pfSense 2.4.5-RELEASE-p1 Now Available
-
Not yet, we are still looking into it
-
@jimp said in pfSense 2.4.5-RELEASE-p1 Now Available:
Not yet, we are still looking into it
Perfect, thank you!!!
-
Does this issue with packages also affect snort? The system I updated didn't have any packages, but one of my systems has snort, so wondering if I should hold off before updating it.
-
@bimmerdriver said in pfSense 2.4.5-RELEASE-p1 Now Available:
Does this issue with packages also affect snort? The system I updated didn't have any packages, but one of my systems has snort, so wondering if I should hold off before updating it.
In my case snort was not affected but many other packages were. But if it's a timing thing, I may have just been lucky. Having said that, the packages did actually install and were usable after installation despite need to kill the pkg-static process.
-
@bimmerdriver
I had snort and after upgrade it shown a new version available and all went thru without any problems -
after upgrade to P1 Everything OK . no problem, just wondering L2TP server is up but clients not able connect to server.
L2TP: waiting for connection on [wan ip] 1701
l2tps started, version 5.8 (root@pfSense_v2_4_5_amd64-pfSense_v2_4_5-job-01 23:02 6-Dec-2019)
l2tps Multi-link PPP daemon for FreeBSD -
2.4.5 had issues, 2.4.5p1 has more problems, not just on my personal firewall but on another I support, system specs are exact.
I know the PfSense team does their best to ensure stability and reliability but I can't help but feel like the ball has been dropped somewhere.
In all my years of using PfSense I've never seen so many problems unless using a software NIC like realtek and when a user has a problem the answer should NEVER be "wipe and reload". For a commercial client this means down time, lots of hours trying to fix the problem or calling the PfSense technical support and having them fix the problem and now that I think about it, from a commercial standpoint is a great opportunity to make some extra cash whether intentional or not.I was told with 2.4.5 that one should uninstall packages before updating.
Knowing user are running packages is pretty much a given so why should things break just because a update is being applied? Sure there's a lot of code to ensure everything goes smooth but this is a known variable in which updates are being applied.
2.4.5p1 the package installer breaks.... sometimes and I'm told the solutions is to reload from scratch, install the packages then load my config?How is that an acceptable practice? I'm seriously afraid to upgrade any other systems I support because there is a likelihood that they will break and then what? I have to reinstall, preinstall the packages and then re-load the config?
I'm seriously thinking it may be time to leave PfSense and go to something like OPNSense or just forget a open based firewall and going to Ubiquiti.
Oh, and for all those haters that want to flame me, you're another reason I'm thinking of leaving.
I've basicaly said I have (and others) have a problem with the pkg installer and there has been no resolution. -
@Visseroth I understand people can get frustrated when they head into problems, but the best way to deal with them is not shouting. I do not know what your investment in pfSense was, but many get pfSense CE for free so the positive and helpful kind of feedback is appreciated and not the "angry wet towel in the face" kind of feedback.
If you see a problem that other people have complained about and it seems no bug report have yet been reported then please make one at https://redmine.pfsense.org/projects/pfsense/roadmap (create an account or login) or reach out to customer support.Like Maba79 writes in https://forum.netgate.com/topic/154040/packet-manager-broke-in-gui-after-2-4-5-upgrade/6 it seems there is a workaround (I haven't tested it myself):
Executed: killall pkg-static pkg-static upgrade -f Saved the day.Cheers :)
-
@Visseroth
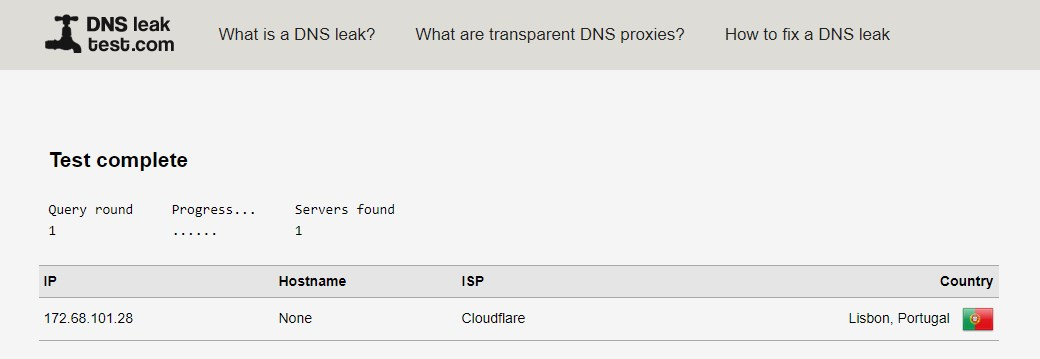
I agree with all your points... there is such a thing as Sofware Engineering, CMM, etc that most companies have thrown down the drain... now it's anti-engineering the daily bread.I was fiddling with browsers x webrtc leaks and then I found out that all OpenVPN connections were leaking my WAN IP DNS... that only happened after the 2.4.5_1 upgrade. I found that very odd... then I went to General Setup, option DNS Server Override, clicked status=checked, saved, then clicked status=unchecked, saved again, then it stopped leaking. So all of you out there may be leaking vpn DNSs right now after upgrade... that's an upgrade bug, a serious one.
I saw people complaining in the past of leakages that happened due to upgrades before, backup and restore... so pfSense team: start to make software engineering great again! Test, Test, Test, Test
I like pfSense, but it's a software for security and privacy, a reason of being... you guys must pay attention.
-
@avr So please report your finding on https://redmine.pfsense.org/projects/pfsense/roadmap and see it get addressed that is the correct place to report stuff if you have steps to reproduce. (You might want to check if others have reported something similar, but if in doubt better report the problem, because it can always be closed as a duplicate.)
-
@al Believe me when I say I wasn't yelling, more of a rant than a yell and to (hopefully )get the attention of the PfSense staff to let them know that it's not OK.
I understand there can be programming bugs and I did already post here...
https://forum.netgate.com/topic/154389/2-4-5r1-update-no-package-re-install/17
and got some help and it helped for a couple packages but I still have things getting stuck and if they are going to treat the CE crowd with crickets, specially those of us that have been with PfSense for over 10 years, if they are going to try and go the direction of Red-Hat and go commercial while forgetting about the little guys that helped get them there then I think it may be time to jump ship.I did try your post and received "pkg-static: Cannot get an advisory lock on a database, it is locked by another process"
Also, in response to the issue I have been having I did make a post days ago and tried what was posted and was very thankful and it didn't work which is why I posted what i did above.
I have no intentions to be a "towel whipper" but commercial issue or not everyone should be taken care of as best as possible and sure I'd call and get technical support but not for $400/incident (which I see is down from $600) but as @avr said this is supposed to be hardened security software, it is the front-line of defense for many networks, it has to be strong, robust but flexible while doing it's job and it is seemingly getting weaker over time and after reading some posts off OPNSense I'm starting to understand why.... https://forum.opnsense.org/index.php?topic=3144.0In the past this forum has had issues responding to posted issue and some people have been flamed and treated harshly, I've been one of them, at least I think so or maybe I'm just being sensitive but I do know that when i respond to clients I do my best to treat them with respect and give them the benefit of the doubt and if they call themselves technically illiterate then GREAT! I then prop them up and let them know that it's ok, that's why I'm here but by no means ever think that I know everything because no one can. I know enough to get the job done and if I don't I'll find someone that does.
Being humble goes a long ways, something much of the world has forgotten. We all get angry and point the finger so quickly and it saddens me greatly!
Anyhow, sorry about the rant again.
I'll post the bug but as I've seen in the past I don't expect to get a resolution, I'll likely get "Not enough information, Ticket Closed" -
@al Bug posted
-
@al Tried logging in, reset my password 3 times as I haven't logged in for quite some time, successfully reset the password each time, login fails each time.
Can't say I didn't try. -
@avr Great :) If you like please post the link to the bug report here as to keep you post and bug report "linked" together. Makes it easier for other people to find your bug report that may experience the same issue as you.
(Also if you find it useful maybe post a link to your forum post in the redmine ticket you created.)
Thanks
@Visseroth I understand your frustration and feelings. My only advice is reach out, describe/report, be succinct/to the point etc. People at Netgate are also people. You, I and the people at Netgate have probably both been the ones giving and getting support and trying to do our best. If Netgate does not do the best then it is the management problem, but somehow to me it is misplaced to have the critique posted here in the forum where we all should help each other and e.g. write bug reports when it seems needed and getting things back on track. :) So maybe - if needed - have a special "write to management" kind of channel if some specific general quality problem arises over and over again.
I know I probably cannot interface your problem and frustration 100% with this answer, but I do understand you frustration - trust me! -
@al
Issue:
After 2.4.5_1 upgrade OpenVPN connections started leaking WAN IP DNS
https://redmine.pfsense.org/issues/10664 -
@avr said in pfSense 2.4.5-RELEASE-p1 Now Available:
@al
Issue:
After 2.4.5_1 upgrade OpenVPN connections started leaking WAN IP DNS
https://redmine.pfsense.org/issues/10664Isn't dns-leakage while using VPN-clients a general problem in pfSense? Can't see what your have done would help there in the first place.
Do you have DNS Query Forwarding in the forwarder enabled? -
@Bob-Dig Enable Forwarding Mode is disabled
-
@Visseroth Strange. Please try using a different browser or an anonymous tab when logging in - it could be some cache stuff or an old cookie or something else that gives a problem.
-
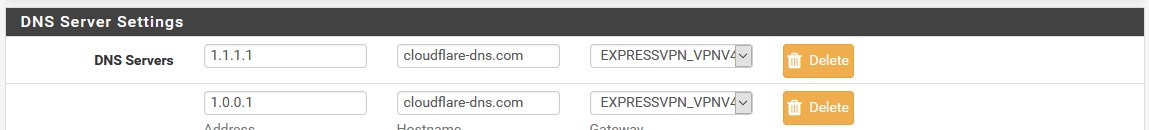
@avr Ok, same here. But I think tinkering under general setup is no solution in the first place. The only solution I am aware of is using only the vpn-client(s) as Outgoing Network Interfaces in the resolver. Works flawlessly.
-
Issue:
After 2.4.5_1 upgrade OpenVPN connections started leaking WAN IP DNS
https://redmine.pfsense.org/issues/10664Hi,
this is a misstatement:
"So all of you out there may be leaking vpn DNSs right now after upgrade... that's an upgrade bug, a serious one."this is not the case for everyone...