Unable to watch specific streaming video content
-
Hi there,
I am trying to watch some online training videos from a given content provider (via O'Reilly / Pearson training), using my home workstation which is behind my pfSense device. The pages include an embedded video player which attempts to load the video then times out with a long message related to "network error" as per below. Unfortunately I can't copy/paste the text or expand the window to get the full message.
Error:
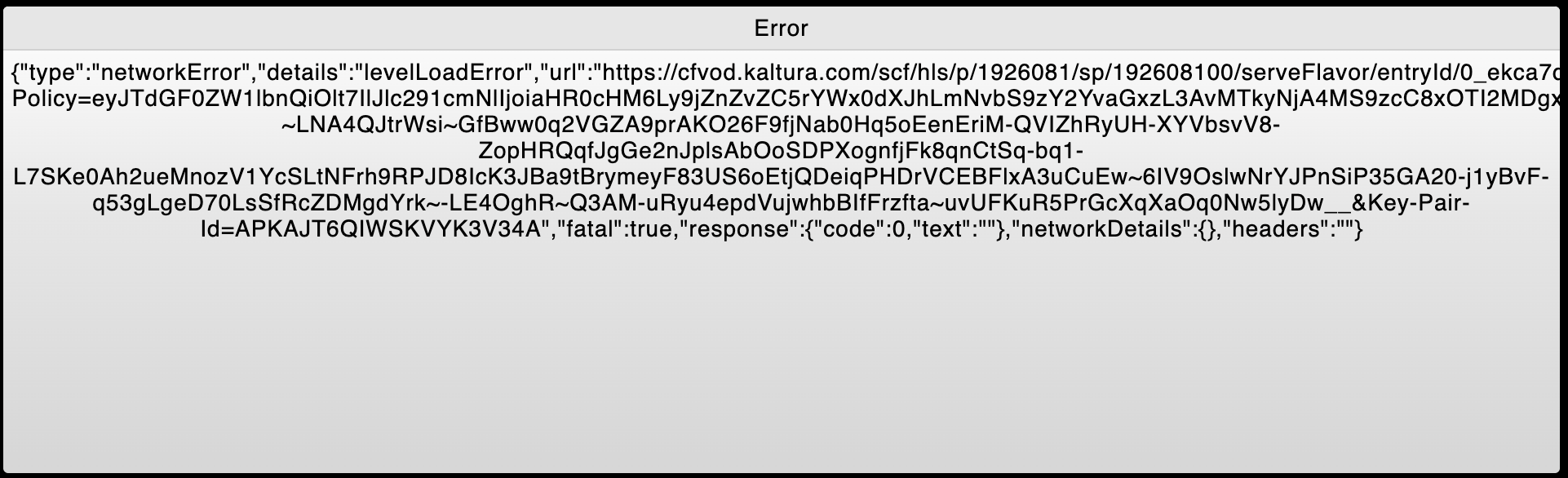
I am able to access the same videos from two other networks, namely internal work network and over LTE. This is what leads me to believe that pfSense could be the problem.
I have been running pfBlockerNG, squid proxy server, snort and ClamAV. I've disabled them all and I still get the same issue.
I'm really not sure how to diagnose the issue from here. I don't know what IPs/traffic is being involved in this video player so I struggling to find if anything is getting blocked in the firewall.
I don't have any problems with any other sites/videos, just this one. I don't recognise the player.
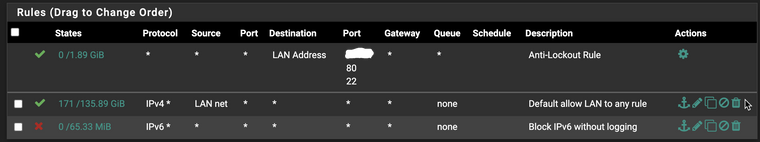
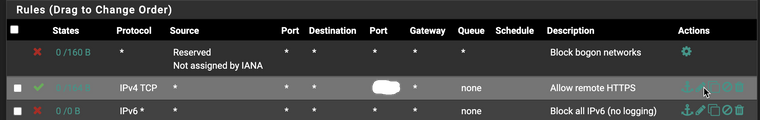
I believe my firewall rules are very simple, not much different from the default install.
LAN rules:
WAN rules:
Please can someone help me to diagnose this further? I have seen other threads related to streaming issues (for the likes of Netflix/Amazon prime), but none of the discussion/solutions seem to apply.
-
Does your workstation think it should be able to use IPv6?
;cfvod.kaltura.com. IN AAAA ;; ANSWER SECTION: cfvod.kaltura.com. 7200 IN CNAME d2xproa6koigec.cloudfront.net. d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:4600:19:597a:e108:c5a1 d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:7800:19:597a:e108:c5a1 d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:ce00:19:597a:e108:c5a1 d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:f800:19:597a:e108:c5a1 d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:da00:19:597a:e108:c5a1 d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:8a00:19:597a:e108:c5a1 d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:b600:19:597a:e108:c5a1 d2xproa6koigec.cloudfront.net. 60 IN AAAA 2600:9000:211d:1400:19:597a:e108:c5a1 -
@Derelict Um, I'm not sure how to answer that! If you are suggesting that it needs to allow IP v6, could you help me to set that up?
I just tried disabling those IP v6 related rules, still didn't enable the video.
I then created a LAN rule to mirror the allow LAN to any rule, changing the protocol to IPv6. Still didn't help.
-
Hard to say. I'm just imparting that if your host thinks it has IPv6 connectivity but really doesn't, it could try to connect that way.
Not sure why you would specifically block IPv6 if you don't know whether your hosts have it or not.
Does Status > Interfaces show IPv6 addresses?
-
@Derelict No, it doesn't have IPv6 in the interfaces status. btw. I had originally put in those rules to try to block the significant number of log messages related to IPv6 (which I believed I didn't need).
Any other ideas?
-
Simply disabling (or shutting down) the Snort service does not necessarily remove any IP blocks it inserted. Go to the BLOCKS tab in Snort and clear any IP addresses shown there -- or you can go to DIAGNOSTICS > TABLES, select the snort2c table in the drop-down selector, and clear its contents.
Do you have pfBlocker configured with the DNSBL option? If so, your DNS may have some leftover "residuals" from that setup the are adversely impacting you.
Anytime you are running packages on pfSense, and something either does not work, or stops working, the packages should be assumed as primary suspect. Disabling them is proper, as you have done, but you need to make sure they are all truly disabled for now AND that no residual after effects of the packages' operation remains. That last part is going to be the toughest to verify.
-
@bmeeks Thanks for the suggestions. I've cleared the snort2c table as suggested, and deleted all blocks/alerts that I can find everywhere. Short of uninstalling all the packages (which I only want to do as a last resort) I can't think of anything else to make it cleaner.
However, I may have found something... I enabled "content inspecting on the page". I can get the pages/videos to work if I turn on my VPN. When I am not using the VPN, I get loads of these messages in the browser console which I don't get when it is working.
Access to XMLHttpRequest at 'https://cfvod.kaltura.com/scf/hls/p/1926081/sp/192608100/serveFlavor/entryId/0_ekca7d8w/v/2/ev/14/flavorId/0_35o9cu1n/name/a.mp4/index.m3u8?Policy=eyJTdGF0ZW1lbnQiOlt7IlJlc291cmNlIjoiaHR0cHM6Ly9jZnZvZC5rYWx0dXJhLmNvbS9zY2YvaGxzL3AvMTkyNjA4MS9zcC8xOTI2MDgxMDAvc2VydmVGbGF2b3IvZW50cnlJZC8wX2VrY2E3ZDh3L3YvMi9ldi8xNCoiLCJDb25kaXRpb24iOnsiRGF0ZUxlc3NUaGFuIjp7IkFXUzpFcG9jaFRpbWUiOjE1OTYxMjM3MDB9fX1dfQ__&Signature=BpjlG9BPt3PeG7Xt5QsfrRfGKe65NdpjZnjiDZOFxt~Fdzvd4edF4UXkp4ydyqmogTbQhBjH5C9FhLRccl32OqFZVabOQGtleCgav5sA7uI5jTGdGGpuWTNmUNWqivmu8pwBpN35JumGqAsZDbRu8sY3WmcKgN4c7TiEXelvMKXftW~T9pil4s0Z1YvzIspb7ySSe63YsT7kV5p0~3zWccHo2XB2n87W0WucMfR-tEYs4YPsFxoPObfIw3-ELYyAxBAkCqX4IhzmKOHlpEnTivGWMTQyy8IyQd-ydOT38RTevNt4rJi6iB6D0zkG8q5Hk6vB-HOzM79NmS5HpfRM~Q__&Key-Pair-Id=APKAJT6QIWSKVYK3V34A' from origin 'https://learning.oreilly.com' has been blocked by CORS policy: No 'Access-Control-Allow-Origin' header is present on the requested resource.A quick search and it seems that CORS (Cross Origin Requests) is some sort of security feature to stop sites from using other domains that they are not (forgive me if that is not the exact explanation). This makes sense, because this video is essentially embedded in one site which is embedded in another.
I've also checked that this is not a problem with the video player itself; not only does it work from the site when the VPN is active, but I went to the original content provider's website, and the video player's website, and successfully tested videos from there.
So perhaps something is going on here which is not enabling CORS... using my VPN, my work network, or my mobile network, gets around this. Going through my home network through pfSense does not.
Anyone know of CORS and if pfSense has anything to do with it?
-
If you have not enabled squid I cannot see that the firewall has anything to do with what you are seeing.
-
I agree with @Derelict. pfSense itself has no Layer 7 DPI capability. This sounds like perhaps a browser issue or could also be a web server configuration issue on the remote end. Is strange it works on VPN and elsewhere, but one explanation might be a change in the browser used (or the browser's configuration).
-
Thanks for the responses. I'm at a loss as to how this is happening, very strange.
@Derelict btw. I was using squid (but disabled it, no difference, cleared cache, no difference)
I've emailed the provider's customer support but I doubt they are going to be able to help me on this one as it seems to be a very specific and localised issue :-(.
-
What you are describing really sounds like something that squid might break. What other packages have you installed that could be disabled for testing?
-
@Derelict Here's my service list. Note that I haven't enabled suricata so it can be ignored.
So far I've tried disabling the below with no luck (individually and all at once):
c-icap
clamd
lightsquid_w(
pfb_dnsbl
pfb_filter
snort
squidI could actually uninstall squid without too much drama so maybe I'll try that, perhaps it still lurks around even when disabled.
Edit: Complete uninstall of squid doesn't solve it :-(.
-
You could:
Backup your configuration.
Reset to defaults.
Get basic internet working.
See if the issue still happens.If not then you need to figure out what you did there that broke it.
Personally, I think this stuff is hard enough to make work reliably without throwing up roadblocks everywhere. There are some specific needs for things like IDS/IPS in certain environments and people like to block ads, etc, but you almost always get false positives too.
-
@Derelict Thanks a lot. I actually have a new device on order [with more ports], so I'll take the opportunity to try out a barebones install when that arrives. In the meantime, I can live with this as I have a sub-optimal workaround of using my VPN, unless anyone else has any suggestions of how to further diagnose.
-
This post is deleted!