ExpressVPN OpenVPN won't work
-
Hi
I'm trying to config ExpressVPN OpenVPN on my PfSense but it won't work
I follow the steps from their guide link
I config the OpenVPN > Clients & Interfaces & Certificate Manager > CAs & Certificates.
In status > OpenVPN is UP and Bytes Send / Bytes Received stuck in 10 Kib
I have 1 WAN Interface - 1 LAN Interface & 1 Wireless Interface with an AP as bridge mode, all interfaces have there own IP ranges
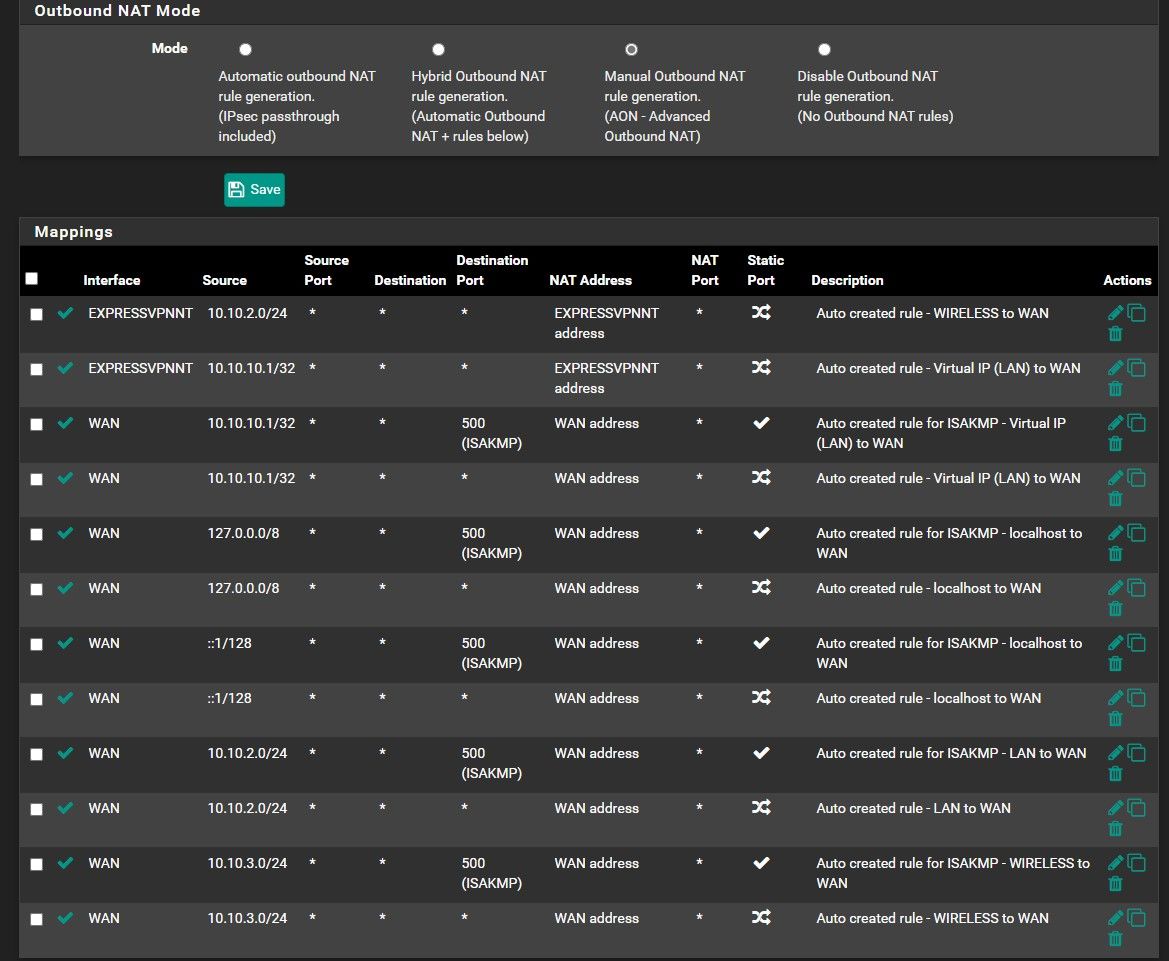
In NAT > Outbound > NAT Mode, I set to Manual and duplicate all WAN rule and edit them to change the interface to ExpressVPNI don't know what is the problem, I think my NAT config is wrong
I talked to their support and they say it seems all the config is ok
could you please help me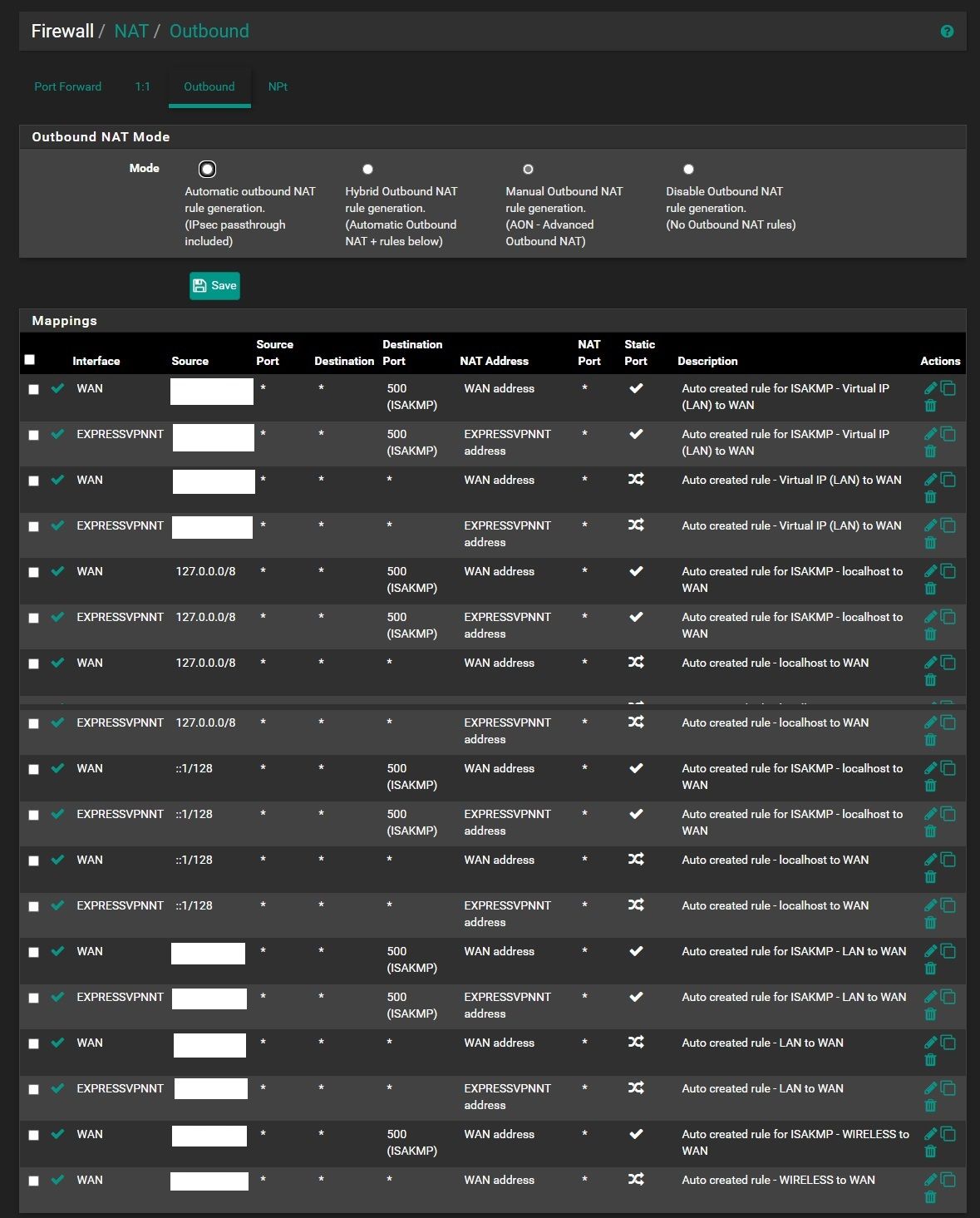
-
Hi,
Is the link itself up :
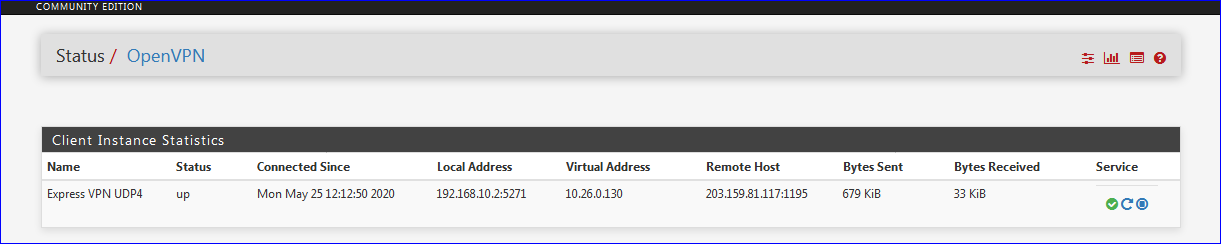
?
The Status > System Logs > OpenVPN should show a nice and clean :
May 25 13:50:59 openvpn 81240 Initialization Sequence Completed May 25 13:50:59 openvpn 81240 /sbin/route add -net 10.26.0.1 10.26.0.101 255.255.255.255 May 25 13:50:59 openvpn 81240 NOTE: unable to redirect default gateway -- Cannot read current default gateway from system May 25 13:50:57 openvpn 81240 /usr/local/sbin/ovpn-linkup ovpnc2 1500 1609 10.26.0.102 10.26.0.101 init May 25 13:50:57 openvpn 81240 /sbin/ifconfig ovpnc2 10.26.0.102 10.26.0.101 mtu 1500 netmask 255.255.255.255 up May 25 13:50:57 openvpn 81240 TUN/TAP device /dev/tun2 opened May 25 13:50:57 openvpn 81240 TUN/TAP device ovpnc2 exists previously, keep at program end May 25 13:50:57 openvpn 81240 ROUTE: default_gateway=UNDEF May 25 13:50:57 openvpn 81240 GDG: problem writing to routing socket May 25 13:50:57 openvpn 81240 Incoming Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication May 25 13:50:57 openvpn 81240 Incoming Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key May 25 13:50:57 openvpn 81240 Outgoing Data Channel: Using 512 bit message hash 'SHA512' for HMAC authentication May 25 13:50:57 openvpn 81240 Outgoing Data Channel: Cipher 'AES-256-CBC' initialized with 256 bit key May 25 13:50:57 openvpn 81240 OPTIONS IMPORT: adjusting link_mtu to 1629 May 25 13:50:57 openvpn 81240 OPTIONS IMPORT: peer-id set May 25 13:50:57 openvpn 81240 OPTIONS IMPORT: --ip-win32 and/or --dhcp-option options modified May 25 13:50:57 openvpn 81240 OPTIONS IMPORT: route options modified May 25 13:50:57 openvpn 81240 OPTIONS IMPORT: --ifconfig/up options modified May 25 13:50:57 openvpn 81240 OPTIONS IMPORT: compression parms modified May 25 13:50:57 openvpn 81240 OPTIONS IMPORT: timers and/or timeouts modified May 25 13:50:57 openvpn 81240 PUSH: Received control message: 'PUSH_REPLY,redirect-gateway def1,dhcp-option DNS 10.26.0.1,comp-lzo no,route 10.26.0.1,topology net30,ping 10,ping-restart 60,ifconfig 10.26.0.102 10.26.0.101,peer-id 14' May 25 13:50:56 openvpn 81240 SENT CONTROL [Server-3583-0a]: 'PUSH_REQUEST' (status=1) May 25 13:50:55 openvpn 81240 [Server-3583-0a] Peer Connection Initiated with [AF_INET]203.159.81.117:1195 May 25 13:50:55 openvpn 81240 Control Channel: TLSv1.2, cipher TLSv1/SSLv3 ECDHE-RSA-AES256-GCM-SHA384, 2048 bit RSA May 25 13:50:55 openvpn 81240 VERIFY OK: depth=0, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-3583-0a, emailAddress=support@expressvpn.com May 25 13:50:55 openvpn 81240 VERIFY X509NAME OK: C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=Server-3583-0a, emailAddress=support@expressvpn.com May 25 13:50:55 openvpn 81240 VERIFY EKU OK May 25 13:50:55 openvpn 81240 ++ Certificate has EKU (str) TLS Web Server Authentication, expects TLS Web Server Authentication May 25 13:50:55 openvpn 81240 Validating certificate extended key usage May 25 13:50:55 openvpn 81240 VERIFY KU OK May 25 13:50:55 openvpn 81240 VERIFY OK: depth=1, C=VG, ST=BVI, O=ExpressVPN, OU=ExpressVPN, CN=ExpressVPN CA, emailAddress=support@expressvpn.com May 25 13:50:55 openvpn 81240 TLS: Initial packet from [AF_INET]203.159.81.117:1195, sid=294262f8 1152496c May 25 13:50:55 openvpn 81240 UDPv4 link remote: [AF_INET]203.159.81.117:1195 May 25 13:50:55 openvpn 81240 UDPv4 link local (bound): [AF_INET]192.168.10.2:0 May 25 13:50:55 openvpn 81240 Socket Buffers: R=[42080->524288] S=[57344->524288] May 25 13:50:55 openvpn 81240 TCP/UDP: Preserving recently used remote address: [AF_INET]203.159.81.117:1195 May 25 13:50:55 openvpn 81240 Incoming Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication May 25 13:50:55 openvpn 81240 Outgoing Control Channel Authentication: Using 512 bit message hash 'SHA512' for HMAC authentication May 25 13:50:55 openvpn 81240 NOTE: the current --script-security setting may allow this configuration to call user-defined scripts May 25 13:50:55 openvpn 81240 MANAGEMENT: unix domain socket listening on /var/etc/openvpn/client2.sock May 25 13:50:55 openvpn 80908 library versions: OpenSSL 1.0.2u-freebsd 20 Dec 2019, LZO 2.10 May 25 13:50:55 openvpn 80908 OpenVPN 2.4.9 amd64-portbld-freebsd11.3 [SSL (OpenSSL)] [LZO] [LZ4] [MH/RECVDA] [AEAD] built on May 4 2020Then, goto Firewall > NAT > Outbound and switch to "Manual Outbound NAT rule generation." and Save.
"Clone" your "Local Network" to WAN NAT rule :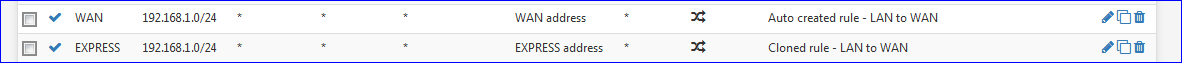
Do this for all local networks that need VPN access (192.168.2.0/24 etc)
No need to do anything with the IPv6 networks. Your VPN ISP doesn't speak "IPv6" (to be verified).
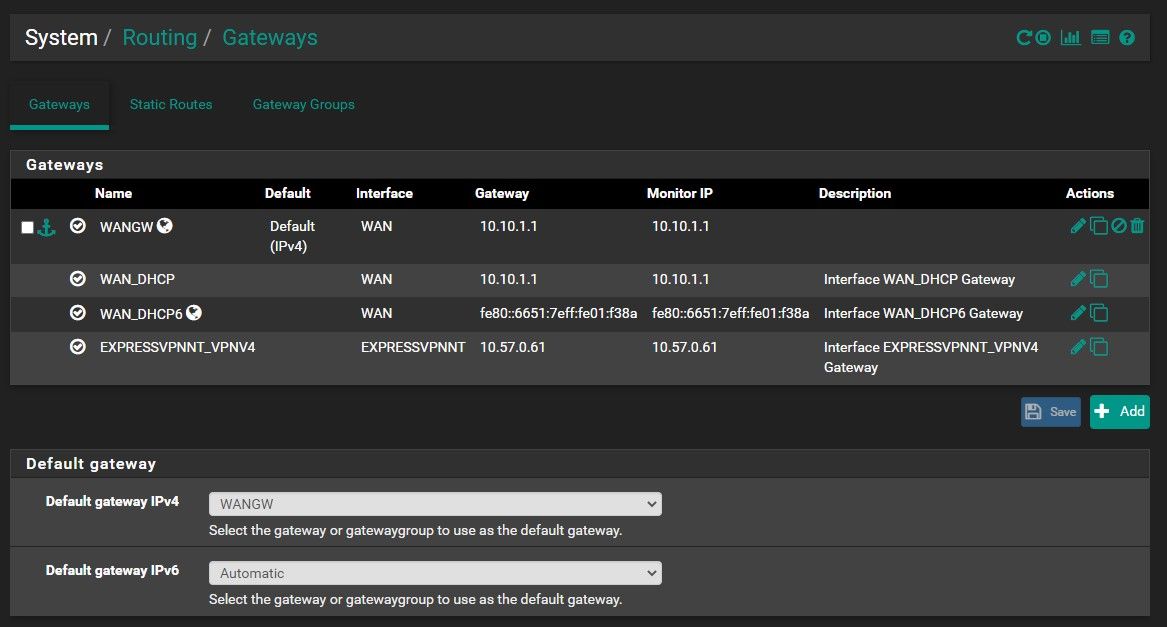
Also : goto System > Routing > Gateways and edit your "VPN CLIENT" gateway.
Enter an IPv4 that actually replies on ping - I took a IPv4 from one of my dedicated servers "some where on the net".
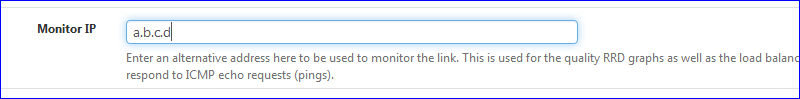
For me, it seems that the VPN gateway IP doesn't reply on ping, so the gateway monitoring persist in showing the interface is down.
Save.By now, you should see :
While here System > Routing > Gateways, select / activate the "VPN CLIENT" gateway as the default "Default gateway IPv4".
-
@Gertjan
Thank you in advance
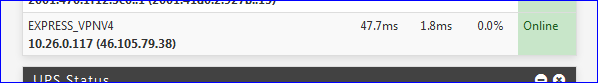
as you can see my connection is up, in fact in traffic graph is showing that I have Send but I don't have any received
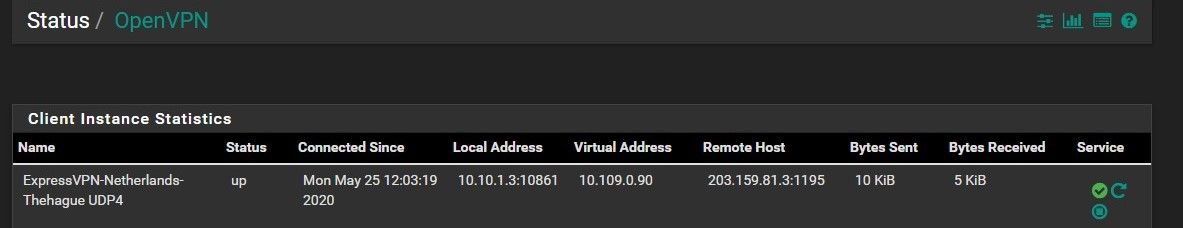
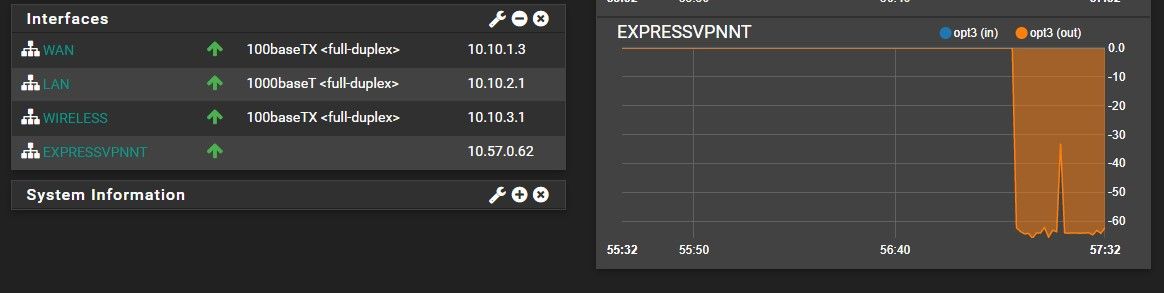
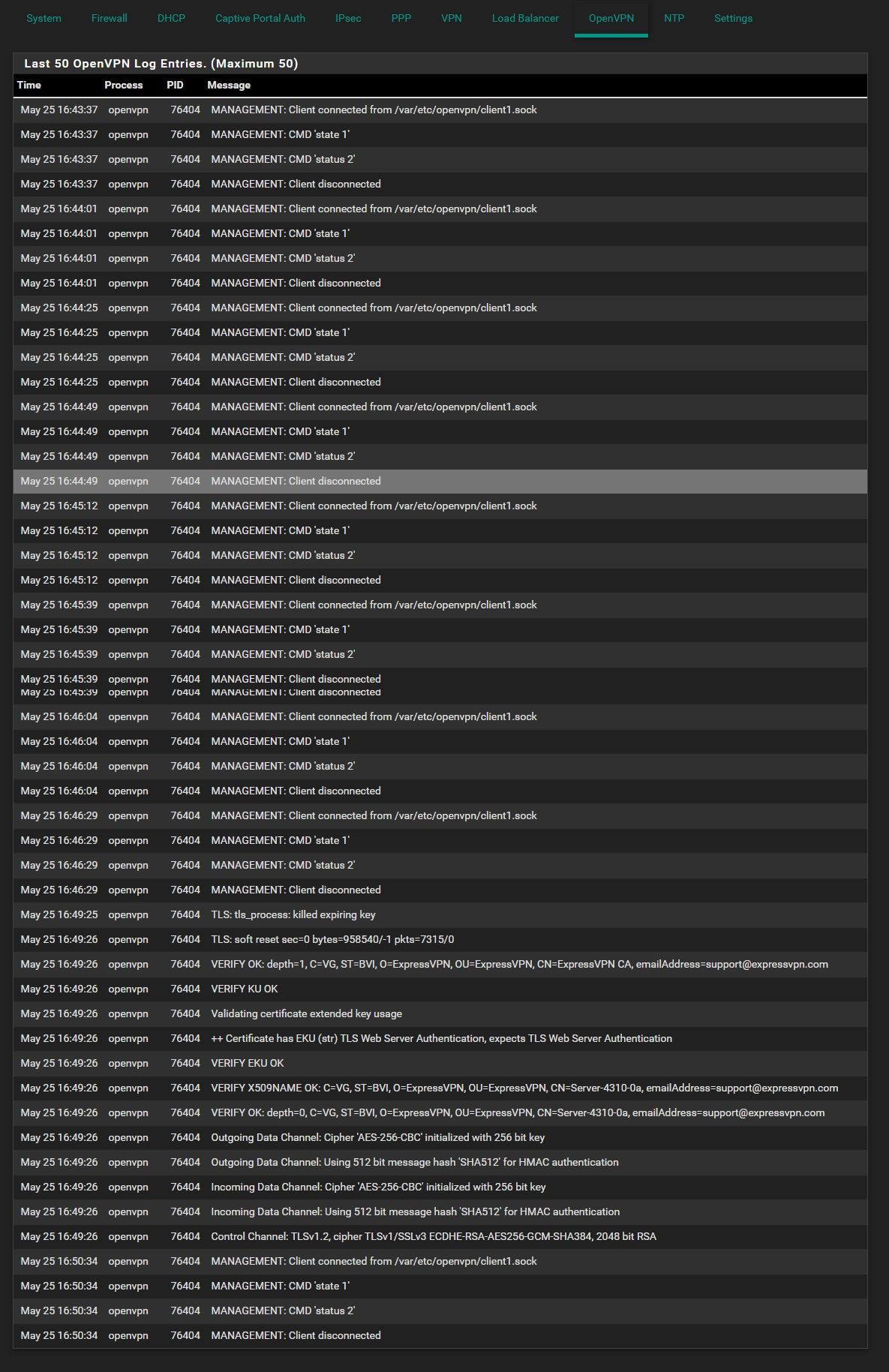
This is my OpenVPN system log:
This is my NAT config:
I'm sorry but I don't understand what should I do in gateway
-
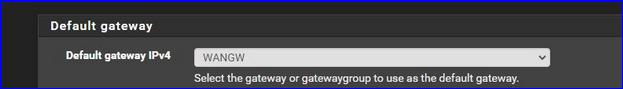
This is a selectable list.
So select your EXPRESS as the default gateway ... )Like :
@Gertjan said in ExpressVPN OpenVPN won't work:
While here System > Routing > Gateways, select / activate the "VPN CLIENT" gateway as the default "Default gateway IPv4".