Unable to access to device on network A from network B on VLAN
-
Hello,
I am trying to migrate some rules that I already had working on another previous network, but I really dont know why, I simply cannot access the damn device.
This is the classic case of a guest network, where its suppose to have internet access, but not to other local networks in general, only to certain devices:
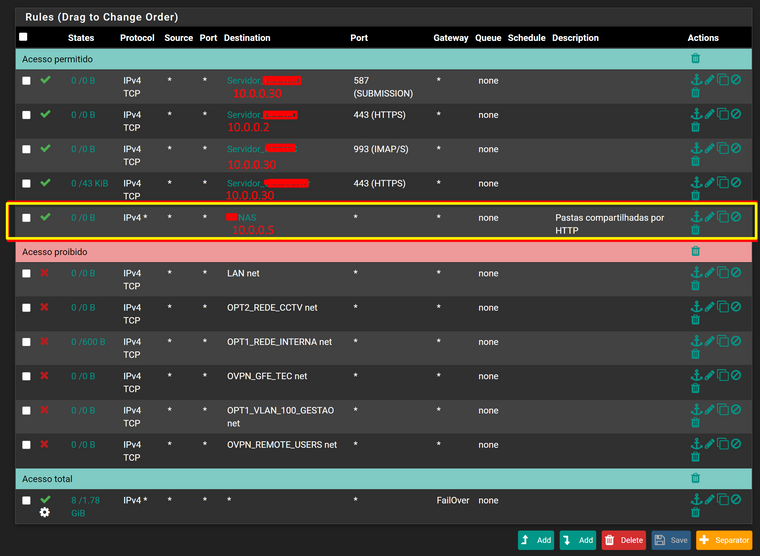
But seems like its possible to access to all the permited mail services but not that NAS 10.0.0.5 at all (I tried previously with ports 80 and 8080 and nothing) with the yellow rectangle.
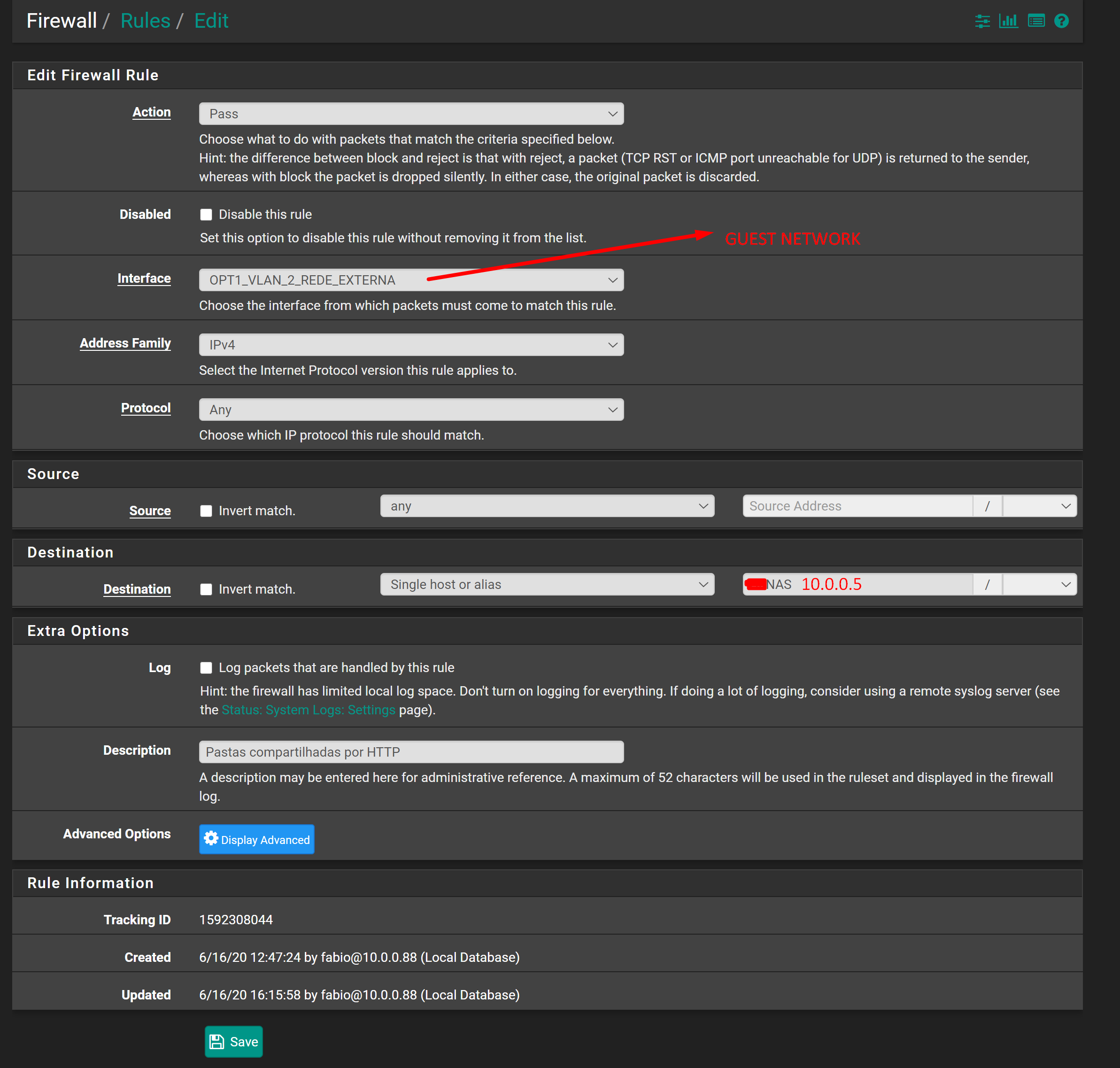
This is how the rule is setup:
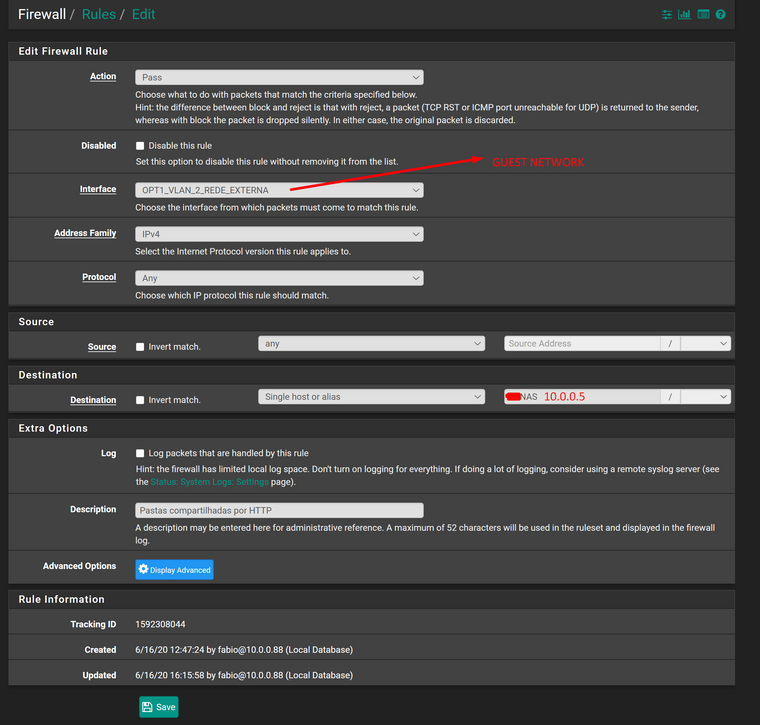
I really dont know why I cannot access that device, not even through ICMP PING.
Note that I can access from another network (an OpenVPN) to this device, without problem, and the device can reach internet and communicate with the rest of the network 10.0.0.0/24 where is it.
Anyone here knows what I am missing here?!
If you need more info feel free to ask.
-
Ensure that it isn't blocked by a floating rule or one on an interface group including the concerned interface.
To investigate, enable the logging in your rules and look in the firewall log to see which rule is applied to that traffic.
If the NAS responses to pings from outside its subnet you may use Diagnostic > Ping and check if you get a responses when using different sources.
-
There is no interface groups set in this firewall or even floating rules.
Just to let you know that I have Pure NAT activated and those 4 working rules with PASS permissions, are set to gain access for NAT rules set in OPT1_REDE_INTERNA net to be acessable from internet.
As a test I changed all block rules in that interface for other subnets, from TCP to ANY:
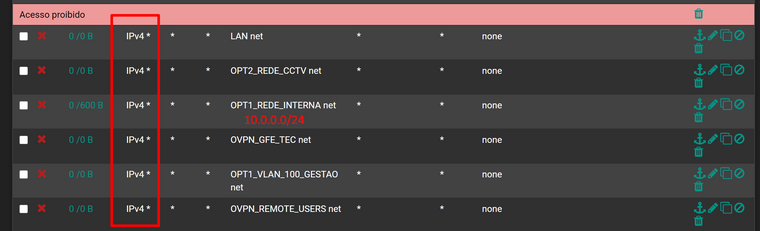
And use diagnostic ping, and I was able to ping from that interface nic 10.0.2.1 to 10.0.0.5:
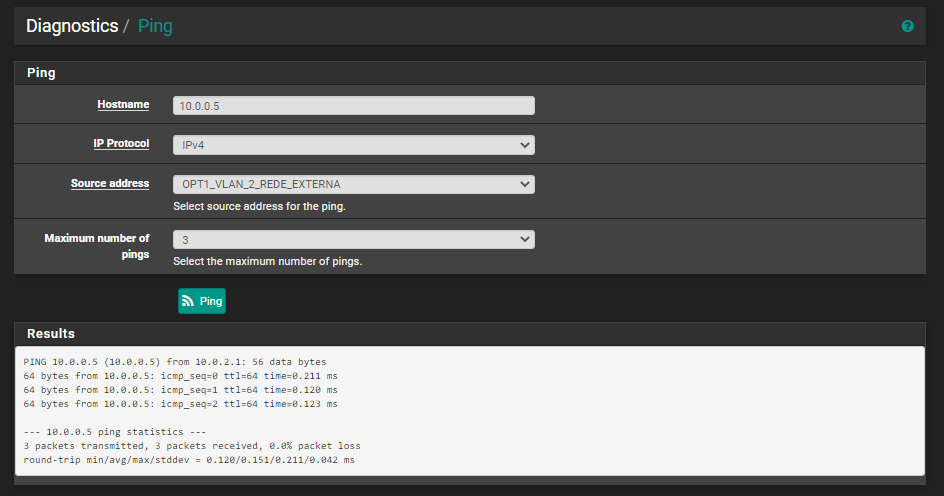
But I also made a ping to 10.0.0.88, who is another machine in OPT1_REDE_INTERNA net, and I was also able to ping, but it was not supposed to do it:
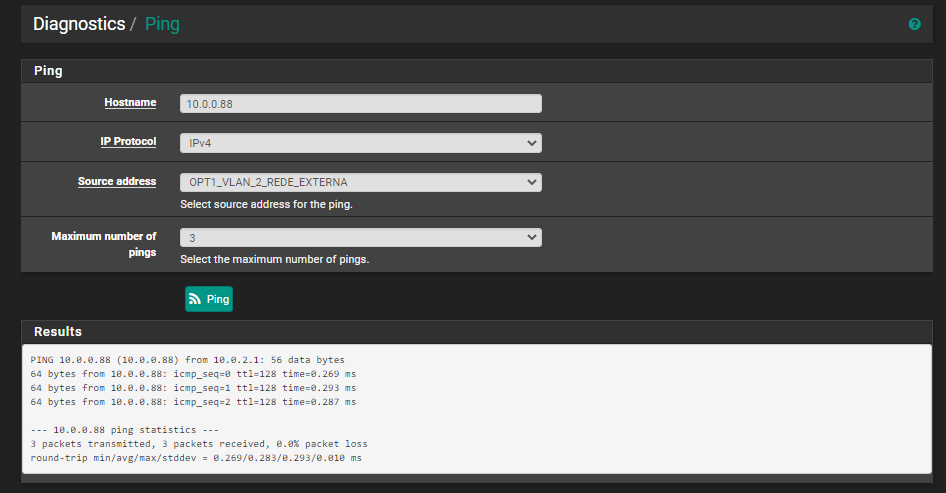
From a laptop device, connected to this subnet 10.0.2.1/24, its unable to ping to those blocked subnets (including 10.0.0.88), even to 10.0.0.5.
Its like all rules instead of those 4 rules and the rule for internet acess, that I have mentioned above, are not being applied to this interface.
This interface is new, I have created a VLAN 2 to run in OPT1 for it, where I had another network already running in OPT1 with the default VLAN 1 untagged (OPT1_REDE_INTERNA), but using this VLAN 2 I have only set a smart switch to use VLAN 2 tagged in the nic connected to pfsense, and the port used to connect to an ubiquiti AP, where I setup the corresponded WIFI to use that VLAN 2.
I have also created another VLAN 3 as a test, in OPT1 as well, and associate it to another WIFI in that AP, and samething, it doesnt respect all the rules created as it happeans with that network in VLAN 2.
I have already check if there was duplicated subnets that could be messing around but there is nothing.
Damn I really dont know what can be overide those rules ... on other interfaces using non tagged VLANs it works as expected, through interface using VLANs not.
I am still using pfsense 2.4.4-RELEASE-p3, and notice that there was some changes in VLANs and Rules in next 3 updates, but I am not sure if could be from that.
-
Seems like on those VLANs, there is something blocking access to bogon networks, even between machines inside of the same VLAN network, who is a also a bogon network.
Only rules in NAT are accessable, that was setup for WAN uplink.
But still not sure if is something on pfsense (even knowing that there is no rules for those interfaces), or HPE 1920s smartswitch in the middle or even on ubiquiti AP LR.
-
So I finaly discovered what was causing this, and it was from Ubiquiti AP, with this option checked:
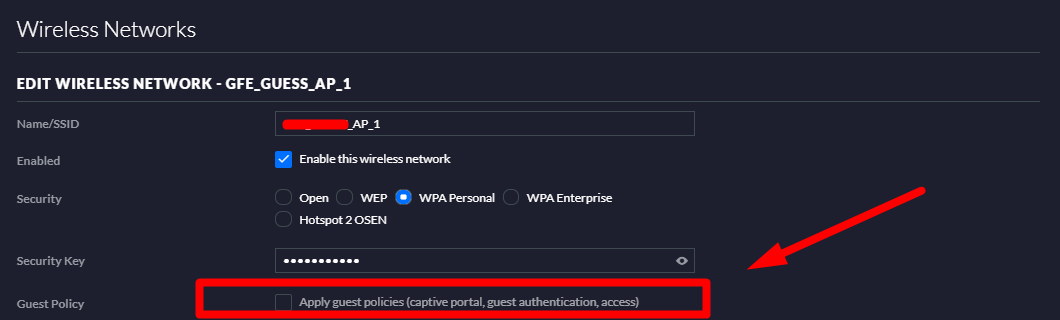
After being enable, to unable, it was necessary to restart all WIFI current connections. Doing that it worked like a charm.
I have set that option because there was a diferent icon associated with devices connected to that wireless network, but I was not expecting that there was rules being applied since I am only using Ubiquiti APs, and not firewalls.
Thanks anyway for the help.