Best setup for SG-1100 guest WiFi with VLAN
-
Hi.
I recently replaced my Netgaer R7000 (running DD-WRT) as edge device with pfSense (SG-1100) and very happy with it. :-)
The R7000 is still in use as Accesspoint providing Wifi and Switch.
Everything is running as one flat network.
Now what I want to do is create one VLAN separated Wifi for Guests. And the trouble starts right here...get clobbered over the head how to get even start with.
Because the SG-1100 is using VLAN internally it looks even more confusing to me. But first let me show how my network actual looks like:
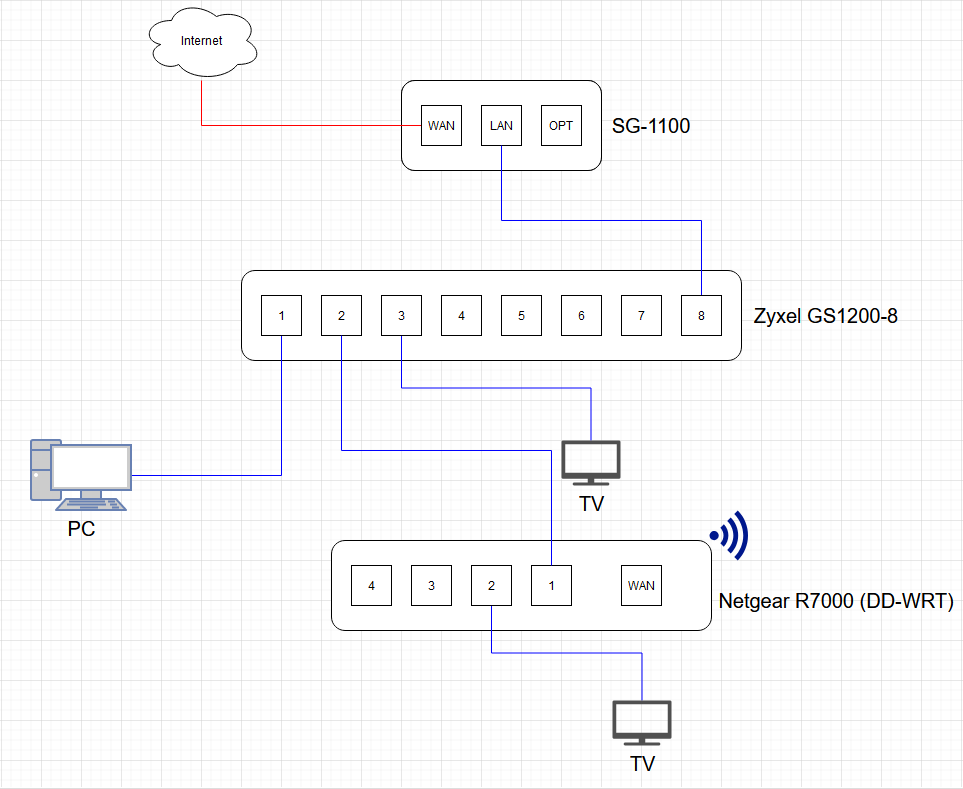
As you see I also use this Zyxel GS1200-8 Switch which also can do VLANs.
Can I leave the LAN configuration completely untouched, just add the GUEST VLAN to pfSense and the Netgear, or do I need to configure the Zyxel with VLANs as well?
Would it be better to use the SG-1100 OPT port for the GUEST network, or would it be a waste of ports? Maybe I'd want to add something like WAN2 later...
As you see I am puzzled how to start and would be happy about recommendations how you guys would do it. :-)Thanks for reading!
-
Does that R7000 support VLANs? If not, you won't be able to do a guest LAN. The way guest WiFi is normally done is with an access point that supports multiple SSIDs and VLANs. When you go beyond basic WiFi, it's better to use a proper AP, rather than using an old WiFi router.
-
With DD-WRT the R7000 supports Multi SSID and VLANs.
-
Through the router portion? Or just the switch? You can test that by configuring a SSID on a VLAN and then looking for tagged frames on the LAN, when you connect to that SSID. If the VLAN only works for packets passing through the router, then what you want to do won't work.
-
I am sure the Switch also supports VLANs.
Here is the default configurationroot@dd-wrt:~# nvram show | grep port.*vlans | sort size: 35470 bytes (30066 left) port0vlans=2 port1vlans=1 port2vlans=1 port3vlans=1 port4vlans=1 port5vlans=1 2 16AFAIK port0 is WAN, port1-4 is the Switch and port5 the CPU.
-
There is a way to put the LAN port and the OPT port on the same VLAN, but if you're wanting to add a kinda low-traffic device(s) to the network, I would just add a guest VLAN to the LAN port. By doing this, you then don't need to pull a second cable, from the OPT port to your Zyxel switch just for this guest network. Keeps it simple.
https://docs.netgate.com/pfsense/en/latest/solutions/sg-1100/switch-overview.html
So, VLANs on pfsense are pretty easy. Not exactly sure how the SG-1100 differs, so I might be wrong on these instructions. I haven't had my hands on one of these boxes yet, so I'm going from memory on setting up other Netgate boxes with VLAN interfaces.
Under the Interfaces tab on the SG-1100, go to Assignments. Go to VLANs, and add a new VLAN, tagging it something like 8 or 9 or 10. Make the parent interface of this new VLAN the LAN interface. That will keep your network flat, kinda.
On your Zyxel switch, tag the number 2 port with the same VLAN number. And, finally, on the DD-WRT Netgear box, tag port 2 with the same VLAN number. You might need to reboot either the switch or the "access point" when you're done, but maybe not.
That should be all that's required. Make sure you've got a DHCP server runnning on the VLAN interface, and make sure you've got a subnet programmed on that interface that doesn't conflict with any other subnet you've got on your SG-1100.
Maybe somebody else that actually has an SG-1100, and has setup an additional VLAN on the LAN port, can check my steps.
Hope that helps.
Jeff
-
Hmmm Netgear Port 2 is one of my TVs, i need to keep them in the LAN.
I want to keep my LAN layout completely untouched, only upgrade the R7000 with a separated Wifi. -
@henrymatthews97 said in Best setup for SG-1100 guest WiFi with VLAN:
Hmmm Netgear Port 2 is one of my TVs, i need to keep them in the LAN.
I want to keep my LAN layout completely untouched, only upgrade the R7000 with a separated Wifi.Ok, you're right, my bad. I meant port 1, tag port 1 with the VLAN number.
-
Wouldn't tagging Netgear port 1 with the guest VLAN ID still cutting off my default LAN (TV Port 2)?
-
It shouldn't. You're simply adding a tag, on top of the other normal traffic, on the access point port or switch port.
Here's mine, VLAN 8 on a 24 port switch, to connect access points back to pfsense. I'm using VLAN 8 for a guest network, and the access points support VLANs and multiple SSIDs. The guest network is running on top of the LAN network in pfsense, and the guest network is setup with its own subnet. Everything works perfectly. In my picture, port GE27 (back to pfsense) would simulate your port 1 on the Netgear.
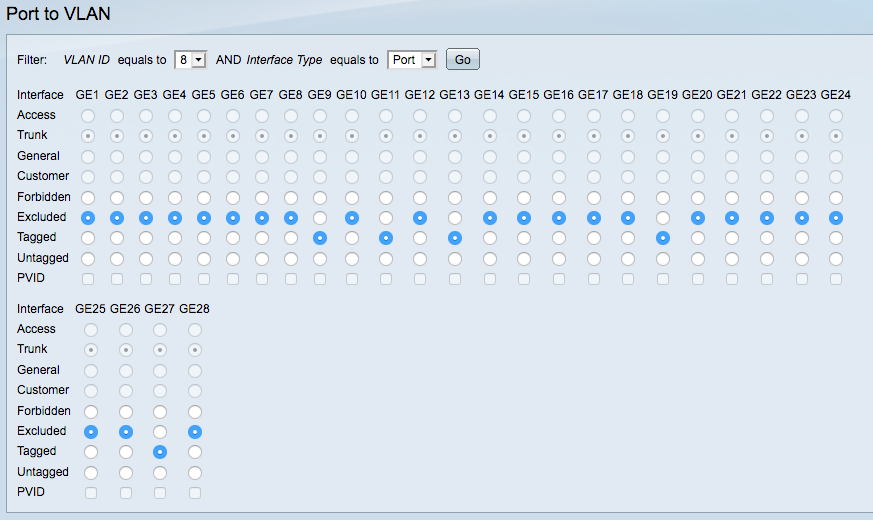
I'm assuming the DD-WRT box you're got will behave the same way.
Sorry, I forgot, your port 8 on the Zyxel also has to be tagged with your new VLAN number.
So, quick summary - add a new VLAN to pfsense, parent interface is LAN, tag port 8 and 2 on Zyxel with your new VLAN number. Then finally, tag port 1 on Netgear with the same number. Tagged and untagged ports on networking gear can exist at the same time, if the gear is any good.
Jeff