Help with '<interface> net' as source
-
Hello,
I have configured a couple of interfaces, among which a 'WHOME' interface with the following rules:
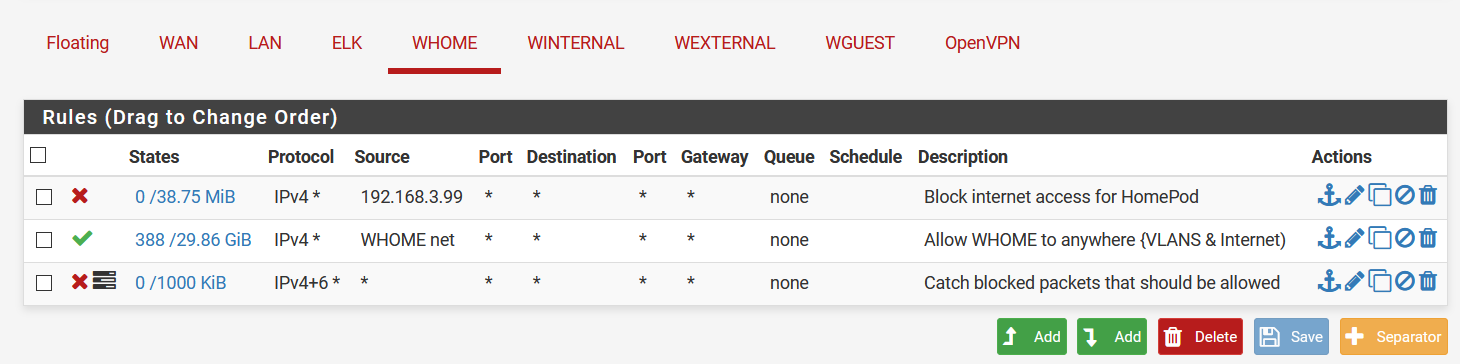
This WHOME interface is assigned to a VLAN:
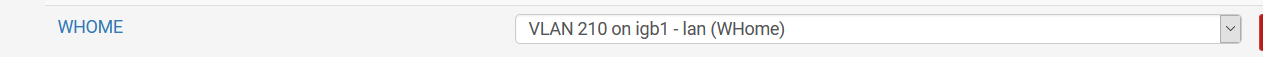
The idea is that everything coming in on that port carrying the 210 tag should be routed to the WHOME interface, and traffic on that interface is free to go wherever it wants.
That all seems fine, however I cannot explain the following firewall blocks:
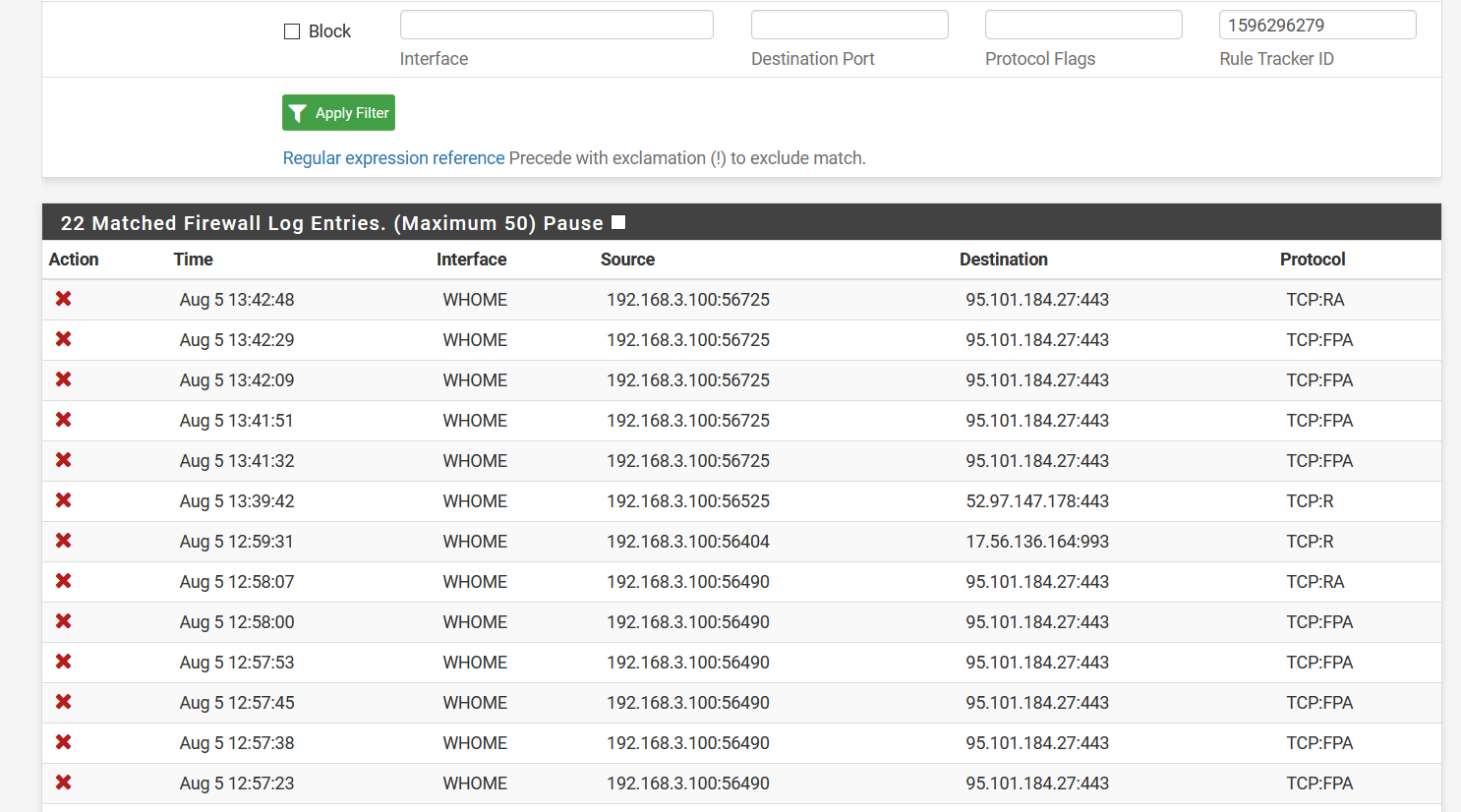
The rule '1596296279' is the firewall rule 'Catch blocked packets that should be allowed' from the first screenshot.
So apparently some packets from the 192.168.3.100 device are not recognized as part of the WHOME interface, even though they do appear in some of the firewall states of that interface:
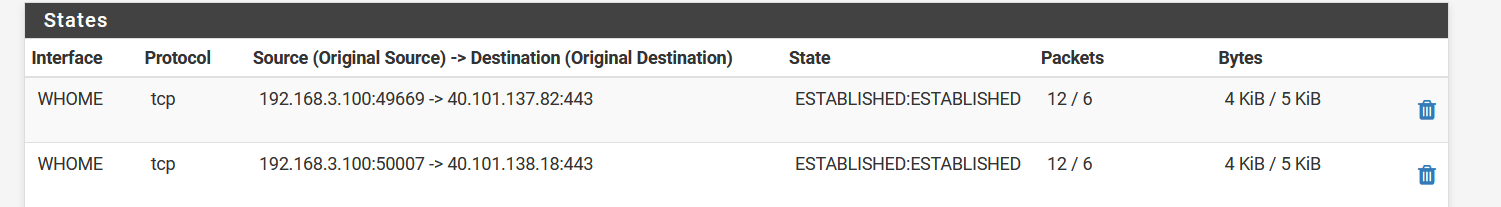
Most packets of the 192.168.3.100 pass fine, it's just some of them do not it seems.
Is this due to the fact that the device that should be tagging these packets (a Ubiquiti AP) makes mistakes? Is it a mistake in my firewall rules? How could I best troubleshoot this behaviour? Any other thoughts?
-
Have you killed the firewall states after adding firewall rules?
You may have asymmetric routing.
-
To be honest, I'm not sure if I killed the states although I've added the last rule 4 days ago and the other ones exist for a long time already. Anyway I will kill them tonight and see if that changes the situation.
-
The problem is still present after resetting the firewall state table.
Any other thoughts? You mentioned 'you may have asymmetric routing', is that a separate potential issue apart from the states that I had to kill?
-
This post is deleted! -
Ok, guess it's no issue at all. I recreated that 'Catch blocked packets that should be allowed' rule with 'WHOME net' as source and it's the same behaviour. According to https://docs.netgate.com/pfsense/en/latest/firewall/troubleshooting-blocked-log-entries-for-legitimate-connection-packets.html it's normal behaviour.