Confusion with PFblockerNG rules and my own and system rules
-
Hi. so i have some doubts about my Rules and how PFblockerNG is affecting them.
so I have these rules in the LAN interface tab (the only LAN interface actually)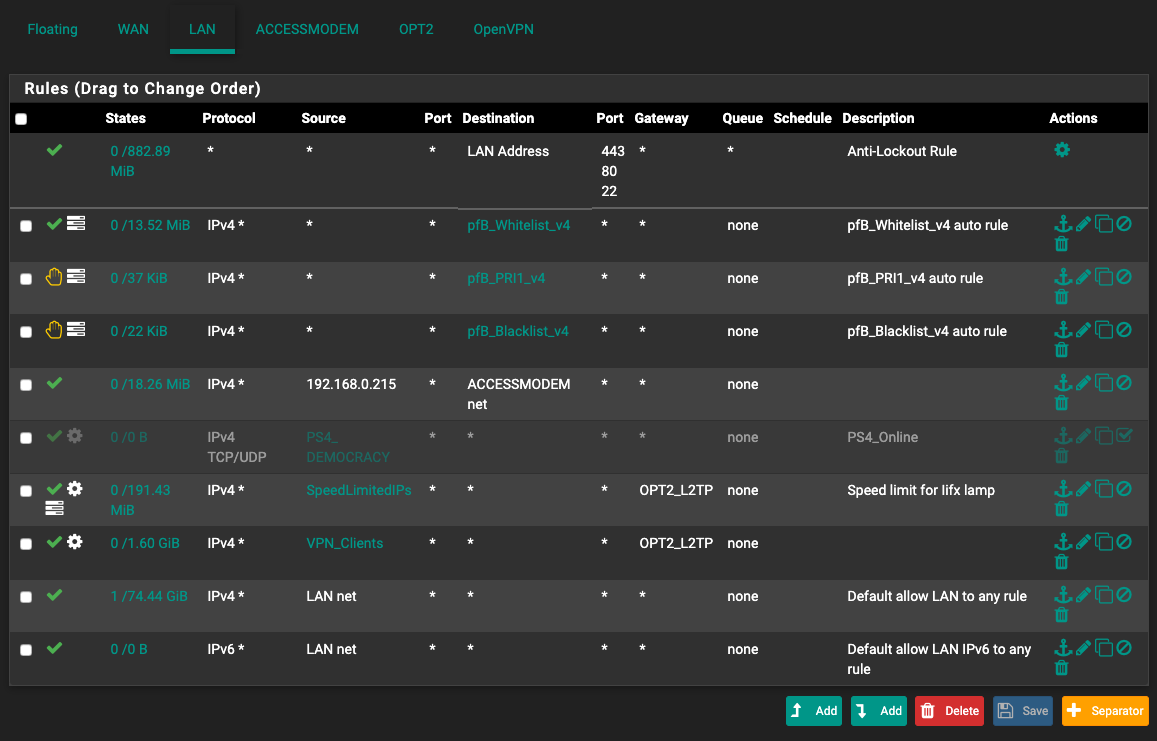
I understand that Rules are processed from top to bottom. the first 2 rules from the bottom are self explanatory. no confusion there. the VPN_Clients rule is just a rule that directs specific devices thru the L2TP gateway and slows them down to 2 mbps up and down (tested it. it works). now this is my first question. 1-lets say a device in the VPN_Clients alias tries to access an IP that is in the whitelist. what would happen? will it use the default gateway and override all of the settings in the VPN rule? or it continues to behave as expected.
I am aware that i can change the rules layout in PFblockerNG. i selected the second option but that just made things even worse.
I also cannot find any setting callled Alias native (running PFblockerNG-devel 2.2.4
2- the speedlimitedIps rule is almost the same as the VPN rule. but its just for a specific device (a lamp. dont ask why i need to route lamp traffic thru a VPN) what if this lamp tries to access a server that is listed in the whitelist? will it obey from the SpeedLimitedIP rule? or it just completely overrides everything
Thank you for your time (if anything is not clear, let me know)
P.S : The accessmodem rule is just there to allow a device (that happens to use the VPN) to be able to access my DSL modem's config page (for monitoring SNRs and such) -
Rules are evaluated top down, first rule to trigger wins - no other rules are evaluated... So if you have some device on your lan that where dest is in the whitelist, then it use your default routing... That might be your vpn, if you setup your vpn client to pull routes, and your default route is out your vpn... Look at routing table.
But once that rule triggers none of those other rules are even going to be evaluated.
-
@johnpoz Ah i see. what about floating rules?
also, i just want PFblockerNG to create the aliases but leave the firewall rules alone. i believe i can achieve this with alias native but i cant find it anywhere. And, personally, for this specific situation, what do you recommend? should i just make it not create rules on its own? or change how PFblockerNG creates its rules -
Floating rules are looked at before interface rules.. Are they marked quick - this is gone over in the docs
https://docs.netgate.com/pfsense/en/latest/firewall/firewall-rule-processing-order.html
i just want PFblockerNG to create the aliases but leave the firewall rules alone
Then do that, that is what I do as well.
-
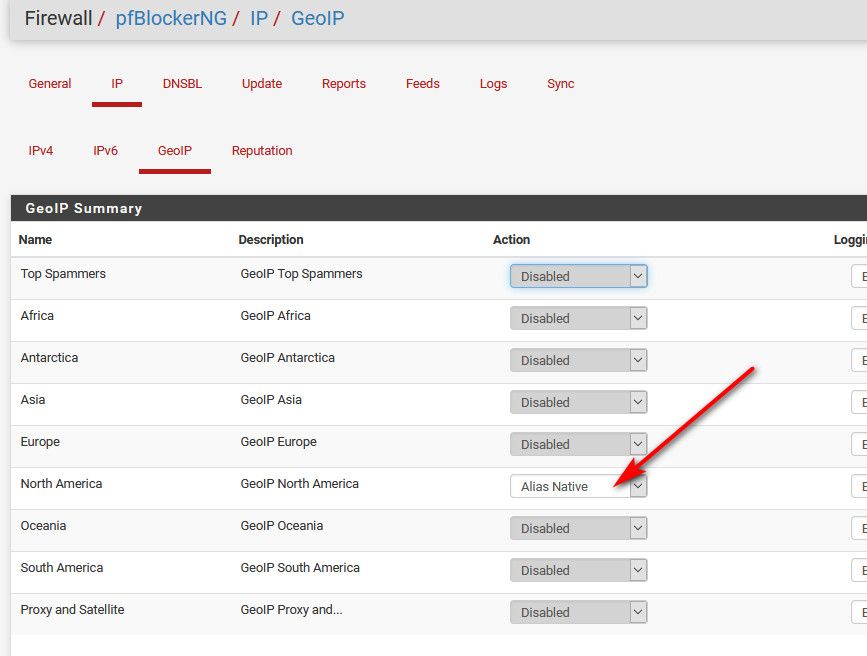
@johnpoz How did you do that? according to google, it should be under GeoIP (for some reason) and its called Alias native. for me, there is nothing there
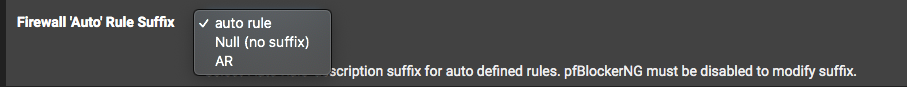 this is the closest thing i could find.
this is the closest thing i could find. -
Just don't pick any interfaces to be applied on.
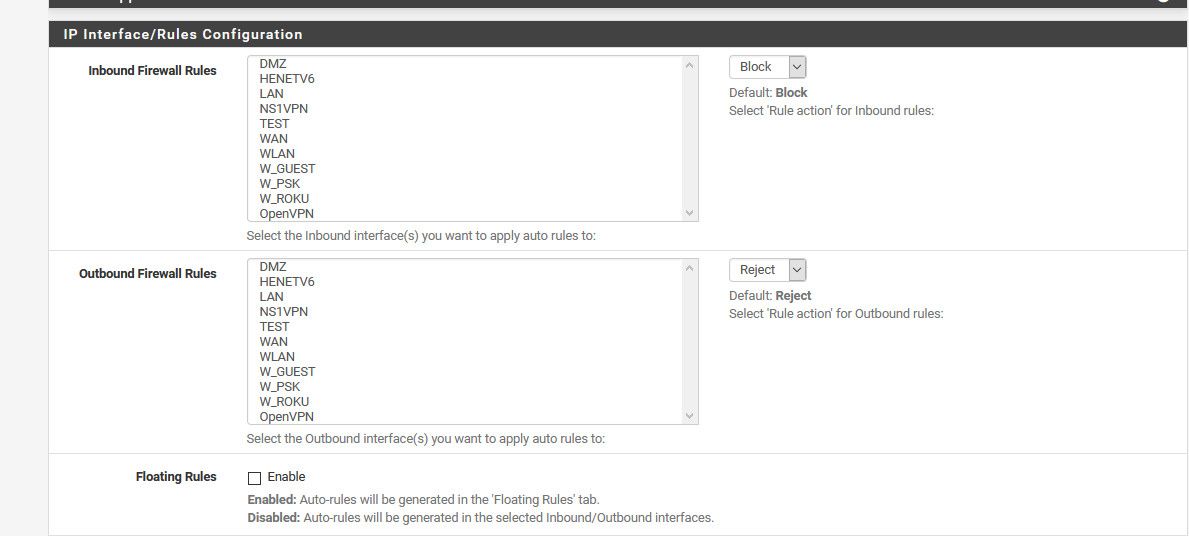
Set your lists to just be native..
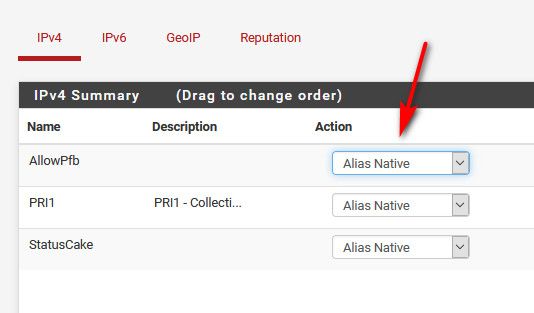
-
@johnpoz Thanks. i dont use the GeoIP section (all disabled. i have no servers that i want to expose) i assume its okay to leave it at disabled? and one last thing. lets say i add an IP to one of my blocklists. assuming that the firewall rule for it is in place, it automatically starts to work correct? thanks for your time
-
Validate that your table gets populated, diag tables.. And then put it in a rule.. You would have to clear any existing states that might be open but sure it would start working as soon as the rules are are applied... Taking into account any preexisting states.
-
@johnpoz alright. thanks man. the rules no longer interfere with my own rules.

-
@johnpoz forgive me for bothering you but even after all of those changes, (except the last one) PFblockerNG still changes the firewall rules. example :
Before running PFblockerNG update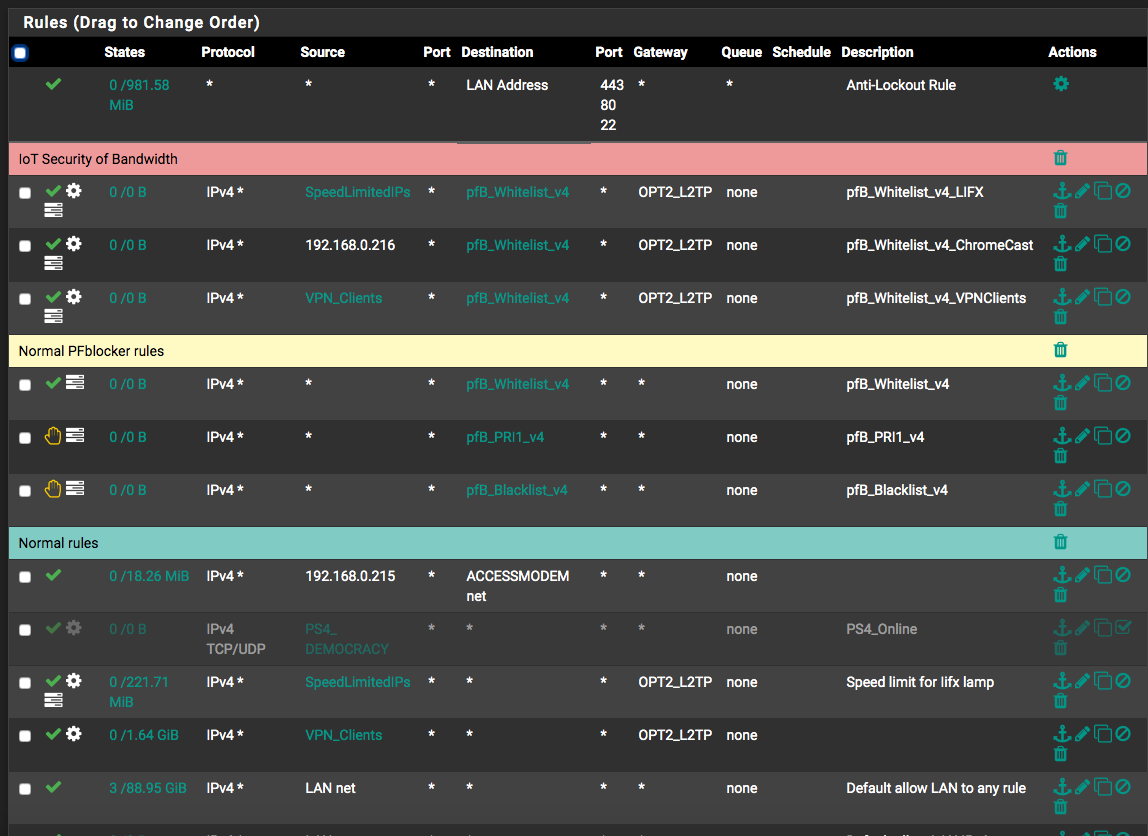
after running pfblocker update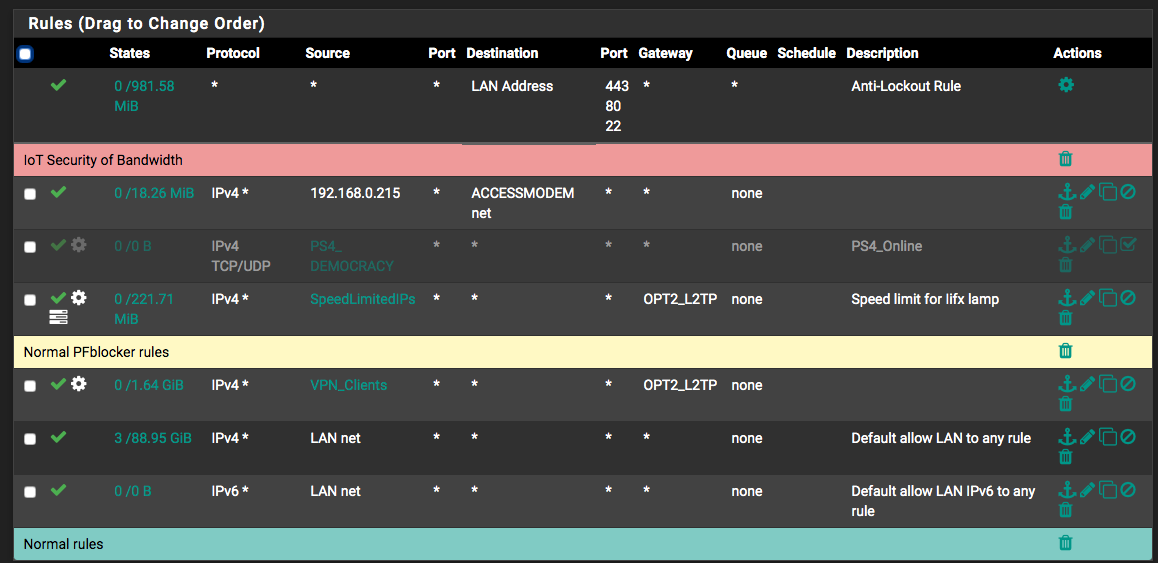
as you can see it deleted its own rules and my rules that were based on the default pfblockerng rules.
i just want it to STOP. i dont want it to even look at the rules anymore -
Showed you how to do that... I have zero pfblocker rules..
-
@lordofpc734 Oh nvm. i just had to rename the rules (changed pfB_ to pfb_) this was in some infoblock in the IPv4 page