VLAN configuration problem
-
Hello,
I have created a virtual machine on a Proxmox server.
on the pfsense, I created 2 VLANs and put a VM on each VM.The problem is that vlan can communicate with each other, even if I add a rule that blocks all traffic on a vlan interface.
Anyone know where the problem comes from?
-
Can you post a screenshot of your VLAN rules?
-
Hello,
-
@mourad13 First thing I can see from your screenshot of OPT20 rules is that you don't have your Source field filled in. In that rule, the Source should really be set to "OPT20 net". And do you mean for it to be a Block rule instead of a Pass rule?
The OPT10 rule is set for only IPv4. So, if that VM on OPT1 is talking IPv6, I don't think any traffic will leave the OPT1 network.
Jeff
-
I made the change, but the vlan10 can still ping the vlan 20.
I tried with OPT10.net as well.Moreover, it seems to me that by default, pfsense blocks all traffic. Shouldn't I have to put a rule to isolate a vlan?
-
@mourad13 Ok, so now, on OPT20, with the change to the rule, the entire OPT20 network is blocked from going to any other destination.
What is it exactly that you are trying to do - block the VLANs from talking to each other, block them from getting to the internet, allow them to go anywhere on your network, allow only 1 to access the other, what?
Jeff
-
Indeed, the vlan20 no longer communicates with the outside.
On the other hand, the vlan10 can still communicate with the VLAN20.If I want to block it, I have to write a rule on OPT10 with source = opt10.net and destination = OPT20.net?
-
@mourad13 Yes, a block rule on OPT10 with source = OPT10net, destination = OPT20net will completely block OPT10net from talking to OPT20net. This rule will not, however, block OPT20net from talking to OPT10net, if a machine on OPT20net initiates the traffic to OPT10net.
Again, what is it exactly that you are trying to do?
Jeff
-
Thank you for your explanation.
I would like only the necessary ports to communicate between the vlans.
For example, between vlan10 (Prod with web server) and vlan30 (database vlan), only port 3306 can communicate. -
Ok then, on your OPT10 interface (that's what you mean by VLAN10, right?), you would make a pass rule for a specific IP address, your web server address, to the specific IP address of the database server on the VLAN30, using ONLY port 3306. You might have to do the same on VLAN30 to VLAN10, but I'm not too sure.
Then, make a second rule to block everything else from VLAN10 to VLAN30. See this screenshot, I'm assuming your web server = 172.16.10.10 and your database server = 172.16.30.10:
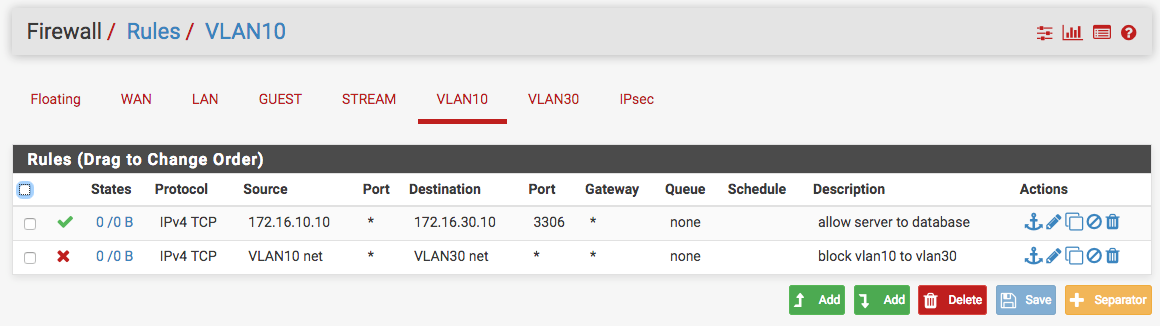
If your gateway settings are the same on both of the vlans, this should all work just fine.
Jeff
-
Perfect, with that, I was able to move forward and better understand the vlan under Pfsense.
Thank you so much.
-
@mourad13 You're welcome, no problem!

