How to trunk the OPT interface on SG-1100.
-
I am new with PFsense, i just got my SG-1100 last week.
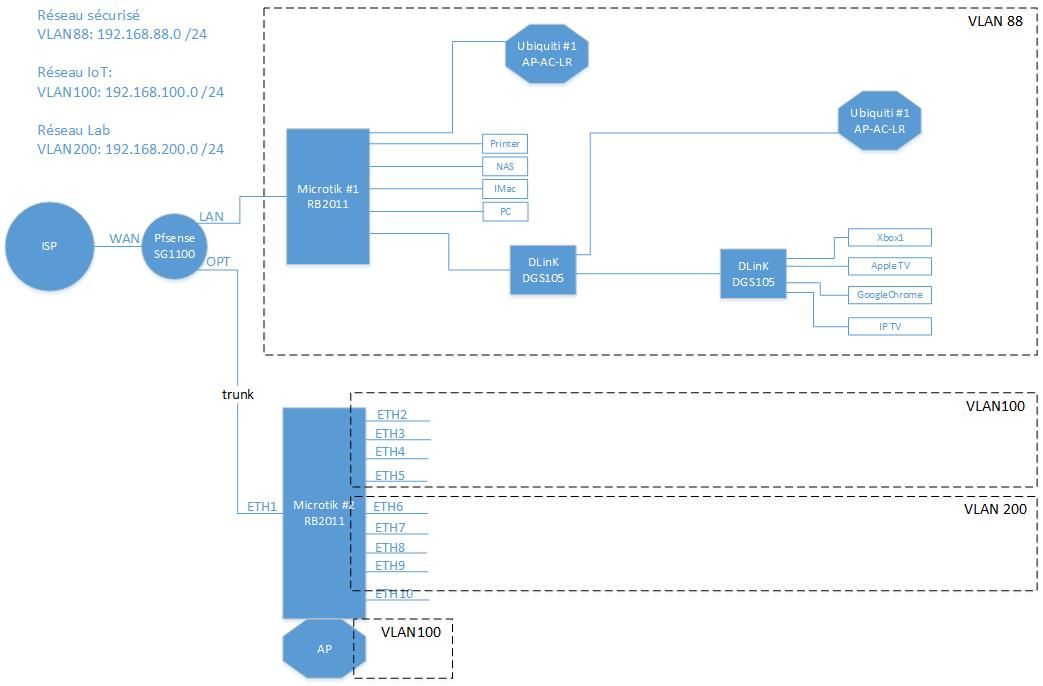
I want to use SG-1100 LAN and OPT physical interfaces independently:
On the physical LAN interface, i will use a single network: 192.168.88.0 /24 (this one is OK)
On the physical OPT interface, i want to use 2 networks: vlan100 et vlan200 (192.168.100.0 and 192.168.200.0) /24I believe i'm missing a configuration in the: interfaces/switch/VLAN since I did not understand how does the "Members" feature works in PFsense...
-
Did you create the VLANs and assign them to new interfaces? https://docs.netgate.com/pfsense/en/latest/book/vlan/pfsense-vlan-configuration.html (they are treated as separate interfaces so have their own firewall rules)
-
This is no different than any other trunk port to any other switch except that the switch is built-in to the SG-1100.
Make the VLANs on mvneta0
Assign them to pfSense interfaces. That will cause that traffic to be tagged to the internal switch on port 0 (The uplink interface from the switch chip to pfSense).
Then, on the internal switch, create the VLANs. Make them tagged on ports 0 (the uplink) and 1 (The OPT1 port).
Set the switch to tag the same VLANs and cross-connect it to the OPT1 port.
-
@teamits I adjusted the firewall rules for each VLAN + I did add DHCP services for each VLAN. I think I did correctly the VLAN \ interface assignments but not sure of the procedure. I have a hard time understanding the Member meaning...
I did not yet go to console mode, just stayed on the GUI, is it easier from the console? -
No it's not easier from the console. If you do it from the console the changes won't stick anyway.
In your case the VLAN membership needs to be 0 tagged and 1 tagged.
This is just like adding member ports to any VLAN on any switch in the world. It is just 802.1q.
-
This post is deleted! -
@Derelict Thanks for your reply. Does that make sense:
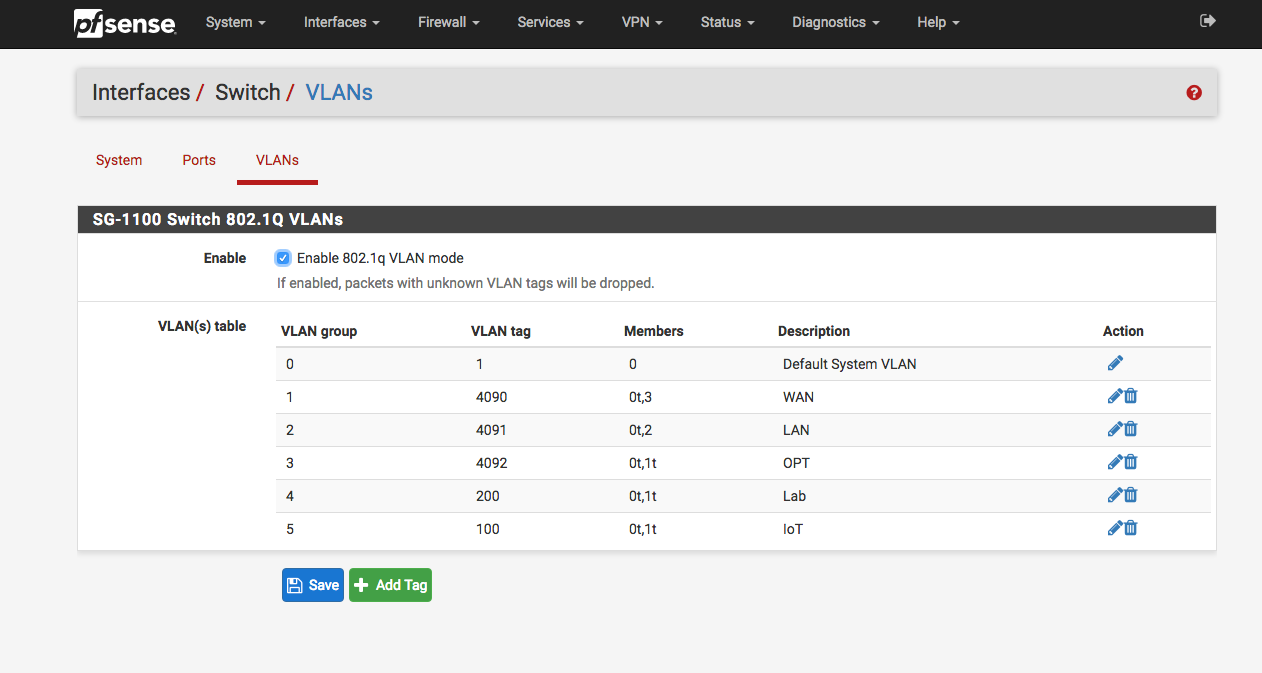
-
Looks fine. Is the switch connected to OPT set to tag VLANs 100 and 200?
-
@Derelict It all works now! thank you, your "Make them tagged on ports 0 (the uplink) and 1 (The OPT1 port)." line made that possible.
What is this 4090,4091 and 4092 VLANs? Is their any packet tagged with those ? Can we remove it?
-
If you do not need 4092 on switchport 1 (OPT) it can be removed. 4090 and 4091 are the untagged VLANs for the WAN and LAN ports. You probably want to leave them alone.