Traffic blocked although rules would allow
-
I am seeing tons of traffic being blocked in the FW logs even if I have rules setup to allow such traffic.
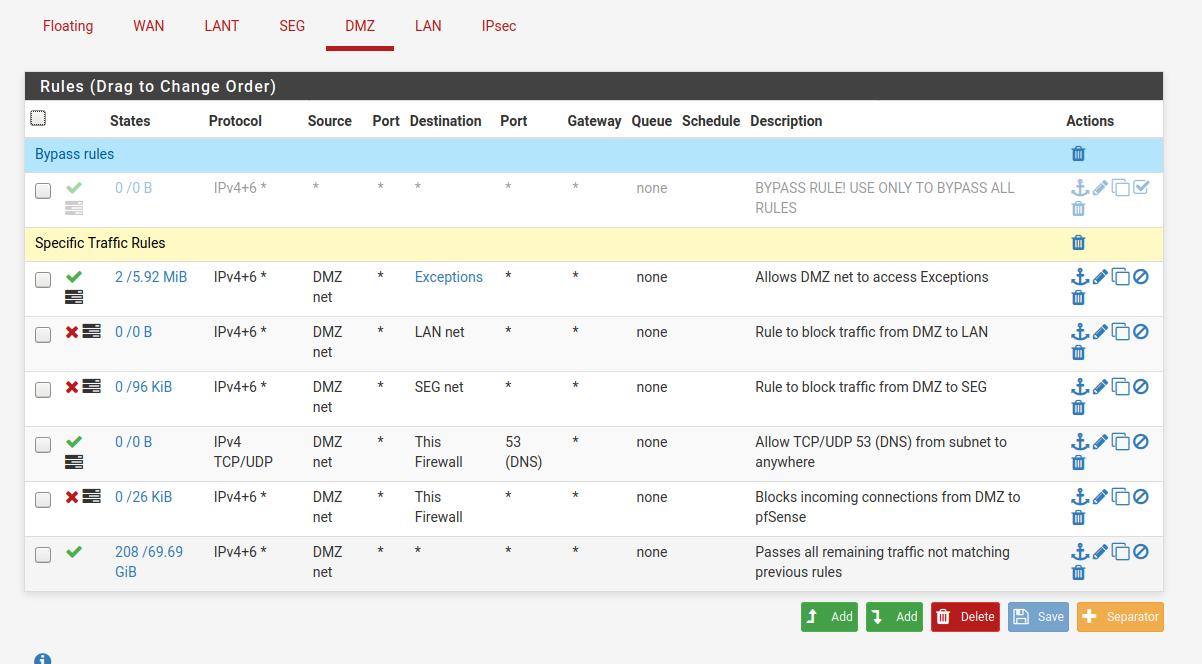
This happens on a "DMZ" interface which is designed to block traffic going to the other interfaces, but allow anything else.Rules are setup as follows:
- Allow traffic to some hosts (exceptions), these are printers, scanners, etc. Using an alias.
- Block any kind of traffic going to LAN interface
- Block any kind of traffic going to SEG interface
- Allow TCP-UDP on Port 53 going to pfsense (so hosts on DMZ can use DNS)
- Block any kind of traffic going to pfsense (to minimize chances of compromising pfsense)
- Allow anything else.
Eveen with the last rule, the logs arre filled with blocked traffic on DMZ. The rules setup has NOT changed in several months, and this week I started experiencing severe connectivity issues on clients connected to DMZ.
The blocked traffic shows descriptions such as
@9(1000000103) block drop in log inet all label "Default deny rule IPv4"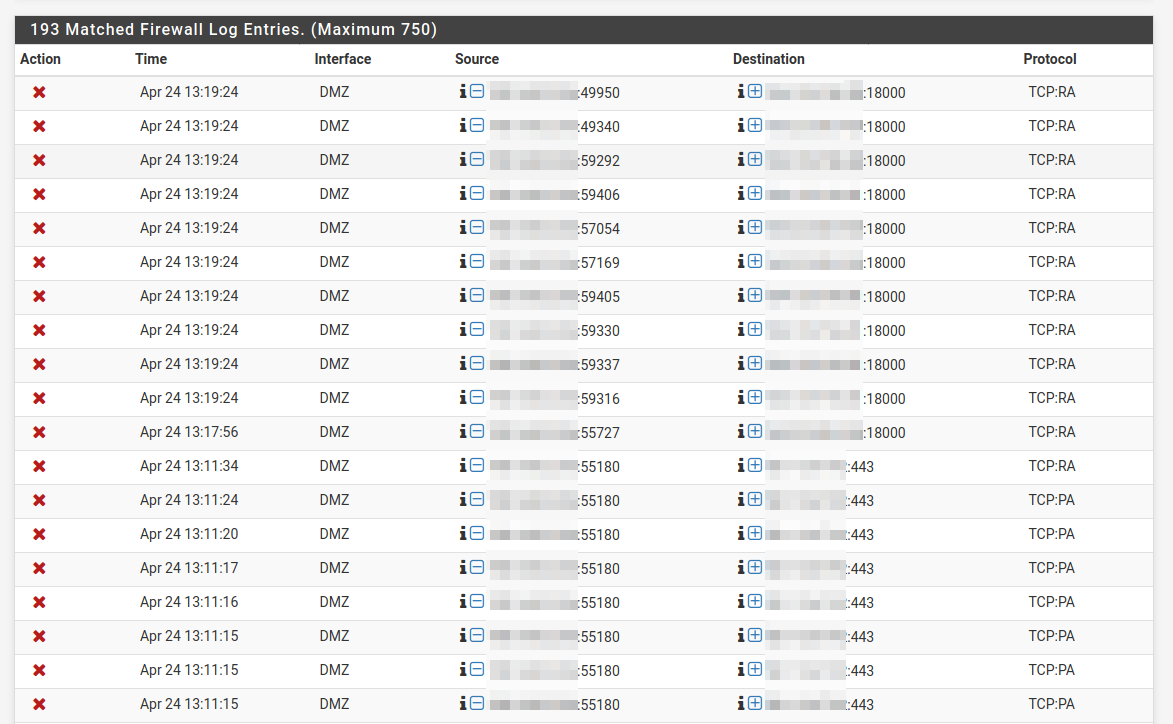
What would be the root cause of this? -
Out of state traffic most likely, asymmetrical traffic flow, etc..
https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-for-legitimate-connection-packets.html
You got a bunch of RA there, and PAs
-
Please excuse my lack of knowledge...
A couple questions.
-
Out of state, asymmetrical, etc.... I am pretty sure that I didnt use to see RA & PA packets like these... But I may be wrong. Is it anything to be concerned about?
-
I do not control the client's configurations connecting to DMZ and the "experience" thru pfsense needs to be as transparent as possible with the following concepts: dont communicate with my private LAN's, and dont touch pfsense. Anything else is allowed. Is there's anything wrong with my FW rules?
-
I am passing OpenDNS's servers to the DMZ clients via ther DNS servers options in the DHCP server. Can I safely delete the rule for port 53? I like to keep the rulesets as simple and straight forward as possible.
Big Thanks!!!
-
-
OK did some more tests.... and found some interesting stuff.
- Seems like more than one client on DMZ will cause similar entries in pfsense's firewall logs. At least, I know this is not isolated to a single machine.
When one of these client (laptop) is connected to DMZ via wired connection (using ports 23 or 24 of my Procurve switch), I dont see any RA, PA or TPA log entries...EDIT: False... I just refreshed the logs and still see tons of these entries while laptop is wired.
Some background on network & pfsense setup:
- LAN (PVID100), SEG (PVID200) & DMZ (PVID 300) are VLAN's based on OPT1 physical interface.
- DMZ clients gets an IP under DMZ by either connecting to ports 23 or 24 of the switch, or by connecting to a Unifi AP which broadcasts 2 tagged networks (LAN + DMZ).
- Port 02 of the switch carries most of the clients and belongs to all VLAN's but is not tagged so to allow IoT...
- Port 01 is tagged to be able to "talk" to pfsense's VLANs which are tagged.

VLAN configuration on the managed procurve switch is:
VLAN Configuration: Port Aware PVID Ingress Filtering Frame Type 1: enabled none disabled Tagged 2: enabled 100 disabled All 3: enabled 100 disabled All 4: enabled 100 disabled All 5: enabled 100 disabled All 6: enabled 100 disabled All 7: enabled 100 disabled All 8: enabled 100 disabled All 9: enabled 100 disabled All 10: enabled 100 disabled All 11: enabled 100 disabled All 12: enabled 100 disabled All 13: enabled 100 disabled All 14: enabled 100 disabled All 15: enabled 100 disabled All 16: enabled 100 disabled All 17: enabled 100 disabled All 18: enabled 100 disabled All 19: enabled 100 disabled All 20: enabled 100 disabled All 21: enabled 200 disabled All 22: enabled 200 disabled All 23: enabled 300 disabled All 24: enabled 300 disabled All Entries in permanent table: 1: 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20,21,22,23,24 100: 1,2,3,4,5,6,7,8,9,10,11,12,13,14,15,16,17,18,19,20 200: 1,2,21,22 300: 1,2,23,24Did I miss something or misconfigure something in there? This setup has been operating for over a solid year now, and before last week, I never truly had any issues to be honest. I also dont see any problems with my LAN clients The only clients showing the log entries are those connected to the Wifi "DMZ" SSID... I never really trusted the Unifi firmware for multiple SSID broadcast and VLAN tagging....