LDAP SSL AD auth Issue with 2.4.5-RELEASE
-
Hi there
As mentioned in the title i've got a pfsense CE firewall running 2.4.5-RELEASE. I'm trying to connect to my local AD server via LDAP with SSL. I'm not able to bind for some reason. After reading several other threads and trying all the suggestions I'm coming up short. I have another 2.3.5 firewall that can connect to the same server just fine. I can't update the firewall right away but I didn't find any LDAP SSL fixes in the release notes for newer versions.
- the CN of the cert matches the hostname of the AD server. I verified this by running this command on the firewall:
openssl s_client -connect {the_server}:636 ... subject=/CN=the_server's_hostname.foo.bar issuer={the_AD_cert_authority} ...- The root CA cert for the CA that issued the server cert is imported as a CA and selected in the LDAP settings as described below
- There are no intermediate certs between the LDAP server cert and CA cert
- pfSense is attempting to use the correct CA as evidenced by the fact that it's creating a temporary file in /var/run/certs with expected CA cert
- I checked the temporary CA file against the cert I grabbed from the openssl output above and got a match:
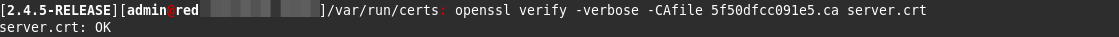
[2.4.5-RELEASE][admin@thefirewall]/var/run/certs: openssl verify -verbose -CAfile 5ef664ff38d6c.ca server_cert.crt server_cert.crt: OK- A packet capture shows that the firewall is responding to the LDAP server that the cert presented doesn't match the CA:
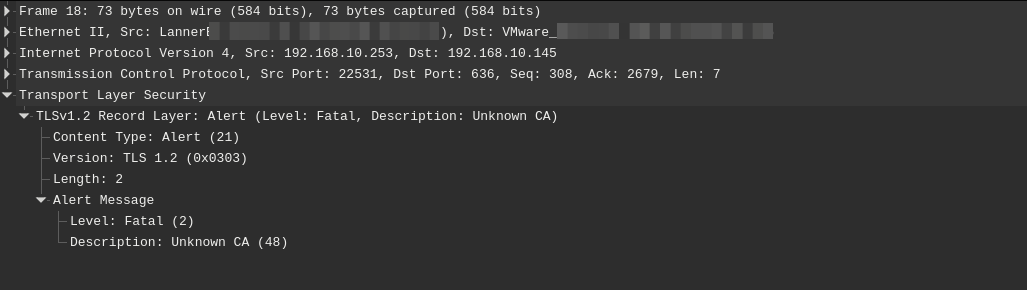
TLSv1.2 Record Layer: Alert (Level: Fatal, Description: Unknown CA)Settings:
Hostname or IP address: {the AD server}
Port value: 636
Transport: SSL - Encrypted
Peer Certificate Authority: {the_AD_cert_authority}
Protocol version: 3
Server Timeout: 25
Search scopeLevel: Entire SubtreeBase DN: {Tree root}
Authentication containers: {OU of admins}
Extended query: unchecked
Bind anonymous: unchecked
Bind credentials: DOMAIN\binduserUser naming attribute: samAccountName
Group naming attribute: cn
Group member attribute: memberOf
RFC 2307 Groups: unchecked
Group Object Class: posixGroup
UTF8 Encode: unchecked
Username Alterations: uncheckedAny help would be greatly appreciated. Thanks!
-
Forgot to mention I have multiple 2.4.4 firewalls with the same issue.
-
Hostname or IP address: {the AD server}
Is that the hostname or an IP address? Is that hostname or IP address listed in the server certificate SAN list?
-
@jimp it's the fully qualified hostname which matches the subject and SAN of the server certificate.
-
OK. First things first, try to run options 16 and 11 from the console (ssh or serial/video console), or reboot after making any changes to the LDAP auth config. Sometimes the PHP LDAP environment gets out of sync and the 16/11 combo is the fastest way to ensure it's consistent.
-
I'm a bit embarrassed to admit that worked. I definitely should have tried that. Thanks!!
-
Hi there,
I just updated my Netgate SG-5100 from version 2.4.3-p3 to 2.4.5-p1 and LDAPS authentication stopped working. Same situation presented by the OP, except I'm using FreeIPA (or Red Hat IdM) as the authentication server.
After several hours of troubleshooting I came across this post. Tried a reboot as well as running the 16/11 options, as Jim pointed out, but with no success.
LDAP Server Settings:
- Hostname or IP address: ipa.company.local
- Port value: 636
- Transport: SSL - Encrypted
- Peer Certificate Authority: Company CA
- Client Certificate: LDAPS Company Cert
- Protocol version: 3
- Server Timeout: 25
- Search scope: Entire Subtree
- Base DN: cn=accounts,dc=celfocus,dc=local
- Authentication containers: cn=users,cn=accounts,dc=company,dc=local
- Extended query: checked
- Query: memberOf=cn=pfsense,cn=groups,cn=accounts,dc=company,dc=local
- Bind anonymous: unchecked
- Bind credentials: uid=iparo,cn=users,cn=accounts,dc=company,dc=local
- User naming attribute: uid
- Group naming attribute: cn
- Group member attribute: memberUid
- RFC 2307 Groups: unchecked
- Group Object Class: posixGroup
- UTF8 Encode: unchecked
- Username Alterations: unchecked
server.crt:
pcap from pfSense:
IPA access log:
[03/Sep/2020:15:02:54.482504753 +0100] conn=1103219 op=-1 fd=192 closed - Peer does not recognize and trust the CA that issued your certificate.Is there anything else I can check?
-
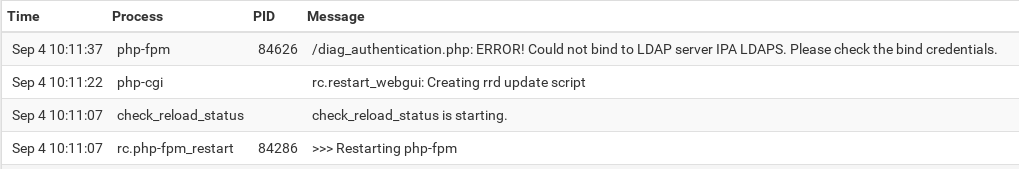
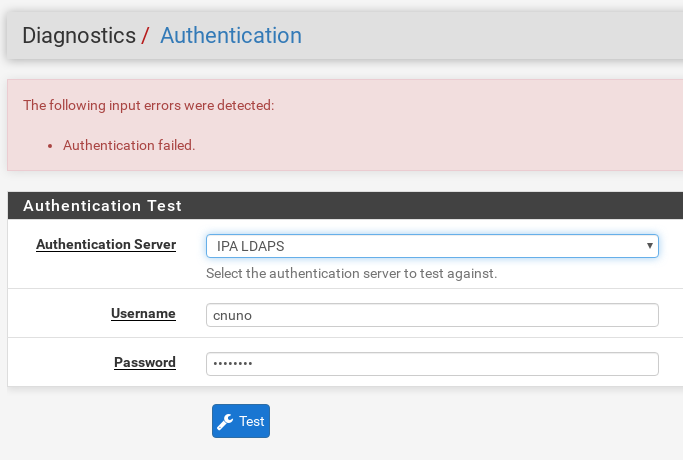
Forgot to post LDAPS auth test and system logs:
System logs: