Open wide rule vs specific rule
-
As an IT in my organization I created my own vlan (management vlan) to simply the process of connecting to different vlan, set firewall rules to grant access to all vlans. The way I see the firewall should work is that there is no need to explicit set individual rule above the wide open rule ( the last rule in the picture) since everything is being taken of by this rule. See image below
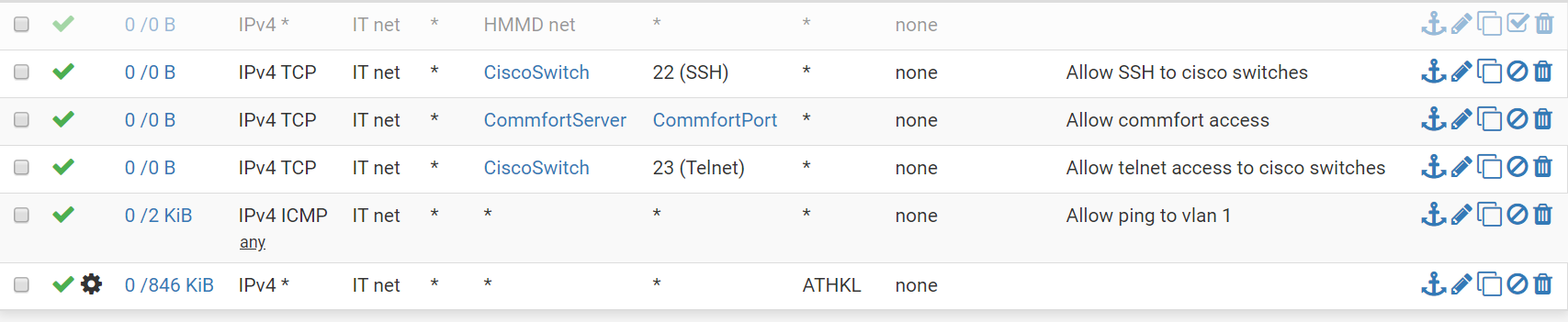
-
Yeah those rules are pointless.. Since you have an any any rule there at the bottom...
Rules are evaluated top down, first rule to trigger wins, no other rules are evaluated.
-
Thank you very much for your reply ..
But it seems that it did not work that's why I setup specific rules. I tried ssh from vlan to cisco switch on another vlan and it couldn't that's why i setup ssh pass rule ..
thanks
-
Well what were the rules on the other interface.. Traffic is evaluated as it enters a interface from that network.
The only interface that has a any any rule on it by default is the first lan interface... If you bring up other interfaces they would have no rules on them..
-
see below rules on one of the interfaces ....
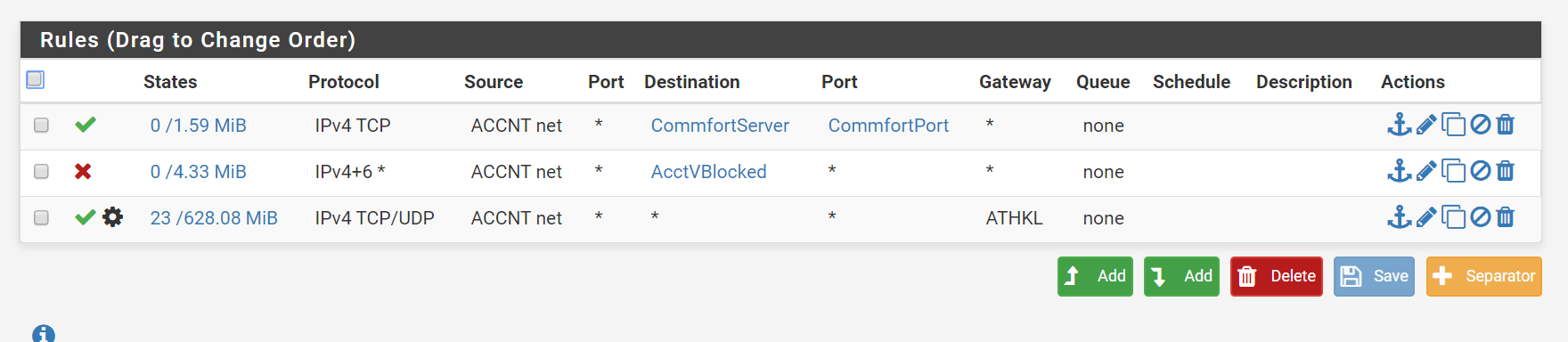
-
The last open rule has the ATHKL in it - I'm assuming that's your gateway.
Traffic from IT Net to CiscoSwitch doesn't go via the gateway since the routing is done internally on the pfsense, hence that last rule won't allow it.
-
If I were doing this, I would make an extra VLAN, like you did. It's the management VLAN. Make sure only your computer(s) can get to this VLAN by setting your smart switch ports to only hand that VLAN to your computer(s). You also have to add the VLAN settings to your computer's network card.
Then, on the VLAN's firewall rules, all you have to do is use 1 rule - allow that VLAN to any destination. That should let you do what you're trying to do - get to any network on the firewall, using any port and/or protocol. If you want to block this management VLAN from getting to other networks (like really private ones, or the internet as an example), put these block rules above the allow any rule.
Basically, I think what you're trying to do is make a separate LAN interface, but only usable for management activities, and then only connect your computer to it.
Jeff