Verizon Fios and IPV6, Which Settings Work?
-
@sirsilentbob can you share your WAN configuration? that allows for this? I have a deployment in Chesapeake and have DHCPv6-PD configured for a /56 prefix but I am not seeing anything.
-
@jeremy-duncan it should be noted that Verizon’s rollout of IPv6 is very limited at this point. They’ve only recently expanded it in parts of Maryland and Virginia, and the rollout is on a CO-by-CO basis. They seemed to pick a few CO’s around Baltimore and a couple in Newport News/Hampton area as their current wave. I think it’s a test of expansion, and we’ll see further ramping up of things in coming weeks. The current expansion happened about two weeks ago now, and there didn’t seem to be anything new last week so they may be just looking at things to make sure everything’s working properly before moving forward again.
-
@mikev7896 I will try to remember to do that soon!
-
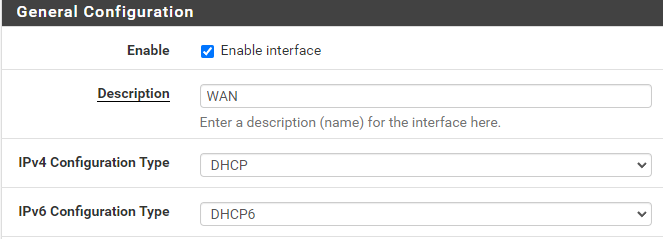
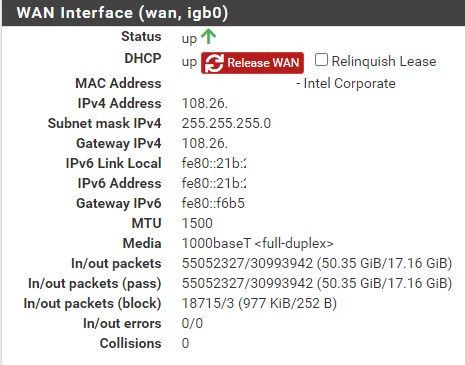
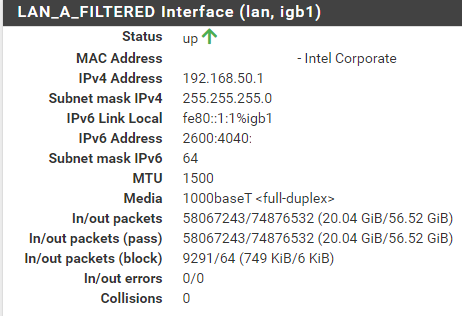
@jeremy-duncan Sure! Basically exactly what Mike shared, let me know if there is anything else more specific you need (photos). I am honestly not fully understanding why the WAN interface is getting an IPv6 "link local" address (FE80) but the actual address is showing on the LAN interface. I have had an interest in IPv6 for probably 10, 12-ish years, and it just looked so... intimidating that I didn't start looking into and messing with it till now. Still much to learn, I am sure.
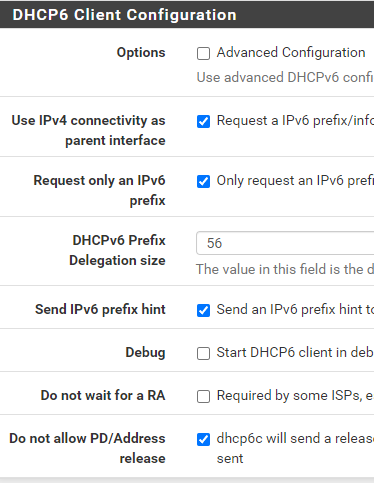
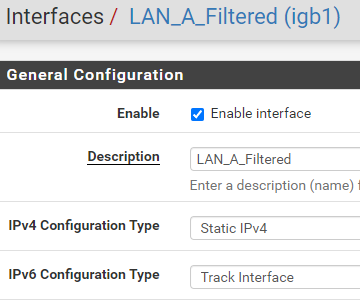
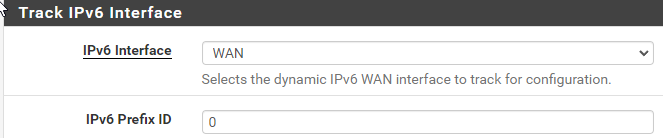
@MikeV7896 A weird thing I had happen since I got this working, I attempted to duplicate the IPv6 settings on additional LANs, not just my primary one, except of course under "Track IPv6 Interface" I put a different IPv6 prefix ID. My primary I used 0, on two more I used 1 and 2. Doing that, I appeared to get IPv6 IPs on those additional LAN segments, but I lost all IPv6 connectivity and everything fell back to IPv4. I saved my config files of course, and just rolled back to how it was with just one LAN configured for IPv6 and then IPv6 began working again. I would expect that there's plenty of IPv6 IPs to provide to other LAN segments, but something escapes me on that. I'm good with just the one LAN having IPv6, but I had hoped that I could allow my RIPE Atlas Probe (which is on an un-filtered network, it needs unrestricted internet access for the measurements it does) to get IPv6 access. Maybe some other time I can try to figure out why other lans kills all IPv6.

-
@MikeV7896 I've submitted as detailed info to you as I can over at DSLR. (I think it needed mod approval) I've done some searching on the subject of taking an isp /56 and being able to put a /64 on each LAN segment. There's tons of reddit posts on it, and like 1 or two here on the Netgate forums. Tracking interface to WAN on each LAN and changing the prefix ID does indeed seem to be the way to do it, but I am seeing posts from a lot of others who are having the same issue, where it just doesn't work, and no resolution. I DID notice that if I check Advanced Configuration that there is a prefix interface drop-down, and only a single LAN is selectable. Maybe only one LAN can get the prefix delegation? Idk, I'll dig into this more I guess.
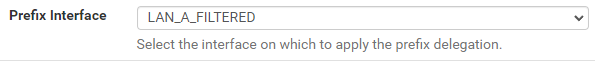
I don't think this is an issue that is specific to Verizon FIOS, as I see many others failing to take a isp /56 and cut it down to multiple /64's on multiple LANs. So, I'll just settle with moving my Atlas Probe that you noticed show up near City Center on the map off it's own LAN onto the one which is getting IPv6 without issues.
@jeremy-duncan Have you had success with your Chesapeake FIOS deployment, or is it still just a tiny bit out of reach of IPv6 for the moment?
-
@sirsilentbob Just wanted to note that I've had no problem taking my /56 and dividing into multiple /64's... I have addresses from four different /64's in use on my pfSense box... my primary LAN, a "test" LAN for a WiFi mesh product I've been testing, an "ATLAS" network for just my probe, and a virtual IP for my WAN interface, and all are working without issue. I don't allow much communication between the networks, (primary LAN can get to everything else, but test and atlas can't get to anything but internet) but everything is working fine on all three, both IPv4 and IPv6.
I'll try and grab some screenshots of my settings over the weekend, but it sounds like your settings are right, so not sure why it would work on one but not others.
-
@sirsilentbob i'm still waiting to see some IPv6 router advertisements or them to respond to my DHCPv6 solicits. Either way, my IPv6 is limited to a hurricane electric tunnel until then...
-
@jeremy-duncan
Router advertisements should happen frequently. Take a packet capture of the DHCPv6 sequence.
To do that:
Shutdown pfsense and unplug WAN cable.
Reboot pfsense and start Packet Capture, filtering on DHCPv6.
Reconnect WAN cable.
After a couple of minutes, download packet capture and examine with Wireshark. -
@jknott way ahead of you i am doing a tcpdump on the external interface... bupkiss. just my DHCPv6 solicits
tcpdump -ni lagg0_vlan2 ip6
tcpdump: verbose output suppressed, use -v or -vv for full protocol decode
listening on lagg0_vlan2, link-type EN10MB (Ethernet), capture size 262144 bytes16:11:02.856512 IP6 fe80::eef4:bbff:fed3:a3e8.546 > ff02::1:2.547: dhcp6 solicit
16:11:59.768654 IP6 fe80::eef4:bbff:fec1:d2e8.546 > ff02::1:2.547: dhcp6 solicit
16:13:14.636935 IP6 fe80::eef4:bbff:fed3:a3e8.546 > ff02::1:2.547: dhcp6 solicit
16:14:02.094810 IP6 fe80::eef4:bbff:fec1:d2e8.546 > ff02::1:2.547: dhcp6 solicit -
@jknott i also force router solicitations..
16:17:57.834172 IP6 fe80::eef4:bbff:fed3:a3e8 > ff02::2: ICMP6, router solicitation, length 16
16:18:01.846522 IP6 fe80::eef4:bbff:fed3:a3e8 > ff02::2: ICMP6, router solicitation, length 16
16:18:05.848481 IP6 fe80::eef4:bbff:fed3:a3e8 > ff02::2: ICMP6, router solicitation, length 16 -
@jeremy-duncan Guessing it's just not on in Chesapeake yet then... the only reports from other DSLR users have been Newport News and Yorktown so far... nothing from Norfolk/Chesapeake/VA Beach.
-
@mikev7896 understood thanks
-
@MikeV7896 Thank you! I'd greatly appreciate it. From what you are saying, it sounds like you are maybe using an on-board NIC for one of your connections and you have four LANs, maybe with a four-port NIC? I am using a 4-port intel gigabit card, and disabled my on-board NIC so I've just got 1 WAN and three LANs. But I'm looking to do a similar setup, a primary lan, a "spare/experimentation" lan and a Atlas Probe lan.
@jeremy-duncan Sorry it isn't working yet for you. Maybe once Verizon finishes up with rolling it out in Newport News & Hampton then they'll migrate over to the southside and start deploying it there...
-
My pfSense box has a SuperMicro motherboard with five onboard NICs... one is OS-accessible but is also shared with the built-in out-of-band management firmware (which I don't use and have disabled in the BIOS), the other four are all dedicated Intel Gigabit NICs. One WAN, 3 LAN. Main LAN connects to a switch for everything else, LAN2 connects to the mesh router, and ATLAS connects directly to the device my Atlas probe is running on.
Our WAN settings vary a little, but I don't think the variances are significant to where your LANs would be affected.
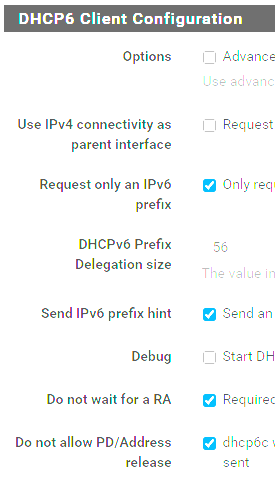
LAN settings, well... there's not much there. I will admit that I'm not using prefix 0 though... LAN = 10, LAN2 = 20, ATLAS = 50...
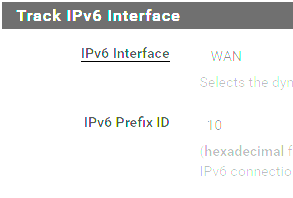
I did look at the advanced DHCP6 config on my WAN interface (since I didn't see any advanced options on my LANs) and I did see this...
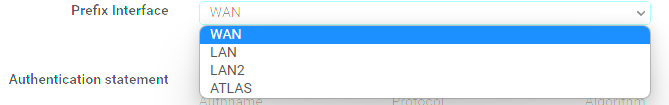
Though I don't have advanced configuration checked normally, and none of the other options in that section are enabled or filled out. WAN was selected by default. -
@mikev7896 Hmm, thanks for sharing. Your drop-down prefix interface being set to WAN is quite interesting to me, I'll try duplicating that! I'll try changing some things when everyone is asleep and won't miss the internet. Also I'll try changing the LAN prefixes from single digit (0, 1 & 2) to double digit ones too.
Could you share how you have your Router Advertisements / Router Mode set, if you get a chance, please? Just wondering if that is a hang-up.
Thanks again!
-
@sirsilentbob My RA router mode setting is Unmanaged. I let SLAAC and RDNSS do its thing, and I've had no issues with any device.
-
@jeremy-duncan
Do they even support IPv6?
-
It doesn't matter which prefix ID you use, so long as they're unique for each interface. I don't use advanced IPv6 settings.
-
@jknott they’re beginning to roll it out on a larger scale. Over the past couple of weeks, reports of IPv6 now being available have come in from five areas near Baltimore MD and three in VA. A business account in NY (don’t remember where in the state) received an email that it should be rolling out up there in June.
-
@MikeV7896 Thanks for your gracious help and sharing of config info.
Unfortunately I guess at this time I think all I can do is go back to my "wrong" configuration that is only allowing IPv6 on a single LAN. I've pretty much duplicated your setup exactly, but it isn't working, WAN_DHCP6 just stays in a Pending state. I checked the box to start DHCP6 client in debug mode, the only "hint" I have is this below log entry, and a search on that missing dhcp6cctlkey file has been fruitless, and even found posts saying that error is unimportant. It must have some sort of importance though, because my config that gives a single LAN IPv6 (when the prefix interface is set to that LAN and not WAN) does not generate that error. I'm just not sure why I can't get it to work on all LAN interfaces.
May 14 13:30:57 dhcp6c 29013 skip opening control port May 14 13:30:57 dhcp6c 29013 failed initialize control message authentication May 14 13:30:57 dhcp6c 29013 failed to open /usr/local/etc/dhcp6cctlkey: No such file or directoryIf anyone has any thoughts or things to try, I am open to suggestions...
Edit: Something else I am seeing, the Service Status for RADVD disappears from the dashboard too but according to the command line it is still running? I have a backup I can roll back to though that should get me back to a single LAN with IPv6. Just changing the settings back doesn't restore connectivity, so something is sticking somewhere... I might save another config file to compare differences between files and then restore to the working single-lan config.