Rules from VLAN to LAN and back
-
Hi,
I've here a tagged VLAN ID=20 with 192.168.20.0/24. This is connected to an access point and clients can get connected to the internet. I want to get them access to the LAN network 192.168.1.0/24 too.
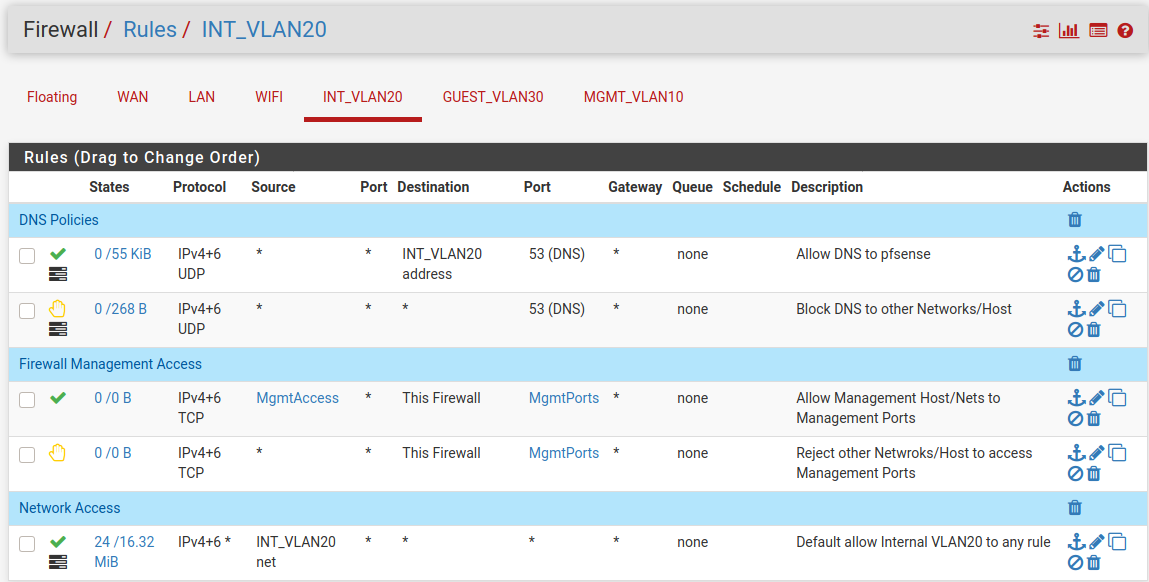
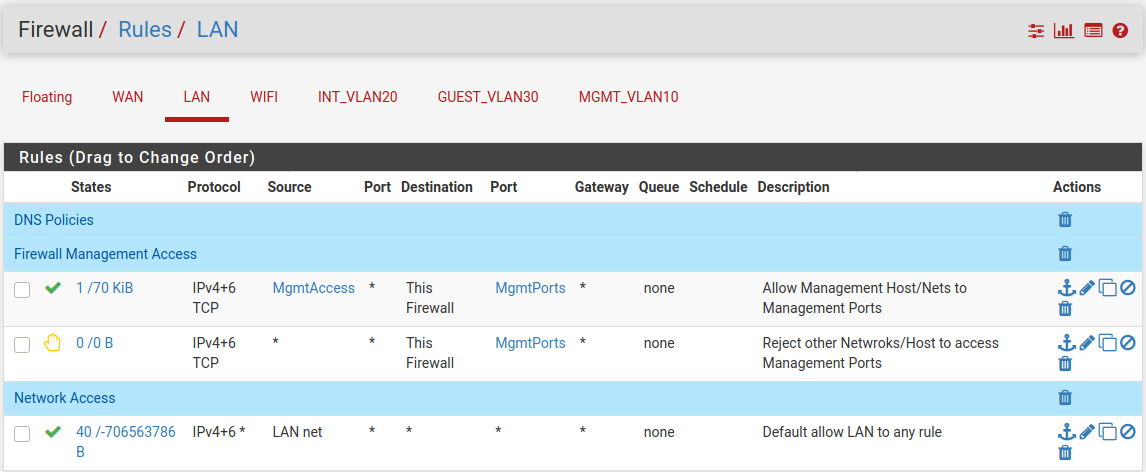
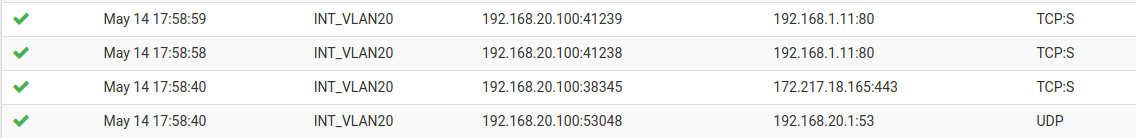
From logs, I have access to an host, e.g. 192.168.1.11, but the host seems to be unable to get the VLAN 192.168.20.0/24 resp. the client inside this network back.
For my understanding LAN should be allowed to go to every network, even GUEST network (which isn't intended later on). So, what happens and how to get it?
Thanks
-
@pfs-ole Make a new firewall rule on interface INT_VLAN20, you could even duplicate the one you already have - "default allow internal VLAN20 to any", and change the destination to "LAN net". After you make and save this rule, move it all the way to the top of the INT_VLAN20 firewall rule list and save the list.
Now test to make sure it works. You might have to, on devices connected to the INT_VLAN20 network, renew their DHCP leases to get the client working correctly.
If this works, then you can tweak it, for example, to only allow access to certain machines/hosts on LAN network, setup a schedule, allow only certain types of traffic (ports) thru to the LAN network, etc.
You can then also start to move the rule down in the list, to an appropriate final resting spot.
Hope that helps.
Jeff
-
thank you for your advice, but it doesn't work or even change something. As I understand this, this is a more concrete forward rule from VLAN20 to LAN which aren't blocked as the logs shows. Maybe I'm wrong?
Edit: Maybe I forgot an important detail to mention. The vlan20 is on Unifi WLAN, connected to a management switch (layer 2 switch called?) going to pfsense. Also on switch is the LAN which isn't VLAN tagged. So, maybe the client in LAN can't connect to the client in VLAN 20 since the switch isn't configured for this? But, isn't the pfsense not capable to do this?
-
@pfs-ole Ok then. On the host on VLAN20, do you have the machine's firewall rules turned off. If it's a Windows machine, for example, if you don't have the internal built-in Windows firewall turned off, it will NOT respond to traffic or requests from other networks.
Same goes for machines on LAN, if they are Windows machines. They will not respond to machines on the VLAN20 network, since that network is not on the same subnet as the LAN network.
Jeff
-
I will check it in the evening. A t this time only linux machines are there and I don't want to allow the windows machines to serve some services.
Anyway, LAN network doesn't know anything about VLANs, where the host to be connected from VLAN20 is located ....