Intentional Asymmetric Routing to a VLAN.
-
All,
I searched the forum, but cannot find what I am looking for. I am relatively new to pfsense (and LOVE IT!).
I have an SG-5100 set up with the obligatory LAN and I have set up one VLAN for a Guest Network to access the internet from a dedicated AP, but nothing else.
However, I would like to be able to access the AP on the VLAN from LAN to administer it.
Particularly, I am set up on 192.168.2.x for LAN and on 192.168.9.x for the VLAN.
If I could could access all of 192.168.9.x from all of 192.168.2.x but not visa versa, that would be great. However, if I can just punch a hole from let's say 192.168.2.100 (my computer) to 192.168.9.10 (the Guest AP), that would b sufficient.
If there is already a thread, please point me to it. Or if you know how to set it up please elucidate the steps and rules for me. THANKS!!
Phizix
-
what does any of this have to do with asymmetric routing ?
you just need to setup firewall rules to block? right?
-
If I used the term wrongly, then forgive me. I want it to act as a one way valve. I don't want any one on the AP to be able to get to my local LAN, but I do want to get to my AP interface to manage it.
That seems to be to be a form of routing - one segment to another, but not in both directions (i.e "asymmetric").
Regardless, if I set a rule on LAN to allow access to Guest, will it allow the AP to respond, but not allow Guest to talk to the LAN?
Phizix
-
Asymmetric routing simply means packets in the different directions take differenet paths. That's all. If you try to block packets in one direction by routing only in that direction, then you will break everything, as you'd not see anything coming back. What you want is a rule to block connections in one direction, which is typical behaviour for a firewall.
-
This really out it is out of the box..
When you create your lan, it defaults to any any rule - lan can go anywhere.
When you create a vlan or another network interface, no rules will be put on that interface... So it would not be able to create any unsolicited traffic into your lan network. But your lan network could create traffic into vlan without be blocked.
All that would be required to block your vlan from talking to lan, would be firewall rule(s) to block what you don't want before you allow to internet..
Here is example setup.
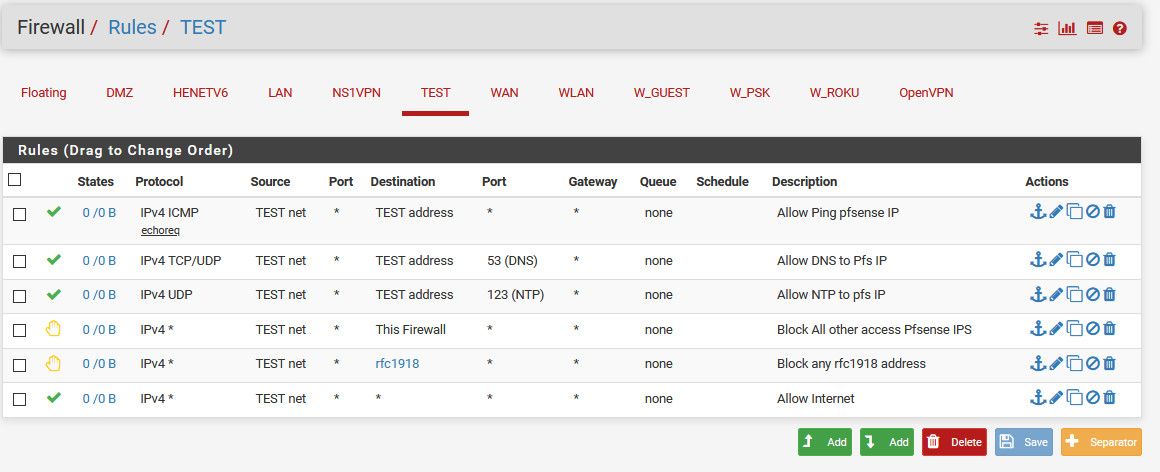
So my rfc1918 alias contains all the rfc1918 space 192.168/16, 10/8 and 172.16/12
So stuff in test (your guest vlan lets say)
Can ping pfsense IP in this vlan
Can ask pfsense via its vlan IP for dns
Can ask pfsense via its vlan IP for ntp
Now all other traffic to any other firewall IP, be it lan, wan, vpn, whatever - is blocked!
Now any traffic to say lan, which is a rfc1918 address - in my case 192.168.9.0/24 would be block... But anything else, ie the internet is allowed. -
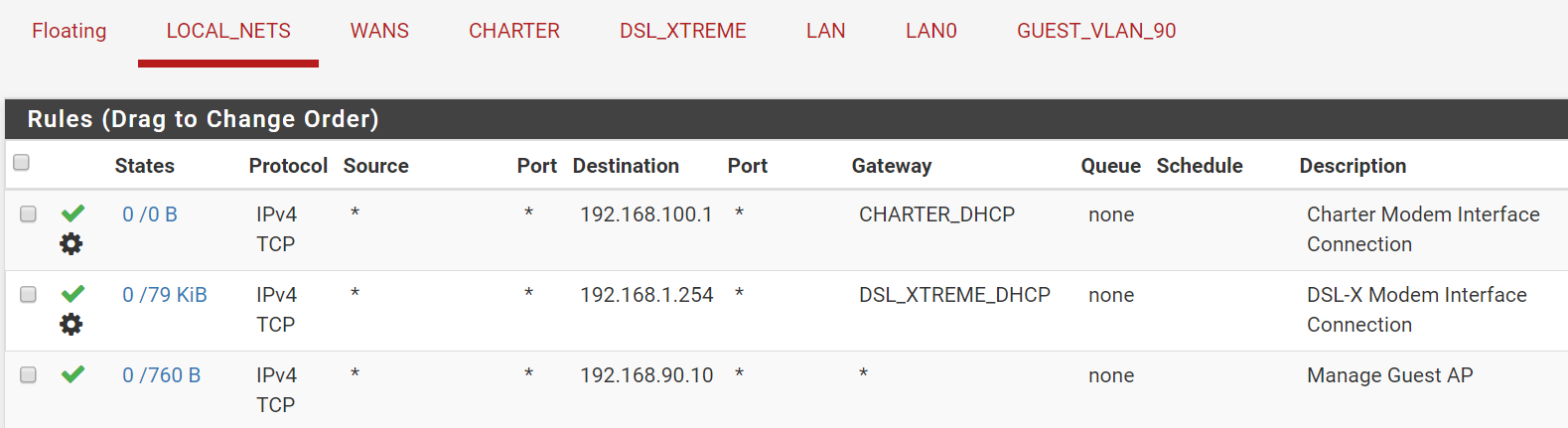
John, I thought it was out of the box too. I forgot that I moved to 192.168.0.x for my main LAN and the VLAN to 192.168.90.x. I say that so the images will make sense.
My interface Group "LOCAL_NETS contains LAN & LAN0. On that Group I have this and a bunch of other rules following:
And on GUEST_VLAN_90
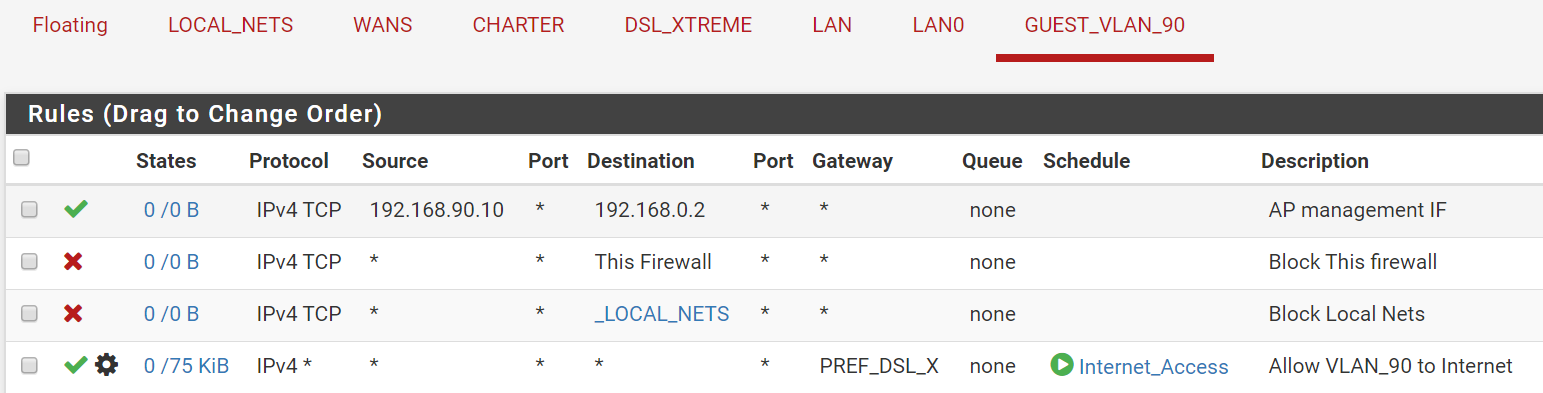
I thought these two rules (rule 3 in pic 1 & rule 1 in pic 2) would allow me to access 192.168.90.10 from 192.168.0.2, or am I missing something?
The AP is not a pfSense firewall. It is a Netgear router that I have pressed into service as an AP. The SG-5100 is at 192.168.0.1 from my machine.
Let me check that the AP is properly responding if I connect via WiFi.
THANKS.
Phizix
-
I don't even have to look at your rules - your forcing shit out gateways... So shits not going to work!! You don't get to other vlans via charter_dhcp gateway.
You have groups setup?
Rules are evaluated top down, first rule to trigger wins, no other rules evaluated.
Keep in mind host firewalls as well, I can allow traffic all day long - if the host trying to talk to firewall doesn't allow it - not going to work.
-
You need to look again. That is to a single IP address that is only accessible from the Internet side of Charter. It is the Charter Modem and similarly for the DSL-XTREME Modem. Those top two rules work fine!!
Sorry but that pisses me off. You didn't even look to see what they are doing and their descriptions.
In order to look at Charter's modem you have to send the request to that private IP on the Charter gateway. Similarly for the DSL-Xtreme Modem IP. That is all those top two rules do.
I have two WANs and this forces requests for their respective modem to the correct WAN for their gateway. The traffic is later balanced between the two gateways and sometimes the request is sent to the other gateway and it will not go to the correct modem and will not load the Modem Management screen.
Surely you have experience with ISP modems that have an access address. If you look it up on Goodle you will see that Spectrum's [Formerly Charter] Modem IP is 192.168.100.1 for most of the Motorola / Arris DOCSIS Modems. In any case that is where mine is and it is on the WAN side of the firewall.
Did you see my note that I have other rules below that send all other traffic out the balanced gateway for all other Internet traffic.
Everything else is working as expected.
I understand that it is top down. It intercepts ONLY those first two addresses. Then everything else passes them by since they DON'T MATCH. I can't do it in reverse.
Phizix
-
I did check to see that if I connect to the Guest network WiFi on my Laptop, I can configure the AP so it is up and it is on 192.168.90.10.
I also confirmed that I cannot connect to the SG-5100 firewall management interface because of the block rule on GUEST_VLAN_90. And I cannot connect through from the laptop to 192.168.0.2 or any other host on that subnet, BUT I can connect to the Internet perfectly well (as long as it it is with the scheduled hours).
I do have a way to administer it, but it would have been nice to not have to pull out my laptop and manage it from my desktop like all of my other devices.
Phizix
-
Dude I did look ;) That was just my gut reaction... These rules are really basic, take your traffic run through your rules.. What will happen.. This isn't rocket science..
You have a source, you have a dest, you have a dest port.. as an option.. You have protocol be it tcp/udp, etc.. Its not that hard..
Traffic is evaluated as it enters an interface..
If you want me to walk through your rules for you - give me the details of the traffic - what is the source IP, what is the dest IP and port and protocol.. And I will tell you if are allowing it or blocking it.. But you can do that yourself..
-
John, I don't understand your last question. The details are right in the rules shown. I am trying to reach 192.168.90.10 from 192.168.0.2 (as shown in rule 3 of the LOCAL_NETS and rule 1 of GUEST_VLAN_90).
I actually did a little experiment and set the top rule of LOCAL_NETS to allow any to any and similarly for GUEST_VLAN_90. Still no joy. My assumption is that the Netgear box is unhappy with a source that is not on the same subnet it is on, so I don't think there was any issue with my rules, but with the AP itself.
Sorry for the irritation, I had just worked to get the Modem access to the two modems working with the Balanced gateways and it is working great. I can consistently get them to come up now.
In any case. I will do some further experiments, but I am pretty sure it is on the NetGear side.
Thanks for the insights, because they did lead me to try the experiment that pointed to the AP itself.
I suspect that it will have to NAT to GUEST_VLAN_90 to get it to respond.
Phizix
-
@Phizix said in Intentional Asymmetric Routing to a VLAN.:
the experiment that pointed to the AP itself.
Does your AP have a gateway set? You can not talk to a device from another vlan/network - if that devices doesn't know how to get off its own network
-
That is correct. The AP is pointed at 192.168.90.1 as it's gateway. The LAN is pointed at 192.168.0.1 as it's gateway.
I am coming to that conclusion myself. So how to get it to make the translation from 192.168.0.x to 192.168.90.x?
Phizix
-
You don't have to do anything.. Other than allow it.. If your lan which is 192.168.0/24 is allowed to go to 192.168.90 (ie the any rule) then it would just work.
As long as the AP has a gateway to get back (pfsense) and not doing any firewalling of its own.
Simple test, sniff on on this vlan where your AP is.. Do you see pfsense sending the traffic?
If your forcing lan out some gateway (ie some vpn) via a policy route - then it wouldn't be able to get to your 192.168.90 network. Put a rule above where you force traffic out a vpn that allows access to the 192.168.90 network.
example: one of my access points is on 192.168.2.2, my lan is 192.168.9/24 I have a rule on my lan that allows everything..
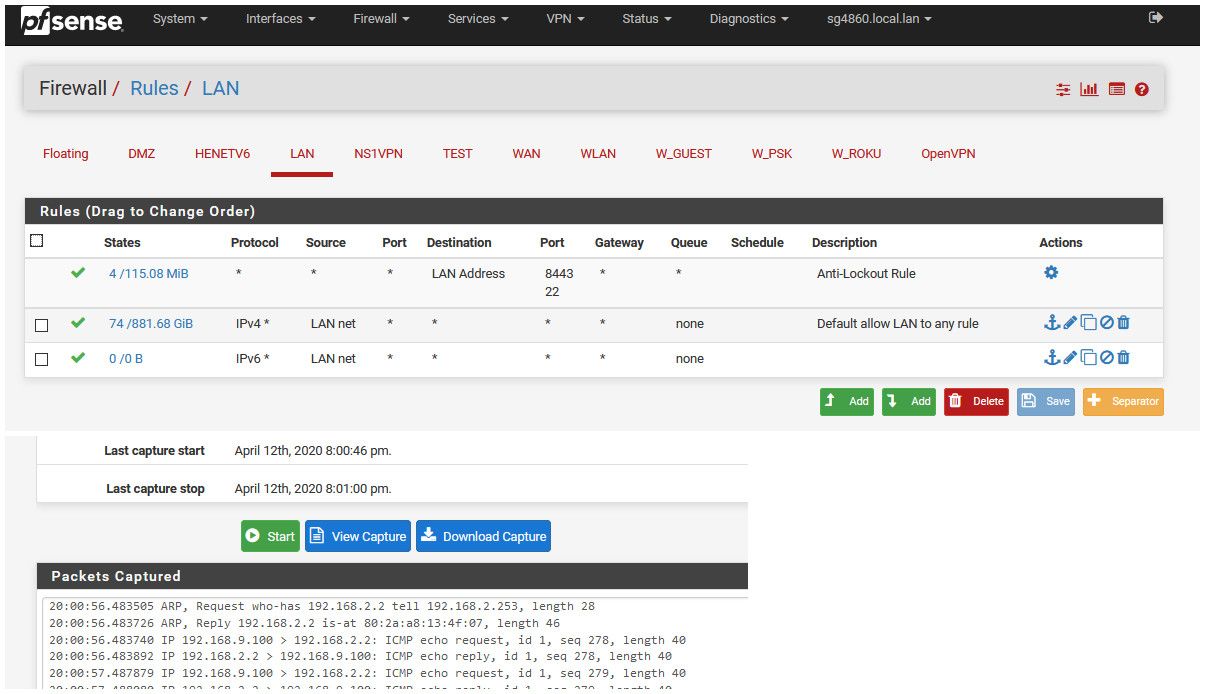
So doing a ping from my 192.168.9.100 box to 192.168.2.2, you can see pfsense arp for the mac of the AP.. And then allowing the traffic.
There is nothing else to do.. This is out of the box.. You could have zero rules on this other vlan and the traffic would be allowed. The network is directly attached to pfsense, so it knows how to get there.
Your rule that you show only allows traffic to 90.10 tcp.. Are you trying to ping, that rule would not allow ping, etc.
Again rules are evaluated top down, first rule to trigger wins, no other rules are evaluated. If you have some rule above that forces traffic out a gateway above a rule that allows what you want, that lower rule would never be evaluated.. And the traffic would be sent out gateway (that can not get there)
If you want me to help.. Be clear an precise.. Show me the traffic you are trying to send.. The rules on the interface the traffic would first hit pfsense. All of them - do you have any floating rules that would be evaluated before your interface rules?
-
DOH! You are right it is set to TCP (copy error), but none of that solved it.
I mentioned earlier that I moved to the top of LAN the default any to any rule and re-enabled it and copied it to the GUEST_VLAN_90 interface also, but no joy.
Those were IPv4*.The NetGear AP (I am using it in router mode attached to one of it's switch ports) works fine for internet access for the WiFi attached devices.
I suspect that internally the NetGear AP is rejecting anything that is not on it's own subnet.
Sanity check - I just repeated the the IPv4* any to any on both LAN and GUEST_VLAN_90 interfaces from their respective interfaces. Nothing. LAN shows data go out, but nothing comes back on the GUEST_VLAN_90 interface.
Phizix
P.S. Thanks for the help. Maybe some kind of inter LAN NAT.
-
@Phizix said in Intentional Asymmetric Routing to a VLAN.:
Maybe some kind of inter LAN NAT.
If your AP is blocking access from other networks, then sure you could always source nat the traffic so your AP thinks the traffic is coming from the pfsense IP in that vlan.. This is a simple outbound nat.. Here I do this to talk to one of my devices that doesn't have a gateway.
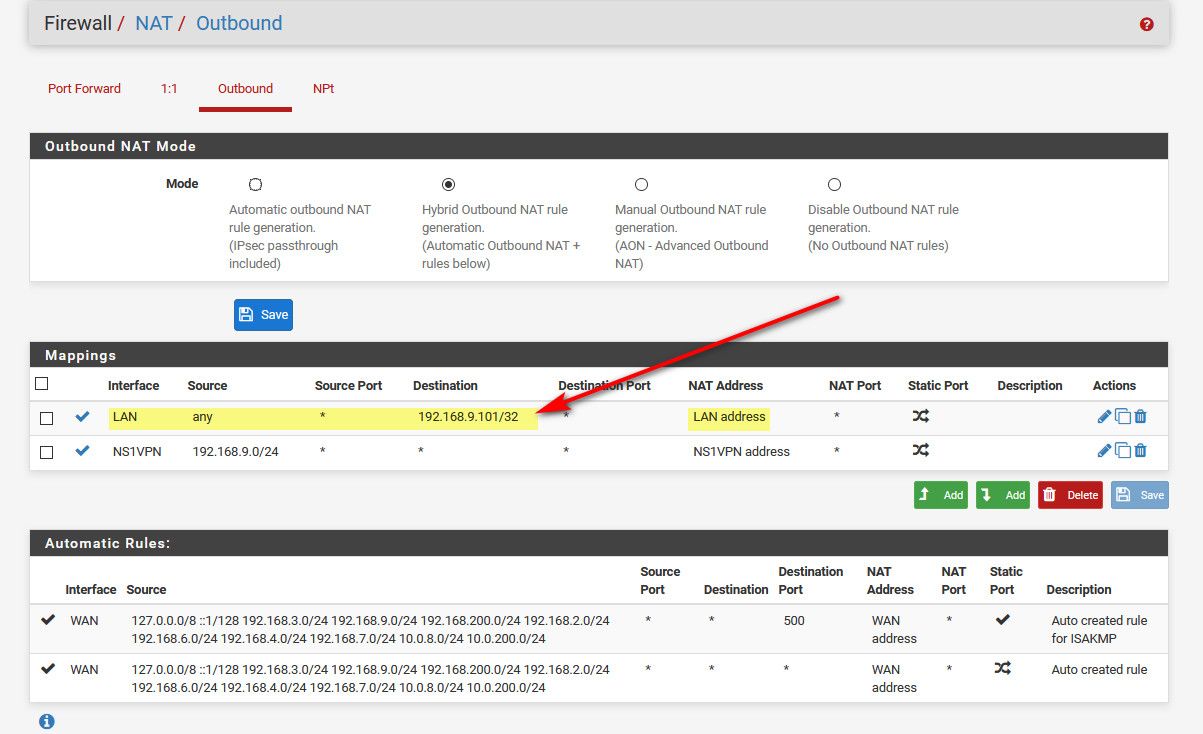
This allows me to talk to this device from my VPN.. Because that device doesn't have gateway to know how to talk back.
If your device has some firewall that prevents access from other vlans - the "correct" way to fix that would be to allow that traffic on the devices firewall.. Only if there is no way to do that would I suggest you source nat. To trick the device into allowing the traffic.
-
You really think a NetGear Wireless router is sophisticated enough to have those kinds of settings? Awww, hell no! LOL!! Unfortunately not. I will try the outbound NAT.
Any matching firewall rules that need to be in place? Same as you showed previously?
Phizix
-
No I don't think that - but just answering your question ;)
-
OK over wireless I looked at the LAN setup on the AP and it has NO gateway. Only on it's WAN interface can you set up a gateway, which I am not using.
I will have to pick it back up tomorrow. I added the outbound NAT with "IPv4* any to any" rules on both interfaces, but still no joy.
I will have to pick it back up tomorrow evening after work. I will do some investigating on my own to see why it will not connect to it. But many thanks for all the advice.
If I figure this out on my own, I will post back so others can benefit from the solution.
Phizix
THANKS AGAIN!
-
Yeah if your using a old wifi router as AP, most native firmware does not allow for setting a gateway on lan side... You might be able to run some 3rd party (openwrt, dd-wrt, etc) they allow it.
If not its a simple source nat to allow such a setup to work.. Or you just admin from that same network or via wifi.
Other option - is some native firmware allows you to set a route - even if not a default gateway, where you could set a router to your lan network. That it would use.
To be honest the correct solution - which cost money ;) Is to get a real AP when your wanting to move into more complex setups where everything is just one flat network. Vs just leveraging some soho device not meant for such setups.
Get real AP that can do vlans, and real switches that can do vlans, etc. It can be done on the cheap, when budgets are limited.