Use of 'Invert Match' against an interface network with a virtual IP address
-
Hi,
I'm seeing that when using the 'Invert Match' check box when specifying an interface network destination, it does not behave correctly when that interface also has a virtual IP address associated with it.
So in my firewall rule on my LAN interface I have the following set up for the destination:
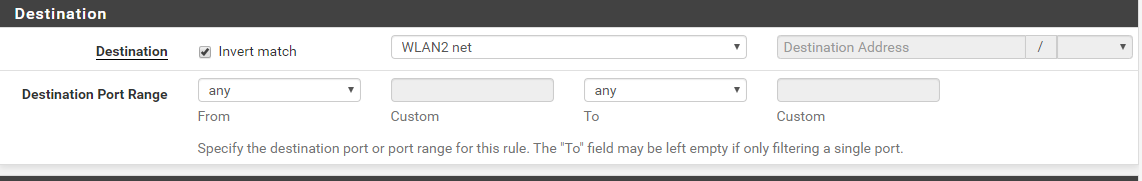
My WLAN2 network is 10.105.112.1/24
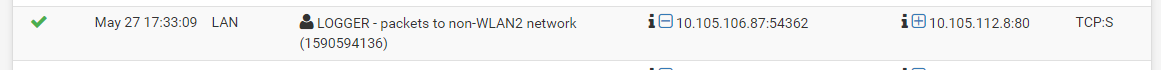
My firewall log entry showing the issue is:
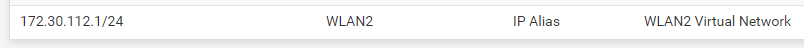
Virtual IP address setting for this network is:
Looking at
/tmp/rules.debugI can see that rule entry as:pass in log quick on $LAN inet proto tcp from { 10.105.106.0/24 172.30.106.0/24 } to { !10.105.112.0/24 !172.30.112.0/24 } tracker 1590594136 flags S/SA keep state label "USER_RULE: LOGGER - packets to non-WLAN2 network"So I'm guessing that the entries in the curly braces are ORed together so the 'to' section always matches.
Is this correct?
If so how would I go about fixing it?
I'm using
2.4.5-RELEASE (amd64) built on Tue Mar 24 15:25:50 EDT 2020 FreeBSD 11.3-STABLE.Kind regards,
mark