How to update ClamAV
-
How to update ClamAV?
-
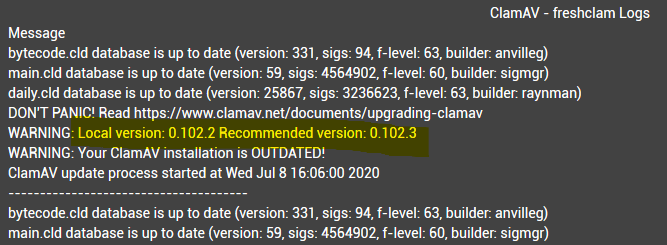
Did you read that don't panic doc? I think I remember this not being a big deal back when I used ClamAV with squid. I think it just means the pfsense package hasn't been updated. I don't think that means the definitions are outdated.
On a side note, unless you have squid doing man-in-the-middle decryption of all traffic, ClamAV is pretty useless. In my use case only ~ 1% of the web traffic was http, so only that 1% was scanned for viruses. Not very effective in my opinion so I got rid of squid and ClamAV.
-
@Raffi_ I read "don´t panic doc". The doc describes how to update/upgrade ClamAV on RedHat, CentOS, Ubuntu, macOS, Windows., but nothing about pfSense/FreeBSD.
So, after abandoning squid and ClamAV, what was your alternative?ive?
-
@hugoeyng said in How to update ClamAV:
So, after abandoning squid and ClamAV, what was your alternative?ive?
It depends on your use case. Is the primary purpose for squid to act as AV scanning on the firewall?
Don't take my word for it, check to see if squid is really doing much in your own environment. Take a look at your squid user access report. Below is an old image from when I last used it. You can see the hit rates are extremely low. The total average was less than 1%.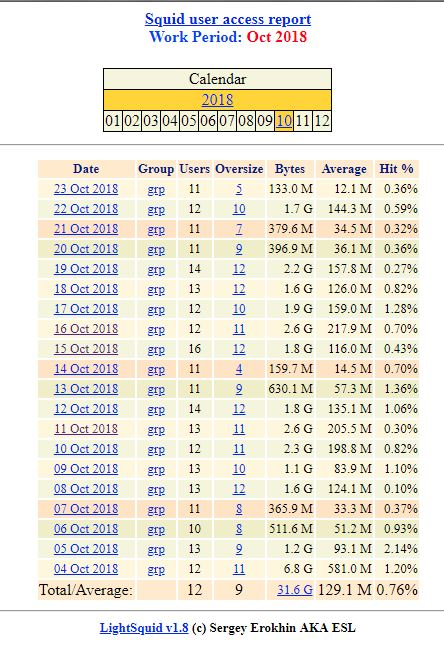
I'm finding a solution like pfblocker-NG devel to be a better option for network security. It does not do virus scanning. the approach is much different. It help prevent access to malicious sites by using maintained blacklists. It may take some fine tuning to get your blacklists right. In other words, you may have to whitelist certain sites that are being falsely flagged as bad. Take it easy with adding lists to start off. I believe squidgaurd can also be used for URL filtering, but what I last recall is that the squid package not getting nearly as much attention or upkeep, if at all. Pfblocker is very actively maintained and there is tons of information, guides, and recommended lists for pfblocker. Suricata (intrusion detection/prevention) is also another package I use for network security. Again, it is very actively maintained. It will also require some fine tuning to avoid false positives and legitimate sites being blocked. There is a learning curve especially with suricata, but the devs of both suricata and pfblocker usually answer questions right on these forums very quickly. If you haven't already, I would say try starting with pfblocker first, then later with suricata. Do them one at a time and don't dive into both right away, because if you start getting a lot of false positives, you will have a difficult time tracking down which tool is blocking the site. In my experience, the majority of my false positives came from suricata. It took me months before I got it fine tuned to a point of very few false positives.
-
You shouldn't abandon ClamAV for this message.
Most servers, available on the Internet, that use ClamAV, has this line it it'log. I have it all my servers.I do NOT want to have the latest package release, I want to have the stable one.
@hugoeyng said in How to update ClamAV:
what was your alternative?ive?
With your router handling 99,99 %% TLS encoded traffic ?
No alternative.
It' all "private data" etc these days. No one sniffs through other person's chat's and mails any more.
Today, network protection can not be centralized on one place (firewall) any more. "Internet users", like "car users", "TV users", etc should follow some sort of 'eduction' about how to use it up front. You can't do more.Virus scanning etc is still useful today for mail protection : all mail comes in on port 25 - TLS encrypted of course, but it winds up in a mail box, using clear text: just a folder with mail files. These files can be scanned, enclosed files like ZIP can be opened and scanned.
edit I agree with @Raffi_ : squid - and other comparable tools, are things of the past.
-
@Gertjan said in How to update ClamAV:
Virus scanning etc is still useful today for mail protection : all mail comes in on port 25 - TLS encrypted of course, but it winds up in a mail box, using clear text: just a folder with mail files. These files can be scanned, enclosed files like ZIP can be opened and scanned.
@Gertjan Interesting point on the email scanning. Didn't think that was the case, but that makes sense.
@hugoeyng As I said, check to see the squid usage in your own case. Supplementing it with the other tools mentioned is a good idea if you're not already doing so.
edit: agree with @Gertjan on educating web users too. You try to do all that you can to help prevent them from going to the wrong site or clicking on the wrong link, but they should know what to look out for. We all have that person that no matter how many times you tell them not to click on the link in the email, how can they resist saving 1000% on their insurance bill.
-
@Raffi_ said in How to update ClamAV:
how can they resist saving 1000% on their insurance bill.
The rich African widow is back. She has 45 kilo of gold just for you, but to finalize the transfer she needs your credit card number.
This still works today.https://www.youtube.com/watch?v=_QdPW8JrYzQ& ( clean the floor first, you'll be rolling there in 15 second s)
-
hahaha the list goes on with these.
Edit: On a more serious note though, the most effective solution I have found for preventing security issues has been on our email server side. We are small company using Office 365 and after a few incidents we had, we opted for the advanced threat protection . That is the best money we spent. I have to say Microsoft is doing a great job of preventing incidents for us. Email is our biggest risk and they have nearly taken all the risk out since all attachments and links are scanned on the server side before it reaches the end user. Since enabling ATP we have not had a single incident with emails. We still get occasional spoofed emails, but I'm not as worried about that since our users are fully aware of what to look out for and to verbally confirm with anyone before wiring money. Sorry for sounding like an advertisement, but this is a true testimony. Key point I'm trying to make here is the email server side is what should really be beefed up if it isn't.
-
@Raffi_ I understood.
In my case, the use is a little bit higher.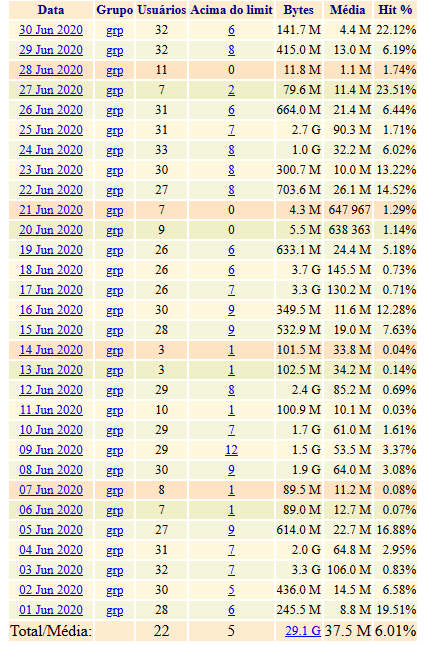
-
@hugoeyng said in How to update ClamAV:
In my case, the use is a little bit higher.
Interesting, yes that does look much more useful than I found. In that case, keep squid and ClamAV definitions up to date which you are already doing. Even in your case it is on average 6% effective, although you do have days it is above 20%. That's surprising. You may still want to consider supplementing squid/ClamAV if you aren't already.
I think @Gertjan made a very good point on that warning message and I agree.
Most servers, available on the Internet, that use ClamAV, has this line it it'log. I have it all my servers.
I do NOT want to have the latest package release, I want to have the stable one.So to be clear, I'm going to repeat that the warning message is nothing to worry about.
-
-
@hugoeyng said in How to update ClamAV:
@Raffi_ Thank you for answering.
@Gertjan I agree with your point: better is to have de stable version. But inyhe
future the stable version will be the 0.102.3. The question is: will the clamav be updated by then?(Virus definition database is updated).
You can do this manually via pkg:
pkg add -f http://pkg.freebsd.org/freebsd:11:x86:64/latest/All/json-c-0.14.txz pkg add -f http://pkg.freebsd.org/freebsd:11:x86:64/latest/All/clamav-0.102.3,2.txzNothing to worry about, doing this for years now, worst thing that could happen is that ClamAV gets downgraded on a pfSense update again.
You can even install your own build of ClamAV, like I do which has the threaded reload patch backported to clamav-0.102.3,2:
https://github.com/Cisco-Talos/clamav-devel/pull/126
-
@Bismarck Worked!
-
I use ssl intercept and it does scan https traffic. With protocols like doh, dns over https, pfblocking is just wackamole. Squid a pain to configure with ssl intercept but it works great once it is configured. ClamAV is a pain when it updates, it hogs resources. So I use cron and it updates in the early hours