a new training to handle the update. pfSense makes it easy : they only ask one thing : being able to read. There is no place to mess up : no one will install a new version on a system will taking down the companies or their private Internet access. For a couple of $$ you have a backup system (an old PC will do) - so the upgrade is two phase. Permits you to fast compare, check. There is a free support forum and redit and the manual and the main Negate blog, a huge channel filled up with in-depth vidoes as a guide line : what do you want more ? You really need more ? Serious ?@chudak said in pfSense 2.4.5 Now Available:
I was trying to be very carefu
As said : RTFM.
@chudak said in pfSense 2.4.5 Now Available:
did not see that system has a new
and there problems started !Like that red traffic light in front of you on an intersection ? You'll be asking for barriers on the road also now ?
More code, more text and more screen will make system less error prone. In theory, yes. But as long as systems deal with humans, there will always be issues.
-
@dennis_s
Like the "copy" functionality within the OpenVPN Client Specific Overrides.- I note that these can be slow to apply though.
I rebooted the router and the first lot of OpenVPN connections were not allocated the IP addresses as specified in the CSO.
Disconnecting each client through the server gui, and letting each client auto reconnect fixed the issue.
ie - they were then assigned the VPN IP addresses as per the CSO rules.
- I note that these can be slow to apply though.
-
@chudak said in pfSense 2.4.5 Now Available:
In my case I was trying to be very careful, but did not see that system has a new version available and simply updated some packages - and there problems started !
I think this can be avoided not by forcing package developers to change anything, but simply by displaying some warning messages in the pfsense UI
Look at how many people having troubles ?!
Hope you agree.
Thx
Perhaps a splash screen such as used by the license agreement and survey would be suitable. I know, Monday Morning QB. :/
-
Update took quite a bit of time on my SG-1100 and I had to reboot my cable modem afterwards. The web interface leads one to believe that the system should reboot in 80 seconds or so. This is not even close. The upgrade took >10 minutes. I ended up using the usb console to see that the system wasn't frozen. I suppose this is a live & learn situation but it would be really nice if the web interface had a link to the readme and a reasonable time estimate based on the hardware. The quick flashing green light (black diamond) isn't all that useful after a while.
-
Thought I'd toss out a couple more data points for upgrade times -- the Supermicro Xeon D based box took about 3 minutes to fully upgrade (i.e. time needed to come back to the login screen). The custom built i3-8100 was about the same - I started the upgrade, walked away for a couple minutes and it was already finished by the time I returned.
-
@Gertjan said in pfSense 2.4.5 Now Available:
@chudak said in pfSense 2.4.5 Now Available:
Look at how many people having troubles ?!
No way.
Count the people that still have problems copying an iPhone to a new iPhone. That will always last. Although it's a finger in the nose trick these days.The pfSense upgrade procedure has been guided, documented and explained - with every major version update, for several years now.
Issues are not possible, because pfSense is a close-to-industrial firewall. They do not oblige you to write out that big cheque like Cisco to have it dealt with, or send one of the employees to a new training to handle the update. pfSense makes it easy : they only ask one thing : being able to read. There is no place to mess up : no one will install a new version on a system will taking down the companies or their private Internet access. For a couple of $$ you have a backup system (an old PC will do) - so the upgrade is two phase. Permits you to fast compare, check. There is a free support forum and redit and the manual and the main Negate blog, a huge channel filled up with in-depth vidoes as a guide line : what do you want more ? You really need more ? Serious ?@chudak said in pfSense 2.4.5 Now Available:
I was trying to be very carefu
As said : RTFM.
@chudak said in pfSense 2.4.5 Now Available:
did not see that system has a new
and there problems started !Like that red traffic light in front of you on an intersection ? You'll be asking for barriers on the road also now ?
More code, more text and more screen will make system less error prone. In theory, yes. But as long as systems deal with humans, there will always be issues.
Open-source software is awesome and I don't submit to the notion that because it's free it has to be of lower quality then commercial software.
Yes RTFM is great concept !
But , are you arguing against throwing a big red banner on top of the UI right after major upgrade to warn users about proper steps and point to release notes, so we have less mistakes ? (similar like we see sometimes for user surveys)
Of cause, there are will be other human errors, but this one will be prevented.
Stay well and healthy and thank you for you support!
-
I did a fresh install of pfSense 2.4.5. But after installing and setting up of pfBlockerNG, massive problems occurred described here.
-
@Bob-Dig said in pfSense 2.4.5 Now Available:
I did a fresh install of pfSense 2.4.5. But after installing and setting up of pfBlockerNG, massive problems occurred described here.
Same but worse here. No boot loader available on a fresh install.
Upgraded from 2.4.4p3 and it worked like a charm until package install.
Running on a 32core XEON setup.
-
@dennis_s
Will there be a 2.4.5-p1 relase that fixes the current problems with update of 2.4.4-p3 to 2.4.5?
Unfortunately I do not see anything on redmine.