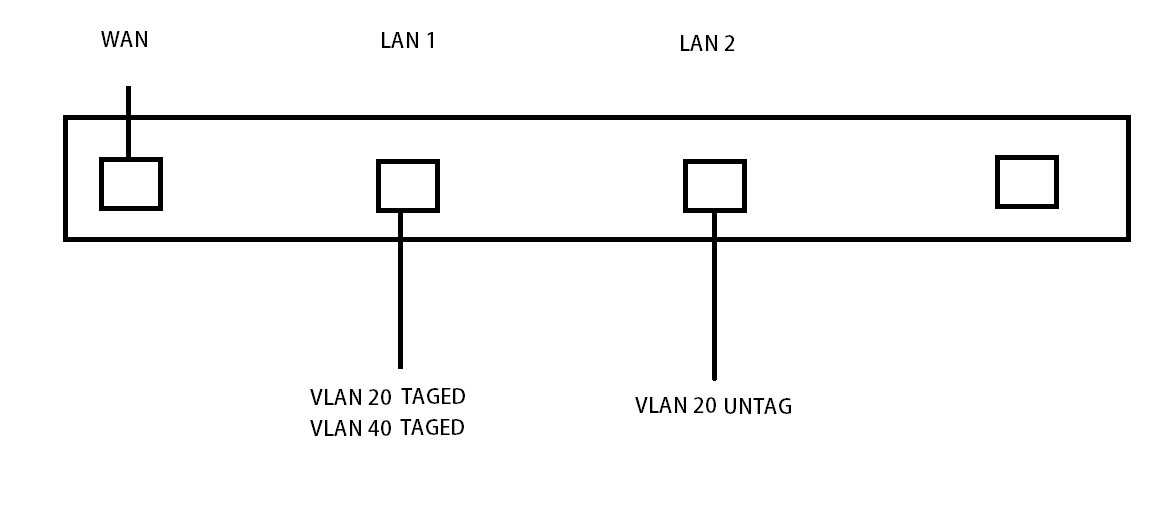
VLAN tag on more than 1 interface
-
I'm so confused about how to tag the same VLAN on two-ports on pfSense.
The following from a Watchguard firewall that I can tag or untag traffic on multiple interfaces, Can I do the same on pfSense?
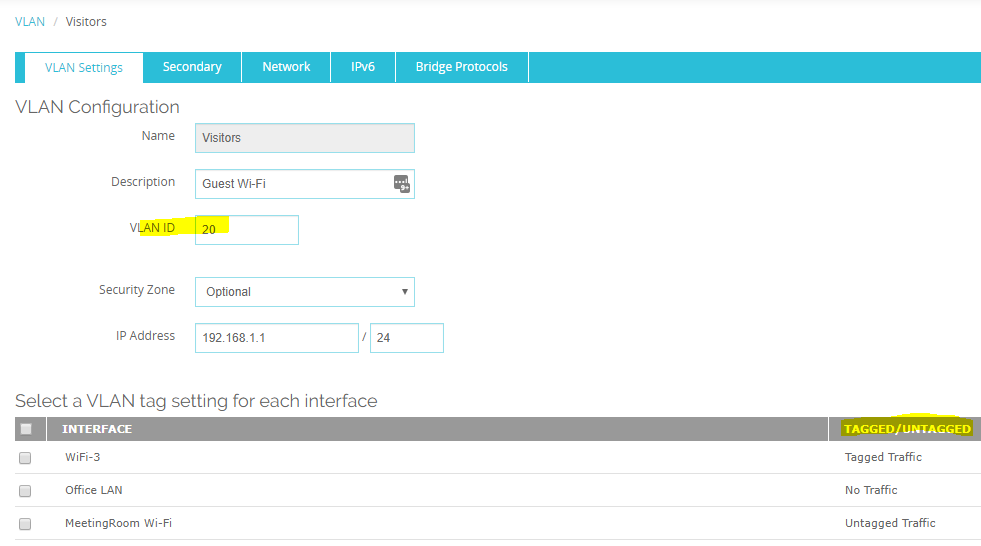
-
Yes, you can. Why do you think you can't?
-
what if I wanna tag VLAN 40 on vmx 3 I have no option? also tried to add the same interface to VLAN but no luck.
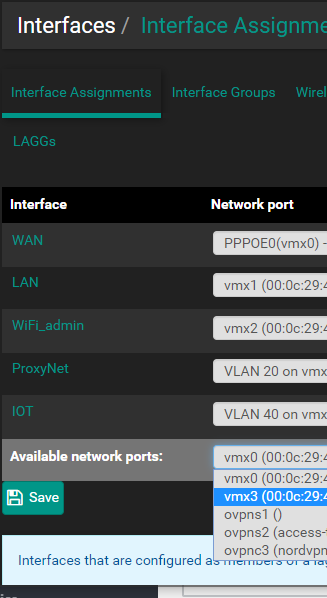
-
@ncm-com said in VLAN tag on more than 1 interface:
'm so confused about how to tag the same VLAN on two-ports on pfSense
How would that work?? I you want more than 1 interface in the same vlan you would need to setup a lagg..
The ports are not switch ports.. And if your doing this as VM.. Why would you think you even want or need to do such a thing? What do you think this would accomplish?
-
I suspect he's talking about one VLAN on the WAN interface and one on the LAN. In that case, it shouldn't be an issue.
-
@johnpoz
Thanks for your reply
I'm trying to untag VLAN on to Vswitch so I can connect to the physical switch outside the esxi, I think I have to setup lagg but not sure how to do this ?
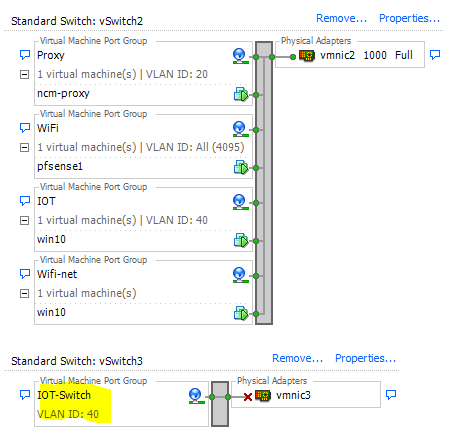
-
@JKnott said in VLAN tag on more than 1 interface:
I suspect he's talking about one VLAN on the WAN interface and one on the LAN
Is that what your talking about @ncm-com.. Vlans outside of pfsense have zero to do with pfsense..l
Please explain exactly what your wanting to do... Your statements as of now don't really make any sense..
You can not place the same vlan on 2 different interfaces in pfsense.. You can't.. You could create a bridge or lag if you want 2 different physical interfaces to be in the same vlan.
As to what your wanting to do with esxi? Do you want it to handle the tags or pass those tags on to pfsense? 4095 vlan id in esxi will pass the tags, any other setting will strip tags.
Thee would be be zero point to creating multiple vnics in esxi and handing them to pfsense and putting them in the same vlan..
I am more than happy to try and help you - but currently have no idea what your trying to accomplish..
-
Many thanks
You can not place the same vlan on 2 different interfaces in pfsense.. You can't.. You could create a bridge or lag if you want 2 different physical interfaces to be in the same vlan.So I think I have to create a LAGG in order to sent traffic through both interfaces? any idea how to do this? I guess I have to create the firewall rules as I can't add the existing VLAN to a new LAGG interface
Thee would be be zero point to creating multiple vnics in esxi and handing them to pfsense and putting them in the same vlan..
there are physical switches connecting outside the esxi so it would be an advantage to untag/tagged traffic to another port -
@johnpoz said in VLAN tag on more than 1 interface:
You can not place the same vlan on 2 different interfaces in pfsense.. You can't..
You can place the same VLAN number on more than one interface. I just did that. I created VLAN 3 on my WAN interface, which I already had on my LAN interface.
bge0.3: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=80003<RXCSUM,TXCSUM,LINKSTATE>
ether 00:16:17:a7:f2:d3
inet6 fe80::216:17ff:fea7:f2d3%bge0.3 prefixlen 64 scopeid 0x8re0.3: flags=8843<UP,BROADCAST,RUNNING,SIMPLEX,MULTICAST> metric 0 mtu 1500
options=80003<RXCSUM,TXCSUM,LINKSTATE>
ether 00:14:d1:2b:ed:ea
inet6 fe80::214:d1ff:fe2b:edea%re0.3 prefixlen 64 scopeid 0xa -
@ncm-com said in VLAN tag on more than 1 interface:
So I think I have to create a LAGG in order to sent traffic through both interfaces?
Why do you want to send traffic through 2 virtual interfaces that are the same network - that serves no purpose...
-
@ncm-com said in VLAN tag on more than 1 interface:
So I think I have to create a LAGG in order to sent traffic through both interfaces? any idea how to do this? I guess I have to create the firewall rules as I can't add the existing VPAN in this case?
Perhaps you'd better describe what exactly you want to do.
-
@JKnott said in VLAN tag on more than 1 interface:
just did that. I created VLAN 3 on my WAN interface, which I already had on my LAN interface.
That is not the same vlan... that is the same vlan ID.. Not the same vlan.. And even if pfsense doesn't stop you from doing that.. Its a horrible IDEA..
-
Yes, I am aware of that and know there is no data connection between them, unless set up in routing. However, the way you wrote what you said left the question open. Regardless, we still need to find out what he wants to do. Earlier on, I got the impression he wanted VLANs on more that one interface, which is certainly possible, even with the same VLAN ID.
-
Please see the above scenario,
I can use LAN1 interface goes to VLAN switch and LAN2 interface to the non-manage switch so the bandwidth will use both interfaces?
-
So, you want the unmanaged switch to be on VLAN 20? If so, then you'd have to create a bridge between LAN 1 & LAN 2. However, the better way would be to just configure a port for VLAN 20 on the managed switch, which would then connect to the unmanaged one.
-
@ncm-com said in VLAN tag on more than 1 interface:
so the bandwidth will use both interfaces?
But your pfsense is virtual... You handle the physical interfaces in esxi... let it do the tagging.. All pfsense needs to know is that its the "lan" and on vnic x
vmx is internal and would be 10ge interface to pfsense..
-
@johnpoz said in VLAN tag on more than 1 interface:
But your pfsense is virtual...
Forgot about that.
-
@johnpoz
I actually connect them to physical adaptors from the esxi
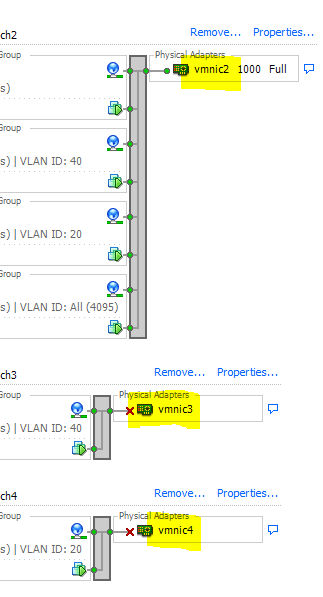
they are gigabit interfaces -
Also what is the bandwidth getting you? Is where this traffic going more than 1 gig? Your wan, multiple other vlans?
Traffic between devices on the same network traffic doesn't even flow through pfsense... So why do you think you need more bandwidth and more than 1 connection into pfsense to leverage that more bandwidth?
Connect both of the physical nics to the same vswitch/port group..
This makes ZERO sense to setup..
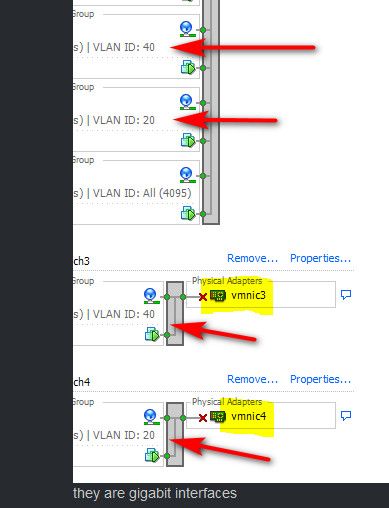
What exactly do you think that accomplishes???
Connect your physical nics to same vswitch, and then break out your different vlans via port groups.
-
@johnpoz
the pfsense is a VM on the host, and I'm trying to send traffic out to different physical adaptors let say vmnic 2 and vmnic 3Connect both of the physical nics to the same vswitch/port group..
I tried the above but no luckI got it, I could untag VLAN 20 using the Vswitch connected to the vmnic2,
but let say if the traffic between VLANs reaching 500mbps it will create a bottleneck on one interface that would not be the case if the traffic using two ports?