PfBlockerNG high CPU
-
Hello!
The always-nxdomain approach should return "domain doenst exist". Maybe it is cached somewhere.
Or...
server:ratelimit-for-domain:amplitude.com 1
...might slow it down enough.
John
-
@lunaticfringe80 said in PfBlockerNG high CPU:
Nvidia Shield
Just looking at the Nvidia Shield. How is it connecting to your pfSense? I see that is capable of connecting via WIFI and hardwired via network cable. I assume your using it via network cable. Is it using a USB network interface? What kind of network interface card are you using in your pfsense? Maybe you have mentioned it, but what kind of hardware are running pfsense on: CPU, memory, network interfaces, etc?
I'm just trying to see if maybe there is something else that hasn't been hashed over that could be causing your issue?
-
@jdeloach said in PfBlockerNG high CPU:
@lunaticfringe80 said in PfBlockerNG high CPU:
Nvidia Shield
Just looking at the Nvidia Shield. How is it connecting to your pfSense? I see that is capable of connecting via WIFI and hardwired via network cable. I assume your using it via network cable. What kind of network interface card are you using in your pfsense? Maybe you have mentioned it, but what kind of hardware are running pfsense on: CPU, memory, network interfaces, etc?
I'm just trying to see if maybe there is something else that hasn't been hashed over that could be causing your issue?
I have the Shield wired. pfSense is on an Odyssey X86 with Intel NICs and Celeron J4105. Specs here.
-
Example of the DNSBL main file : /var/unbound/pfb_dnsbl.conf
local-zone: "film" "transparent" local-data: "adservice.google.film 60 IN A 10.10.10.1"What we know :
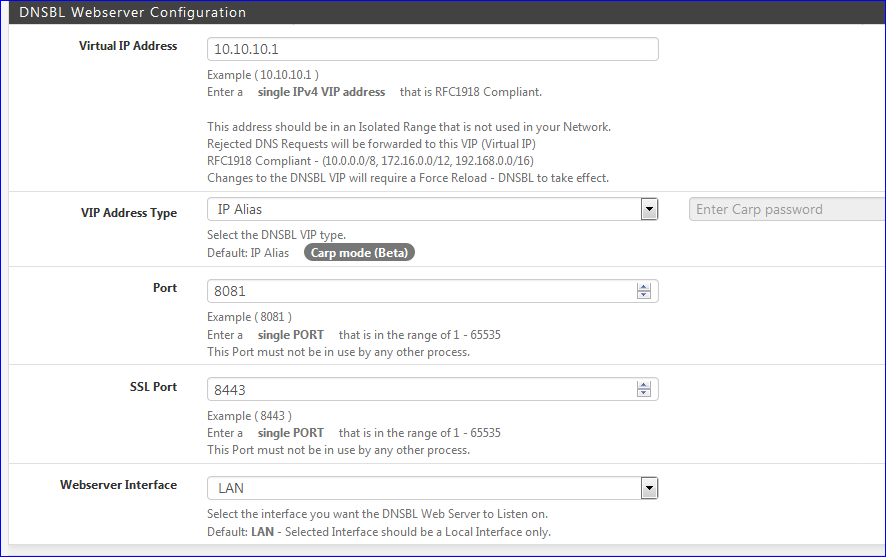
and consider this

So, in my case, the IP 10.10.10.1 has two ports being "served" by a web server : 8081 and 8443.
The idea is understandable : when you look at a web page using a web browser, all URL's on that page that load publicity from remote web sites will get pointed to 10.10.10.1 - and port 80 will get redirected to 8081 (443 to 8443 - which is nice, but won't work) : The pub 'pages'/sections, the content, will get send by .... not the pub generator web site but our internal pfBlockerNG web server that lives at 10.10.10.1.
Now consider some code on some devices : it isn't loading web pages, but other data, using other ports.
Just think about it : look at api.amplitude.com [ edit have a look at https://amplitude.com .... is this Cambridge Analytica 2 ?? ]
That's an URL - being blacklisted probably as "amplitude.com" that gets blocked .... euh ... redirected to our 10.10.10.1.
I'm sure for 99,99 that it is not requesting things on port 80 or port 443. So our NAT rules don't kick in.
It hammers 10.10.10.1 with all the processor aviable power and bandwidth because it didn't get an 'valid' answer The main issue is : the code ius written right out a pile off bll sht - and a first from you guys would be : kill the app on the device that is doing this ( and problem solved ).My idea : what about a pfSense firewall rule that blocks (orrejects) any ports on 10.10.10.1, except our 8081 and 8433.
This way there won't be 15k states because some low-bud-program goes totally haywire.
I bet the pi-hole does just that.The 10.10.10.1 web server only makes sense for http requests .... not some unknown API traffic.
edit : some one can tcpdump this box/device ? I really start be curious what these 'boxes' pomp in and out ....
edit again :
A rule like this :
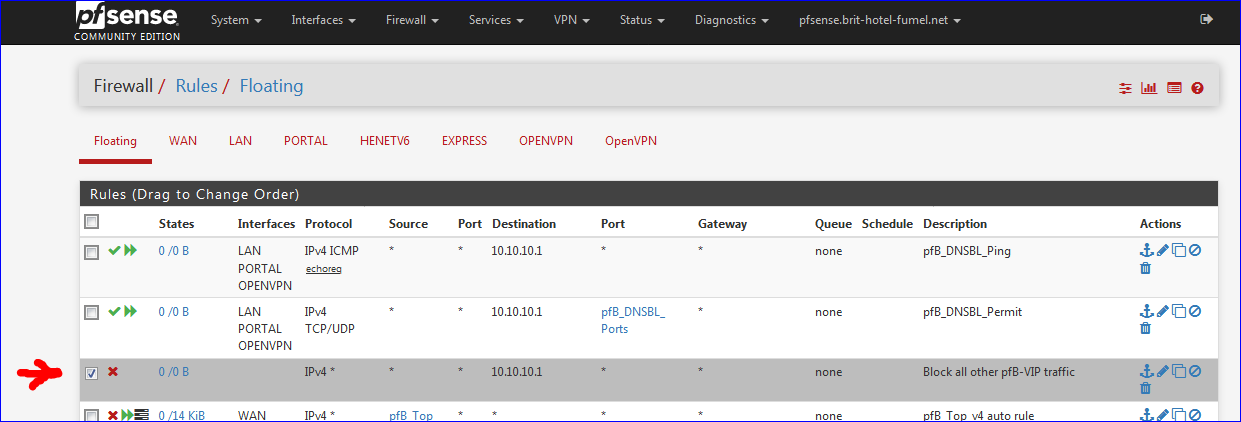
I choose the floating tab, because the other 2 rules that handle 10.10.10.1 access are already there.
I added a third rule, blocking all traffic going to 10.10.10.1 -
I've checked the state tables again to confirm the destination port and it's always 443. It looks like this, but there's pages and pages of it repeated (172.31.250.250 is my DNSBL VIP):

I like your idea, so I thought perhaps I could use the same strategy to simply block that device entirely, and gain back DNSBL logging for the rest of my network, but that doesn't work either. What am I doing wrong? This is what I have:

Another thing that's been bothering me is the disparity between the blocked packets and the total queries as shown here:

Is it normal for it to have so many more packets than queries? It appears to be throwing that percentage off since clearly 100% of my queries have not been blocked. I'm wondering if somehow the traffic is being duplicated or increased in some manner causing the unusual impact to performance?
-
I couldn't get the floating rule to work, but I was able to use the port forward rules to essentially change the sinkhole address just for the Shield like this:

This is just an improved bandaid, though. I just get DNSBL logging back for the rest of my network. I still think the disparty between blocked packets and total queries is part of the core issue.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
I've checked the state tables again to confirm the destination port and it's always 443.
This means the pfBlockerNG-devel's web server throws out the 'blocked page' on every request.
Because the Shield device is stupid enough to re try again, and again there is actually just one real solution : have it repaired/updated/moved.
A web browser wouldn't do that when it loads a page with publicity content.
Your idea to sink hole it seems good ! -
@Gertjan said in PfBlockerNG high CPU:
@lunaticfringe80 said in PfBlockerNG high CPU:
I've checked the state tables again to confirm the destination port and it's always 443.This means the pfBlockerNG-devel's web server throws out the 'blocked page' on every request.
Because the Shield device is stupid enough to re try again, and again there is actually just one real solution : have it repaired/updated/moved.
A web browser wouldn't do that when it loads a page with publicity content.
Your idea to sink hole it seems good !LOL! Have it repaired? Should I call up Nvidia and tell them I'm trying to block their device from phoning in metrics, but my chosen software to do that is getting overwhelmed, so I want them to fix it so it won't try so hard to phone in metrics?
Why the assumption it's the Shield that is broken and not pfblockerng? From where I'm sitting, it looks like pfblockerng is vulnerable to (unintentional?) DoS attacks from streaming set-top-boxes.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
@Gertjan said in PfBlockerNG high CPU:
@lunaticfringe80 said in PfBlockerNG high CPU:
I've checked the state tables again to confirm the destination port and it's always 443.This means the pfBlockerNG-devel's web server throws out the 'blocked page' on every request.
Because the Shield device is stupid enough to re try again, and again there is actually just one real solution : have it repaired/updated/moved.
A web browser wouldn't do that when it loads a page with publicity content.
Your idea to sink hole it seems good !LOL! Have it repaired? Should I call up Nvidia and tell them I'm trying to block their device from phoning in metrics, but my chosen software to do that is getting overwhelmed, so I want them to fix it so it won't try so hard to phone in metrics?
Why the assumption it's the Shield that is broken and not pfblockerng? From where I'm sitting, it looks like pfblockerng is vulnerable to (unintentional?) DoS attacks from streaming set-top-boxes.
If thats the case, then a fair sized network with IoT would bring the pfsense box to its knees fairly easy.
We wouldnt want that would we??
-
@Cool_Corona said in PfBlockerNG high CPU:
@lunaticfringe80 said in PfBlockerNG high CPU:
@Gertjan said in PfBlockerNG high CPU:
@lunaticfringe80 said in PfBlockerNG high CPU:
I've checked the state tables again to confirm the destination port and it's always 443.This means the pfBlockerNG-devel's web server throws out the 'blocked page' on every request.
Because the Shield device is stupid enough to re try again, and again there is actually just one real solution : have it repaired/updated/moved.
A web browser wouldn't do that when it loads a page with publicity content.
Your idea to sink hole it seems good !LOL! Have it repaired? Should I call up Nvidia and tell them I'm trying to block their device from phoning in metrics, but my chosen software to do that is getting overwhelmed, so I want them to fix it so it won't try so hard to phone in metrics?
Why the assumption it's the Shield that is broken and not pfblockerng? From where I'm sitting, it looks like pfblockerng is vulnerable to (unintentional?) DoS attacks from streaming set-top-boxes.
If thats the case, then a fair sized network with IoT would bring the pfsense box to its knees fairly easy.
We wouldnt want that would we??
What do you mean "if" that's the case? Have I not adequately demonstrated it to be? You don't need a fair sized IoT network, just a single STB will do. If denial is all you've got left to offer, I'll quit wasting my time providing all this testing data and go back to just using what works.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
LOL! Have it repaired? Should I call up Nvidia and tell them I'm trying to block their device from phoning in metrics, but my chosen software to do that is getting overwhelmed, so I want them to fix it so it won't try so hard to phone in metrics?
Euuh .... well, yes ! That's the origin of the problem.
It's like you trying to login to this forum, and not using the right password. You'll get an error page. A couple of milliseconds later, you try again, and again. How many states do you think you are going to use on the Netgate (pfSense) front end router / how many sessions files will get opened on their Web servers ?
The thing is, this is a script, no a human, so it chain-guns away ....
I've a fail2ban running on my mail/web/dns servers just for this, as it is a known ever going on problem. fal2ban was invented decades ago just for this. It boils down to use scripts on the server side to protect against scripts on the user's side.The thing is, the device (an app ?) uses a 443 port, which is normally a port used by a web browser to connect to a web server. The traffic will get redirected to the pfBlocker-NG's web server. And it keeps hammering, as it doesn't accept "no" for an answer.
For software that hammers, what about some a traffic shaping rules ? That's the way to protect a web server (mail server, whatever). Or, as you did, sink hole it.True, in this case, pfBlocker-NG isn't protected.
Yet ;)edit : btw : the fact pfBlcoker-NG using a web server to "serve" empty pub pages is a dead-end solution.
Nearly all traffic is https anyway, so the traffic send won't get accepted by our browsers anyway - because it's a pure MITM action.
Using a 0.0.0.0 address (Black holing) is the only solution. And simply ditching the "443" redirect. -
@Gertjan the DNSBL VIP is already supposed to be a sinkhole. I'm having to protect that sinkhole with another sinkhole. I shouldn't have to do that, especially since this sinkception breaks reporting. I didn't have to do that with pihole.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
the DNSBL VIP is already supposed to be a sinkhole
Im' not reading sink hole :
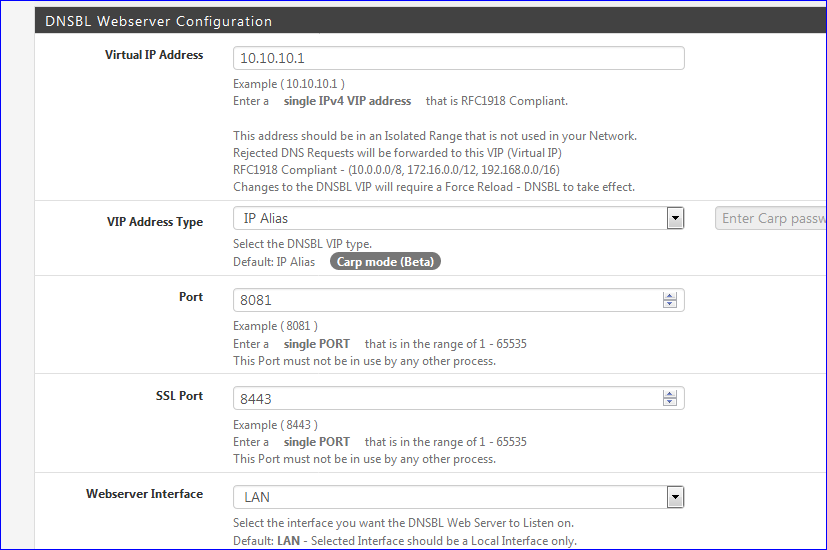
I'm reading "a web server".
Sending traffic to a web server is not sink holing it ....edit :
If you know which DNSBL feed is blocking your device, switch it here :
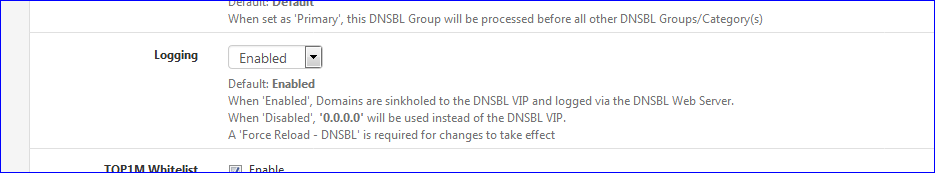
or better : make your own DNSBL feed file, with only the domain nam, the one the device is using, have it loaded at the top, and sink that one exclusivity..
-
@Gertjan A sinkhole is a destination address that unwanted traffic is redirected to using things like false DNS replies. Pfblockerng is designed to listen on its sinkhole address, which is why it is vulnerable where pihole does not. So I have to create a second sinkhole address to protect the first one.
-
@Gertjan said in PfBlockerNG high CPU:
The thing is, the device (an app ?) uses a 443 port, which is normally a port used by a web browser to connect to a web server. The traffic will get redirected to the pfBlocker-NG's web server. And it keeps hammering, as it doesn't accept "no" for an answer.
Hello!
Well, you are not really telling the device "no", you are returning a "blocked" page that isn't speaking its secret "language".
If you want to tell that particular device "NO" when it hits a blocked domain you could modify the pfsense file at /usr/local/www/pfblockerng/www/dnsbl_default.php and stick some variation of code like this at the top :
<?php
$deviant_ips = array ("192.168.0.6", "192.168.0.7", "192.168.0.8");
if (in_array ($ptype ['REMOTE_ADDR'], $deviant_ips))
{
http_response_code (404);
die();
}
?>Save it as a different name in the same folder and then load it on Firewall -> pfBlockerNG -> DNSBL -> DNSBL Configuration -> Blocked Webpage. You have to save it and reload it because it will copy it to the file dnsbl_active.php, which is the file actually used on the block page.
Of course, it still might not take "no" for an answer...
John
-
@serbus I'll try that next to see what impact it has. I don't want to be forced to sacrifice logging to solve this.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
I don't want to be forced to sacrifice logging to solve this
You don't need to : see what I proposed above.
@lunaticfringe80 said in PfBlockerNG high CPU:
A sinkhole is a destination address that unwanted traffic is redirected ...
And that already far to much. The word sink-hole is misleading.
When the DNS returns, 0.0.0.0 for a domain, the device will not initiate a connection. 0.0.0.0 isn't a valid routable address anyway. Nothing will move on the wire so pfSense doesn't get bothered - smacked in the face xx hundred times a second. The device will recognise this as a domain does not - "does not exist" and that will force to stop sending useless requests.
When the DNS returns a 10.10.10.1 (the pfBlockerNG-devel default setting) we all presume that a web browser will use port 80 - (or the useless port 443) so it can serve an "empty : non pub here page" - or whatever dummy page you uploaded.
The one @serbus proposes is very interesting. Put in the array the devices that behave badly and see what happens. -
Hello!
This might give more insight into how to deal with the shield/amplitude or other similar devices/services...
https://developers.amplitude.com/docs/http-api-v2
Pfb will probably block the link, but it is interesting...at least as long as you are the vampire and not the "donor".
John
-
@Gertjan said in PfBlockerNG high CPU:
@lunaticfringe80 said in PfBlockerNG high CPU:
I don't want to be forced to sacrifice logging to solve this
You don't need to : see what I proposed above.
Your suggestion above was quite literally to disable logging. See the word just to the left of what you suggested I switch? Also, I'm reading both sinkholed and web server.

@serbus Your suggestion to use a custom block page that sends a 404 appears to be working. So far so good.
-
@lunaticfringe80 said in PfBlockerNG high CPU:
Also, I'm reading both sinkholed and web server.
Important note : 'English' is not my native language. More somewhat between second and third.
I'm probably confounding "Black hole" with "Sink hole"'.And you're right : When you put the/a DNSBL in own it's DNDBL feed file - a manually created feed - prioritize it and then set Logging to "Disabled" for this DNSBL file then there are no more logs. Because the device will not access the network, because it can't use a obtained 0.0.0.0 address.
This is where I consider that 0.0.0.0 is a black hole (== nothing comes in (into pfSense) because nothing comes out (of the device).
Logging won't work at that moment for very obvious reasons.If you keep the VIP as the "Sink hole" then the device will "hit" the pfBlockerNG-devel web server - and leave a log trace at that moment.
With all the related consequences ..... as the device won't take no for an answer == what created the problem raised in this thread.