suricata fail to launch after update
-
Hey all
I´m new in here and this is my first post, im not english so sorry for my spelling..i got pfsense
2.5.0-DEVELOPMENT (amd64)
built on Mon Jul 06 01:01:56 EDT 2020
FreeBSD 12.1-STABLEi just update with lastest update and now my suricata dont work, is just gone from the menu drop down.
i ditn´t stop and disable the suricata before update, dont know if this cause this error?
i tried to uninstall and install it again with same fail :-/
i got this:Crash report begins. Anonymous machine information:
amd64
12.1-STABLE
FreeBSD 12.1-STABLE df4360fdf61(devel-12) pfSenseCrash report details:
PHP Errors:
[06-Jul-2020 12:02:44 Europe/Copenhagen] PHP Warning: filesize(): stat failed for /usr/local/etc/suricata/suricata_53171_em0/rules/suricata.rules in /usr/local/pkg/suricata/suricata_generate_yaml.php on line 1009
[06-Jul-2020 12:02:44 Europe/Copenhagen] PHP Warning: filesize(): stat failed for /usr/local/etc/suricata/suricata_53171_em0/rules/flowbit-required.rules in /usr/local/pkg/suricata/suricata_generate_yaml.php on line 1011
[06-Jul-2020 12:02:44 Europe/Copenhagen] PHP Warning: filesize(): stat failed for /usr/local/etc/suricata/suricata_53171_em0/rules/custom.rules in /usr/local/pkg/suricata/suricata_generate_yaml.php on line 1013No FreeBSD crash data found.
hope you guys can help, or do i need a fresh pfsense install ?
-
@pet1975 said in suricata fail to launch after update:
Hey all
I´m new in here and this is my first post, im not english so sorry for my spelling..i got pfsense
2.5.0-DEVELOPMENT (amd64)
built on Mon Jul 06 01:01:56 EDT 2020
FreeBSD 12.1-STABLEi just update with lastest update and now my suricata dont work, is just gone from the menu drop down.
i ditn´t stop and disable the suricata before update, dont know if this cause this error?
i tried to uninstall and install it again with same fail :-/
i got this:Crash report begins. Anonymous machine information:
amd64
12.1-STABLE
FreeBSD 12.1-STABLE df4360fdf61(devel-12) pfSenseCrash report details:
PHP Errors:
[06-Jul-2020 12:02:44 Europe/Copenhagen] PHP Warning: filesize(): stat failed for /usr/local/etc/suricata/suricata_53171_em0/rules/suricata.rules in /usr/local/pkg/suricata/suricata_generate_yaml.php on line 1009
[06-Jul-2020 12:02:44 Europe/Copenhagen] PHP Warning: filesize(): stat failed for /usr/local/etc/suricata/suricata_53171_em0/rules/flowbit-required.rules in /usr/local/pkg/suricata/suricata_generate_yaml.php on line 1011
[06-Jul-2020 12:02:44 Europe/Copenhagen] PHP Warning: filesize(): stat failed for /usr/local/etc/suricata/suricata_53171_em0/rules/custom.rules in /usr/local/pkg/suricata/suricata_generate_yaml.php on line 1013No FreeBSD crash data found.
hope you guys can help, or do i need a fresh pfsense install ?
Those particular messages from PHP are warnings not fatal errors, so they are not the cause of your failure to start issue. I suspect they are just victims in a manner of speaking.
You need to look in two places for hints on the startup failure.
-
Look first in the pfSense system log to see if there are any Suricata startup-related messages logged there that give any hints.
-
Next, go to the LOGS VIEW tab in Suricata and select the
suricata.logfile for the interface and see what's in there. If you don't see the cause of the startup failure in that log, then proceed with step #3 below. -
Try to start Suricata from a shell prompt so you can see if there are any missing libraries. Open a shell prompt (command-line session) on the firewall either directly on the console or via an SSH connection. Use this command to start Suricata and show version information --
/usr/local/bin/suricata -VSuricata should show the current version information for the binary and then exit. If you see any errors about missing libraries instead, then you have found the source of your failure to start.
Post back here with what you find.
-
-
thanks for repley
solution 1
didt´n show any error regarding suricata, it just said all package start succesfully :-)solution 2
not at option because suricata is missing from the dropdown menu under services :-( is just gonein Command Prompt /usr/local/bin/suricata -V
it says
"This is Suricata version 5.0.2 RELEASE"thanks for trying to help :-)
-
@pet1975 said in suricata fail to launch after update:
thanks for repley
solution 1
didt´n show any error regarding suricata, it just said all package start succesfully :-)solution 2
not at option because suricata is missing from the dropdown menu under services :-( is just gonein Command Prompt /usr/local/bin/suricata -V
it says
"This is Suricata version 5.0.2 RELEASE"thanks for trying to help :-)
If Suricata is missing, then the installation did not complete. Writing the entry under SERVICES is one of the last things done.
Let's try another approach. Follow these steps --
- If Suricata shows up under SYSTEM > PACKAGES on the Installed Pacakges tab, the click the trash icon to delete it. If it does not show up there, then open another shell prompt session on the firewall and remove the Suricata GUI package using this command:
pkg delete pfSense-pkg-suricata-5.0.2_3-
Once Suricata is removed return to SYSTEM > PACKAGES and on the Available Packages tab find Suricata and install it again. Let the install complete. It shoud show a green complete bar. Note the installation progress messages as they scroll by. See if any errors are shown. In particular look for any messages about the GeoIP database.
-
When the install completes, but BEFORE leaving that page, copy the entire contents of the scrolling textbox and paste them back into a reply post to this thread. I want to see if anything is happening during the install process.
I know you've already tried a reinstall, but what I want to get from the steps above is the complete output of the installation log. I need that to verify my hypothesis.
-
Installing pfSense-pkg-suricata...
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
Checking integrity... done (0 conflicting)
The following 21 package(s) will be affected (of 0 checked):New packages to be INSTALLED:
barnyard2: 1.13_5 [pfSense]
broccoli: 1.101,1 [pfSense]
cyrus-sasl: 2.1.27_1 [pfSense]
groff: 1.22.4_3 [pfSense]
hiredis: 0.13.3 [pfSense]
hyperscan: 4.7.0_3 [pfSense]
jansson: 2.12 [pfSense]
libnet: 1.1.6_5,1 [pfSense]
libpaper: 1.1.24.4 [pfSense]
libpcap: 1.9.1_1 [pfSense]
libyaml: 0.2.2 [pfSense]
mysql57-client: 5.7.30_1 [pfSense]
nspr: 4.26 [pfSense]
nss: 3.53.1 [pfSense]
pfSense-pkg-suricata: 5.0.2_3 [pfSense]
protobuf: 3.11.4,1 [pfSense]
psutils: 1.17_5 [pfSense]
py37-yaml: 5.3.1 [pfSense]
python27: 2.7.18 [pfSense]
suricata: 5.0.2_3 [pfSense]
uchardet: 0.0.6 [pfSense]Number of packages to be installed: 21
The process will require 202 MiB more space.
[1/21] Installing libpaper-1.1.24.4...
[1/21] Extracting libpaper-1.1.24.4: .......... done
[2/21] Installing uchardet-0.0.6...
[2/21] Extracting uchardet-0.0.6: .......... done
[3/21] Installing psutils-1.17_5...
[3/21] Extracting psutils-1.17_5: .......... done
[4/21] Installing nspr-4.26...
[4/21] Extracting nspr-4.26: .......... done
[5/21] Installing cyrus-sasl-2.1.27_1...
*** Updated user `cyrus'.
[5/21] Extracting cyrus-sasl-2.1.27_1: .......... done
[6/21] Installing python27-2.7.18...
[6/21] Extracting python27-2.7.18: .......... done
[7/21] Installing groff-1.22.4_3...
[7/21] Extracting groff-1.22.4_3: .......... done
[8/21] Installing protobuf-3.11.4,1...
[8/21] Extracting protobuf-3.11.4,1: .......... done
[9/21] Installing libyaml-0.2.2...
[9/21] Extracting libyaml-0.2.2: ......... done
[10/21] Installing nss-3.53.1...
[10/21] Extracting nss-3.53.1: .......... done
[11/21] Installing libpcap-1.9.1_1...
[11/21] Extracting libpcap-1.9.1_1: .......... done
[12/21] Installing libnet-1.1.6_5,1...
[12/21] Extracting libnet-1.1.6_5,1: .......... done
[13/21] Installing py37-yaml-5.3.1...
[13/21] Extracting py37-yaml-5.3.1: .......... done
[14/21] Installing jansson-2.12...
[14/21] Extracting jansson-2.12: .......... done
[15/21] Installing hyperscan-4.7.0_3...
[15/21] Extracting hyperscan-4.7.0_3: .......... done
[16/21] Installing hiredis-0.13.3...
[16/21] Extracting hiredis-0.13.3: .......... done
[17/21] Installing broccoli-1.101,1...
[17/21] Extracting broccoli-1.101,1: .......... done
[18/21] Installing mysql57-client-5.7.30_1...
[18/21] Extracting mysql57-client-5.7.30_1: .......... done
[19/21] Installing suricata-5.0.2_3...
[19/21] Extracting suricata-5.0.2_3: .......... done
[20/21] Installing barnyard2-1.13_5...
[20/21] Extracting barnyard2-1.13_5: ...... done
[21/21] Installing pfSense-pkg-suricata-5.0.2_3...
[21/21] Extracting pfSense-pkg-suricata-5.0.2_3: .......... done
Saving updated package information...
done.
Loading package configuration... done.
Configuring package components...
Loading package instructions...
Custom commands...
Executing custom_php_install_command()...=====
Message from cyrus-sasl-2.1.27_1:--
You can use sasldb2 for authentication, to add users use:saslpasswd2 -c usernameIf you want to enable SMTP AUTH with the system Sendmail, read
Sendmail.READMENOTE: This port has been compiled with a default pwcheck_method of
auxprop. If you want to authenticate your user by /etc/passwd,
PAM or LDAP, install ports/security/cyrus-sasl2-saslauthd and
set sasl_pwcheck_method to saslauthd after installing the
Cyrus-IMAPd 2.X port. You should also check the
/usr/local/lib/sasl2/*.conf files for the correct
pwcheck_method.
If you want to use GSSAPI mechanism, install
ports/security/cyrus-sasl2-gssapi.
If you want to use SRP mechanism, install
ports/security/cyrus-sasl2-srp.
If you want to use LDAP auxprop plugin, install
ports/security/cyrus-sasl2-ldapdb.Message from python27-2.7.18:
--
Note that some standard Python modules are provided as separate ports
as they require additional dependencies. They are available as:bsddb databases/py-bsddb
gdbm databases/py-gdbm
sqlite3 databases/py-sqlite3
tkinter x11-toolkits/py-tkinter===> NOTICE:
This port is deprecated; you may wish to reconsider installing it:
EOLed upstream.
It is scheduled to be removed on or after 2020-12-31.
Message from groff-1.22.4_3:
--
In order to be able to use the html driver, you need to install the following
packages:- ghostscript
- netpbm
=====
Message from mysql57-client-5.7.30_1:
--
This is the mysql CLIENT without the server.
for complete server and client, please install databases/mysql57-serverMessage from suricata-5.0.2_3:
--
If you want to run Suricata in IDS mode, add to /etc/rc.conf:suricata_enable="YES" suricata_interface="<if>"NOTE: Declaring suricata_interface is MANDATORY for Suricata in IDS Mode.
However, if you want to run Suricata in Inline IPS Mode in divert(4) mode,
add to /etc/rc.conf:suricata_enable="YES" suricata_divertport="8000"NOTE:
Suricata won't start in IDS mode without an interface configured.
Therefore if you omit suricata_interface from rc.conf, FreeBSD's
rc.d/suricata will automatically try to start Suricata in IPS Mode
(on divert port 8000, by default).Alternatively, if you want to run Suricata in Inline IPS Mode in high-speed
netmap(4) mode, add to /etc/rc.conf:suricata_enable="YES" suricata_netmap="YES"NOTE:
Suricata requires additional interface settings in the configuration
file to run in netmap(4) mode.RULES: Suricata IDS/IPS Engine comes without rules by default. You should
add rules by yourself and set an updating strategy. To do so, please visit:http://www.openinfosecfoundation.org/documentation/rules.html
http://www.openinfosecfoundation.org/documentation/emerging-threats.htmlYou may want to try BPF in zerocopy mode to test performance improvements:
sysctl -w net.bpf.zerocopy_enable=1Don't forget to add net.bpf.zerocopy_enable=1 to /etc/sysctl.conf
Message from barnyard2-1.13_5:
--
Read the notes in the barnyard2.conf file for how to configure
/usr/local/etc/barnyard2.conf after installation. For addtional information
see the Securixlive FAQ at http://www.securixlive.com/barnyard2/faq.php.In order to enable barnyard2 to start on boot, you must edit /etc/rc.conf
with the appropriate flags, etc. See the FreeBSD Handbook for syntax:
http://www.freebsd.org/doc/en_US.ISO8859-1/books/handbook/configtuning-rcng.htmlFor the various options available, type % barnyard2 -h after install or read
the options in the startup script - in /usr/local/etc/rc.d.Barnyard2 can process unified2 files from snort or suricata. It can also
interact with snortsam firewall rules as well as the sguil-sensor. Those
ports must be installed separately if you wish to use them.Cleaning up cache... done.
Success -
@pet1975 said in suricata fail to launch after update:
Executing custom_php_install_command()...=====
This line from the installation log is not correct --
Executing custom_php_install_command()...=====It is incomplete as there should be a series of new lines printed showing various things happening related to migrating configuration settings, downloading rules and rebuilding interface
suricata.yamlconfiguration files. I don't see any of that.Also, the "====" text is extremely weird and should not be there. Is that exactly how it appeared in the textbox on your firewall, or did something get whacked during the copy/paste operation over to the forum post?
I assume Suricata is still not showing up under the SERVICES menu either?
-
this is exactly what the txt are from the green install box
no still no suricata in the SERVICES menu :-(
Maybe i should make a clean install of pfsense? install all update and then install the package ?
-
Sorry to be late responding. I've been working today on the next update for the Suricata package.
As part of that work, I just now installed Suricata on a pfSense-2.5 DEVEL virtual machine without issues. Here is the install log --
Installing pfSense-pkg-suricata... Updating pfSense-core repository catalogue... pfSense-core repository is up to date. Updating pfSense repository catalogue... pfSense repository is up to date. All repositories are up to date. The following 12 package(s) will be affected (of 0 checked): New packages to be INSTALLED: hiredis: 0.13.3 [pfSense] hyperscan: 4.7.0_3 [pfSense] jansson: 2.12 [pfSense] libmaxminddb: 1.4.2 [pfSense] libnet: 1.1.6_5,1 [pfSense] libpcap: 1.9.1_1 [pfSense] libyaml: 0.2.2 [pfSense] nspr: 4.26 [pfSense] nss: 3.53.1 [pfSense] pfSense-pkg-suricata: 5.0.3 [pfSense] py37-yaml: 5.3.1 [pfSense] suricata: 5.0.3 [pfSense] Number of packages to be installed: 12 The process will require 38 MiB more space. 138 KiB to be downloaded. [1/1] Fetching pfSense-pkg-suricata-5.0.3.txz: .......... done Checking integrity... done (0 conflicting) [1/12] Installing nspr-4.26... [1/12] Extracting nspr-4.26: .......... done [2/12] Installing libyaml-0.2.2... [2/12] Extracting libyaml-0.2.2: ......... done [3/12] Installing nss-3.53.1... [3/12] Extracting nss-3.53.1: .......... done [4/12] Installing libpcap-1.9.1_1... [4/12] Extracting libpcap-1.9.1_1: .......... done [5/12] Installing libnet-1.1.6_5,1... [5/12] Extracting libnet-1.1.6_5,1: .......... done [6/12] Installing libmaxminddb-1.4.2... [6/12] Extracting libmaxminddb-1.4.2: .......... done [7/12] Installing py37-yaml-5.3.1... [7/12] Extracting py37-yaml-5.3.1: .......... done [8/12] Installing jansson-2.12... [8/12] Extracting jansson-2.12: .......... done [9/12] Installing hyperscan-4.7.0_3... [9/12] Extracting hyperscan-4.7.0_3: .......... done [10/12] Installing hiredis-0.13.3... [10/12] Extracting hiredis-0.13.3: .......... done [11/12] Installing suricata-5.0.3... [11/12] Extracting suricata-5.0.3: .......... done [12/12] Installing pfSense-pkg-suricata-5.0.3... [12/12] Extracting pfSense-pkg-suricata-5.0.3: .......... done Saving updated package information... done. Loading package configuration... done. Configuring package components... Loading package instructions... Custom commands... Executing custom_php_install_command()...Saved settings detected... Migrating settings to new configuration... done. Downloading Emerging Threats Open rules md5 file... done. There is a new set of Emerging Threats Open rules posted. Downloading... done. Downloading Snort VRT rules md5 file... done. There is a new set of Snort rules posted. Downloading... done. Downloading Snort GPLv2 Community Rules md5 file... done. There is a new set of Snort GPLv2 Community Rules posted. Downloading... done. Installing Emerging Threats Open rules... done. Installing Snort rules... done. Installing Snort GPLv2 Community Rules... done. Updating rules configuration for: WAN ... done. Updating rules configuration for: LAN ... done. Cleaning up after rules extraction... done. The Rules update has finished. Generating suricata.yaml configuration file from saved settings. Generating YAML configuration file for WAN... done. Generating YAML configuration file for LAN... done. Finished rebuilding Suricata configuration from saved settings. Setting package version in configuration file. done. Executing custom_php_resync_config_command()...done. Menu items... done. Services... done. Writing configuration... done. ===== Message from suricata-5.0.3: -- If you want to run Suricata in IDS mode, add to /etc/rc.conf: suricata_enable="YES" suricata_interface="<if>" NOTE: Declaring suricata_interface is MANDATORY for Suricata in IDS Mode. However, if you want to run Suricata in Inline IPS Mode in divert(4) mode, add to /etc/rc.conf: suricata_enable="YES" suricata_divertport="8000" NOTE: Suricata won't start in IDS mode without an interface configured. Therefore if you omit suricata_interface from rc.conf, FreeBSD's rc.d/suricata will automatically try to start Suricata in IPS Mode (on divert port 8000, by default). Alternatively, if you want to run Suricata in Inline IPS Mode in high-speed netmap(4) mode, add to /etc/rc.conf: suricata_enable="YES" suricata_netmap="YES" NOTE: Suricata requires additional interface settings in the configuration file to run in netmap(4) mode. RULES: Suricata IDS/IPS Engine comes without rules by default. You should add rules by yourself and set an updating strategy. To do so, please visit: http://www.openinfosecfoundation.org/documentation/rules.html http://www.openinfosecfoundation.org/documentation/emerging-threats.html You may want to try BPF in zerocopy mode to test performance improvements: sysctl -w net.bpf.zerocopy_enable=1 Don't forget to add net.bpf.zerocopy_enable=1 to /etc/sysctl.conf Cleaning up cache... done. SuccessNotice that this section of my log is quite different from yours:
Executing custom_php_install_command()...Saved settings detected... Migrating settings to new configuration... done. Downloading Emerging Threats Open rules md5 file... done. There is a new set of Emerging Threats Open rules posted. Downloading... done. Downloading Snort VRT rules md5 file... done. There is a new set of Snort rules posted. Downloading... done. Downloading Snort GPLv2 Community Rules md5 file... done. There is a new set of Snort GPLv2 Community Rules posted. Downloading... done. Installing Emerging Threats Open rules... done. Installing Snort rules... done. Installing Snort GPLv2 Community Rules... done. Updating rules configuration for: WAN ... done. Updating rules configuration for: LAN ... done. Cleaning up after rules extraction... done. The Rules update has finished. Generating suricata.yaml configuration file from saved settings. Generating YAML configuration file for WAN... done. Generating YAML configuration file for LAN... done. Finished rebuilding Suricata configuration from saved settings. Setting package version in configuration file. done. Executing custom_php_resync_config_command()...done. Menu items... done. Services... done. Writing configuration... done. =====Your log only shows the five "=" characters.
- Did you have an existing Suricata configuration on this firewall before?
- Is the firewall current with the latest pfSense-2.5 snapshot (assuming you are still running the DEVEL version of pfSense on the box)?
If you are still running pfSense-2.5, and you are not current with the most recent snapshot, try removing the Suricata package and then updating to the most recent snapshot of pfSense-2.5. When that is finished, try installing Suricata again and post back with the results. I'm really perplexed at this point about what the issue could be. As I mentioned, I installed Suricata without incident today on a current 2.5-DEVEL snapshot of pfSense. I did have an existing Suricata configuration on the virtual machine, but I first deleted the package and saved my config before installing the package again.
-
This is after i delete Suricata, update snapshot and then install suricata again. and still no suricata in service menu
Installing pfSense-pkg-suricata...
Updating pfSense-core repository catalogue...
pfSense-core repository is up to date.
Updating pfSense repository catalogue...
pfSense repository is up to date.
All repositories are up to date.
Checking integrity... done (0 conflicting)
The following 21 package(s) will be affected (of 0 checked):New packages to be INSTALLED:
barnyard2: 1.13_5 [pfSense]
broccoli: 1.101,1 [pfSense]
cyrus-sasl: 2.1.27_1 [pfSense]
groff: 1.22.4_3 [pfSense]
hiredis: 0.13.3 [pfSense]
hyperscan: 4.7.0_3 [pfSense]
jansson: 2.12 [pfSense]
libnet: 1.1.6_5,1 [pfSense]
libpaper: 1.1.24.4 [pfSense]
libpcap: 1.9.1_1 [pfSense]
libyaml: 0.2.2 [pfSense]
mysql57-client: 5.7.30_1 [pfSense]
nspr: 4.26 [pfSense]
nss: 3.53.1 [pfSense]
pfSense-pkg-suricata: 5.0.2_3 [pfSense]
protobuf: 3.11.4,1 [pfSense]
psutils: 1.17_5 [pfSense]
py37-yaml: 5.3.1 [pfSense]
python27: 2.7.18 [pfSense]
suricata: 5.0.2_3 [pfSense]
uchardet: 0.0.6 [pfSense]Number of packages to be installed: 21
The process will require 202 MiB more space.
[1/21] Installing libpaper-1.1.24.4...
[1/21] Extracting libpaper-1.1.24.4: .......... done
[2/21] Installing uchardet-0.0.6...
[2/21] Extracting uchardet-0.0.6: .......... done
[3/21] Installing psutils-1.17_5...
[3/21] Extracting psutils-1.17_5: .......... done
[4/21] Installing nspr-4.26...
[4/21] Extracting nspr-4.26: .......... done
[5/21] Installing cyrus-sasl-2.1.27_1...
*** Updated user `cyrus'.
[5/21] Extracting cyrus-sasl-2.1.27_1: .......... done
[6/21] Installing python27-2.7.18...
[6/21] Extracting python27-2.7.18: .......... done
[7/21] Installing groff-1.22.4_3...
[7/21] Extracting groff-1.22.4_3: .......... done
[8/21] Installing protobuf-3.11.4,1...
[8/21] Extracting protobuf-3.11.4,1: .......... done
[9/21] Installing libyaml-0.2.2...
[9/21] Extracting libyaml-0.2.2: ......... done
[10/21] Installing nss-3.53.1...
[10/21] Extracting nss-3.53.1: .......... done
[11/21] Installing libpcap-1.9.1_1...
[11/21] Extracting libpcap-1.9.1_1: .......... done
[12/21] Installing libnet-1.1.6_5,1...
[12/21] Extracting libnet-1.1.6_5,1: .......... done
[13/21] Installing py37-yaml-5.3.1...
[13/21] Extracting py37-yaml-5.3.1: .......... done
[14/21] Installing jansson-2.12...
[14/21] Extracting jansson-2.12: .......... done
[15/21] Installing hyperscan-4.7.0_3...
[15/21] Extracting hyperscan-4.7.0_3: .......... done
[16/21] Installing hiredis-0.13.3...
[16/21] Extracting hiredis-0.13.3: .......... done
[17/21] Installing broccoli-1.101,1...
[17/21] Extracting broccoli-1.101,1: .......... done
[18/21] Installing mysql57-client-5.7.30_1...
[18/21] Extracting mysql57-client-5.7.30_1: .......... done
[19/21] Installing suricata-5.0.2_3...
[19/21] Extracting suricata-5.0.2_3: .......... done
[20/21] Installing barnyard2-1.13_5...
[20/21] Extracting barnyard2-1.13_5: ...... done
[21/21] Installing pfSense-pkg-suricata-5.0.2_3...
[21/21] Extracting pfSense-pkg-suricata-5.0.2_3: .......... done
Saving updated package information...
done.
Loading package configuration... done.
Configuring package components...
Loading package instructions...
Custom commands...
Executing custom_php_install_command()...=====
Message from cyrus-sasl-2.1.27_1:--
You can use sasldb2 for authentication, to add users use:saslpasswd2 -c usernameIf you want to enable SMTP AUTH with the system Sendmail, read
Sendmail.READMENOTE: This port has been compiled with a default pwcheck_method of
auxprop. If you want to authenticate your user by /etc/passwd,
PAM or LDAP, install ports/security/cyrus-sasl2-saslauthd and
set sasl_pwcheck_method to saslauthd after installing the
Cyrus-IMAPd 2.X port. You should also check the
/usr/local/lib/sasl2/*.conf files for the correct
pwcheck_method.
If you want to use GSSAPI mechanism, install
ports/security/cyrus-sasl2-gssapi.
If you want to use SRP mechanism, install
ports/security/cyrus-sasl2-srp.
If you want to use LDAP auxprop plugin, install
ports/security/cyrus-sasl2-ldapdb.Message from python27-2.7.18:
--
Note that some standard Python modules are provided as separate ports
as they require additional dependencies. They are available as:bsddb databases/py-bsddb
gdbm databases/py-gdbm
sqlite3 databases/py-sqlite3
tkinter x11-toolkits/py-tkinter===> NOTICE:
This port is deprecated; you may wish to reconsider installing it:
EOLed upstream.
It is scheduled to be removed on or after 2020-12-31.
Message from groff-1.22.4_3:
--
In order to be able to use the html driver, you need to install the following
packages:- ghostscript
- netpbm
=====
Message from mysql57-client-5.7.30_1:
--
This is the mysql CLIENT without the server.
for complete server and client, please install databases/mysql57-serverMessage from suricata-5.0.2_3:
--
If you want to run Suricata in IDS mode, add to /etc/rc.conf:suricata_enable="YES" suricata_interface="<if>"NOTE: Declaring suricata_interface is MANDATORY for Suricata in IDS Mode.
However, if you want to run Suricata in Inline IPS Mode in divert(4) mode,
add to /etc/rc.conf:suricata_enable="YES" suricata_divertport="8000"NOTE:
Suricata won't start in IDS mode without an interface configured.
Therefore if you omit suricata_interface from rc.conf, FreeBSD's
rc.d/suricata will automatically try to start Suricata in IPS Mode
(on divert port 8000, by default).Alternatively, if you want to run Suricata in Inline IPS Mode in high-speed
netmap(4) mode, add to /etc/rc.conf:suricata_enable="YES" suricata_netmap="YES"NOTE:
Suricata requires additional interface settings in the configuration
file to run in netmap(4) mode.RULES: Suricata IDS/IPS Engine comes without rules by default. You should
add rules by yourself and set an updating strategy. To do so, please visit:http://www.openinfosecfoundation.org/documentation/rules.html
http://www.openinfosecfoundation.org/documentation/emerging-threats.htmlYou may want to try BPF in zerocopy mode to test performance improvements:
sysctl -w net.bpf.zerocopy_enable=1Don't forget to add net.bpf.zerocopy_enable=1 to /etc/sysctl.conf
Message from barnyard2-1.13_5:
--
Read the notes in the barnyard2.conf file for how to configure
/usr/local/etc/barnyard2.conf after installation. For addtional information
see the Securixlive FAQ at http://www.securixlive.com/barnyard2/faq.php.In order to enable barnyard2 to start on boot, you must edit /etc/rc.conf
with the appropriate flags, etc. See the FreeBSD Handbook for syntax:
http://www.freebsd.org/doc/en_US.ISO8859-1/books/handbook/configtuning-rcng.htmlFor the various options available, type % barnyard2 -h after install or read
the options in the startup script - in /usr/local/etc/rc.d.Barnyard2 can process unified2 files from snort or suricata. It can also
interact with snortsam firewall rules as well as the sguil-sensor. Those
ports must be installed separately if you wish to use them.Cleaning up cache... done.
Success -
@pet1975:
Did you have a Suricata configuration on this box in the past? I'm wondering if something is corrupted inside the Suricata section of yourconfig.xmlfile.I know the package code works because I've done several installs over the last few weeks onto virtual machines as part of my testing.
Your installation appears to be failing when trying to locate and migrate an existing Suricata configuration into the new version installation. That is assuming that you had Suricata on this box at some point in the past.
I assume that you can see the package listed as being installed under SYSTEM > PACKAGE MANAGER on the Installed Packages tab, so let's try completely removing everything and installing a green field setup. Follow these steps.
-
Make a backup of your current configuration using the menu option under DIAGNOSTICS in pfSense. Save the
config.xmlfile that generates someplace on your local PC where you are accessing the pfSense GUI. -
Once you have the backup completed, open this URL in your browser. Replace the "myfirewall" part with whatever the IP address of your firewall's LAN interface is. My example uses HTTP, but if you have your GUI configured for HTTPS, then use that prefix.
http://myfirewall/suricata/suricata_global.php
-
That should open a Suricata GUI page. Scroll down to the bottom and uncheck the box to save settings when de-installing the package. Save that change.
-
You can browse around the other Suricata tabs if desired and view any existing configuration to help you reconstruct everything if the next step works.
-
Now go to SYSTEM > PACKAGE MANAGER and remove (delete) the Suricata package. This time, the option you "un-ticked" on the GLOBAL SETTINGS tab should result in all Suricata configuration information being removed from your firewall's
config.xmlfile. -
When that completes, try installing Suricata once more. This time I'm hoping it installs and shows up under the SERVICES menu. There will be no existing settings, though. Suricata will install with a blank slate.
If the steps above work, then the Suricata section of your firewall configuration has somehow gotten corrupted. You will need to reconfigure your Suricata setup from scratch.
If the steps above don't work and Suricata still does not appear under the SERVICES menu, then I am truly stumped as to what your problem could be.
-
-
thanks for helping :-)
i will try all the steps your writing here late night, and come back with the result, hopefull a succesfull one.
otherwise i make a backup config.xml and do a clean pfsense install. -
wuhuu!!
your solution worked :-)
i can now see Suricata on the service menu.
thank you very much!!! i really appreciate that -
@pet1975 said in suricata fail to launch after update:
wuhuu!!
your solution worked :-)
i can now see Suricata on the service menu.
thank you very much!!! i really appreciate thatThen that seals the deal in terms of the original root cause. Something in the <suricata> section of your
config.xmlfile was fatally corrupted and that was causing the install script to die. Installing packages on pfSense with GUI components in them is a multistep process. The entire process is under the control ofpkg, but during the installation process there is a provision for the package being installed to have some "hooks" into the process. The IDS/IPS packages (Suricata and Snort) use those hooks to do some initial setup as part of the GUI package installation. Part of that setup involves detecting an existing configuration from the previous installation and restoring or reusing it to create the new configuration. But if that previously stored configuration is invalid for some reason and the called GUI code crashes, that can cause the rest of the installation to not finish. In your case, sounds like the part that never finished was writing the final piece of the package information into the part ofconfig.xmlthat provides the entries under SERVICES in the pfSense menu. -
@pet1975:
If you are willing to share that backup of yourconfig.xmlI encouraged you to create before performing the last package deletion step, I would love to take a look into the <suricata> section to see what was causing the issue. Perhaps it is something I can write detection code for into the package and prevent future issues for someone.If you are willing to share, contact me via PM (chat) here on the forum and I can provide you an email address to send the file to. You can sanitize the portions that you feel contain confidential info.
Thanks,
Bill -
i just pm you regarding and email :-)
-
-
@pet1975 said in suricata fail to launch after update:
i just pm you regarding and email :-)
Imported your configuration into my test virtual machine and then installed the Suricata package. It failed to complete installation with the current package version posted in the pfSense packages repository (Suricata v5.0.2_3). It failed the same as it has with you previously. Nothing shows under the SERVICES menu for Suricata after the package installation.
However, installing the latest Suricata package version that I am currently testing was successful. That package version is 5.0.3, and it will be available soon for the pfSense-2.5 DEVEL branch and then a bit later for the pfSense-2.4.5 RELEASE branch.
Even better news is I found what the root problem is, and it is what I had suspected. If you have the option on the GLOBAL SETTINGS tab checked to enable download of the GeoLite2 database, but your MaxMind database license key is invalid, that download will fail. The current PHP script, when detecting that failure performs an exit() call instead of a return() call. Calling exit() in PHP terminates the currently running script. That is in turn prematurely terminating the Suricata package installation PHP script so that the remainder of the installation (putting the entry under the SERVICES menu) fails to complete. Here is the error from the system log -- (I changed the order to show the recent event first, so read the entries from the bottom up for the chronological sequence)
Jul 11 11:37:55 php 92290 [Suricata] ERROR: GeoLite2-Country IP database update check failed. The GeoIP database was not updated! Jul 11 11:37:55 php 92290 [Suricata] ALERT: The Account ID or License Key for MaxMind GeoLite2 is invalid. Jul 11 11:37:54 php 92290 [Suricata] Checking for updated MaxMind GeoLite2 IP database file...So the root cause of your issue is that your MaxMind GeoLite2 database download license key is invalid. If you fix this, then your Suricata installation will complete even with the current version. To fix this, go to this URL: https://myfirewall_ip/suricata/suricata_global.php. Replace "myfirewall_ip" with the correct value. Once on the tab, scroll down to this area --
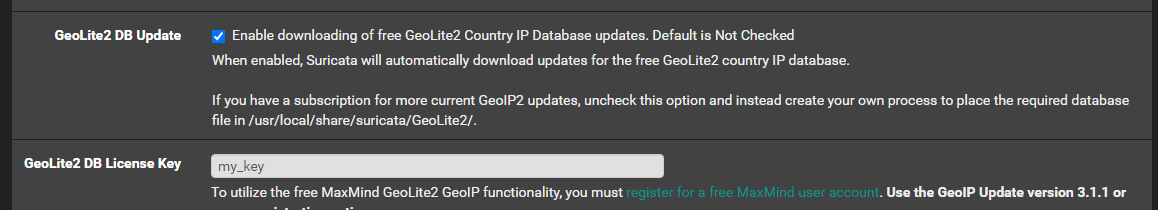
If you do not want to use GeoIP rules with Suricata, then uncheck the box for GeoLite2 DB Update. If you do want to use GeoIP rules, then you will need to enter a valid license key. The current key you will see listed is not valid. In the screenshot above, I deliberately obfuscated your key for privacy. Save the changes you make on this screen and then run the remove and reinstall Suricata sequence again. It should complete successfully and show up under the SERVICES menu.
In the upcoming 5.0.3 Suricata version I have changed the GeoLite2 database install code so that a failure to download the database does not terminate the rest of the installation script.
