What are the reqs to SNI Microsoft's web servers with HAProxy?
-
Way back, years now, I had a working SNI frontend on HAProxy that'd work fine with any web server, then I guess some feature was added that as a result outdated my config and broke things down. Since then I cannot SNI with Microsoft's web servers again.
Recently I found an article about IIS moving a step later the SNI greeting or whatever they do and that being the reason why it doesn't work--I'm paraphrasing almost to the point of making stuff up bc I lost the article; it didn't say explicitly how this is dealt with, I'm sure it implied it b,ut I couldn't catch it, I'm not technical enough.
So… I've been tweaking HAProxy here and there to see what works but I haven't been able to make it work. I've made health checks work in L6 and L7 but it still fails to connect all the way out from the client's end, there's always a 500-class error, usually SSL-related. Probably the obvious solution would be to modify the server instead but that's not always an option, that's why I referred to "Microsoft's servers" and not IIS in the beginning. Windows Server has this other web server whose name I forgot, something very Apache's httpd, that behaves the same. ADFS for instance uses that. I also found out with the new info, but not before spending hours tweaking, that checks should be only SSL checks (WTF!) and nothing related to header injection/manipulation and stuff because it's the raw stream passing through anyway. At least I'm good there.
httpd and NGINX work fine in the SNI frontend. It then does the looparound backend to offloading where it's hit/miss for IIS, mostly not working. Thankfully (and IDK why) my ISP lets me dial several PPPoE connections on the same ONT, and I just port-forward that to ADFS' Web Application Proxy using a different IP address, ADFS WAP doesn't play nice with Let's Encrypt though, so I have to further route that through Cloudflare's proxy to change the internal certs for something else. It's a lot of settings. I need to learn to do it properly specially if the ISP's multiple PPPoE thing is an "unintentional feature" and they catch on sometime soon. :/
I appreciate you help and any tips you have. :)
-
@skilledinept said in What are the reqs to SNI Microsoft's web servers with HAProxy?:
Recently I found an article
It may have been this: https://www.forwardproxy.com/2019/05/ssl-handshake-errors-after-placing-iis-service-behind-a-reverse-proxy/#more-235 but I remember different colors and it's like 1% of what I said, so…yeah.

-
@skilledinept
What does your current server configuration line look like in the haproxy.cfg (bottom of settings tab)?
Do you have both check-sni and sni keywords on that line? -
@PiBa said in What are the reqs to SNI Microsoft's web servers with HAProxy?:
at does your current server configuration line look like in the haproxy
There is no server line. At least not as a header, there are server lines on many of the sections though. In the SNI front end:
Um...no, there's no server line on the front end, I'm still pasting it though:
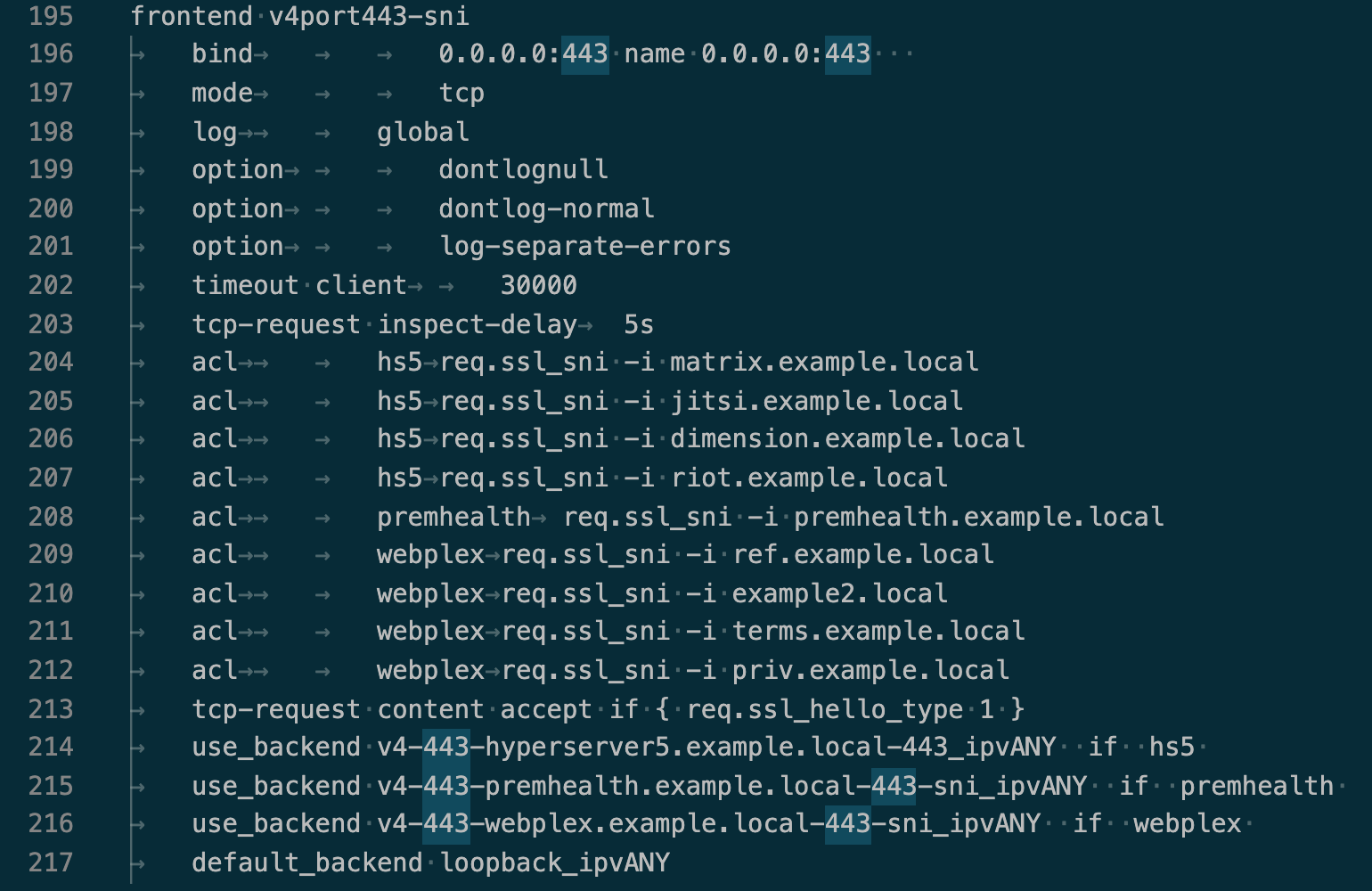
Overnight I removed all the Microsoft servers and move them back where they were, but, here's an Linux SNI back end, it runs httpd and a Java-based server--they were basically configured the same:
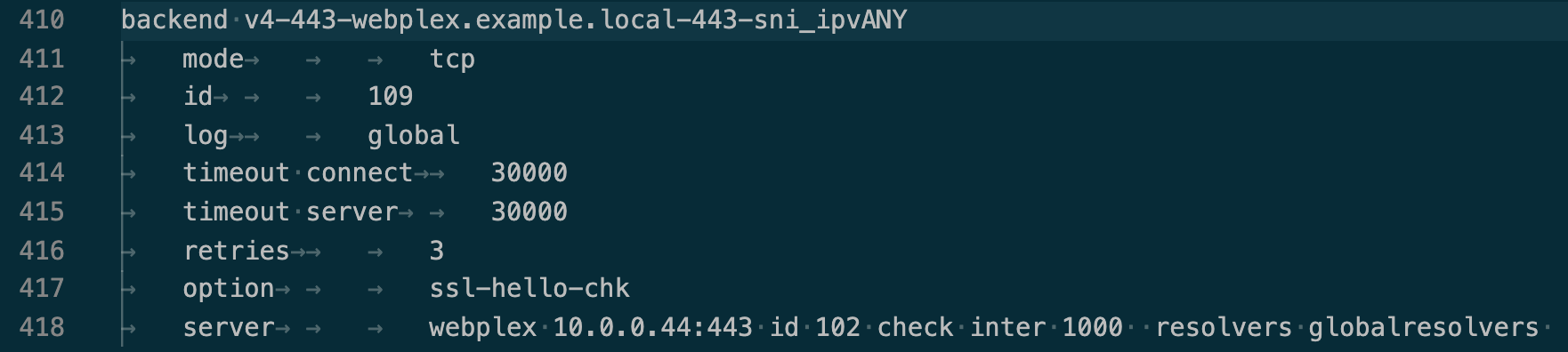
I thought Java applets (or servlets?? IDK) were the most most annoying thing to proxy but Microsoft outdid itself once again.
 Thanks for answering, BTW.
Thanks for answering, BTW. -
@skilledinept
The 'server line' is on the backend ;).. Line 418 in above screenshot.The current ssl-hello-chk you have only does a L6 check effectively.. Not really 'complete' regarding a valid http request.. I would change the health-check back to HTTP. And enable ssl-checks checkbox on the server config.
And adding some advanced options on the "Per server pass thru" like
sni str(ref.example.local) check-sni ref.example.local. See if that makes at least that domain function properly. -
@PiBa said in What are the reqs to SNI Microsoft's web servers with HAProxy?:
And adding some advanced options on the "Per server pass thru" like sni str(ref.example.local) chec
So far no luck, that whole config file makes it easier to understand a lot of stuff though, at least I can out two and two using the officials docs. I'm going to stop to bathe my bitch (canine) before it's cold and I'll try again with a huge set of data I found by visiting the website with the network inspector open:
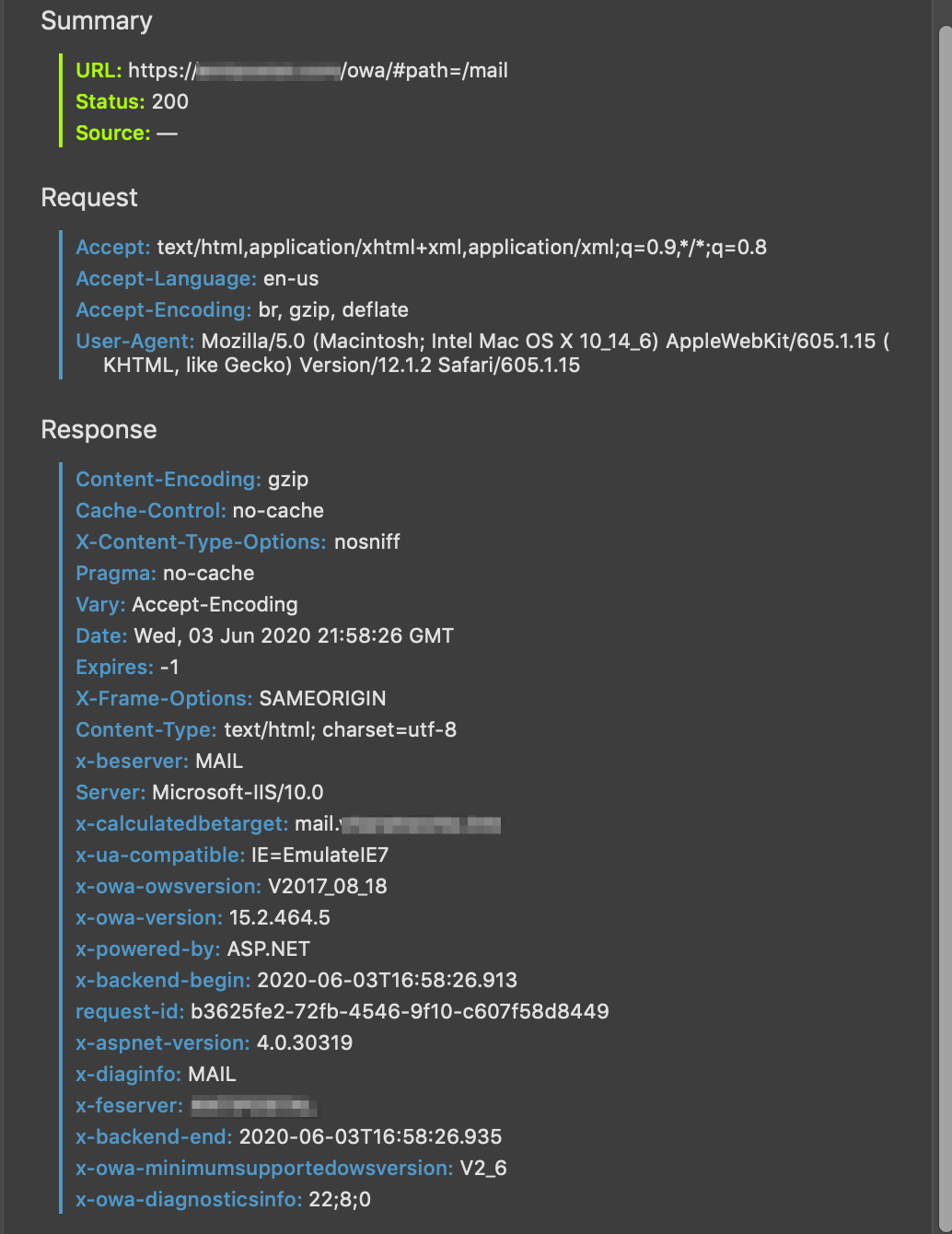
I'm using Exchange server because it's the one where enable offloading it's a checkbox within the web UI instead of back on IIS. I figured it would be less picky. Not really. Thanks for your help, I appreciated it immensely.


-
@skilledinept
If your now sending a request for https://mail.domain.tld/owa and getting a status 200 back from IIS / exchange that sounds like the ssl - sni / http connection is functioning properly..
So what is the part still causing you trouble.?Perhaps its sending a redirect at some point for a wrong url/ip that 'confuses' the client? But you will need to inspect the actual requests/responses to find such problems, and then see if a workaround can be made..
-
@PiBa said in What are the reqs to SNI Microsoft's web servers with HAProxy?:
sni str(ref.example.local) check-sni ref.example.local
Hey apologies for going MIA. Things have been crazy.
I tried what you told me and you were beyond correct -- except that -- it wasn't immediately obvious because I health checks wouldn't work. So I disabled them et voilà!
Not only that, ADFS and ADFS Web Application Proxy now work too! So far I only tried the pages available in ADFS itself, like IdP-Initiated Sign-On and Password Update to avoid going more levels in, I won't have to anyway because I don't need ADFS WAP for proxying at all, only for auth. HAProxy can handle the rest.
It's not much but hopefully I can help pay it forward with this:
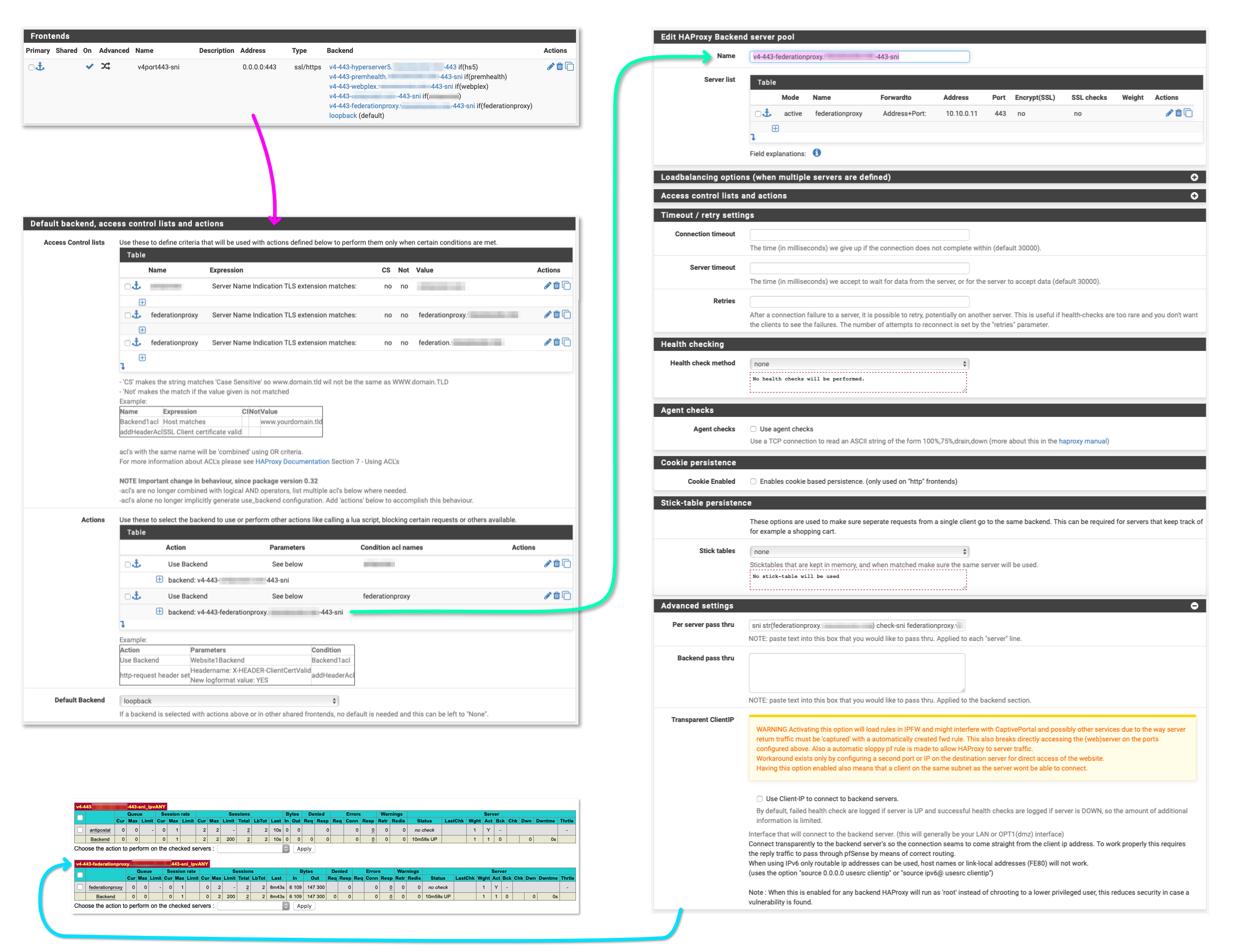
Thanks!
-
@skilledinept
What does the haproxy status page LastChk column say when you enable "SSL checks" on the server, and configure healthcheck method to 'http' ? Wrong method? Try GET perhaps? Or wrong host, try adding a Host header? Or forbidden? Try allowing the 401 status as valid.