Suricata Rules Failed to Load
-
I'll be the first to tell you that I know very little about Suricata; I can set it up, select WAN Categories, drop some rules, etc., but that's about it. I'm seeing something that I have a question about nonetheless.
In the Services > Suricata > Logs View tab, the Log File to View > suricata.log, I noticed a line that states:
<Info> -- 1 rule files processed. 30472 rules successfully loaded, 165 rules failed
Examples of the rules that failed ususally start with something like this:
<Error> -- [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - previous keyword has a fast_pattern:only; set. Can't have relative keywords around a fast_pattern only content
<Error> -- [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - "http_header" keyword seen with a sticky buffer still set. Reset sticky buffer with pkt_data before using the modifier.
<Error> -- [ERRCODE: SC_ERR_PCRE_PARSE(7)] - parse error, ret -1, string 2,=,1,1,relative,little,bitmask 0x8000
<Error> -- [ERRCODE: SC_WARN_JA3_DISABLED(309)] - ja3 support is not enabled
<Error> -- [ERRCODE: SC_WARN_JA3_DISABLED(309)] - ja3(s) support is not enabledFor brevity, an example of one of the rules is:
<Error> -- [ERRCODE: SC_ERR_INVALID_SIGNATURE(39)] - error parsing signature "alert tcp $EXTERNAL_NET $HTTP_PORTS -> $HOME_NET any (msg:"MALWARE-CNC Win.Trojan.Sodebral HTTP Response attempt"; flow:to_client,established; file_data; isdataat:!193; content:"INTERNACIONAL"; depth:13; content:!"Content-Length"; http_header; content:"Transfer-Encoding: chunked"; http_header; metadata:impact_flag red, policy balanced-ips drop, policy security-ips drop, ruleset community, service http; reference:url,www.virustotal.com/en/file/e0290c3900445dc00ca24888924e37fa6ac17ecaddc60591e32b81536b9f5ef7/analysis/; classtype:trojan-activity; sid:32607; rev:2;)" from file /usr/local/etc/suricata/suricata_32313_igb7/rules/suricata.rules at line 578
Is there anything that I need to do to get all of the rules to load successfully? Any suggestions would be appreciated. Thank you.
-
What rules downloads do you have enabled? In other words, what you "checked" on the GLOBAL SETTINGS tab in terms of enabled rules downloads. And most importantly, what have you entered into the space for Snort rules tarball filename, if anything?
-
In the Global Settings tab, I've enabled the following -
- Install ETOpen Emerging Threats rules: ETOpen is a free open source set of Suricata rules whose coverage is more limited than ETPro is checked.
- Install Snort rules: Snort free Registered User or paid Subscriber rules is checked.
- Snort Rules Filename: snortrules-snapshot-29151.tar.gz, to include entering my Snort Oinkmaster Code in the appropriate box.
I think this is the info you are looking for.
-
It is normal for quite a few of the Snort Subscriber rules to fail on Suricata. Suricata is not Snort, and it can't understand some of the Snort rule keywords. For those rules it does not support or know how to interpret, it will print an error in the log and skip loading that rule. So a number of rule loading errors is normal when using Snort rules with Suricata. How many rule loading errors you get is determined by which particular Snort rule categories you have enabled. If you attempt to enable all the Snort rules, the number of rules that will fail to load is close to 1000 if I remember correctly.
The error about JA3 support not being enabled is because that feature is not yet configured in the GUI. You can enable that option manually, if desired, by editing some PHP files. But for home use there really is no point at all for doing that.
-
Thanks for that explanation Bill. That helps. I appreciate it. I thought I may have been doing something wrong
 .
. -
@bmeeks said in Suricata Rules Failed to Load:
The error about JA3 support not being enabled is because that feature is not yet configured in the GUI.
Hi Bill,
Any documentation on how to enable this in the command prompt? Cheers
-
@propercactus said in Suricata Rules Failed to Load:
@bmeeks said in Suricata Rules Failed to Load:
The error about JA3 support not being enabled is because that feature is not yet configured in the GUI.
Hi Bill,
Any documentation on how to enable this in the command prompt? Cheers
Unfortunately, I forgot to add that option to the GUI. However, if you want to use it, find this section in the file/usr/local/pkg/suricata/suricata_yaml_template.incstarting on line 356:I will fix this in the next GUI package update.After further research, my rusty, old memory recalled that the setting is actually under the APP PARSERS tab. It can be enabled there. See an updated post down below.
-
After some subsequent research, I discovered this setting is already in the GUI. So disregard (or undo) the changes to the PHP source file I mentioned earlier. I forgot where I had placed it ...
 .
.It is on the APP PARSERS tab for the interface, down in the TLS Settings section. It is off by default, but can be enabled by checking the box as shown. Restart Suricata on the interface after making this change so that it will see the new setting.
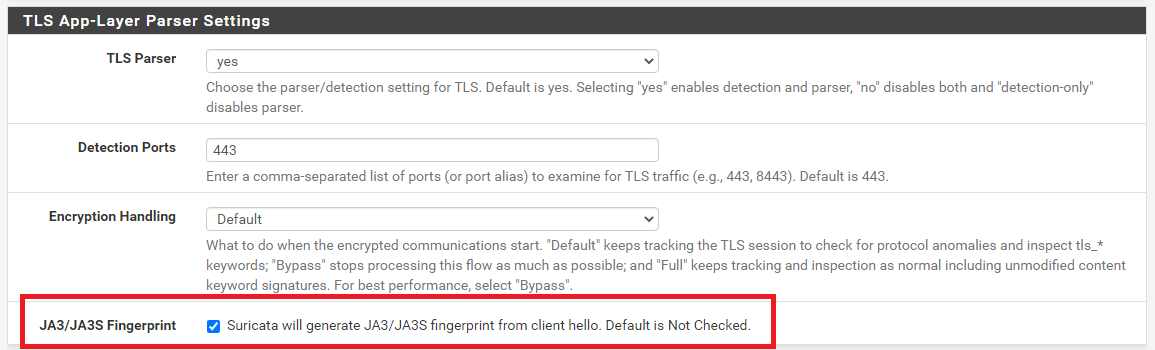
-
@bmeeks Thanks Bill,
I actually had a sneaking suspicion I'd seen it and had it in my to do list to check it so thanks for confirming.