pfSense-on-a-Stick with a Cisco Switch
-
Hi there. I apologize in advance for my ignorance as I am somewhat new to pfSense.
I am trying to set up 3 separate VLANs on my network; Wireless, Servers, and IOT. I am using a Cisco Catalyst 2960 switch (it was the cheapest thing I could find that supported VLANs) which I configured as:
VLAN 10: FA0/1-8
VLAN 20: FA0/9-16
VLAN 30: FA0/17-23
and FA0/24 as the trunk port to pfSense.On pfSense, I have created 3 LAN sub-interfaces with static IPv4s:
bce1.10: 192.168.10.1/24
bce1.20: 192.168.20.1/24
bce1.30: 192.168.30.1/24Each sub-interface has a corresponding DHCP server set up and an allow all rule to allow inter-vlan communication.
My problem occurs when I try to plug a device into any port on VLAN 20 or VLAN 30. VLAN 10 works great, but VLAN 20 and VLAN 30 do not. The devices are able to receive DHCP traffic, but they are not able to communicate with pfSense at all! Pinging 192.168.20.1 on VLAN 20 from the device does not result in a timeout, but... nothing...! I am able to ping from VLAN 10 to VLAN 20 and get a response, but the device cannot communicate the other way.
I thought that maybe it was an encapsulation issue, but I was not able to set encapsulation on the Switch, so (I assume) there is no encapsulation on that switch.
I am completely lost as to what is going on. Any help is truly appreciated!
-
How are the switch ports configured?
If they are reliably getting a lease from the correct DHCP server it is probably all set correctly.
You should probably show your work on the firewall rules on the pfSense interfaces.
-
Thanks for replying so quick!
FA0/1 - 8 are set to mode access mode on VLAN 10.
FA0/9 - 16 are set to mode access mode on VLAN 20.
FA0/17 - 23 are set to access mode on VLAN 30.
FA0/24 is set to trunk mode all VLANs.These are my three interfaces firewall rules.
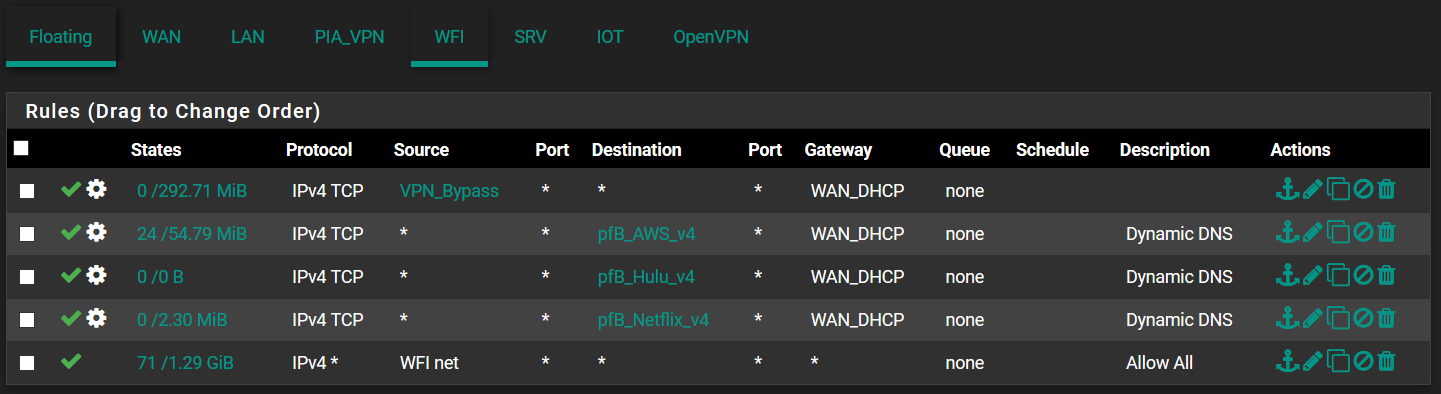
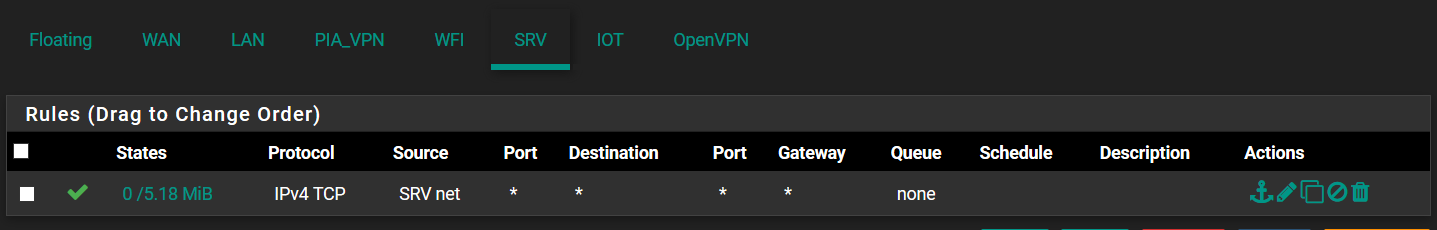
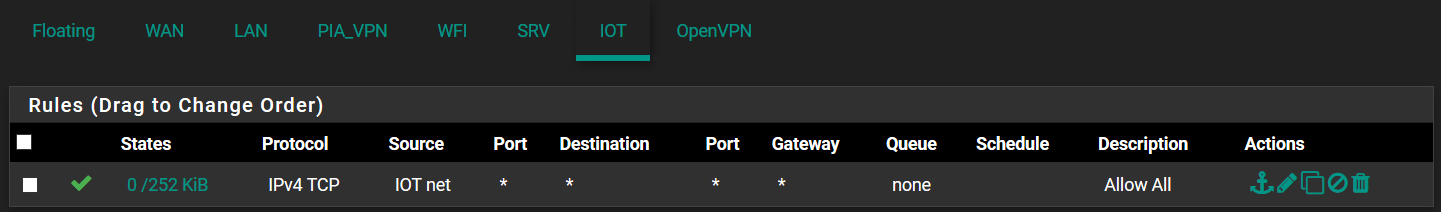
-
Your rules should be protocol any not protocol TCP. Use the default pass rule on LAN as an example.
-
Aha! You are a lifesaver. I feel like an idiot. Thank you so much!