Youtube cast across VLANs
-
I know I'm missing something and my fellow pfSensers will help me figure it out.
I have seen and read several others topics discussing how to cast (mostly chromecast) across subnets and VLANs using Avahi. I followed videos and advice in some posts but have not had luck yet. I don't know if casting from the Youtube app is the same or similar to chromecast? But in any case, it doesn't work for me.
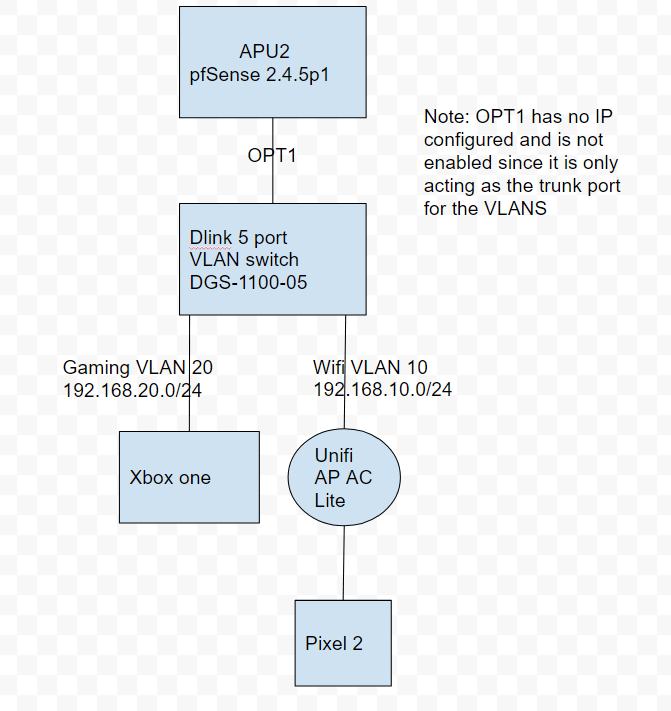
Here is my setup at home which is working perfectly, except for being able to cast youtube videos from my Pixel 2 to my Xbox one in a different VLAN. As a sanity check, it works when I put my unifi on the gaming VLAN, same layer 2 (of course).
The packages I have,
backup
cron
ntopng
pfblockerDuring my testing here is what I have done so far with no success...
- Enabled Avahi with reflection on both VLAN interfaces.
- Disabled all my block rules on floating tab which I normally use to prevent subnets from talking to each other.
- Placed any<->any rules at the top of both Gaming and Wifi VLANs to ensure no ports are being blocked.
- Disabled pfblocker and forced reload to be sure it was not somehow causing problems.
- IGMP snooping is disabled on the Dlink switch. It is disabled by default. From my understanding, IGMP snooping could be useful for really big networks for saving bandwidth and preventing DOS attacks. I'm not worried about either on my tiny network at home so I left it alone.
Is Avahi even the right tool for the job? Should I instead be using IGMP proxy? Or both Avahi and IGMP proxy? Or something else entirely?
I do see mdns and ssdp traffic when I perform a capture on the VLAN interfaces, but when I tried to compare mdns/ssdp traffic in the working scenario vs broken scenario, I don't see anything that looks obviously different. I admittedly don't really know what to look for either, so that is one issue.Any guidance would be appreciated.
Thank you,
Raffi -
You might not like this advice... But I am not a fan of breaking any sort of L2 boundary for discovery, etc.
As a simple solution to this problem, why would you not just create a ssid on your gaming vlan.. And when you want to cast something from your phone to your xbox - just click you phone over to that ssid?
This is way simpler solution.. And now your not broadcasting discovery multicast into other L2 networks.
If I can train my wife to click over to specific ssid to print via airprint, I am sure you could figure out how to change your wifi network to cast to your xbox ;)
-
@johnpoz said in Youtube cast across VLANs:
You might not like this advice... But I am not a fan of breaking any sort of L2 boundary for discovery, etc.
As a simple solution to this problem, why would you not just create a ssid on your gaming vlan.. And when you want to cast something from your phone to your xbox - just click you phone over to that ssid?
This is way simpler solution.. And now your not broadcasting discovery multicast into other L2 networks.
If I can train my wife to click over to specific ssid to print via airprint, I am sure you could figure out how to change your wifi network to cast to your xbox ;)
Thanks @johnpoz. I knew you were going to suggest that :)
I read your other posts on similar topics. I actually might end up doing that. My only worry is not remembering to switch back to the other ssid when I'm done casting. It wouldn't be a big deal, but the gaming VLAN does have UPNP so I don't want anything on there unless it is absolutely necessary. The other solution I was thinking of was to get a remote with a qwerty keyboard for my xbox so I wouldn't need to bother with casting at all :) I'm not a fan of searching Youtube with an xbox control. -
Your UPnP should be restricted to your xbox IP for sure anyway, or any other IPs that might be needing UPnP. So even if your other device - which would be what, your phone? was on there it wouldn't be able to use UPnP anyway.
Out of curiosity.. Since I don't get the point of it - what do people watch on youtube that they would want to cast to a big screen in the first place? If your using youtube TV, wouldn't you want to use the device's control... I would think using your phone to try and control your xbox and cast to it would be a horrible solution to be honest..
Another solution would be to just get say a roku, or a apple tv, or etc... To do your streaming with... Then just use their remote to control whatever you doing.
Breaking L2 boundaries isn't really a solution for anything.. You broke the devices into their own L2 for a reason.. But now you want to forget that security and break the boundary you put in place ;) Might well just go back to single L2 to be honest.
-
@johnpoz said in Youtube cast across VLANs:
Your UPnP should be restricted to your xbox IP for sure anyway
How would I restrict UPNP?
I followed @DaddyGo guide for my xbox and ps4.
https://forum.netgate.com/topic/153514/nat-issues-when-playing-games-on-two-computers/10
Are the static NAT entries restricting UPNP?
Also for the sake of not having to worry about ports I have the any<->any rule on the Gaming VLAN. Not the most secure so I figured I would segment it.@johnpoz said in Youtube cast across VLANs:
Out of curiosity.. Since I don't get the point of it - what do people watch on youtube that they would want to cast to a big screen in the first place?
I don't NEED this to work. I really don't use casting much, but it would be nice and this is more of a learning process for me than anything else.
-
@Raffi_ said in Youtube cast across VLANs:
How would I restrict UPNP?
You could do it via firewall rules allowing only specific IP to talk that port to pfsense, or you would restrict it in the UPnP setup as well.
What you should be learning is breaking L2 boundaries breaks security, and like pretty much anything designed to make it easier for the user security suffers..
To use L2 discovery, you really should be on that L2.. If your not - then what is the reason for the discovery, or what is the point of the segmentation in the first place.
Yeah companies take short cuts to make shit easy for the user, but then again they are also lowering security.. Sorry while UPnP can make it easy for the user - its not a good idea from a security point of view at all. Same with one big flat network where user can just broadcast and discovery anything.. Not a good idea for many different reasons.
Why can they not just say hey to use X you need to be able to talk to its IP on port X.. So open that on your firewall, and put in our client or have the fqdn you want to use resolve to that iP, etc. Now all this discovery is not needed, or doesn't have to work to use their product, etc.
-
@johnpoz said in Youtube cast across VLANs:
You could do it via firewall rules allowing only specific IP to talk that port to pfsense, or you would restrict it in the UPnP setup as well.
Thanks for the tip, I didn't know you could do that. My solution to restricting UPNP was by only putting my gaming consoles on that segment. Every now and then there seems to be an article pointing out issues with devices using UPNP or CVE related to it. Because of its inherent nature of being insecure, I thought it was best to completely isolate any devices like gaming consoles which basically require UPNP.
What you should be learning is breaking L2 boundaries breaks security, and like pretty much anything designed to make it easier for the user security suffers..
To use L2 discovery, you really should be on that L2.. If your not - then what is the reason for the discovery, or what is the point of the segmentation in the first place.Agreed, easier for the user usually makes it less secure and vice versa.
Due to my limited knowledge,
- I did not know you can limit UPNP to specific devices on a segment.
- Because I didn't know #1, I assumed allowing multicast across segments is not as big a risk as allowing trusted devices on the same layer 2 with UPNP enabled. That logic could be wrong as well since I have very limited knowledge on both topics.
So even with this new information, I don't think I'll bother with casting. If one day I decide I really need it, I'll look into a remote for my xbox with a small qwerty keyboard. I hardly ever use casting anyway. Actually, now that I think about it, maybe I could even use voice commands on my xbox to search on youtube rather than trying to type with the xbox control. I have to see if that's possible.
Yeah companies take shortcuts to make shit easy for the user, but then again they are also lowering security.. Sorry while UPnP can make it easy for the user - its not a good idea from a security point of view at all. Same with one big flat network where user can just broadcast and discovery anything.. Not a good idea for many different reasons.
Why can they not just say hey to use X you need to be able to talk to its IP on port X.. So open that on your firewall, and put in our client or have the fqdn you want to use resolve to that iP, etc. Now all this discovery is not needed, or doesn't have to work to use their product, etc.I agree with you on this too. I don't agree with the use of UPNP, but I didn't designed the gaming console, I just want to play games sometimes :)
-
To be honest when my son's were here - this was many years ago and they had a PS.. They never complained that x didn't work.. And I had no UPnP enabled or any port forwards. So have you tried just turning off UPnP - what doesn't work? The only time you would need that is hosting a game..
But sure you can lock down UPnP either by preventing access to the port UPnP is listening on talking to pfsense IP.. Or just in the UPnP setup you can limit what source IP can make requests, and what it can make requests for.. Normally limit it to its own IP as good practice.
-
@johnpoz said in Youtube cast across VLANs:
To be honest when my son's were here - this was many years ago and they had a PS.. They never complained that x didn't work.. And I had no UPnP enabled or any port forwards. So have you tried just turning off UPnP - what doesn't work? The only time you would need that is hosting a game..
But sure you can lock down UPnP either by preventing access to the port UPnP is listening on talking to pfsense IP.. Or just in the UPnP setup you can limit what source IP can make requests, and what it can make requests for.. Normally limit it to its own IP as good practice.
At first I didn't have UPNP enabled and my xbox seemed to be working OK online. I only had one odd issue which my friend said he got a message saying I just came online, but that was about 20 minutes after we were already in a chat party so clearly I was already online. I didn't have any other issues, but when I tested the network connection, the xbox would complain about my NAT type being strict and not having UPNP enabled so it may cause issues. I think it may only be needed for specific games, but I didn't want to have to deal with issues later so I enabled UPNP and created the static NAT entry for the ps4 and xbox. That solved those NAT type issues with both consoles.
I will look further into restricting UPNP as you mention if I do decide to put all my devices on the same layer 2. For now, I think I'll leave it as is. I can't get past my distrust of UPNP (usually plagued & problematic?). I'm afraid I would read a headline tomorrow about a UPNP CVE that is able to bypass restrictions :)
-
@Raffi_ said in Youtube cast across VLANs:
UPNP as you mention if I do decide to put all my devices on the same layer 2.
UPnP is always dangerous... @Raffi_
(an enemy of any firewall and/or router)
but if handled well, it is indispensable for the gamemy son is an active PS4 player...
(only when he study, he don't....)his buddies taught he to speak english (very well) in the PS4 community (game world), ergo on PS4 is the best and cheapest English teacher...

I only tolerate it, in our home network, because the teach.....