DUO Implementation for pfSense Based OpenVPN Server with RADIUS (AD) Integration - Step by Step
-
DUO Implementation for pfSense Based OpenVPN Server with RADIUS (AD) Integration- Step by Step
In case someone needs step by step instructions for implementing DUO for OpenVPN w/Radius. This is for Microsoft AD environment. You may change it as needed, if you have a different authentication environment.
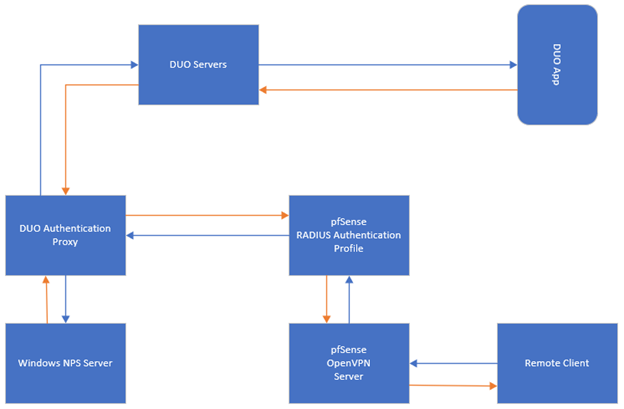
Requirements:- pfSense
a. OpenVPN Server
b. RADIUS Authentication - Windows Network Policy Server (NPS)
- DUO Authentication Proxy (most likely a VM)
Implementation: - Configure OpenVPN Server with RADIUS authentication method and use the RADIUS Authentication Server you configured. Details are in the link below
https://docs.netgate.com/pfsense/en/latest/vpn/openvpn/authenticating-openvpn-users-with-radius-via-active-directory.html - Test the new OpenVPN Server with an AD user to make sure it is fully functional.
- Login to DUO site and configuration application protection profile. Select OpenVPN as the app to protect.
- Install DUO Authentication Proxy on a separate VM (you don’t have to but make sure it is not in conflict with anything else wherever you decide to install it). Link is below
https://dl.duosecurity.com/duoauthproxy-latest.exe - Edit the following file with the parameters below
C:\Program Files (x86)\Duo Security Authentication Proxy\conf\authproxy.cfg
[radius_client]
host=NPS_Server_IP_Address
secret=The_Secret_Used_During_NPS_pfSense_RADIUS_Configuration[radius_server_auto]
ikey=DUO_Identification_Key_From_DUO_App_Protection_Settings_Page
skey= DUO_Secret_Key_From_DUO_App_Protection_Settings_Page
api_host= DUO_API_Host_From_DUO_App_Protection_Settings_Page
radius_ip_1=LAN_IP_Address_Of_pfSense
radius_secret_1= The_Secret_Used_During_NPS_pfSense_RADIUS_Configuration
failmode=safe
client=radius_client
port=1812Make sure everything else is removed or disabled in this file.
6. Start (or restart if already started) the “DuoAuthProxy” Service in windows Services (in DUO Authentication Proxy VM)
7. Go to Windows NPS server configuration page and add DUO Authentication Proxy under RADIUS Clients section, use the IP address of DUO Authentication Proxy VM’s IP address.
8. Test the whole setup from a client computer with OpenVPN client.Good luck
-cmkrs
- pfSense
-
@cmkrs said in DUO Implementation for pfSense Based OpenVPN Server with RADIUS (AD) Integration - Step by Step:
to Windows NPS server configuration page
This doesnt work.
-
Thanks for the great start.
A few items I had to add and validate to make it all work.
I was not able to publish my findings and step-by-step process - Akismit flagged it as SPAM - under this forum.
So, I published it to my web site at this link: https://d-b-s.com/documents
Credits: This is a compilation of several articles on the WEB, but it started here with this article as it had the most information. Thanks.