How to prevent device from communicating over a local network and Internet
-
Good morning, sir,
I have identified a device (a LG sound bar, SL10Y) that initiates an IPv4 and IPv6 connection (DHCP request)
The network configuration is built-in in the LG firmware, so it is not possible to change or disable these settings.
If I unplug the network cable, the wifi will automatically activate and he will want a valid hotspot to leave me alone.
I find this device extremely unhealthy.Not knowing the nature of the traffic that this device can generate and not being a fan of the microphones that it integrates.
I would like to forbid it any traffic on the local network with its IPv4 and IPv6 address.
Basically prevent her from communicating with anything else than herself ;)The existing rules on my local network are the following.
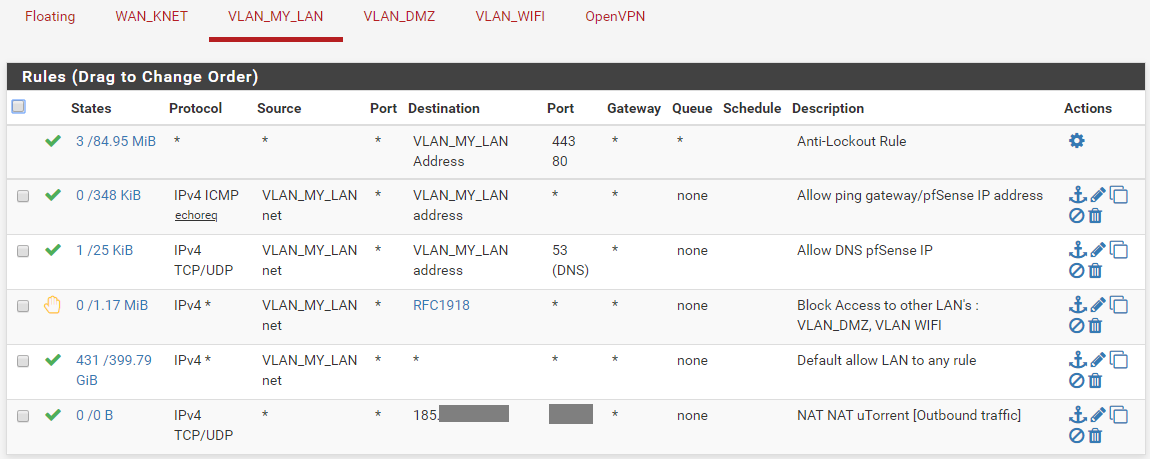
Can you please tell me what kind of rule I need to create and the parameters to use?
I also need to know where I should place this rule please?In advance, thank you for your help.
-
@Elrick75 said in How to prevent device from communicating over a local network and Internet:
with anything else than herself ;)
Then you need to put it on its own vlan with no other devices on that network.. pfsense has zero to do with things talking to each other on the same network.
-
@Elrick75
To expound a little more on what user @johnpoz posted -- devices on the same IP subnet (same LAN if you want to look at that way) can and do communicate directly with each other through the network switch (or hub) they are connected to. The firewall is never in that pathway, thus the firewall can't do anything about them talking to each other.The only time devices on a LAN will communicate with the firewall is if they need some specific service from the firewall (such as a DNS lookup from the local
unboundresolver) or they need to communicate with a device that is not on the same IP subnet as them. In other words, when they need to talk to something on the Internet they will go through the firewall, but when they only want to talk to each other they will do that directly bypassing the firewall.@johnpoz's solution for you is to create another IP subnet (a VLAN) and put this troublesome device on that network all by itself. Doing this requires you have a network switch that understands VLANs, or if you a spare port on your firewall you can directly connect this troublesome device there and configure that port as a different IP subnet.
There is no way to prevent devices on the same LAN from talking with each other using firewall rules because the firewall will never see that traffic. It will flow from one device directly into the network switch port, then through the network switch fabric, and directly out the port the other device is connected to.
-
Thank you for your answer.
I will create a new VLAN on my switch dedicated on specific port for this shitty device.